A Method of Security Strengthening Router
A router and security technology, applied in the field of wireless Internet security applications, can solve problems such as attacks and difficult protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
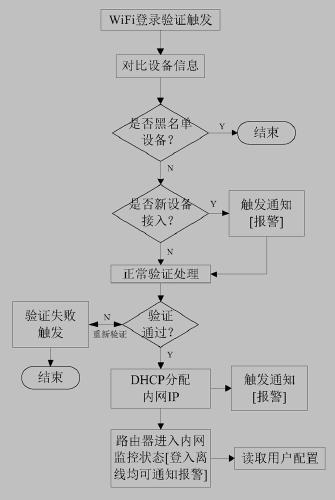
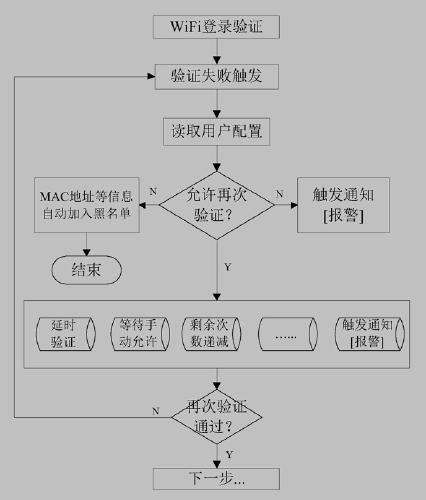
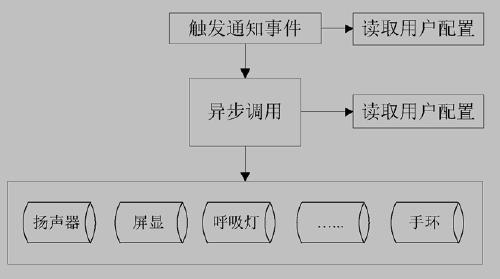
[0026] as above figure 1 As shown, when a new WiFi login verification request arrives, the router judges based on the MAC address of the client device, whether the device is listed in the router's blacklist? If yes, discard the verification request; if no, continue to judge whether it has logged in to the router before, if not, it is the first request for a new client to log in to the network, triggering a notification [alarm] event (*Note 1: see image 3 Explanation, the same below); if it is a client that has logged in before and requests to log in again, the trigger notification [alarm] event is omitted, and the verification process is directly started.
[0027] If the WiFi password verification is passed once, the IP address can be assigned by the router DHCP (in the case of dynamic IP allocation), and according to the user configuration in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com