A trusted network connection method based on ipsec
A network connection and trustworthy technology, applied in the field of IPsec-based trusted network connection, can solve the problems of not considering how to protect terminal security, unable to ensure service trustworthiness, etc., to achieve the effect of ensuring dynamic trustworthiness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
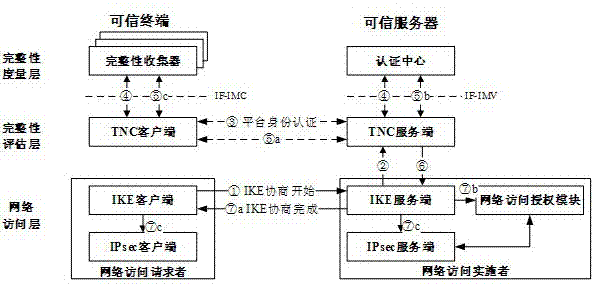
[0026] When the trusted terminal accesses the trusted server, the underlying communication channel uses the IPsec security channel. Before the life cycle of the security association (SA) used by the IPsec security channel ends, both parties need to conduct an IKE session to generate a new security association (SA).
[0027] This patent adds platform identity authentication and integrity verification to the process of IKE session connection establishment, so that when the security association (SA) is periodically updated through the IKE session between the terminal and the server, the platform identity authentication, integrity verification is also periodically performed. verify. Proceed as follows:
[0028] 1) The IKE client initiates negotiation to the IKE server, and the first step is key negotiation.
[0029] 2) When the key negotiation between the IKE client and the IKE server is successful, the IKE server notifies the TNC server that an IKE negotiation request is coming...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com