A hash storage method based on ip quintuple
A quintuple and hash technology, applied in the field of network session statistics and analysis, can solve the problems of slow addition and search, uneven distribution of hashes, etc., achieve uniform distribution of hash storage, reduce hash conflicts, and improve hash The effect of storage efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
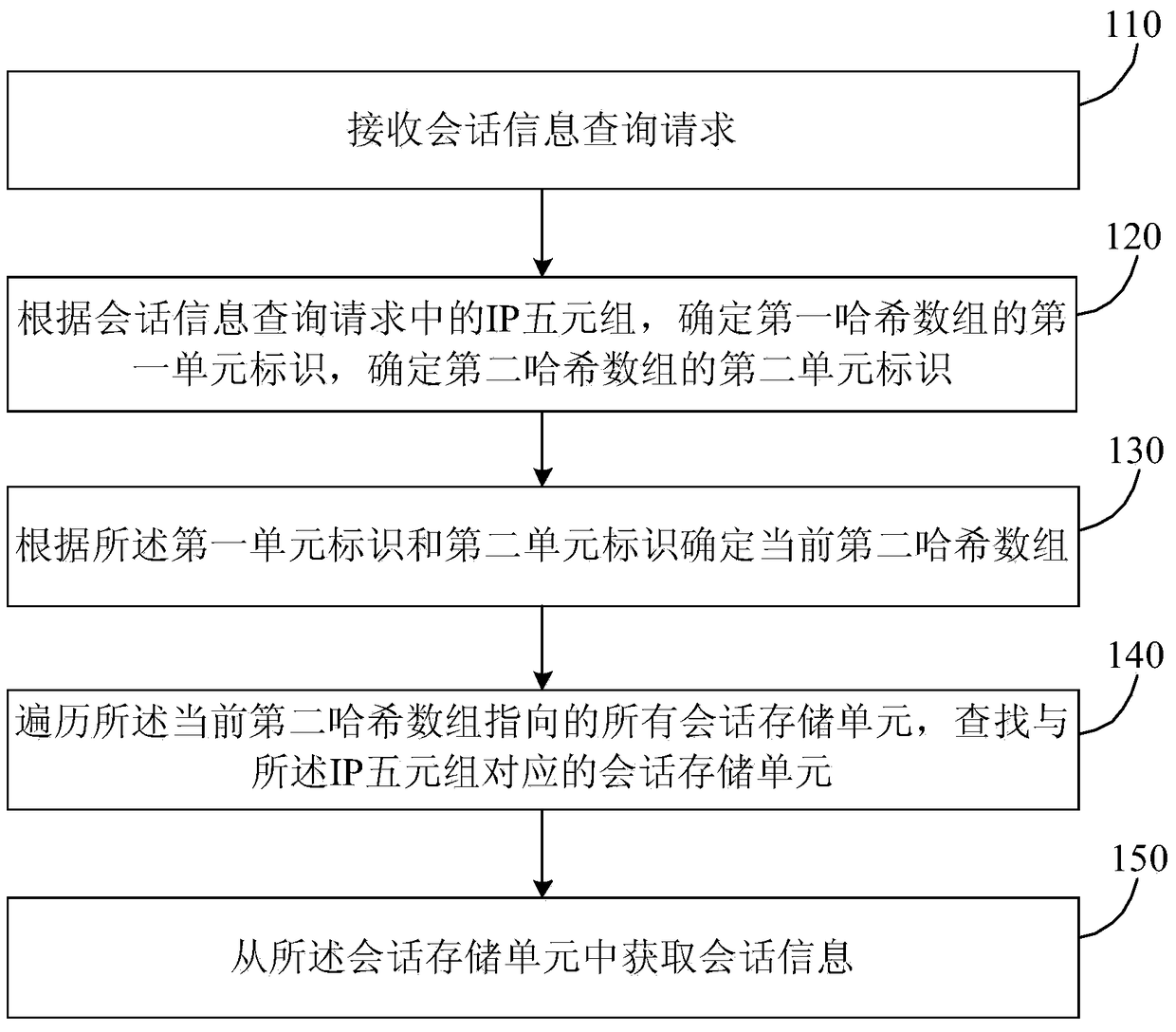
[0022] figure 1 It is a schematic flowchart of an IP quintuple-based hash storage method provided by Embodiment 1. This method is applicable to the case of converting larger data information into smaller data information and storing them in a large-traffic network environment, which is convenient for access and statistical analysis. The method is executed by a device based on an IP quintuple hash storage method, the device can be set in a terminal, and can be realized in the form of software and / or hardware. For example, operators such as Internet Service Provider (ISP, Internet Service Provider), Internet Content Provider (ICP, Internet Content Provider), Internet Data Center (IDC, Internet Data Center) and other operators can use this method to detect and clean the traffic. Ensure the normal and stable operation of the network and the normal development of business.
[0023] Such as figure 1 As shown, the method includes:
[0024] S110. Receive a session information quer...
