Matrix permission implementation method based on RIM real identity management system
A technology of real identity and management system, applied in transmission systems, data processing applications, instruments, etc., can solve problems such as difficult work synchronization, reduced work efficiency, and difficult work management software collaborative services, achieve freedom of authority, and improve efficiency. , the effect of reducing the probability of error
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
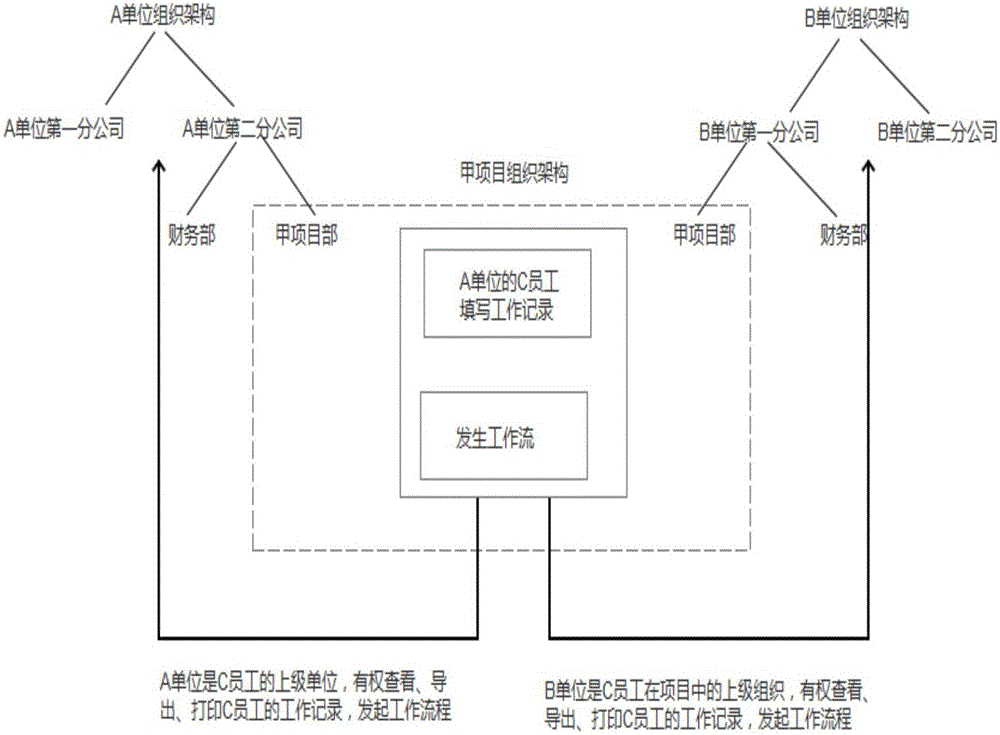
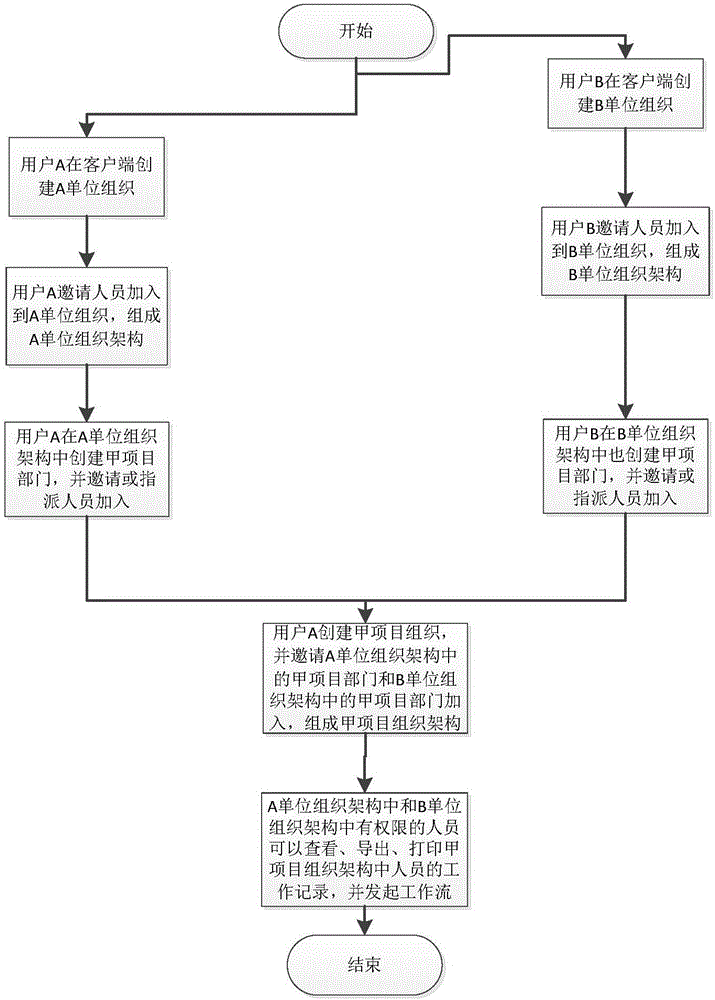
[0026] Embodiment 1, in the current society, there will definitely be intersections between companies, that is, the same job between two companies, so as to improve the efficiency of the work. The present invention provides a real identity based on RIM The implementation method of the matrix authority of the management system is mainly completed by attaching to the RIM identity management system. What is the RIM identity management system? In detail, the RIM identity management system also includes the RIM identity management method using the system, details as follows:
[0027] A RIM identity management method is applied to an identity management system, and the method specifically includes the following steps:
[0028] 1) Identity entry
[0029] A. First, establish a storage module and related identification and entry modules;
[0030] B. Enter the identity card number of the person to be managed (user) in the ID card identification input module, and the ID card identifica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com