Method, terminal and server for realizing screen digital watermarks
A technology of digital watermarking and realization method, applied in the field of information hiding, can solve problems such as failure to leak secrets, and achieve the effect of being difficult to remove
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
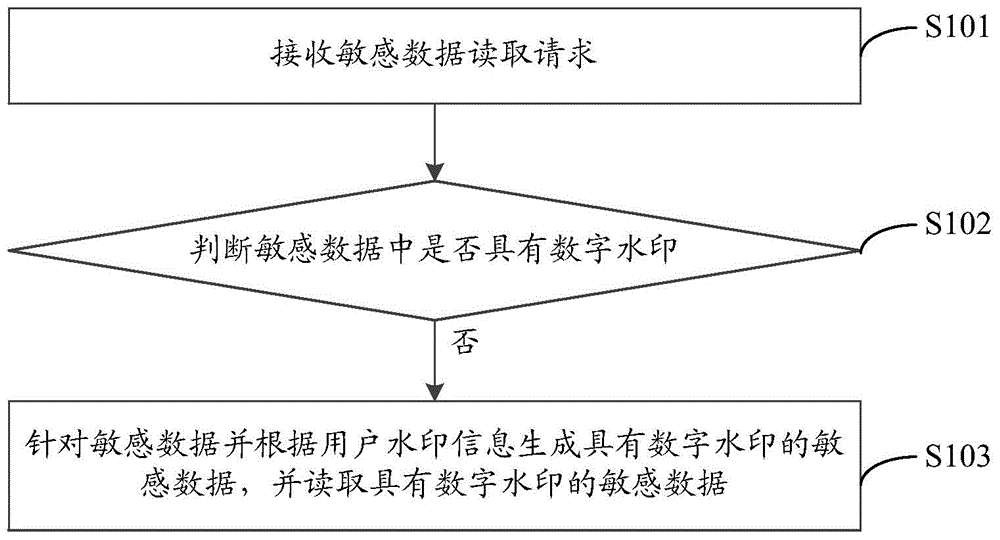
[0034] see figure 1 , figure 1 It is a flow chart of the implementation method of screen digital watermarking provided by Embodiment 1 of the present invention, and the details are as follows:
[0035] In step 101, a sensitive data read request is received.
[0036] Wherein, the sensitive data read request indicates sensitive data.
[0037] In step 102, it is judged whether there is a digital watermark in the sensitive data.
[0038] Wherein, upon receiving the sensitive data read request, the sensitive data is not read immediately, but whether there is a digital watermark in the sensitive data is judged first.
[0039] In step 103, sensitive data with a digital watermark is generated for the sensitive data according to the user watermark information, and the sensitive data with the digital watermark is read.
[0040] Among them, when it is judged that there is no digital watermark, sensitive data with a digital watermark will be generated for the sensitive data, and the u...
Embodiment 2
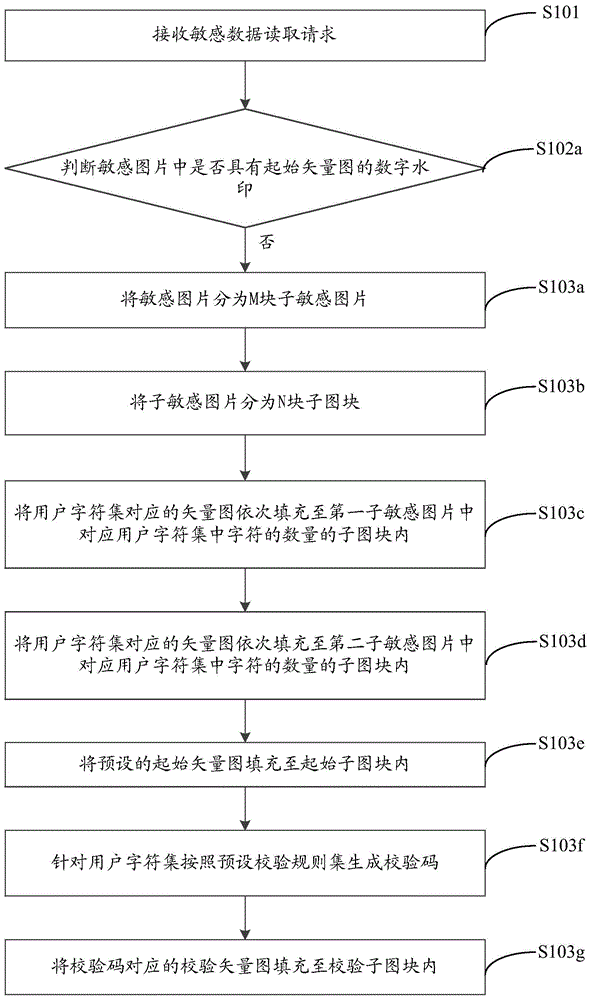
[0044] It should be noted that the method of the embodiment of the present invention also provides a way to generate sensitive data with a digital watermark, please refer to figure 2 , figure 2 It is a flow chart of the implementation method of the screen digital watermark provided by Embodiment 2 of the present invention, in figure 1 On the basis of , when the sensitive data is a sensitive image, such as figure 2 As shown, step 103 may include:
[0045] Step 103a, divide the sensitive picture into M sub-sensitive pictures.
