Payment method and payment system by sensitive information identification
A sensitive information and identification technology, which is applied in the field of network security, can solve problems such as information leakage, encryption difficulties, and easy loopholes, and achieve excellent technical effects, save key storage, and simple processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
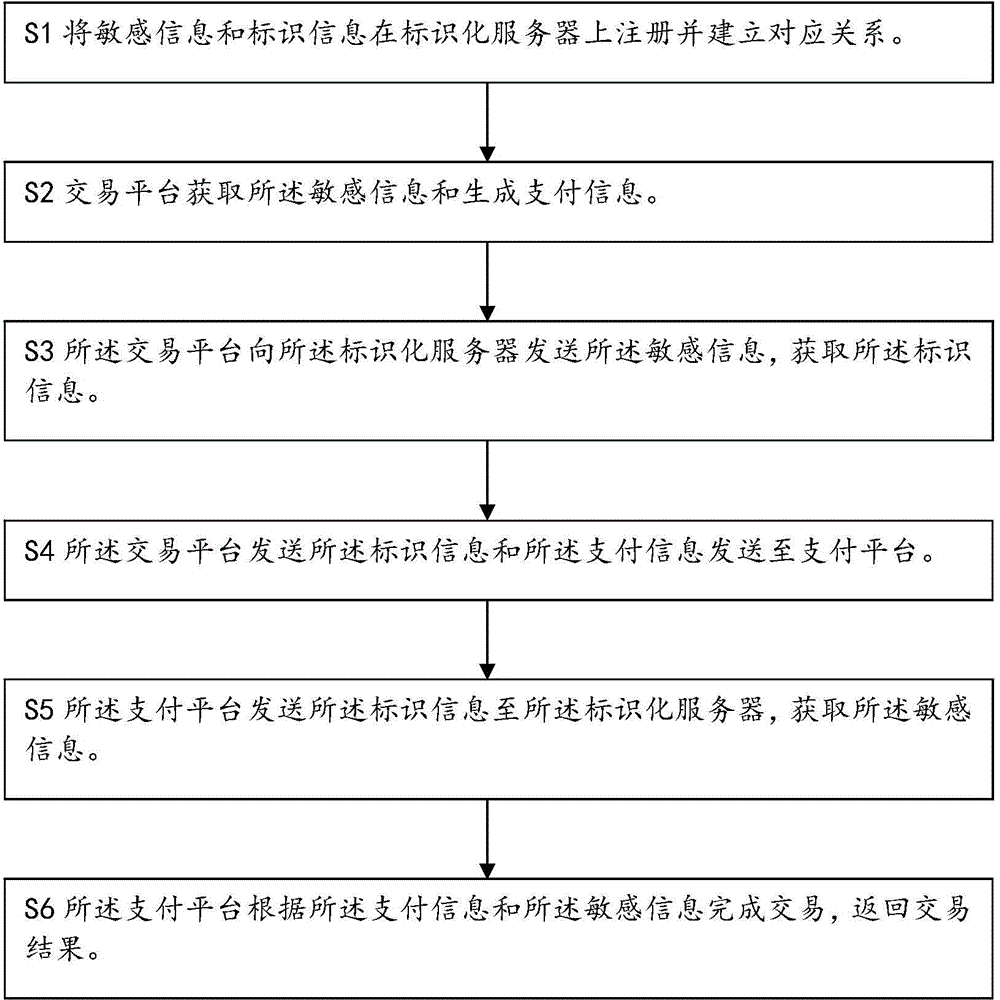
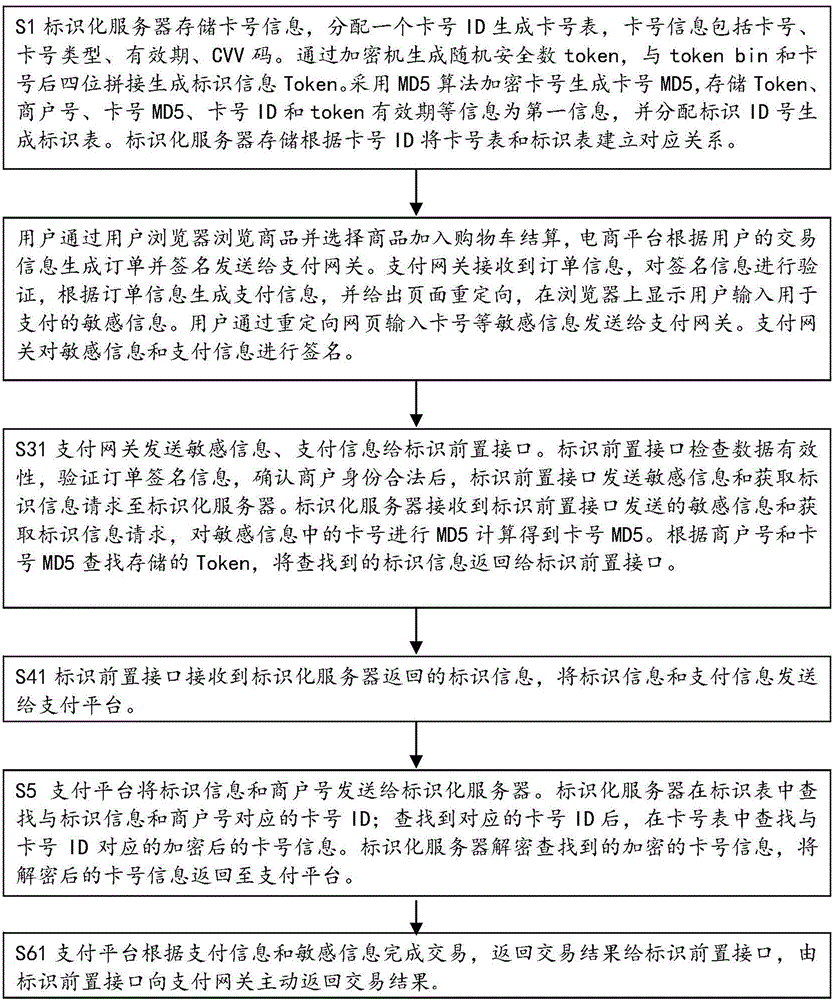
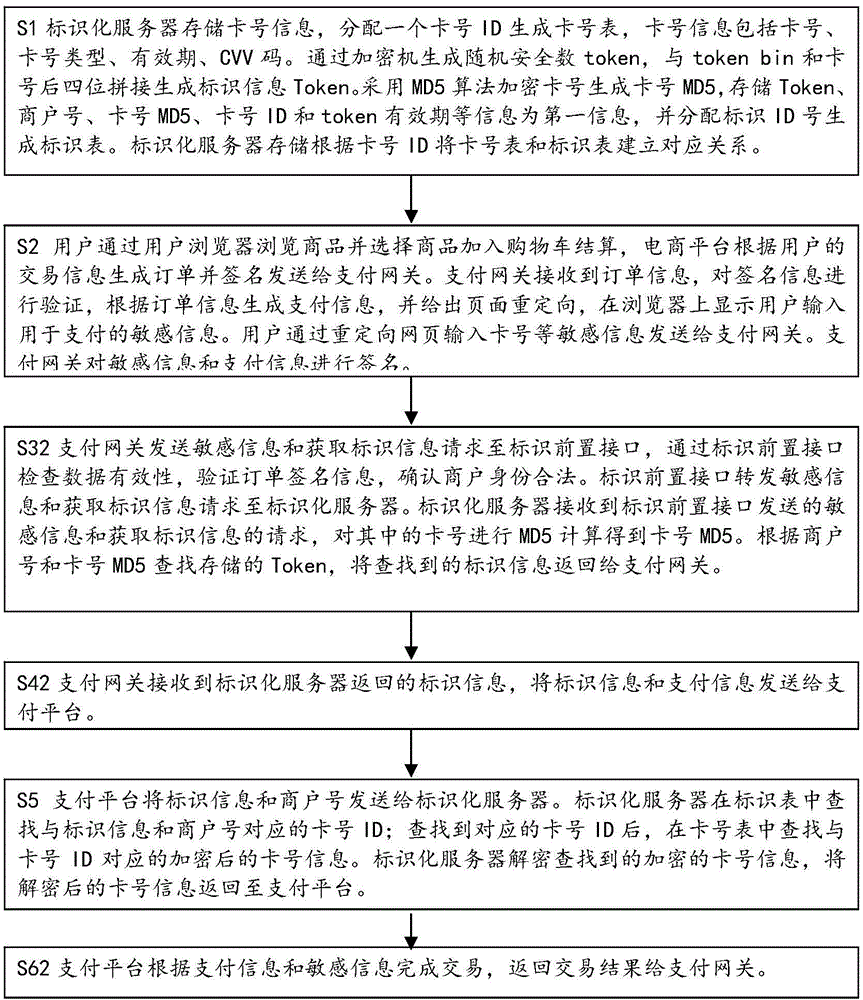
[0053] Such as figure 1Shown is a schematic flow chart of the steps of the payment method for marking sensitive information of the present invention. As a specific embodiment 1 of the present invention, the present invention provides a payment method for marking sensitive information, including:
[0054] S1 registers sensitive information and identification information on the identification server and establishes a corresponding relationship;
[0055] S2 trading platform obtains sensitive information and generates payment information;
[0056] S3, the transaction platform sends the sensitive information to the identification server to obtain the identification information;
[0057] S4, the transaction platform sends the identification information and the payment information to the payment platform;
[0058] S5 The payment platform sends the identification information to the identification server to obtain the sensitive information;
[0059] S6 The payment platform completes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com