Encryption method, encryption system, decryption method and decryption system of picture
An encryption method and encryption system technology, applied in the field of encryption system, photo encryption method, decryption method and decryption system, can solve problems such as poor security performance, inability to encrypt in real time, and untargeted encryption targets, etc., to achieve high security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
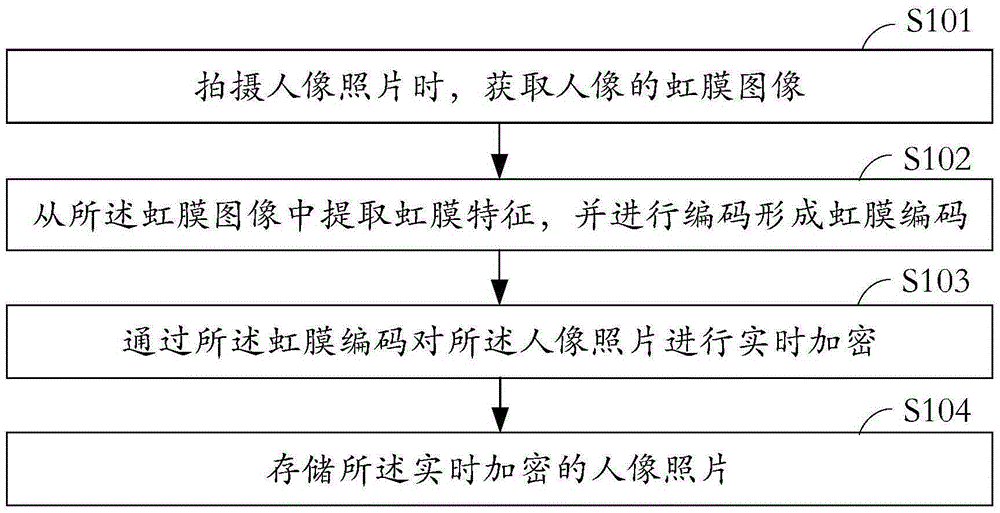
[0041] see figure 1 , which is a schematic flow chart of the photo encryption method provided by the embodiment of the present invention.
[0042] Specifically, the encryption method of the photos includes:
[0043] In step S101, when taking a photo of a portrait, an iris image of the portrait is acquired.
[0044] It can be understood that the acquisition of the iris image specifically includes:
[0045] (1) Obtain an iris image through the camera when taking a portrait photo; or
[0046] (2) After the portrait photo is taken, the iris image is intercepted from the portrait photo.
[0047] In step S102, iris features are extracted from the iris image, and encoded to form an iris code.
[0048] It can be understood that this step specifically includes:
[0049] (1) Position the iris by determining the positions of the inner circle (the boundary between the iris and the pupil), the outer circle (the boundary between the iris and the sclera) and the quadratic curve (the bou...
Embodiment 2
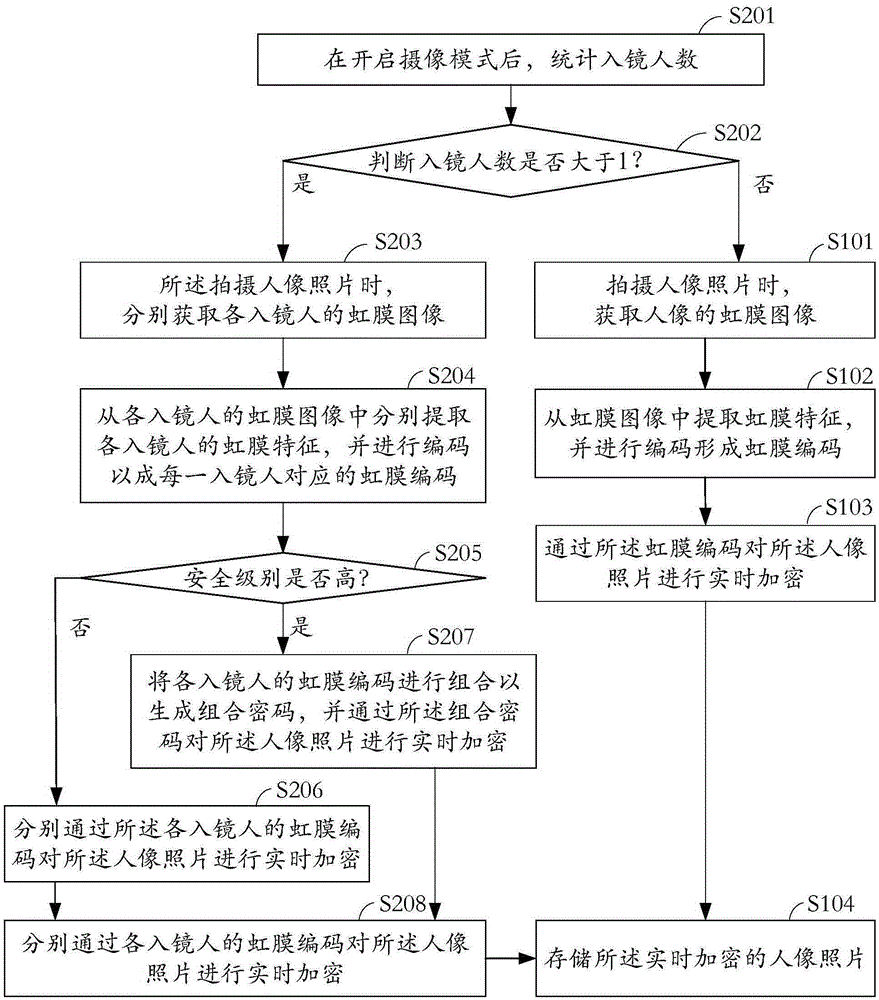
[0057] see figure 2 , which is a schematic flow chart of the photo encryption method provided by the embodiment of the present invention. figure 2 neutralize figure 1 The same steps still start with S1, with figure 1 Different steps start with S2 to show their differences.
