A timely user revocation method based on attribute-based encryption in cloud environment
An attribute-based encryption and cloud environment technology, which is applied in user identity/authority verification and key distribution, can solve the problems of slow revocation efficiency of cloud storage users, and achieve the effects of timely revocation, pressure reduction and workload reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
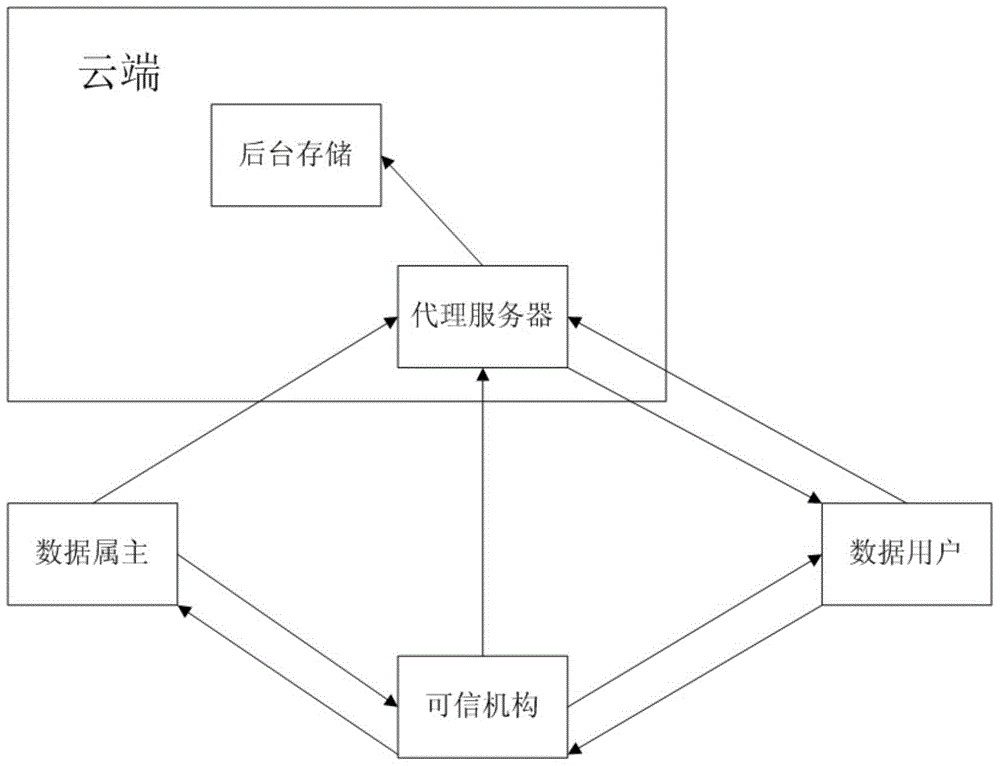
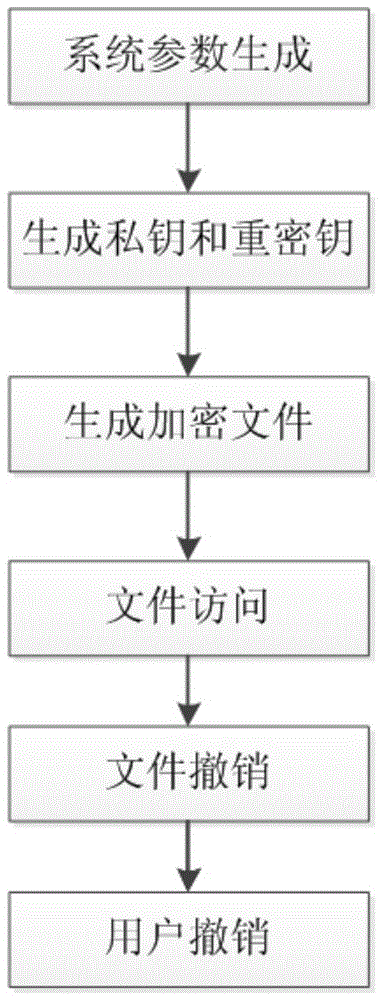
[0101] Such as figure 2 As shown, the present invention proposes a timely user revocation method based on attribute-based encryption under a cloud environment, which includes the following steps:
[0102] Step 1: System parameter generation;
[0103] The trusted organization first randomly selects generators, generates bilinear groups and bilinear maps, and generates two pairs of master keys and public keys. The master key is reserved and the public key is made public;
[0104] Step 2: Generate private key and proxy key;
[0105] The user provides relevant information to the trusted organization and applies for access to the private key; the trusted organization assigns the corresponding data attributes according to the information provided by the user and generates the private key SK u And send it to the user; the data owner sends the special attribute set of the file F to the trusted organization, and the trusted organization generates the private key SK for it x , and g...
