Power terminal vulnerability attack detection method based on message features
A power terminal and attack detection technology, applied in neural learning methods, electrical components, biological neural network models, etc., can solve problems such as concealment, latent and high destructiveness, and achieve convenient defense measures, recognition accuracy and reliability Improve the effect of accurate detection and recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The following are specific embodiments of the present invention and in conjunction with the accompanying drawings, the technical solutions of the present invention are further described, but the present invention is not limited to these embodiments.
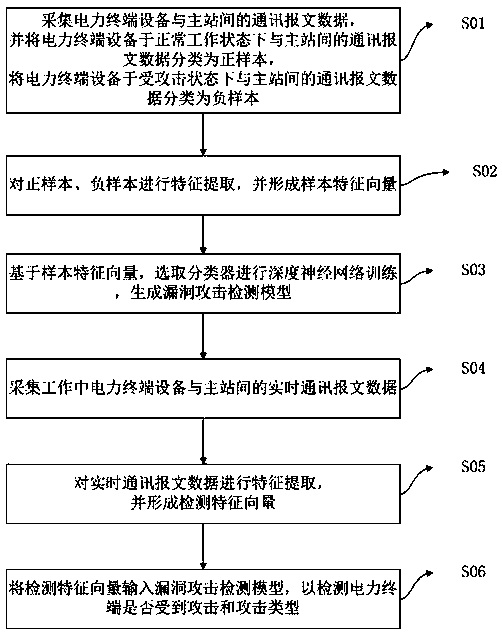
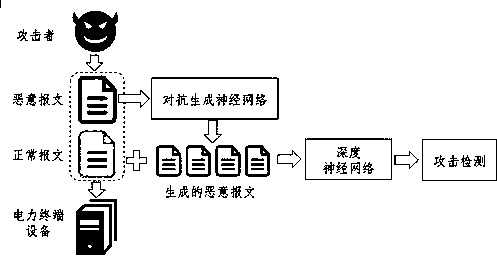
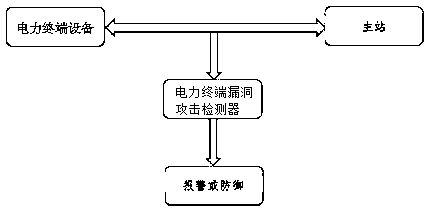
[0053] Such as Figure 1-3 According to the present invention, a method for detecting vulnerability attacks of electric power terminals based on message characteristics includes:
[0054] Step S01, collect the communication message data between the power terminal equipment and the main station, and classify the communication message data between the power terminal equipment and the main station under normal working conditions as positive samples, and classify the power terminal equipment under attack The communication message data with the master station is classified as a negative sample;
[0055] Step S02, performing feature extraction on positive samples and negative samples, and forming sample feature vectors;
[005...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com