A system and method for implementing a pseudo-secure network architecture based on hardware reconfiguration
A security network and system implementation technology, which is applied in the field of implementation system of mimic security network architecture, can solve the problems of not considering the security and reliability of system hardware, and the protection has little effect, so as to achieve the effect of improving system reliability and defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
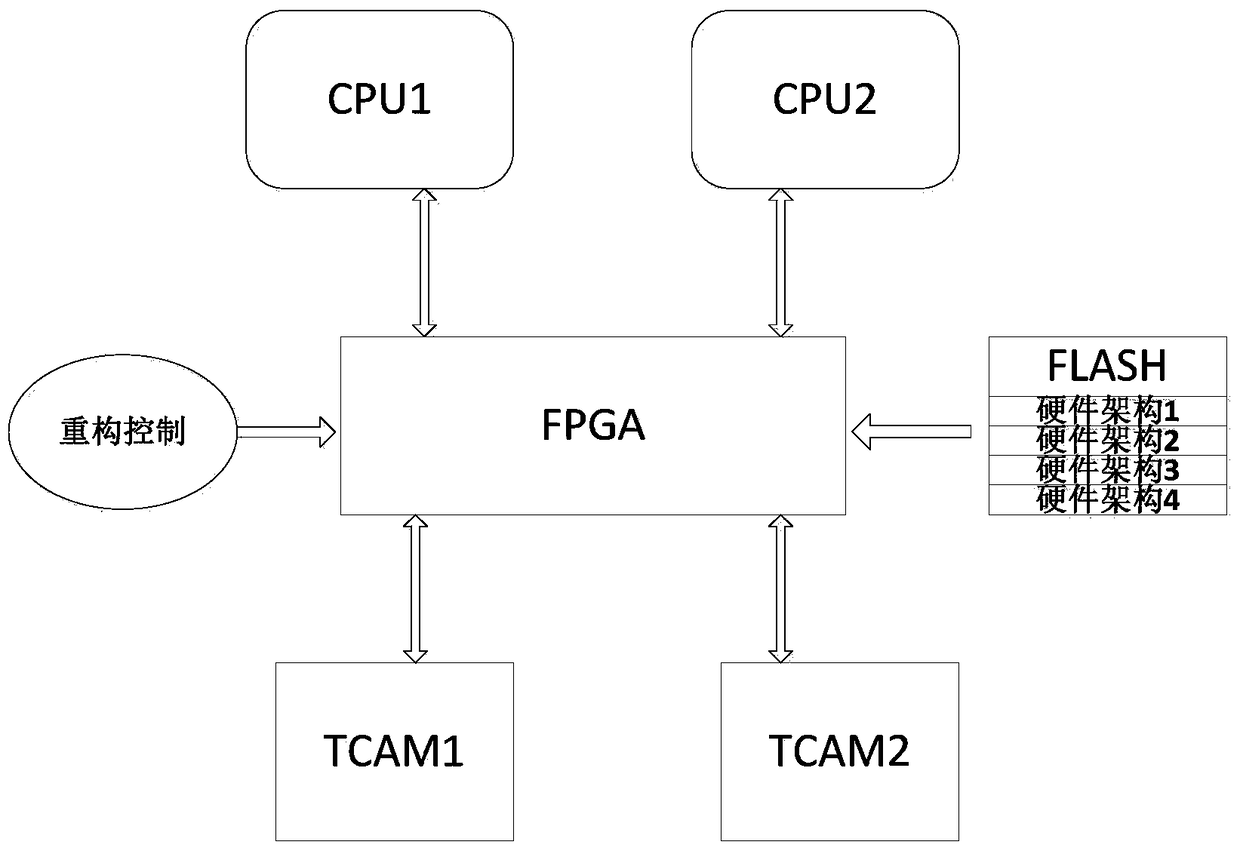
[0042] Specific embodiment 1: as figure 2 As shown, the system includes two mutually independent CPU chips (CPU1 and CPU2), two TCAM chips, FPGA chip and memory flash;
[0043] Among them, 4 reconstructed hardware architecture forms are stored in flash, including hardware architecture 1: using CPU1 and TCAM1 for hardware combination; hardware architecture 2: using CPU1 and TCAM2 for hardware combination; hardware architecture 3: using Hardware combination of CPU2 and TCAM1; and hardware architecture 4: use CPU2 and TCAM2 for hardware combination, in which CPU1 and CPU2 can use products from different manufacturers, and the FPGA reconfiguration method uses dynamic reconfiguration, which is reconfigured within the CPU chip settings. The structural control mechanism is to select one of the four hardware architectures sequentially or randomly every day for combined use of hardware. In this way, the system hardware level can be randomly switched and used in different hardware arc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com