trigger user authentication in the communication network
A technology of communication network and communication equipment, which is applied in the field of user re-authentication, and can solve problems such as the inability to prevent unauthorized access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
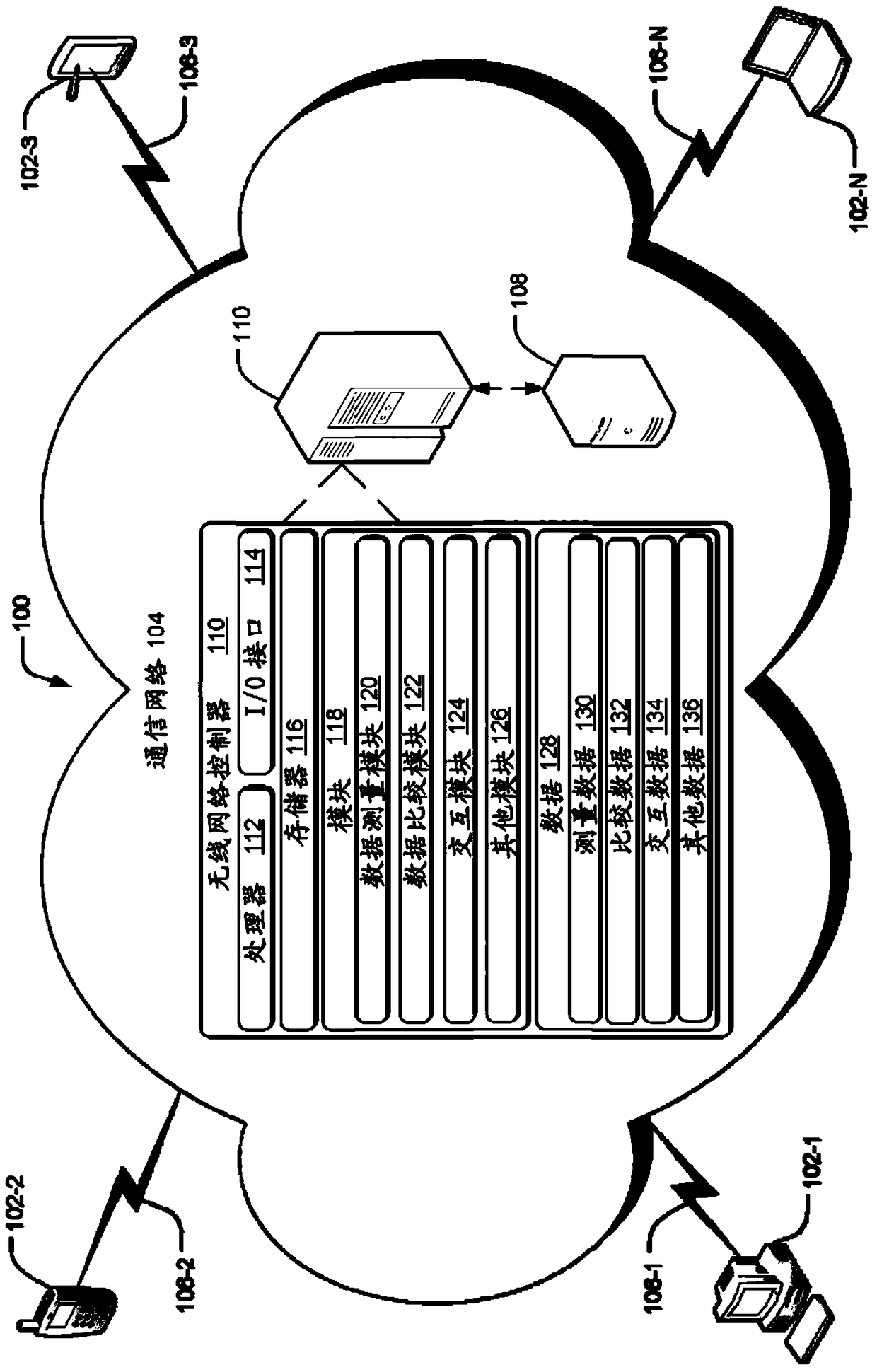
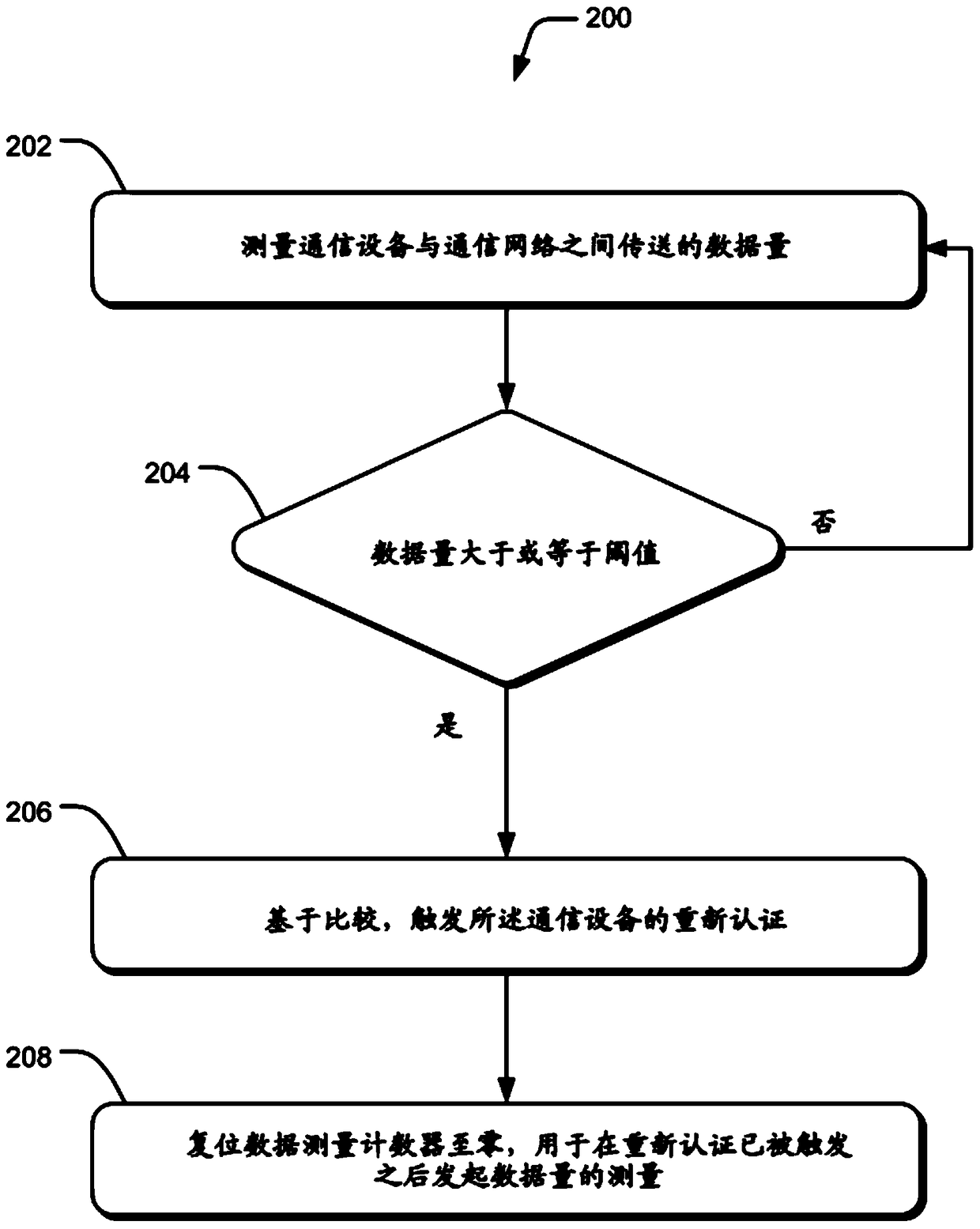
[0015] This topic relates to user reauthentication in communication networks. The method can be implemented in various communication devices communicating over various networks. Communication devices that can implement the methods include, but are not limited to, cellular phones, smart phones, personal digital assistants (PDAs), portable computers, desktop computers, wireless data cards, servers, and the like. Communication networks in which the method may be implemented include, but are not limited to, Code Division Multiple Access (CDMA) implementing Evolution Data Optimized or Evolution Data Unique (EVDO), Global System for Mobile Communications (GSM) networks, Universal Mobile Telecommunications System (UMTS) ) network, Wideband Code Division Multiple Access (W-CDMA) network, etc. Although the description herein refers to an EVDO system, those skilled in the art will understand that, albeit with some variations, the methods and systems may be implemented in other communic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com