Picture uploading safety detection method and device
A security detection and image uploading technology, applied in the field of network security, can solve problems such as malicious attacks, achieve the effect of improving security, realizing security detection and processing, and reducing the probability of malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
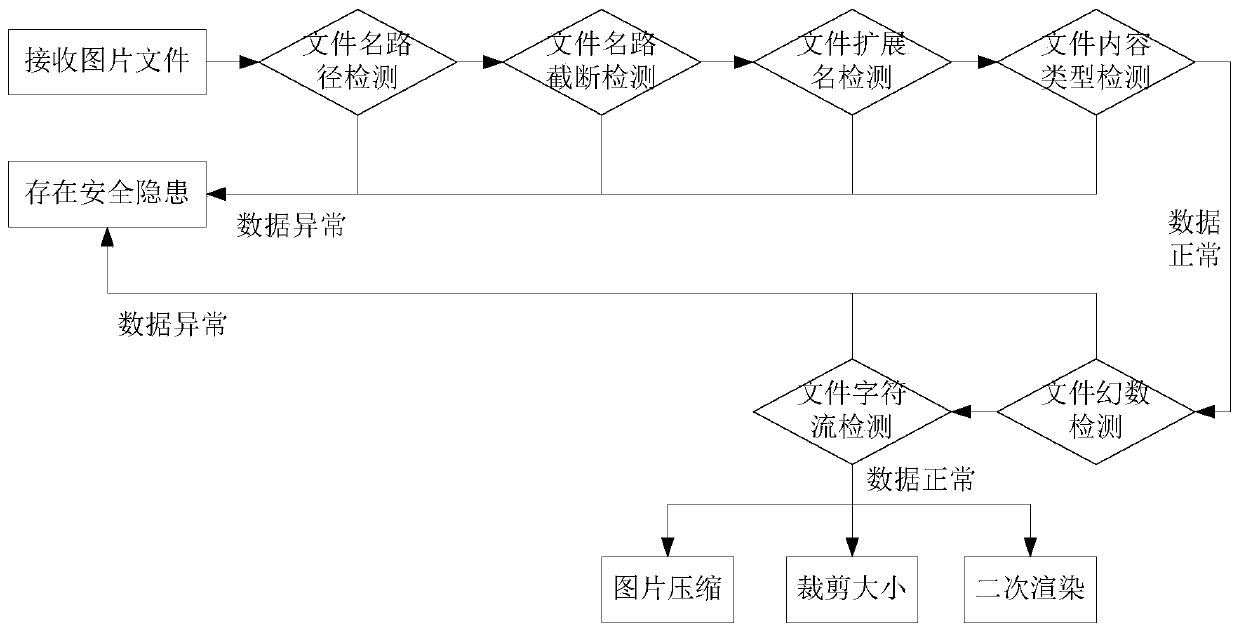
[0025] The security detection method of picture upload of the present invention, such as figure 1 As shown, it comprises the following steps: Step 1. Receive the uploaded picture file, detect the parameters of the picture file, if the parameters of the picture file are abnormal, then determine that there is a security risk in the picture file; Step 2. If the picture file The parameters of the file are normal, and the character stream of the picture file is obtained, and the similarity matching is performed between the character stream and the malicious code in the malicious code library. If the similarity is greater than a preset value, it is determined that the picture file has a security risk.
[0026] Specifically, the image file received and uploaded is generally the image file uploaded by the server receiving the client, and the image file includes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com