A file security access control method based on cloud computing technology
A security access control and file access technology, applied in the field of information security, can solve the problems of unable to manage files and ensure that file information is not leaked, and achieve the effect of ensuring security and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
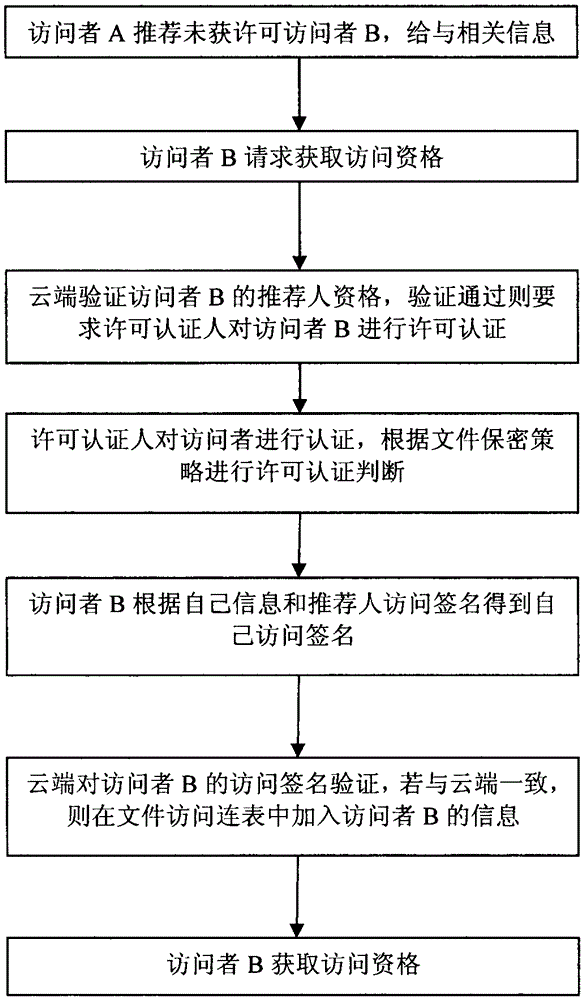
[0035] reference figure 1 , The specific process of a file security access control method based on cloud computing technology is as follows:
[0036] Step 1: Visitor A with access authority recommends visitor B who is not permitted, and informs visitor B of B’s recommendation information;
[0037] Step 2: Visitor B obtains the recommendation information and sends an application review to the cloud server to request access to the file;
[0038] Step 3: After the cloud receives the request information, it first verifies the referrer A’s access qualification, if A does not have the access qualification, it ends; otherwise, proceed to step 4;
[0039] Step 4: Authenticate the identity of visitor B, and require the pre-set license certifier to authenticate visitor B. If the license authentication judgement is not passed according to the document confidentiality policy, it ends; otherwise, go to step 5. ;
[0040] Step 5: Visitor B performs Hash operation on referrer A's visit signature and ...
Embodiment 2
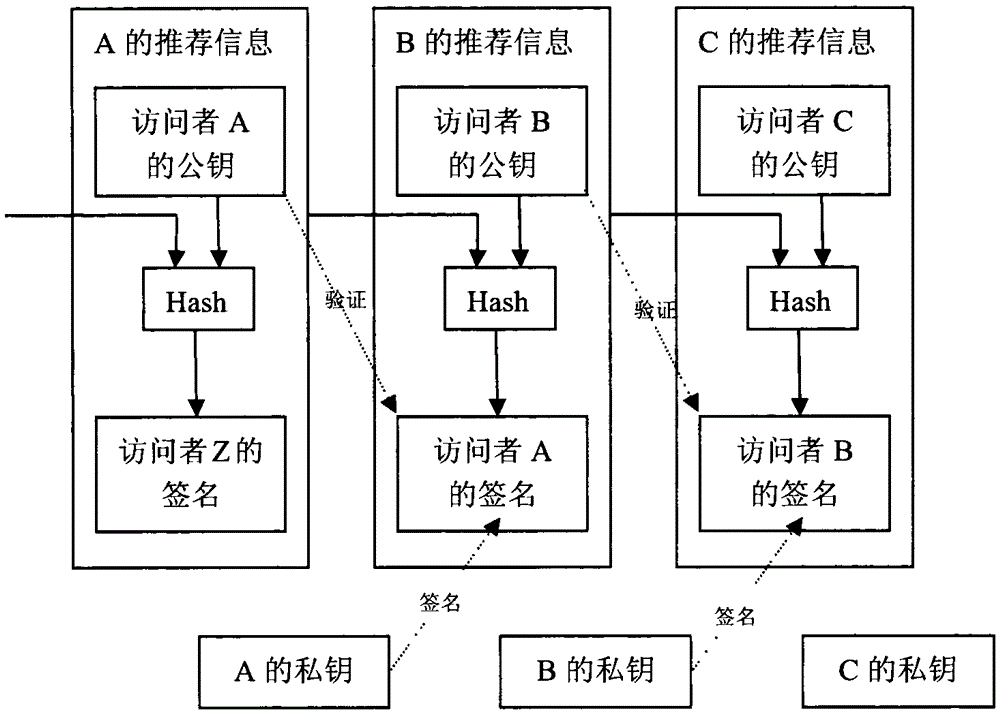
[0043] The visitor recommendation information chain shown in this embodiment is as follows figure 2 As shown, after the visitor B obtains the recommended information, he applies for the access authority to the server, and the server conducts review. Each recommendation information is broadcast to the entire network, and the verified information data is added to the recommendation information chain recognized by the entire network using a distributed time stamp algorithm. The recommended information has the signature of the recommender A, which enables the server to verify the authenticity of the information if necessary; if the visitor B violates the law, the signature can be used to hold the visitor B and his recommender A accountable; When the visitor B has a problem, the information can be used to know the recommender of B and the person recommended by B, so that they can be assessed, avoiding the problem from being enlarged, and ensuring information security.
Embodiment 3
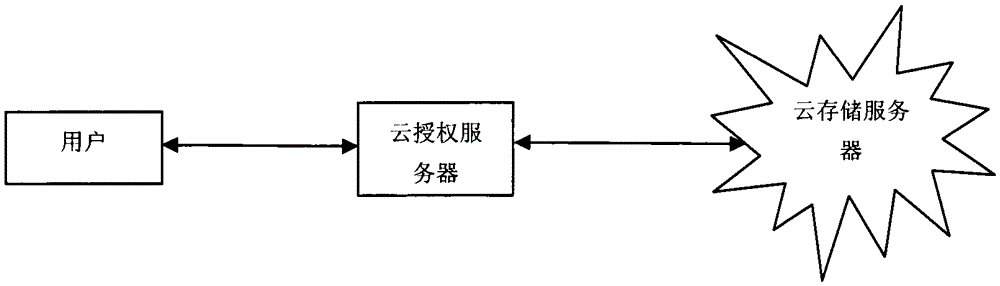
[0045] This embodiment provides a brief schematic diagram of a user accessing cloud storage data, such as image 3 Shown. When a user applies for access to a cloud storage file or recommends a new user, he must first receive the qualification review of the cloud authorization server, and only after passing the review of the authorization server can he perform operations such as file access.
[0046] The user file access qualification involved in the present invention needs to be periodically reviewed on the cloud server to ensure the safety of important files. When the following two situations occur, the cloud server will review the user's access qualifications:
[0047] (1) When users apply to the cloud authorization server for access to important files stored in the cloud, avoid illegal users from accessing important files;
[0048] (2) When a user recommends a new user to the cloud authorization server, ensure that the user has the authority to recommend a new user.
[0049] The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com