LTE-Advanced air interface monitor decryption apparatus and method
A technology of air interface and monitoring instrument, which is applied in the direction of safety devices, electrical components, wireless communication, etc., and can solve problems such as inapplicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
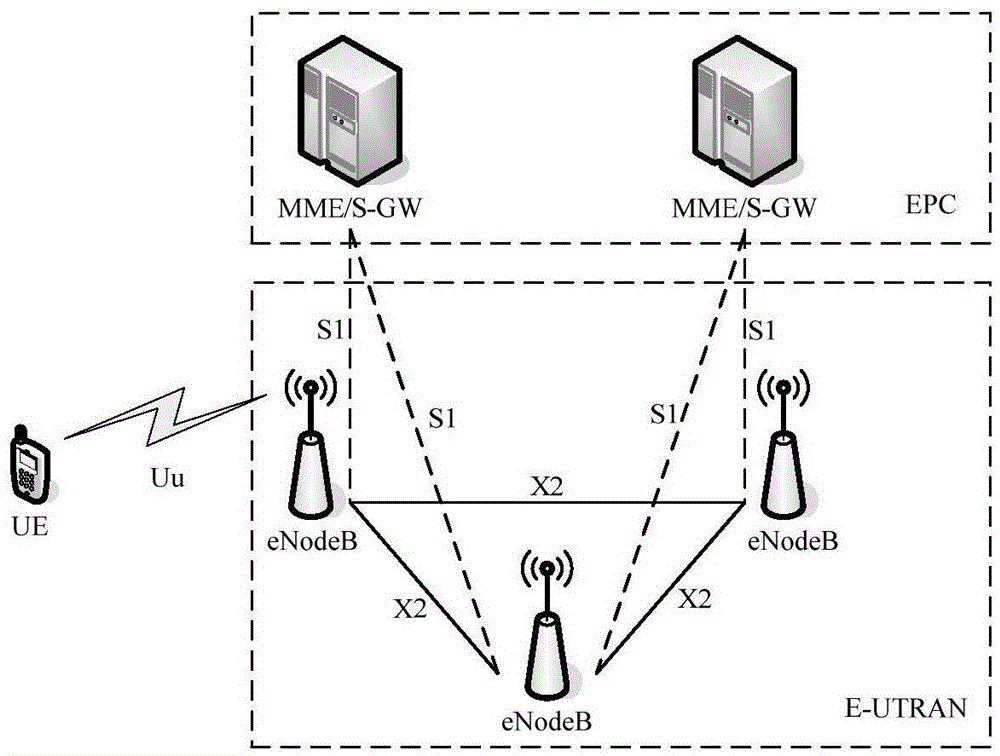
[0047] Such as figure 1 As shown, the LTE system is composed of UE, E-UTRAN, and EPC. Among them, E-UTRAN is composed of multiple eNodeBs, EPC is composed of multiple MME / S-GWs, UE and eNodeB are connected through the Uu interface, and eNodeBs are connected through X2 Interface connection, the eNodeB and MME / S-GW are connected through the S1 interface.
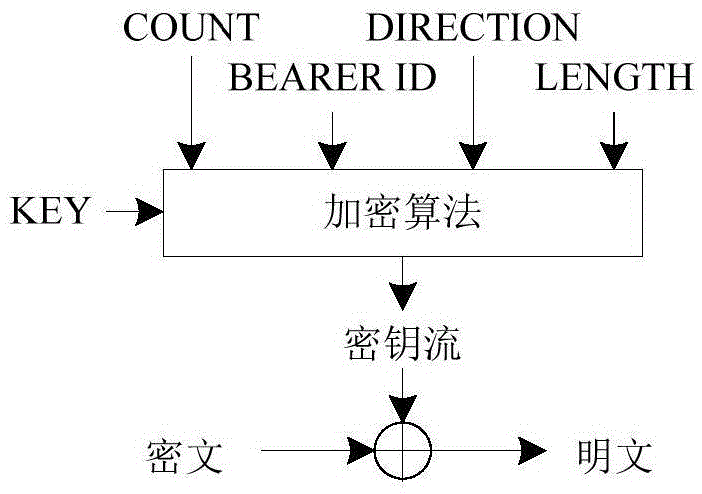
[0048] Such as figure 2 As shown, the input parameters include the decryption key KEY, the counter value COUNT, the bearer identifier BEARERID, the uplink and downlink direction indication DIRECTION, and the length of the key stream LENGTH. The input parameters are calculated by the encryption algorithm to calculate the key stream, and the key stream is XORed with the ciphertext. Then generate plaintext.
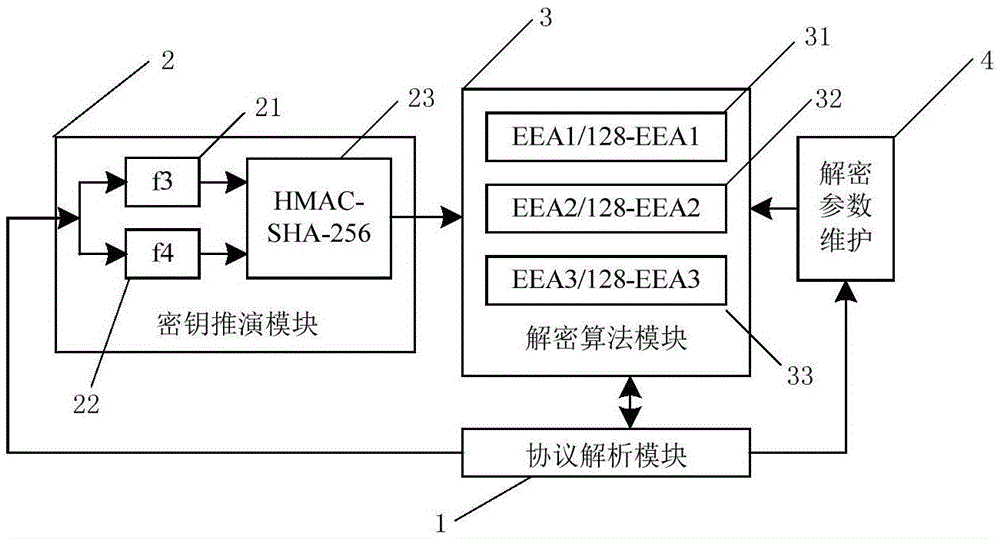
[0049] Such as image 3 As shown, the decryption device of the LTE-Advanced air interface monitor includes a protocol analysis module 1, a key derivation module 2, a decryption algorithm module 3 and a decryption paramet...
Embodiment 2
[0063] On the basis of the foregoing embodiments, the present invention also mentions a decryption method of an LTE-Advanced air interface monitor (such as Figure 4 Shown), the signaling on the air interface is decrypted, wherein, proceed as follows:
[0064] Step 1: Analyze the RRC connection establishment message through the protocol analysis module, extract the parameter rb-Identity carried therein, parameter ASBEARERID=rb-Identity-1;
[0065] Step 2: Analyze the authentication request message through the protocol analysis module, and extract the parameter RAND carried in it;
[0066] Step 3: Through the key derivation module and using the known root key K and RAND, calculate CK and IK; use CK and IK to calculate KASME; use KASME to calculate KNASenc and KeNB; use KeNB to calculate KUPenc and KRRCenc; when decrypting NAS messages, parameter NASKEY=KNASenc; when decrypting ASRRC messages, parameter ASKEY=KRRCenc; when decrypting AS user data, parameter ASKEY=KUPenc;
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com