Method and device for determining an attack surface of a terminal
A terminal and equipment technology, applied in the field of Internet security, can solve problems such as economic loss, strengthening mail monitoring, and incompatible with the enterprise's personalized network environment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
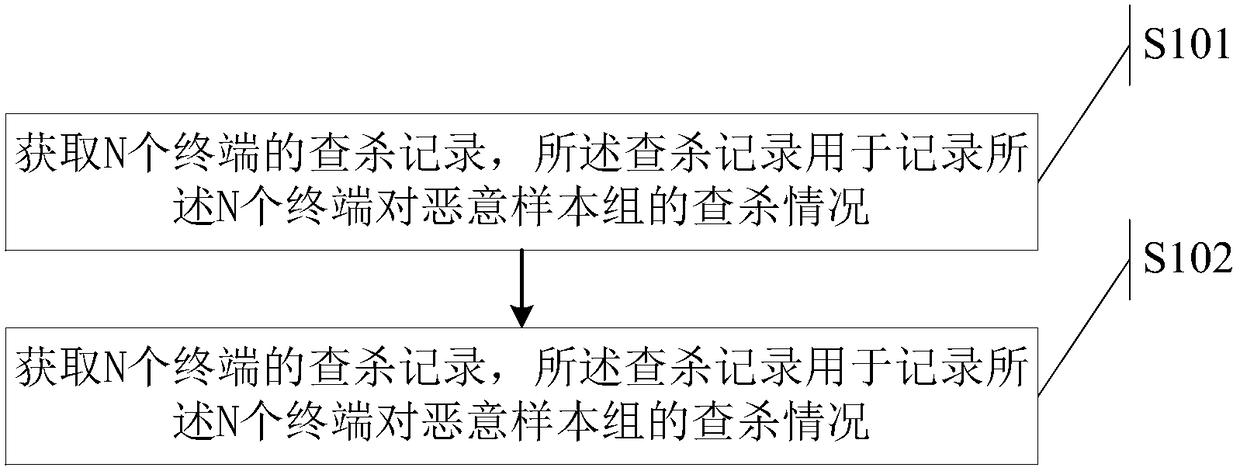
[0037] The general idea of the technical solution in the embodiment of the application is as follows:
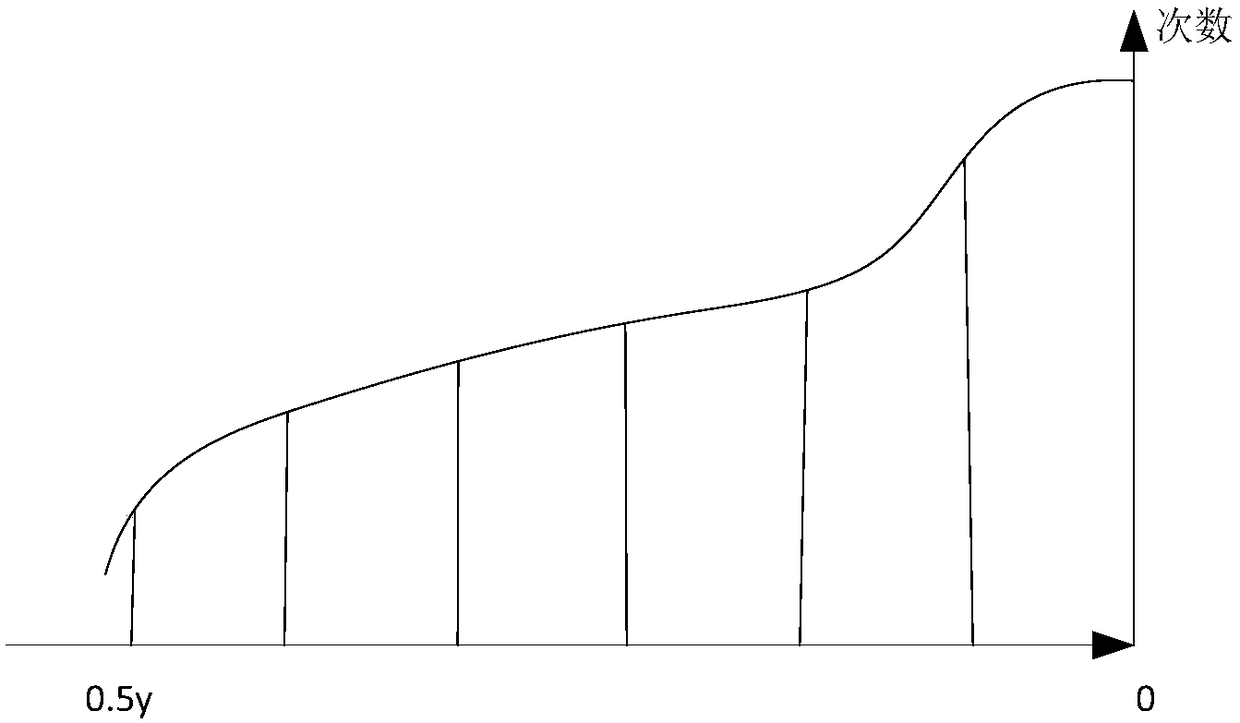
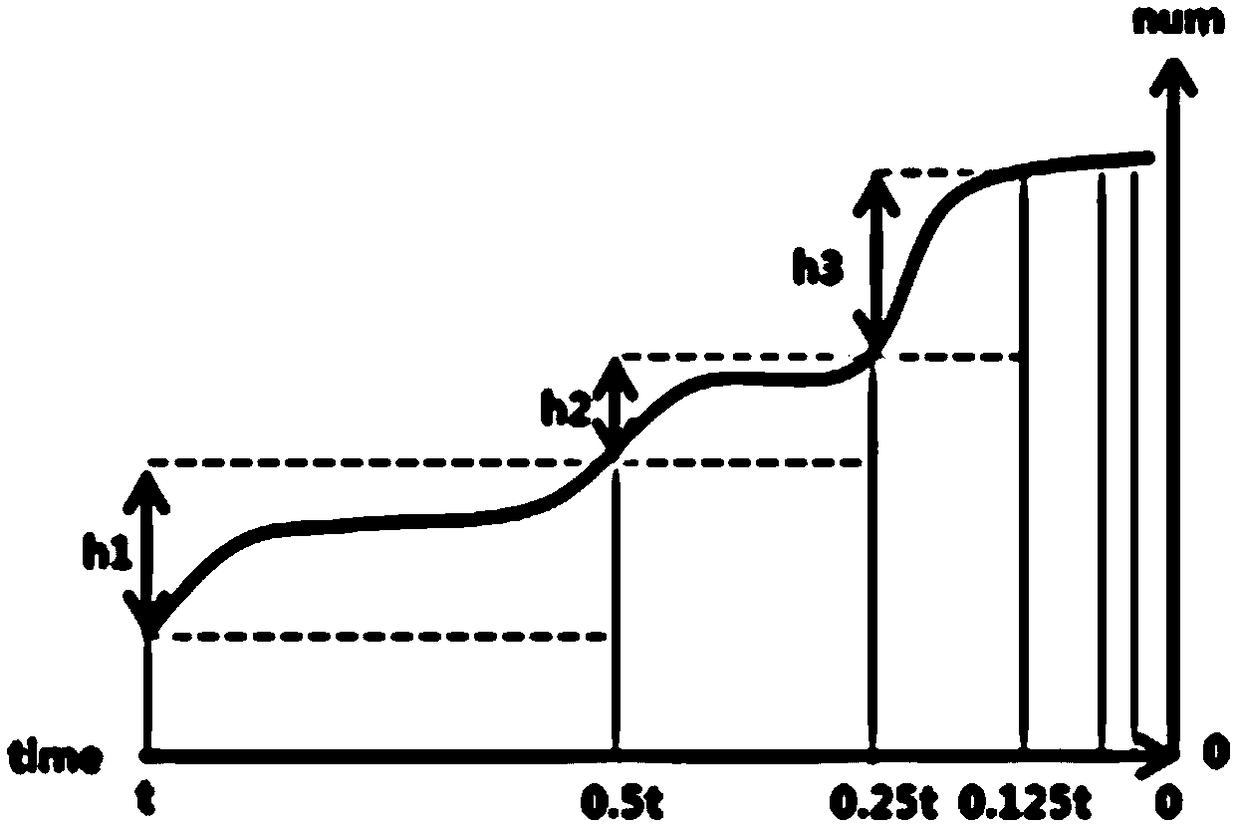
[0038] Obtain the killing records of N terminals, the killing records are used to record the killing of the malicious sample group by the N terminals, wherein, N is a positive integer; then according to the killing records, determine the N The attack surface of each terminal attacked by the malicious sample group, where the attack surface is used to characterize the threat degree of the malicious sample group to the terminal. That is, starting from the direct result of malicious sample attacks, that is, the killing records, determine the threat level of each terminal in the enterprise that is easily attacked by malicious sample groups, thereby exposing the weak terminals in the enterprise that are most likely to be attacked by malicious samples. The terminal adopts direct defense measures, which is conducive to formulating more targeted defense measures against malicious s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com