Link camouflage system and method
A technology for linking information and requesting parties, applied in transmission systems, electrical components, etc., can solve problems such as system drag and failure to meet expectations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
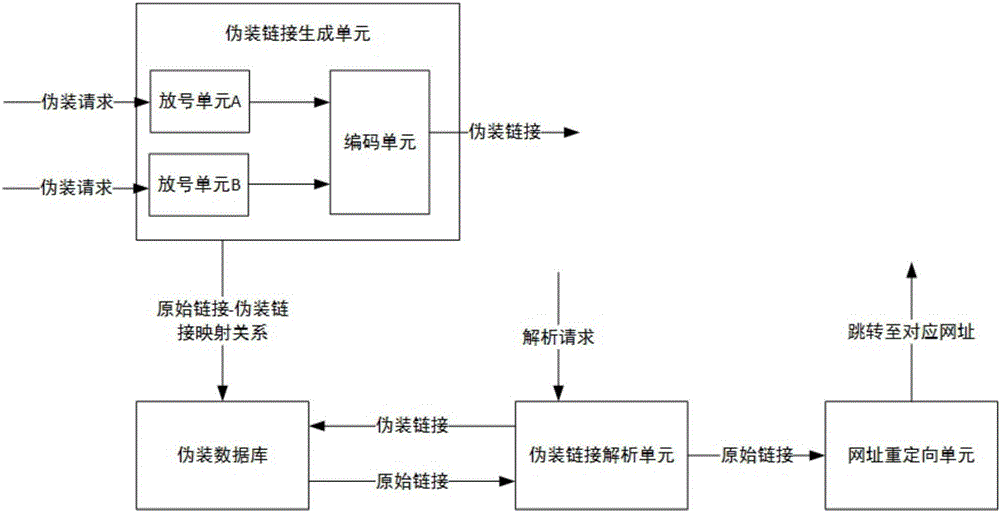
[0038] like figure 1 As shown, a link camouflage system includes a camouflage link generation unit, a camouflage database, a camouflage link parsing unit and a URL redirection unit. The fake link generating unit is used to convert the original link in the fake request into a corresponding fake link, store the mapping relationship between the original link and the fake link in the fake database and return the fake link to the requester.
[0039]The masquerading link generating unit receives and generates a request corresponding to the masquerading link sent by the requesting end. Specifically, the masquerading link generation unit includes a number distribution unit and a coding unit. There are two number allocation units, and each number allocation unit also includes a calculation unit. The initial number value of the number allocation unit A is 0, and the initial number value of the number allocation unit B is 1. For each camouflage link generation request, the number allo...
Embodiment 2
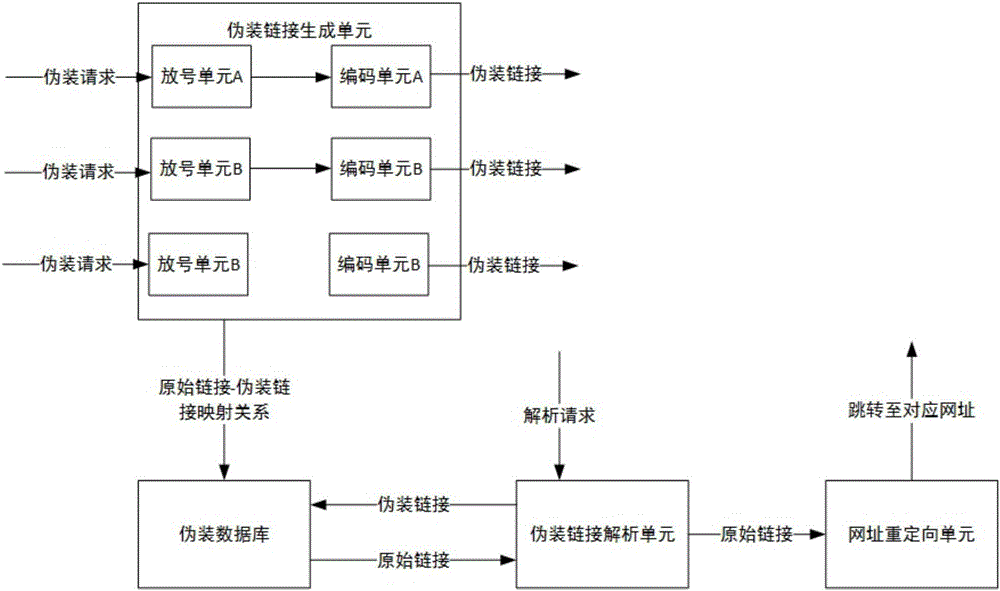
[0061] like image 3 As shown, a link camouflage system includes a camouflage link generation unit, a camouflage database, a camouflage link parsing unit and a URL redirection unit. The fake link generating unit is used to convert the original link in the fake request into a corresponding fake link, store the mapping relationship between the original link and the fake link in the fake database and return the fake link to the requester.
