Sound key and computer security protecting method
A computer security and computer technology, applied in the direction of digital data authentication, etc., can solve problems such as being easily cracked, and achieve the effect that it is not easy to steal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
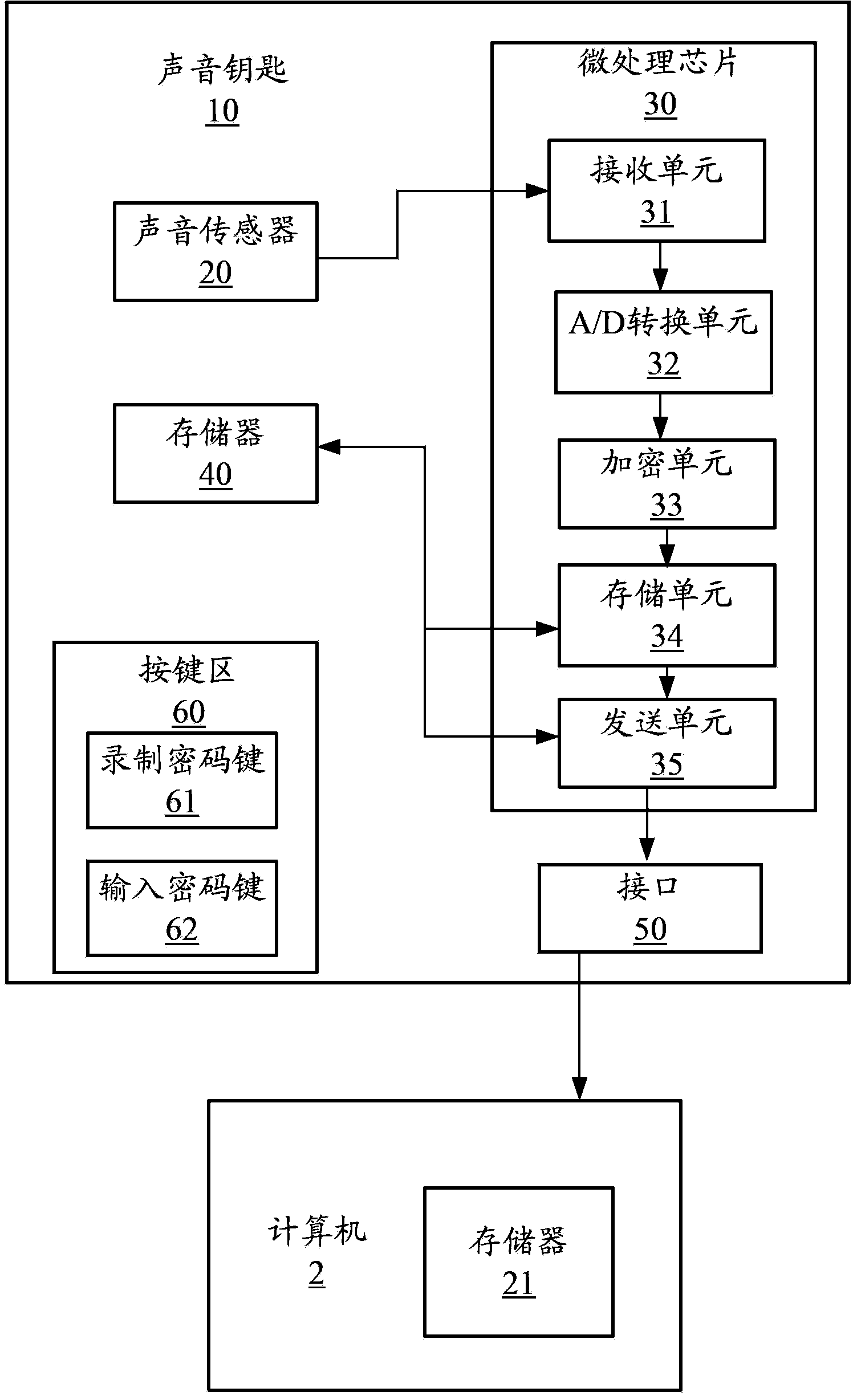
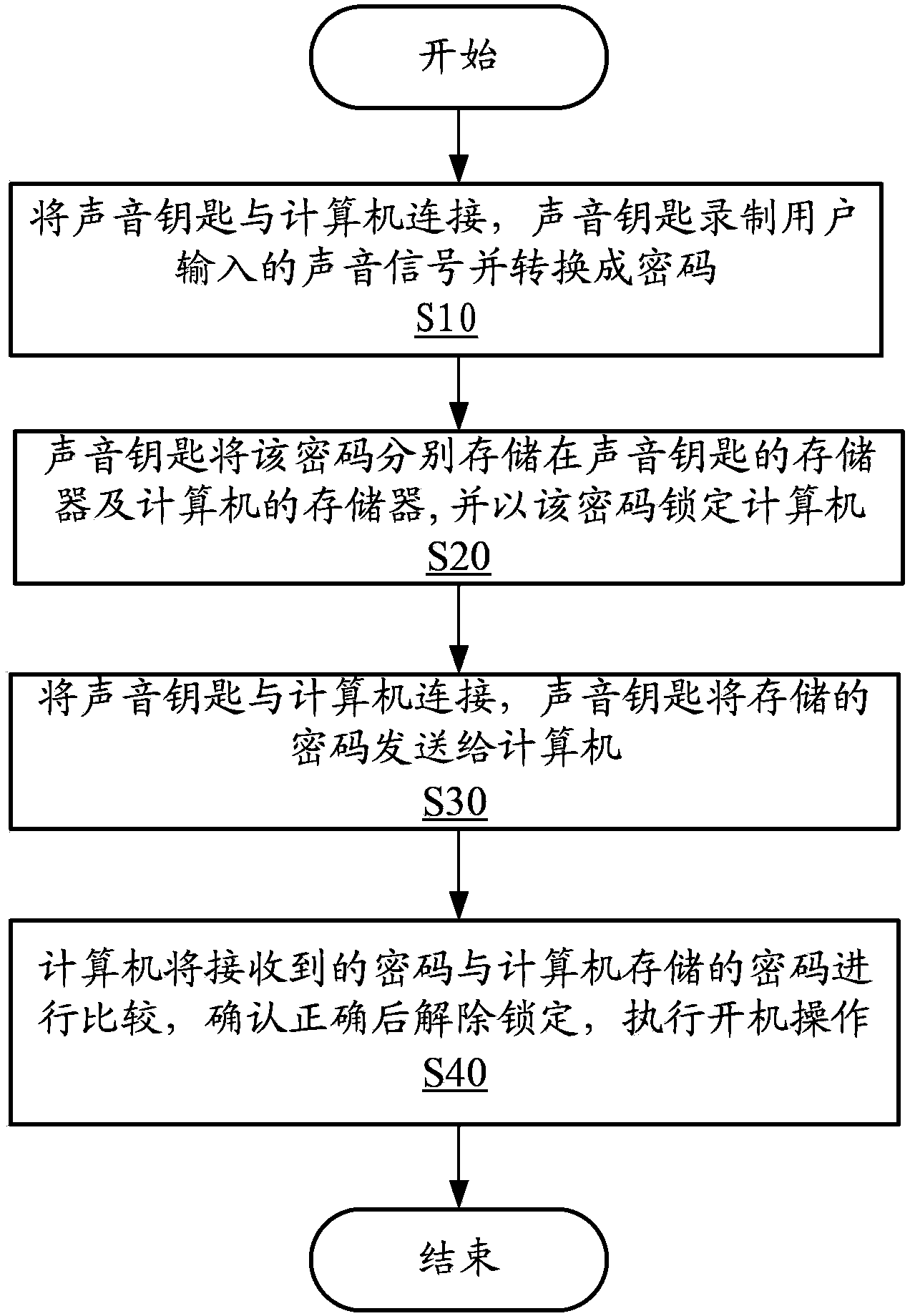
[0012] refer to figure 1 Shown is a functional block diagram of a preferred embodiment of the sound key 10 of the present invention. In this embodiment, the sound key 10 includes a sound sensor 20 , a microprocessor chip 30 , a memory 40 and an interface 50 . The micro-processing chip 30 includes a receiving unit 31 , an analog / digital (A / D) conversion unit 32 , an encryption unit 33 , a storage unit 34 and a sending unit 35 . Units 31-35 are components containing solidified computerized program instructions, and the computerized programs contained in each unit can complete special functions (for details, please refer to the specific introduction of units 31-35 below).
[0013] The sound key 10 is a portable electronic device, which can be connected to the computer 2 through the interface 50 to perform encryption and decryption operations on the computer 2 . The interface 50 can be a serial interface, a USB interface and the like. The sound key 10 can also include a keypad ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com