Embodiment 2
[0049] This embodiment is based on Embodiment 1, and further performs the following operations after traversing all session storage units pointed to by the current second hash array and searching for the session storage unit corresponding to the IP quintuple:
[0050] If the session storage unit corresponding to the IP quintuple is not found, then apply for a new session storage unit in the storage space, store the IP quintuple information in the new session storage unit, and use according to the first hash The first unit identifier and the second unit identifier calculated by the Hive function and the second hash function determine a final second hash array, and the final second hash array is used to point to the new session storage unit.
[0051] Further, if the final second hash array does not point to the session storage unit, directly make the final second hash array point to the new session storage unit, and then return to the new session storage unit session information...
Embodiment 3
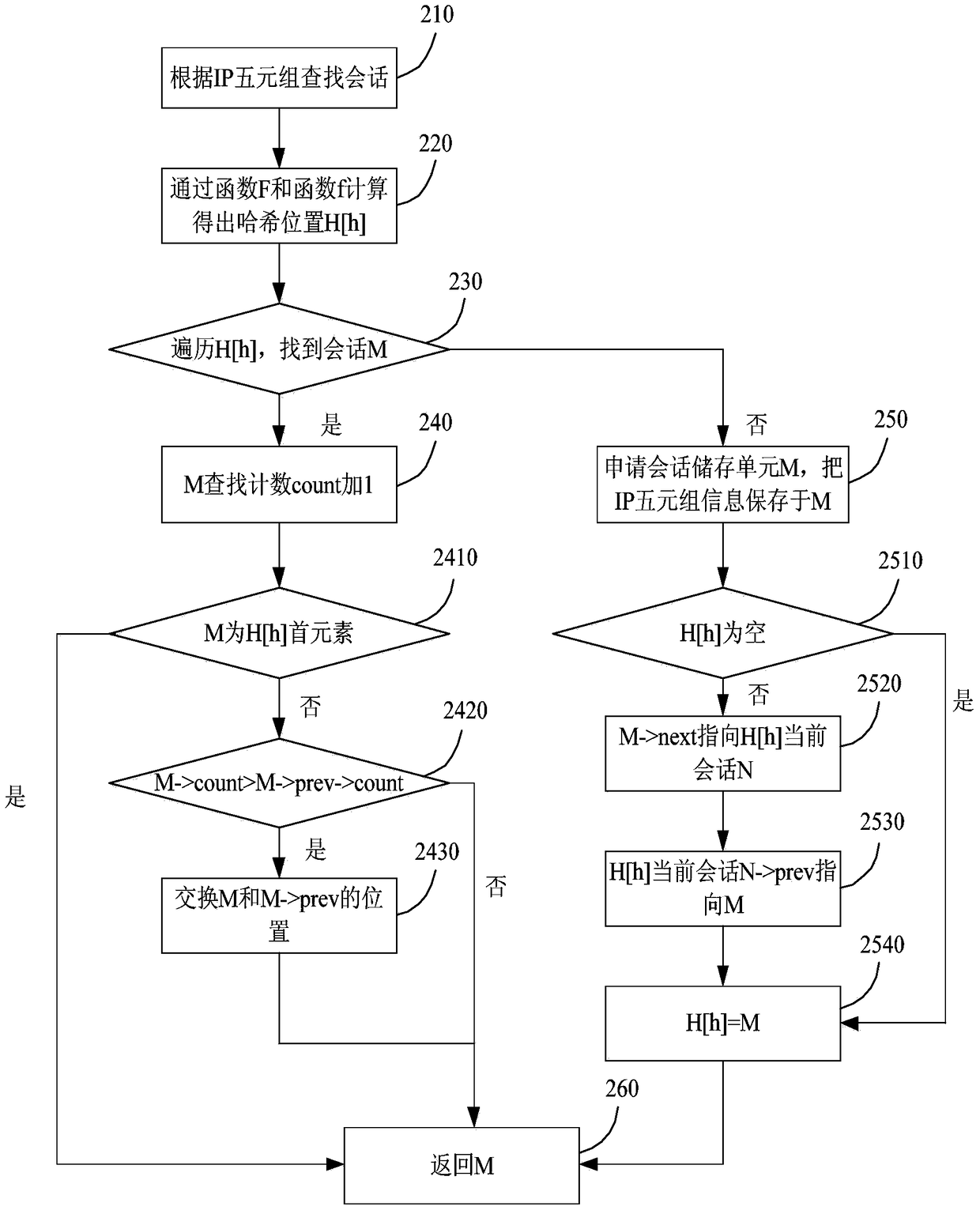
[0056] figure 2 It is a schematic flowchart of an IP quintuple-based hash storage method provided by Embodiment 3. In this embodiment, on the basis of the foregoing embodiments, the entire solution is embodied and described in a complete manner for easy understanding. This embodiment only describes the hash storage method based on the IP quintuple but does not limit the method.
[0057] First, in this embodiment, the first hash function is set to F, and the second hash function is set to f. The length of the first hash array H is A, and the length of the second hash array h is a. Set the storage unit structure M{link[sip,dip,sport,dport,protocol],prev,next,count} to store IP quintuple information.
[0058] Such as figure 2 As shown, the method includes:
[0059] S210. Find the session according to the IP quintuple.
[0060] S220. Calculate and obtain the hash position H[h] through the function F and the function f.
[0061] Obtain the first unit ID and the second unit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com