A Data Forwarding Method for Assessing the Reputation of Selfish Nodes
A technology of selfish nodes and forwarding methods, applied in the field of opportunistic network data forwarding strategies, can solve problems such as limited node cache, fast energy consumption, and affecting network topology connectivity, achieving low computational complexity and ensuring fairness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with accompanying drawing, the present invention will be further described:
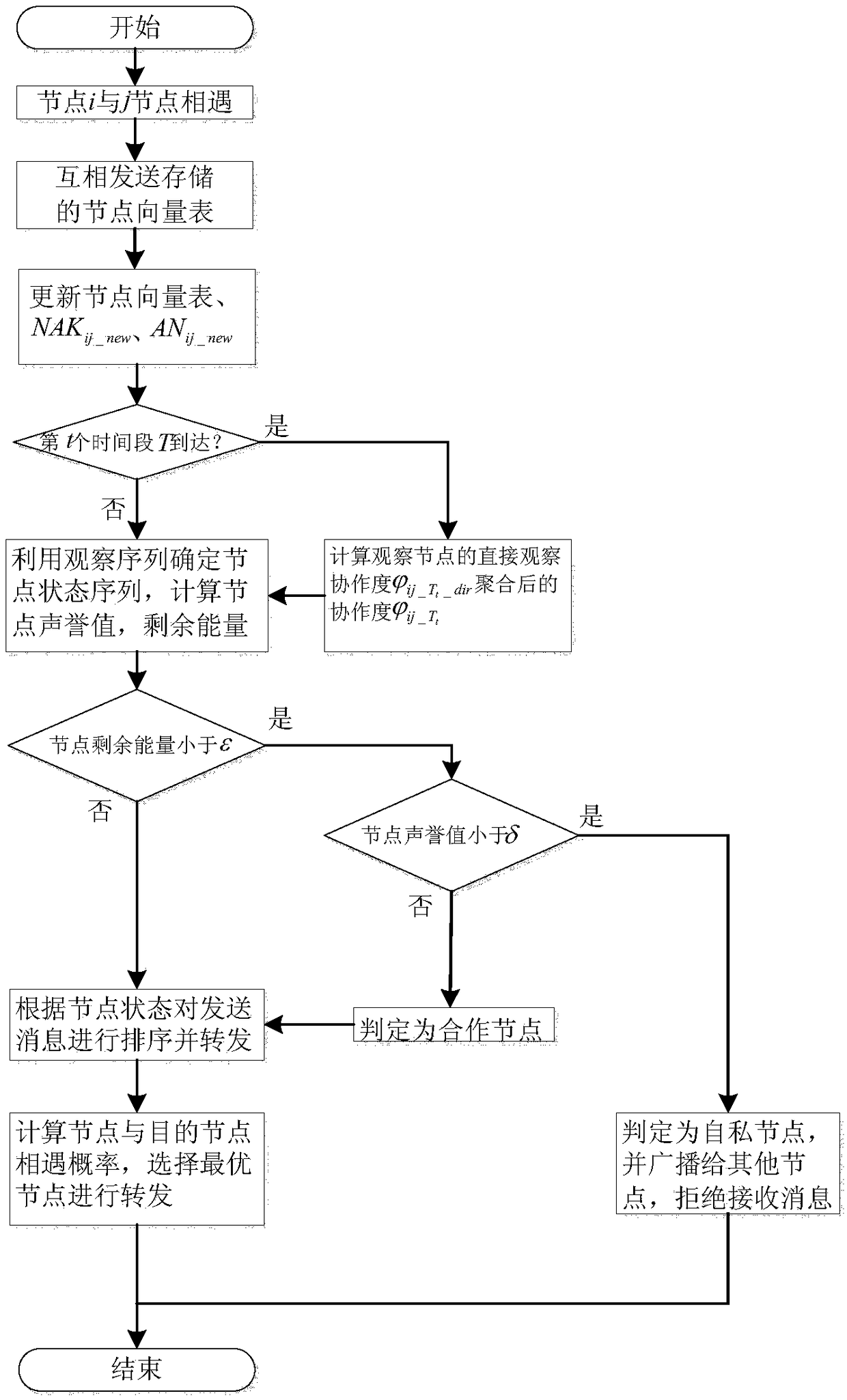
[0026] The present invention establishes a corresponding node vector table through the interaction between nodes, records the cooperation degree and information vector of the node, and updates the cooperation degree of the node according to the number of nodes refusing to receive or receive messages, and utilizes the cooperation degree state observed in each time period T The interval calculates the maximum state probability of the node, and calculates the reputation value of the node. When the remaining energy of the node is the energy threshold, it is judged that if the reputation value of the node is higher than or equal to the threshold, it is a cooperative node, otherwise it is a selfish node.