Embodiment 2
[0175] Assuming that a data owner O stores file F in CBS, user U applies to a trusted institution for partial private keys, and then sends an access request to CPSP for file F. The data owner performs two operations on the file: 1. Revoke the user; 2. Delete the file.
[0176] Its specific implementation plan is:
[0177] (1) The trusted organization first randomly selects generators, generates bilinear groups and bilinear maps, and generates two pairs of master keys and public keys. The master key is reserved and the public key is made public.
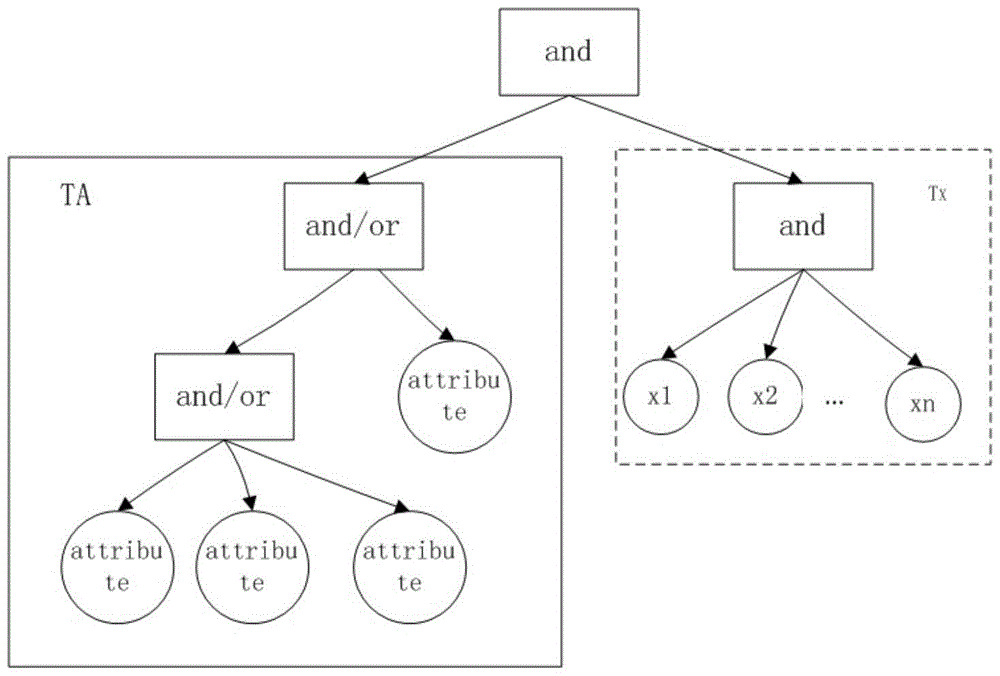
[0178] (2) The data owner selects the attribute set for the file F to construct the access control tree T A , select a special attribute set to construct an access control tree T x , encrypt file F to generate ciphertext CT, and send it to CPSP.
[0179] (3) CPSP selects a unique ID number for the file, generates a user revocation list for the file, saves the file to CBS, and then returns the ID number to the data owner.
[0180] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com