A solution to phishing attacks on Android platform
A phishing attack and solution technology, applied in the software field, can solve problems such as affecting system performance, unable to intercept phishing applications, losing monitoring effects, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the accompanying drawings. It should be noted that the present embodiment provides detailed implementation steps and specific operation methods on the premise of the technical solution, but the protection scope of the present invention is not limited to the present invention. Example.
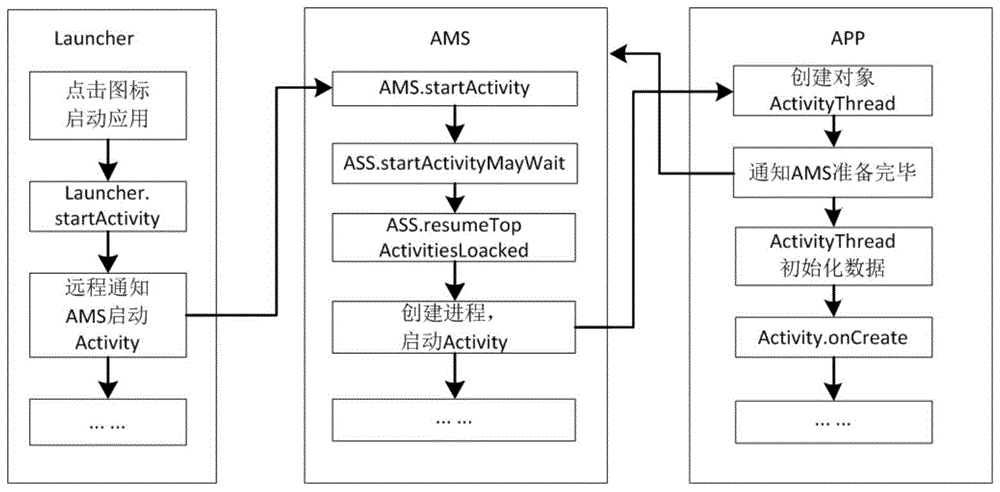
[0050] On the Android platform, the activation of all applications is the responsibility of the activity management service AMS of the framework layer, and the application layer has no authority to interfere with the process of AMS. A solution to phishing attacks on the Android platform is to set an identification and interception module in AMS. Specifically include the following processes:
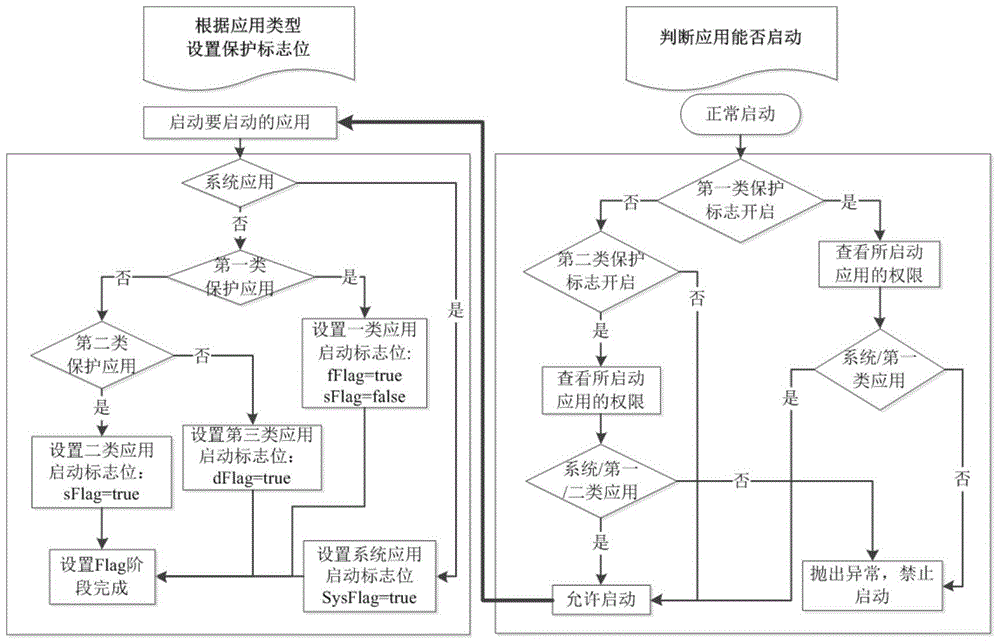
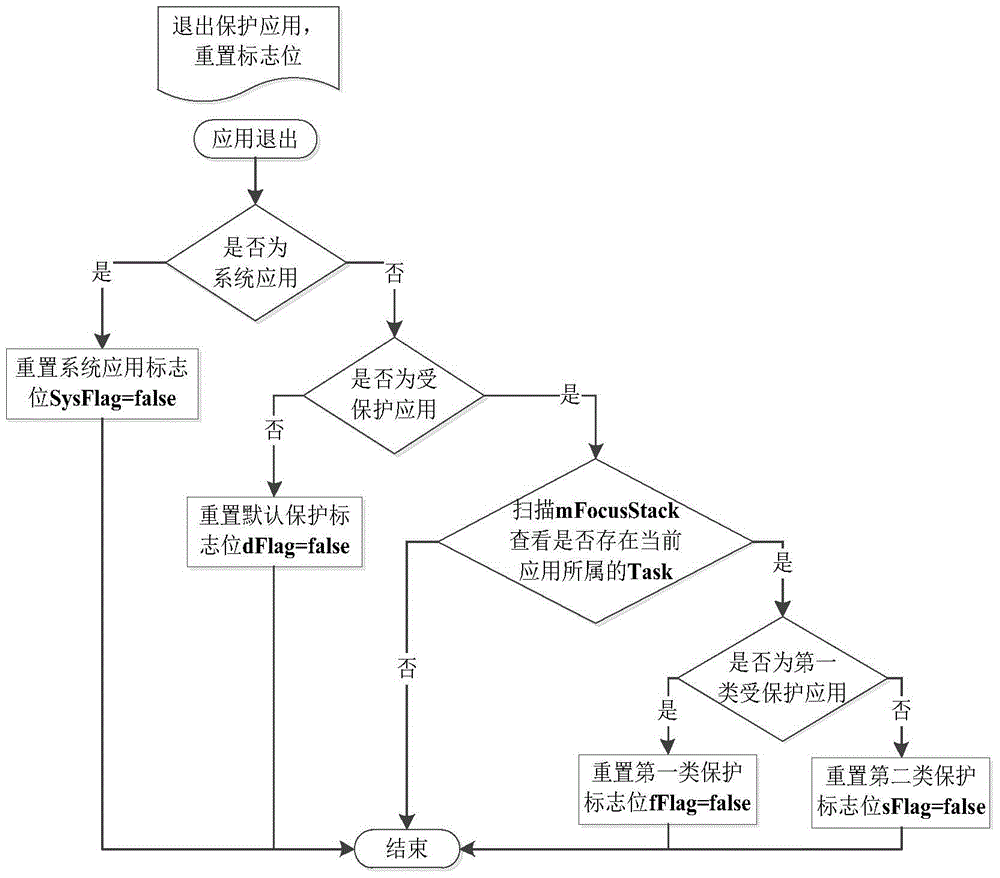
[0051] According to the security sensitivity of the application, the user divides the applications in the mobile phone into three categories except the system application: the first type of protected application, the second t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com