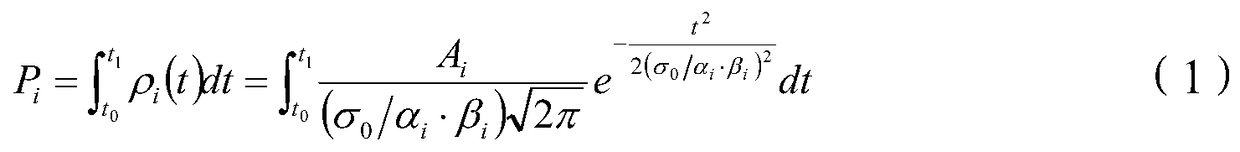An information security early warning method and device
An information security and information network technology, applied in the field of information security early warning methods and devices, can solve problems such as inability to perform accurate early warning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] It should be noted that, in this method, a meta-model can be established in advance, and the meta-model is set with an information asset type attribute, which corresponds to at least the following asset types: operating system, middleware (carrier server), database, application. Wherein, the operating system may include a windows operating system, a Linux operating system, etc.; the application may include system applications, various third-party applications, and the like.
[0055] When conducting information security assessment for any information network system, according to the types of information assets in the preset meta-model, each information asset can be counted and an information asset library can be established; it should be noted that, in the preset meta-model The types of information assets can be added or deleted, so each information asset in the information asset database obtained by statistics can only be related to the type of information assets retaine...
Embodiment 2
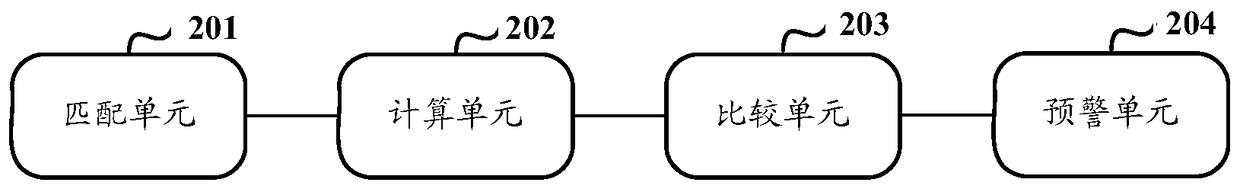
[0091] like figure 2 As shown, it is an information security early warning device provided in Embodiment 2 of the present invention, and the early warning device includes the following units:
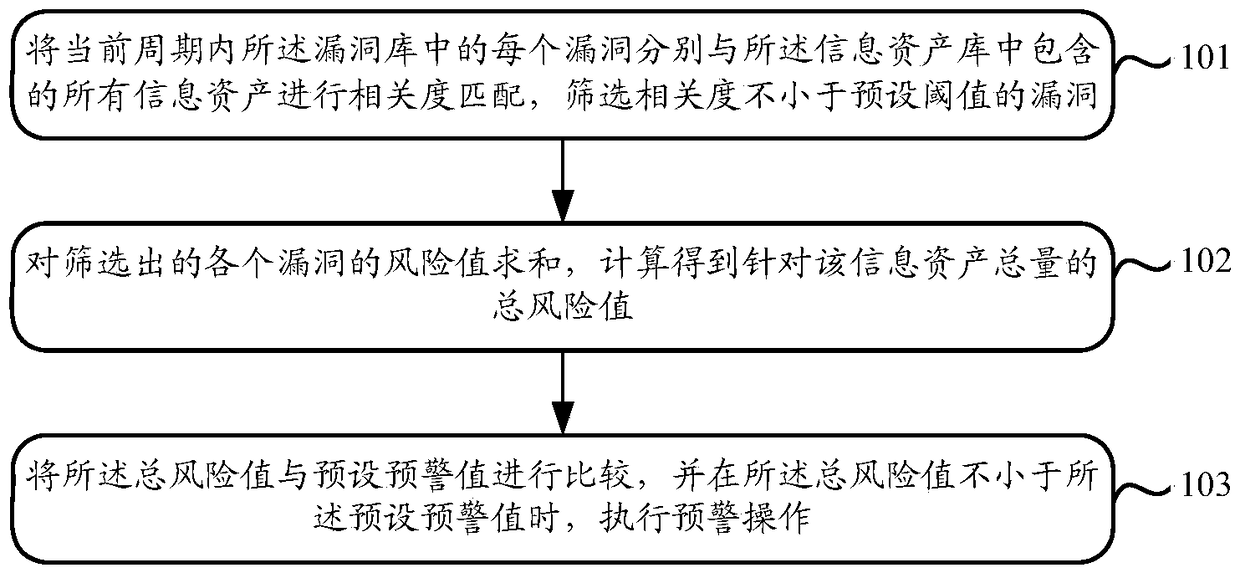
[0092] The matching unit 201 is configured to perform correlation matching between each vulnerability in the vulnerability database in the current period and all information assets contained in the information asset database, and screen vulnerabilities whose correlation degree is not less than a preset threshold.
[0093] Preferably, the matching unit 201 is specifically used for:
[0094] Count each information asset contained in the current information asset library, and normalize to obtain the sum of the unit vectors of each information asset: in, represents the unit vector of the jth information asset;
[0095] Count the information assets threatened by the i-th vulnerability in the current vulnerability database, and normalize to obtain the sum of the unit vectors of each inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com