Model encryption and decryption method and device based on asymmetric interval insertion of encryption characters
An asymmetric and character-based technology, applied in encryption devices with shift registers/memory, secure communication devices, computer security devices, etc., can solve problems such as easy cracking of model encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] According to the present embodiment, there is provided a method of inserting interval based on asymmetric encryption model character decryption embodiment, it is noted that the steps illustrated in the flowchart drawings can be executable instructions, such as a set of computer a computer system execute, and although in the flowchart shown in a logical order, but in some cases, may be different from the steps in the order shown or described herein.
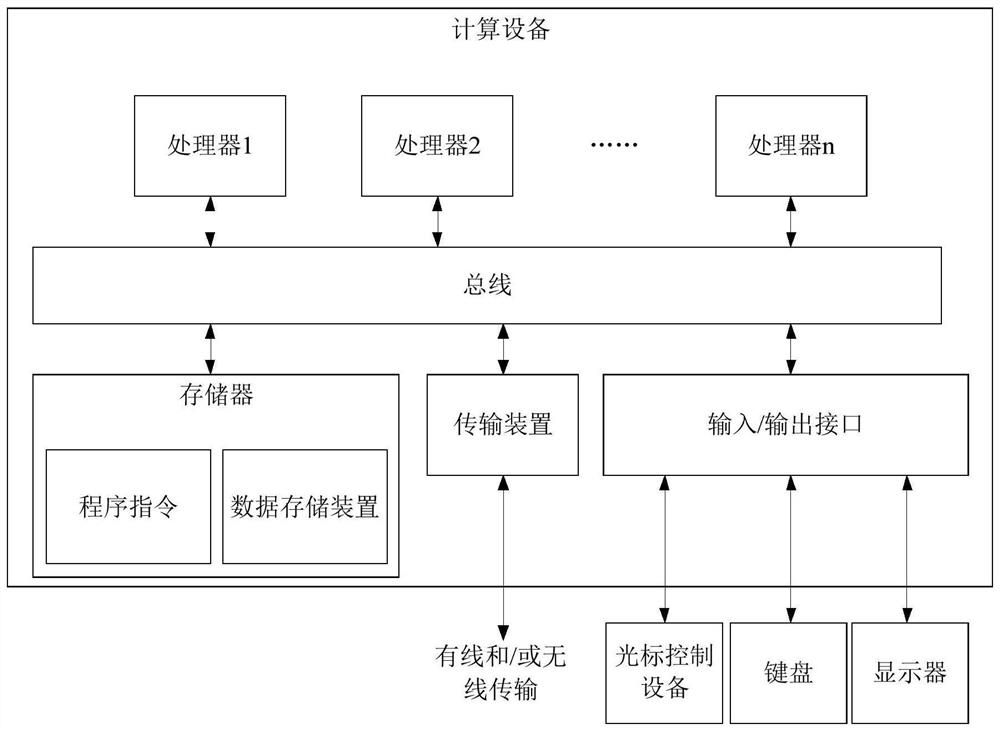
[0066] Embodiment of the method provided in this embodiment may be performed in the embodiment the mobile terminal, computer terminal, a server or similar computing device. figure 1 Shows a block diagram of a hardware configuration for implementing a method of computing device model encrypted decryption methods based on asymmetric character insertion interval. like figure 1 , The computing device may include one or more processors (processors may include, without limitation, a microprocessor or a programmable logic device FPGA ...
Embodiment 2
[0107] Figure 5 A model encryption device 500 based on an asymmetric interval inserted into the encrypted character according to the first aspect of the present embodiment is shown, and the apparatus 500 corresponds to the method according to the first aspect of the first embodiment. refer to Figure 5 As shown, the device 500 includes:
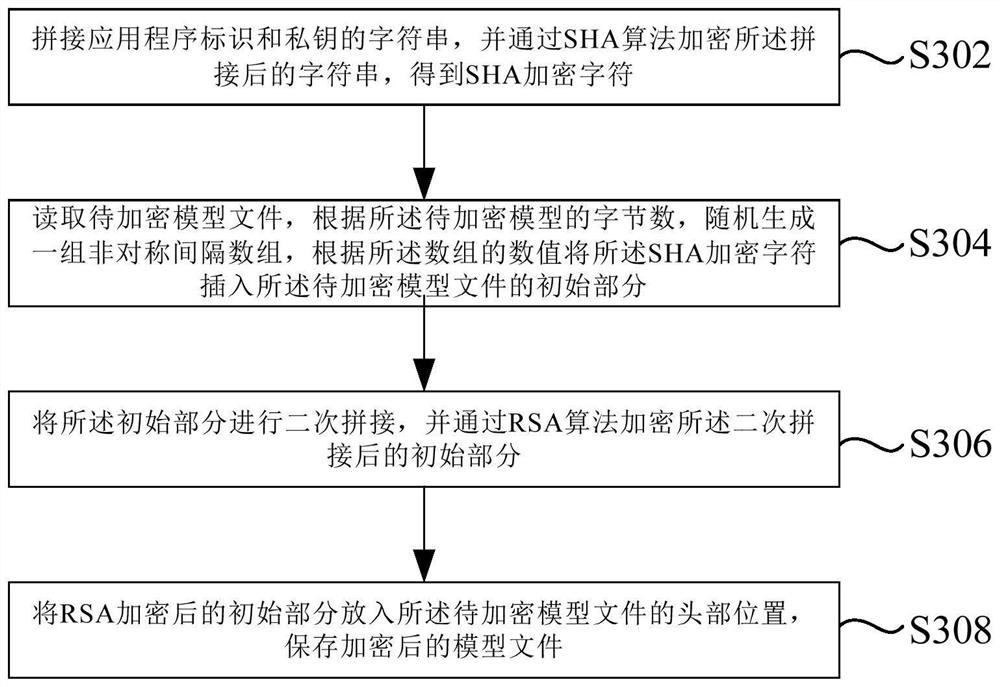
[0108] SHA encryption module 510, a string for splicing the application identifier and private key, and encrypts the spliced string after the SHA algorithm to obtain SHA encryption characters;
[0109] The array generating module 520 is configured to read the model file to be encrypted. According to the number of bytes to be encrypted, randomly generate a set of asymmetric interval number, insert the SHA encryption character inserting the SHA encrypted character into the desired. The initial part of the encryption model file;
[0110] The RSA encryption module 530 is configured to twice the initial portion and encrypt the initial portion of the...
Embodiment 3
[0121] Figure 7 A model encryption apparatus 700 based on an asymmetric interval is inserted into the encrypted character according to the first aspect of the present embodiment is shown, and the apparatus 700 corresponds to the method described in accordance with the first aspect of the first embodiment. refer to Figure 7 As shown, the device 700 includes:
[0122] First processor 710;
[0123] The first memory 720 is connected to the first processor for providing an instruction for processing the following processing step for the first processor:
[0124] Stitching the application identifies the string of the private key, and encrypts the spliced string after the SHA algorithm to get the SHA encryption character;
[0125] Read the model file to be encrypted, based on the number of bytes to be encrypted, randomly generate a set of asymmetric interval, insert the SHA encryption character into the initial portion of the model file to be encrypted according to the value of the ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com