Encryption Algorithm Realization Method and System
A technology of encryption algorithm and implementation method, which is applied in the direction of transmission system, electrical components, etc., and can solve the problems that encryption technology is easy to be cracked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0046] figure 1 It is a schematic flowchart of an encryption algorithm implementation method provided in the first embodiment of the present invention. This method is suitable for scenarios where information needs to be transmitted securely, and can be executed by an encryption algorithm implementation system, wherein the system can be implemented by software and / or hardware , and generally can be integrated in the terminal. Such as figure 1 As shown, the method includes:
[0047] Step 110, the first terminal generates a first key pair according to a first set rule, wherein the first key pair is composed of a first public key and a first private key;
[0048] In this embodiment, the first terminal specifically refers to a device capable of sending and receiving data, and running related software such as key generation, encryption, and decryption (for example, a key generator, etc.). Typical examples can be: computers, smartphones and other terminals.
[0049] In this embod...
no. 2 example
[0076] figure 2 It is a schematic flowchart of an encryption algorithm implementation method provided by the second embodiment of the present invention. This embodiment is optimized on the basis of the above-mentioned embodiments. In this embodiment, the first setting rule is optimized as: a rule generated according to a first algorithm defined by a user or a rule generated according to a second algorithm randomly selected by a program. rule.
[0077] Correspondingly, the method in this embodiment specifically includes:
[0078] Step 210, the first terminal generates a first key pair according to the rules generated by the first algorithm defined by the user or according to the rules generated by the second algorithm randomly selected by the program, wherein the first key pair is composed of the first public key and The composition of the first private key;
[0079] In this embodiment, the first algorithm defined by the user specifically refers to at least two encryption a...
no. 3 example
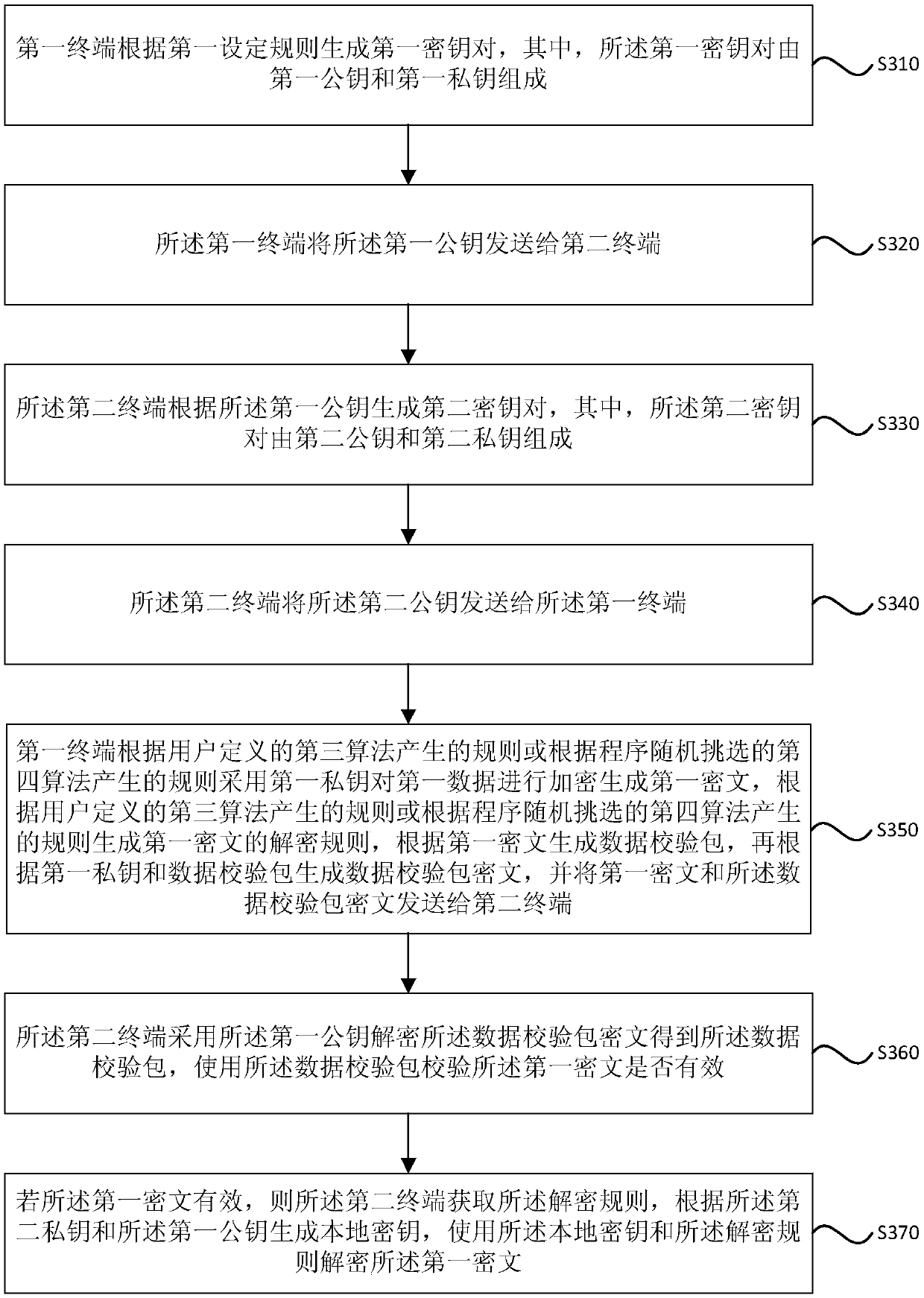
[0095] image 3 It is a schematic flowchart of an encryption algorithm implementation method provided by the third embodiment of the present invention. This embodiment is optimized on the basis of the above embodiments. In this embodiment, the second setting rule is optimized as: a rule generated according to a third algorithm defined by the user or a rule generated according to a fourth algorithm randomly selected by a program. rule.
[0096] Correspondingly, the method in this embodiment specifically includes:
[0097] Step 310, the first terminal generates a first key pair according to a first set rule, wherein the first key pair consists of a first public key and a first private key;
[0098] Step 320, the first terminal sends the first public key to the second terminal;
[0099] Step 330, the second terminal generates a second key pair according to the first public key, wherein the second key pair consists of a second public key and a second private key;
[0100] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com