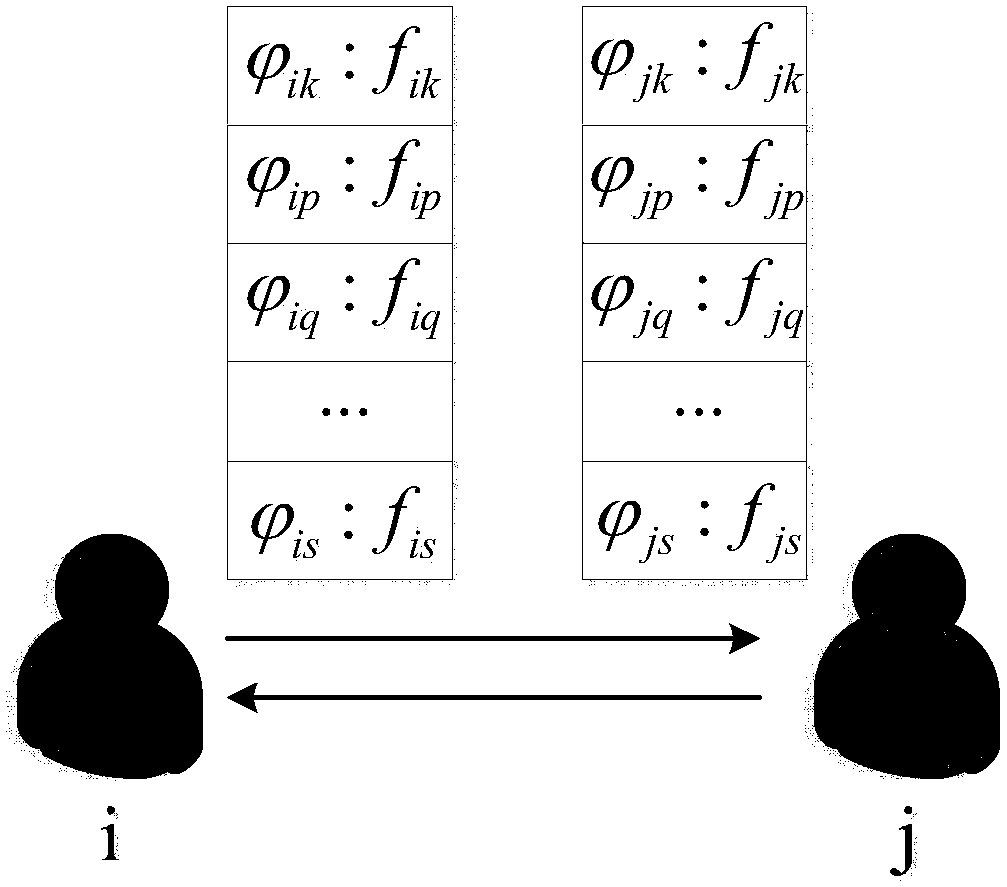
[0027] Such as figure 2 Shown is the flow chart of node encounter in the present invention, that is, when node i and node j meet, the node vector table needs to be exchanged ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com