[0058] Specifically, the encryption method of the photos includes:
[0059] In step S201, after the camera mode is turned on, count the number of people in the camera.
[0060] The step of counting the number of people in the mirror specifically includes:
[0061] (1) Mark the portrait in the mirror through the display frame;
[0062] (2) receiving a trigger instruction for each display frame; and
[0063] (3) Counting the number of triggering instructions as the number of people entering the camera.
[0064] It can be understood that, by triggering the image of the person entering the mirror through the display frame, it is possible to effectively avoid collecting iris information of irrelevant p...
Embodiment 3
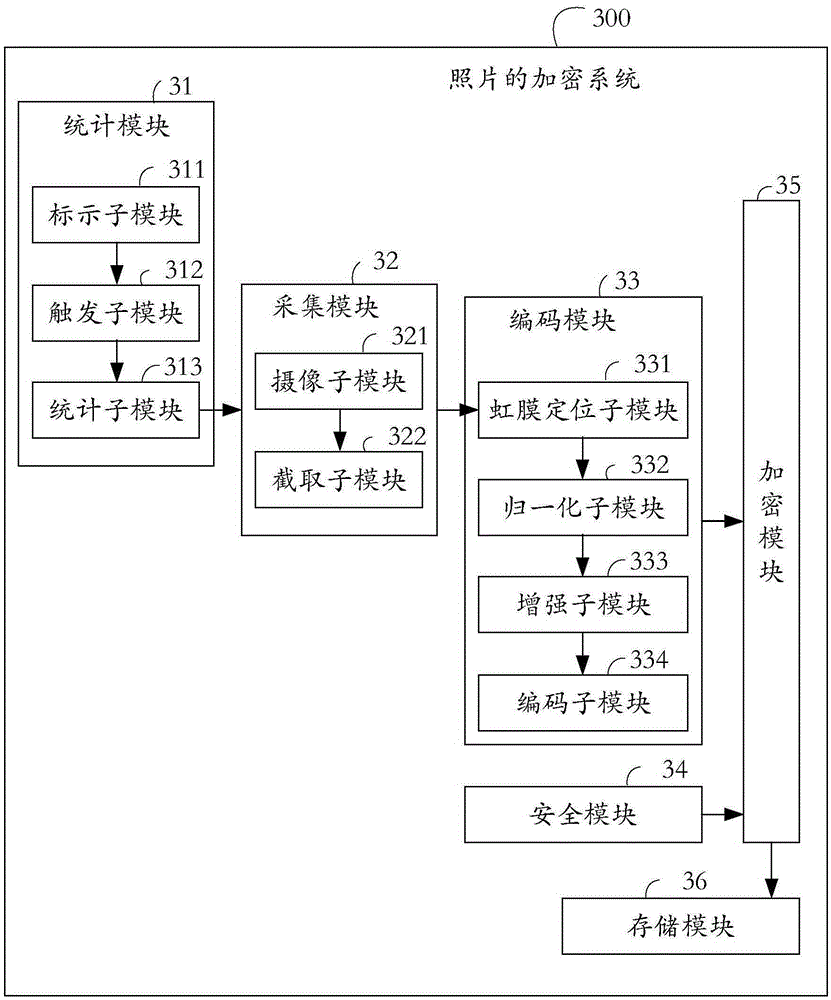
[0086] see image 3 , is a block diagram of the photo encryption system provided by the embodiment of the present invention.
[0087] Specifically, the photo encryption system 300 includes:
[0088] The statistics module 31 is used for counting the number of people in the mirror, and judging whether the number of people in the mirror is greater than 1.
[0089] Specifically, the statistics module 31 includes: a marking submodule 311 , a triggering submodule 312 , and a statistics submodule 313 . Wherein, the marking sub-module 311 is used to mark the portrait of the person in the mirror through the display frame. The trigger sub-module 312 is configured to receive a trigger instruction for each display frame. The counting sub-module 313 is used to count the number of triggering instructions as the number of people entering the camera.
[0090] It can be understood that, by triggering the image of the person entering the mirror through the display frame, it is possible to e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com