Invisible address implementation method capable of being supervised by third party
An implementation method and address technology, which is applied to user identity/authority verification and key distribution, and can solve problems such as impracticality, security risks, and cumbersome proofs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
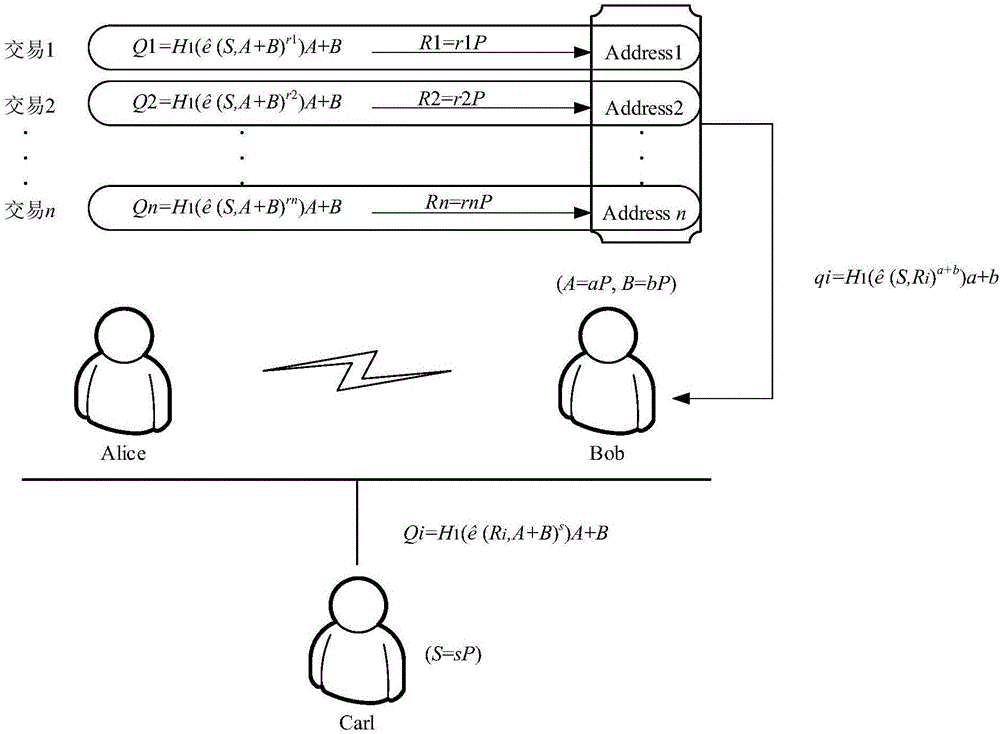
[0014] The core of the present invention is the one-time address generation technology. Since the user's address is identified on the blockchain, and the address is generated by the public key, it is the invention to generate the one-time public key corresponding to a certain transaction for the user. core.
[0015] Specifically, the present invention:
[0016] (1) Utilizing the nature of bilinear pairing, the design not only allows third-party regulatory agencies to perform supervision and audit functions with only one key, but also ensures that the user's address is invisible to third-party observers. (Indirectly protect the privacy of users).
[0017] (2) Based on the characteristics of additive homomorphism in the cyclic group, the transaction receiver can recover the private key corresponding to the stealth address by using the random intermediate value contained in the transaction, the private key in his possession, and the public key of the supervisor to perform algebraic ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com