[0046] Wherein, M is an integer not less than 1, and when dividing the sub-sensitive picture, it can be divided according to the preset size of the sub-sensitive picture.
[0047] For example, the size of each sub-sensitive picture is divided into 120px*150px, where px is a pixel, and the size of the sub-sensitive picture can be divided according to the actual situation.
[0048] Step 103b, dividing the sub-sensitive picture into N sub-picture bloc...
Embodiment 3
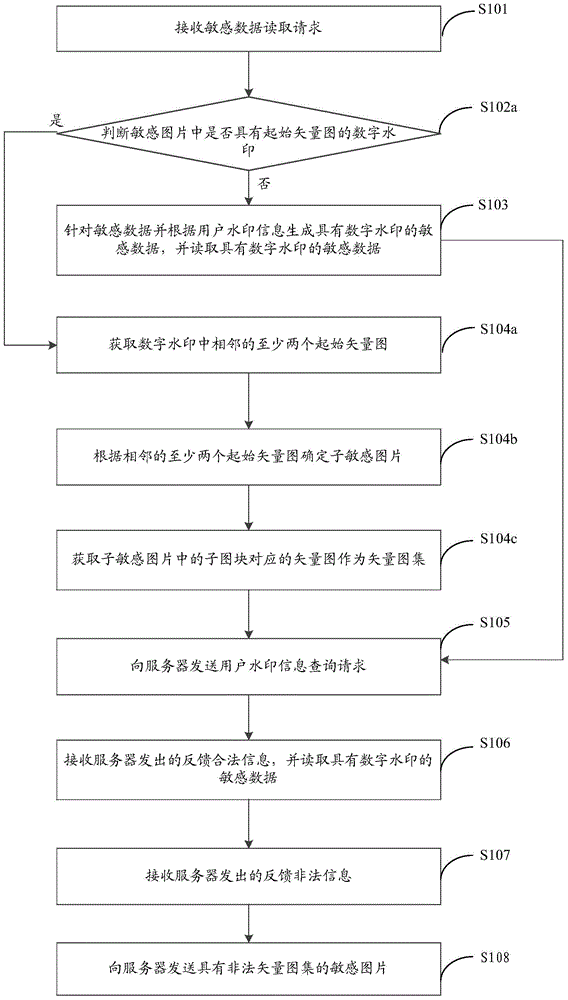
[0076] see image 3 , image 3 It is a flow chart of the implementation method of the screen digital watermark provided by Embodiment 3 of the present invention, such as image 3 shown in figure 1 or figure 2 On the basis of , methods may also include:
[0077] Step 104: Determine a vector map set of user watermark information corresponding to the digital watermark according to the digital watermark.
[0078] Wherein, if there is a digital watermark in the sensitive data, the vector map set of user watermark information corresponding to the digital watermark can be determined according to the digital watermark.
[0079] Step 105, sending a user watermark information query request to the server.
[0080] Wherein, after the vector map set is determined, a user watermark information query request is sent to the server, and the user watermark information request carries the vector map set of the user watermark information corresponding to the digital watermark.
[0081] It ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com