Method and system for machine-card two-way authentication
A two-way authentication, machine card technology, applied in wireless communication, network data management, electrical components, etc., can solve problems such as poor flexibility and invalid authentication mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. However, the embodiments of the present invention are not limited thereto.
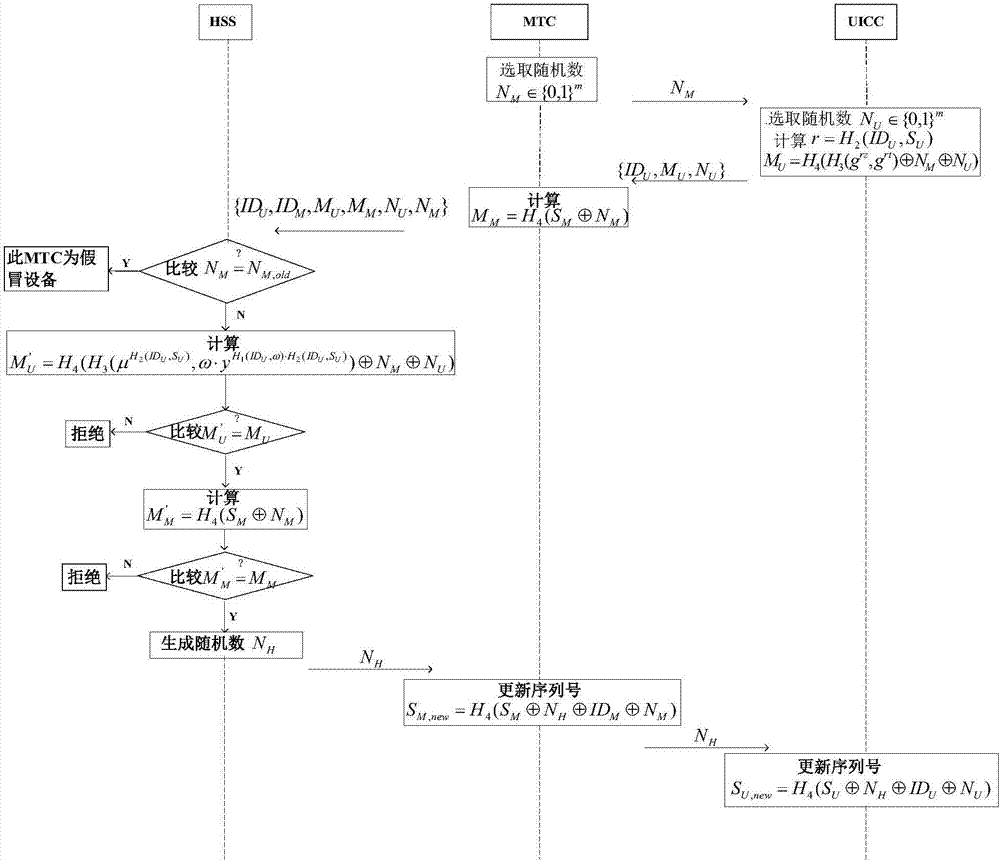
[0049] The embodiment of the method of the present invention is based on the computational Diffie-Hellman problem, and in the process of two-way authentication, the network side can update the secret information preset in the device and the card in time, resisting the attacker's eavesdropping, replay, etc. attacks, so that the scheme has higher security. Store the serial numbers of MTC devices and UICCs through HSS; the serial numbers of MTC devices and UICCs are not public and are secret information; HSS maintains the initial random value list of MTC devices and the list of serial numbers of MTC devices and UICCs; HSS only distributes part of the private key For UICC, there is no key escrow issue.
[0050] Such as figure 1 As shown, it is a flowchart of the principl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com