[0062] The masquerading link generating unit receives and generates a request corresponding to the masquerading link sent by the requesting end. Specifically, the masquerading link generation unit includes three number allocation units and encoding units corresponding to the three number allocation units respectively. There are three number allocation units, and each number allocation unit also includes a calculation unit. The initial number value of number allocation unit A is 0, the initial number value of number allocation unit B is 1, an...
Embodiment 3
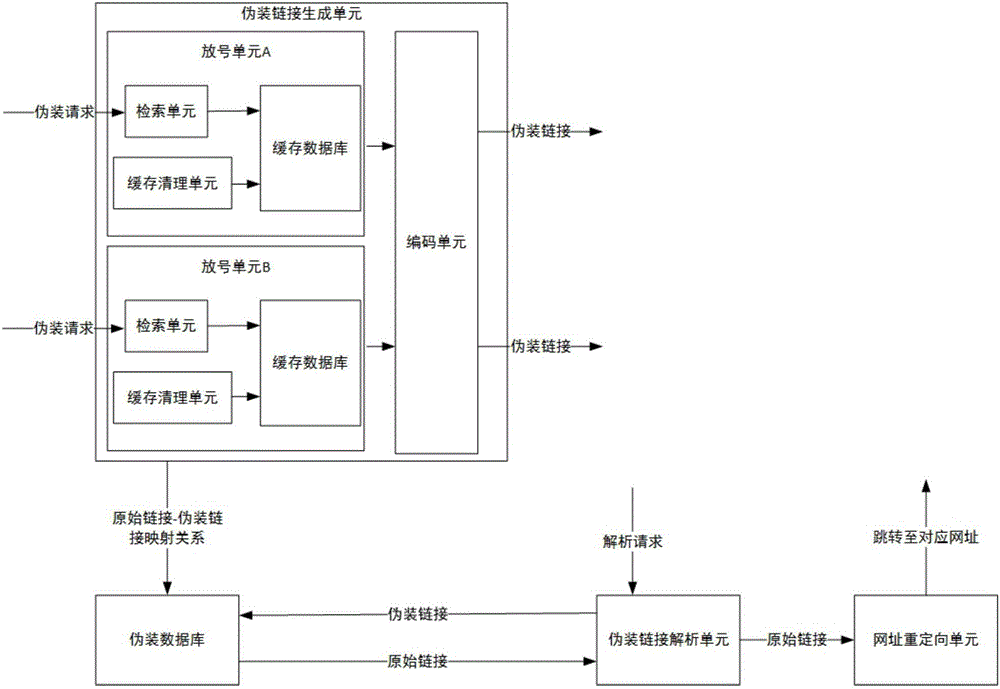
[0084] like Figure 5 , a link camouflage system, comprising a camouflage link generation unit, a camouflage database, a camouflage link parsing unit and a URL redirection unit. The fake link generating unit is used to convert the original link in the fake request into a corresponding fake link, store the mapping relationship between the original link and the fake link in the fake database and return the fake link to the requester.
[0085] The masquerading link generating unit receives and generates a request corresponding to the masquerading link sent by the requesting end. Specifically, the fake link generation unit includes a number allocation unit, an encoding unit, a retrieval unit, a cache cleaning unit, and a cache database. There are two number allocation units, and each number allocation unit also includes a calculation unit. The initial number value of the number allocation unit A is 0, and the initial number value of the number allocation unit B is 1. For each c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com