Login authentication method, terminal and server
A login authentication and server technology, applied in the computer field, can solve problems such as low operating efficiency, and achieve the effect of saving operating time and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
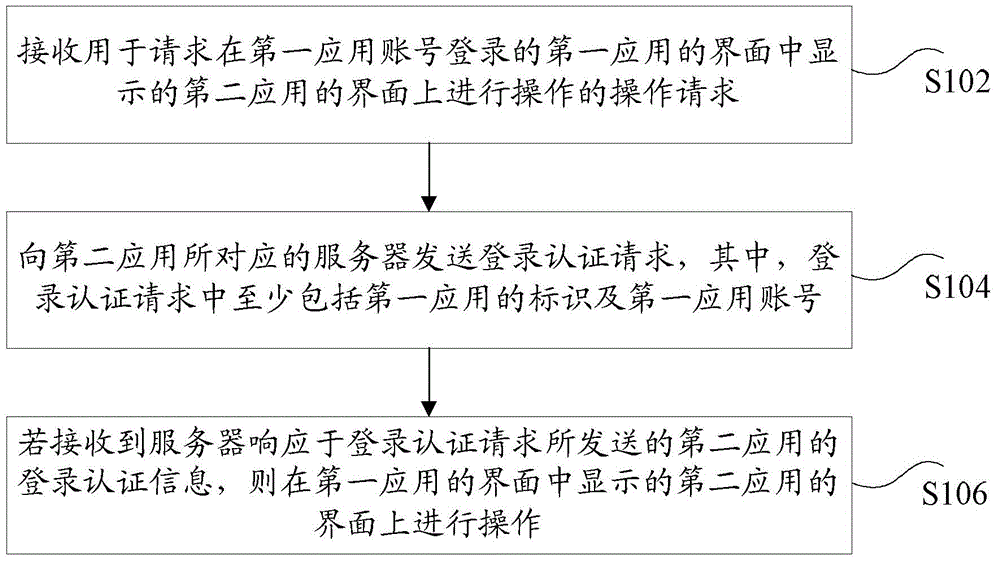
[0027] According to an embodiment of the present invention, a login authentication method is provided, such as figure 1 As shown, the method includes:
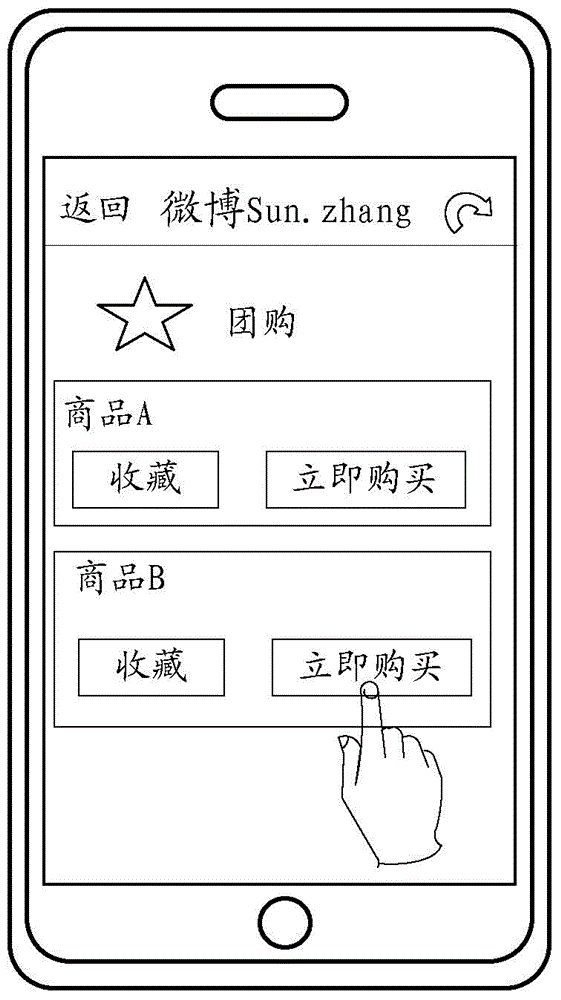
[0028] S102. Receive an operation request for requesting to operate on the interface of the second application displayed on the interface of the first application logged in with the first application account;
[0029] S104. Send a login authentication request to a server corresponding to the second application, where the login authentication request includes at least the identifier of the first application and the first application account;
[0030] S106, if the login authentication information of the second application sent by the server in response to the login authentication request is received, perform operations on the interface of the second application displayed on the interface of the first application.
[0031] Optionally, in this embodiment, the above-mentioned login authentication method can be applied to an authen...
Embodiment 2
[0062] According to an embodiment of the present invention, a login authentication method is also provided, such as Figure 7 As shown, the method includes:
[0063] S702. Receive a login authentication request sent by a terminal running the second application, where the login authentication request includes at least the identifier of the first application and the first application account, where the first application logged in with the first application account on the terminal The interface of the second application is displayed in the interface;
[0064] S704, in response to the login authentication request, search for a second application account for logging in the second application corresponding to the first application identifier and the first application account in the login authentication request;
[0065] S706. If the second application account is found, generate login authentication information of the second application according to the second application account; ...
Embodiment 3
[0101] According to an embodiment of the present invention, a terminal for implementing the above login authentication method is also provided, such as Figure 10 As shown, the terminal includes:
[0102] 1) a receiving unit 1002, configured to receive an operation request for requesting to operate on the interface of the second application displayed on the interface of the first application logged in with the first application account;
[0103] 2) The first sending unit 1004 is configured to send a login authentication request to a server corresponding to the second application, wherein the login authentication request includes at least the identifier of the first application and the first application account;
[0104] 3) The operation unit 1006 is configured to operate on the interface of the second application displayed on the interface of the first application when receiving the login authentication information of the second application sent by the server in response to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com