Docker platform dynamic protection method based on trusted computing
A trusted computing and platform technology, applied in secure communication devices and key distribution, can solve problems such as high complexity, inability to guarantee the dynamic integrity of running services, and inability to isolate and store metric values
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
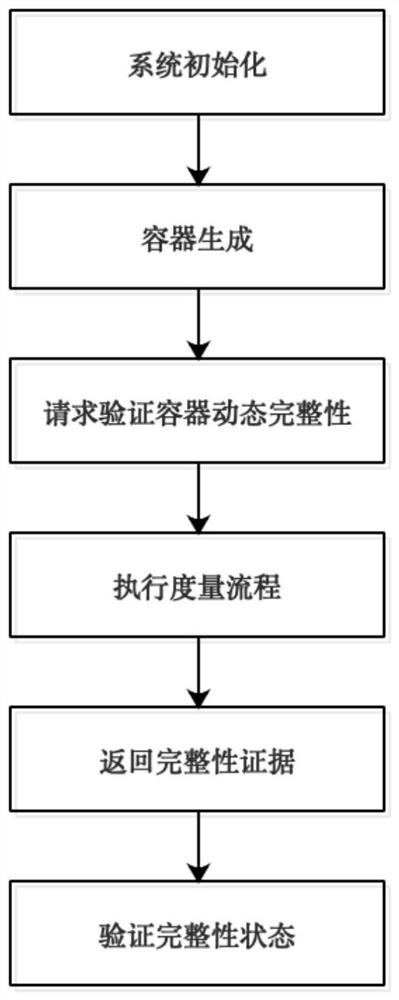
[0061] The present invention will be further described below in conjunction with the accompanying drawings. Such as figure 1 Shown, the present invention comprises the following steps:
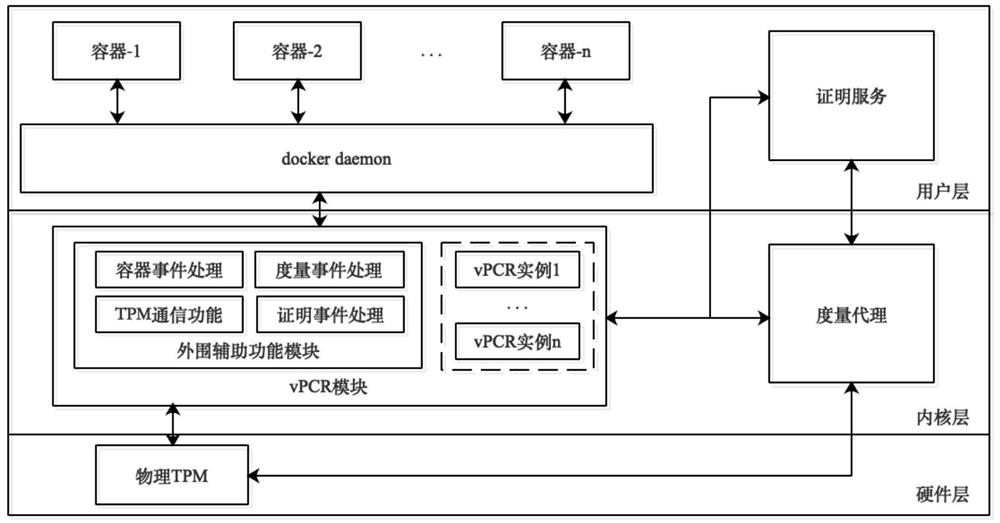
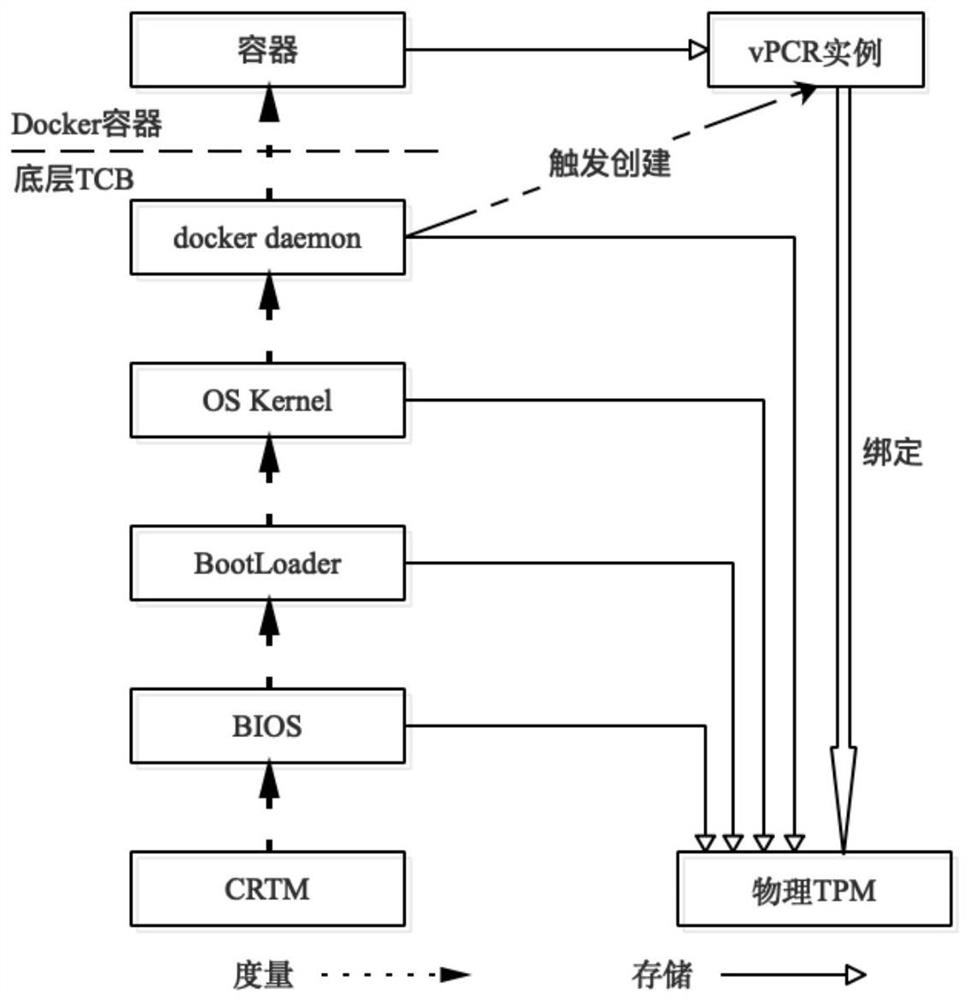
[0062] Step 1, system initialization: the / sys / kernel / security / vpcr / pcr_old file is generated during the initialization of the vPCR module (set the value in it as PCR old ), which is used to record the old value of the PCR (set to pPCR) in the physical TPM bound to the vPCR instance. When the initialization is completed, the PCR old and pPCR are both 0. The overall architecture of the vPCR module is as follows figure 2 shown. During the initialization process of the measurement agent module, a dynamic measurement file of the host domain is generated, and the PID namespace of the host domain is recorded.
[0063] Step 2, container generation: the user requests the Docker platform to generate a container to run the specified service. During the container generation process, the transfer of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com