Method and device for detecting malicious code
A malicious code and detection module technology, applied in the field of malicious code detection, can solve problems such as the huge variety of plug-in programs and the inability of protection software to completely prevent plug-in program intrusion, and achieve the effect of accurate judgment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Specific embodiments of the present disclosure will be described in detail below. It should be noted that the embodiments described here are for illustration only, and are not intended to limit the present disclosure.
[0020] The following examples are used to illustrate the present disclosure, but not to limit the scope of the present disclosure.
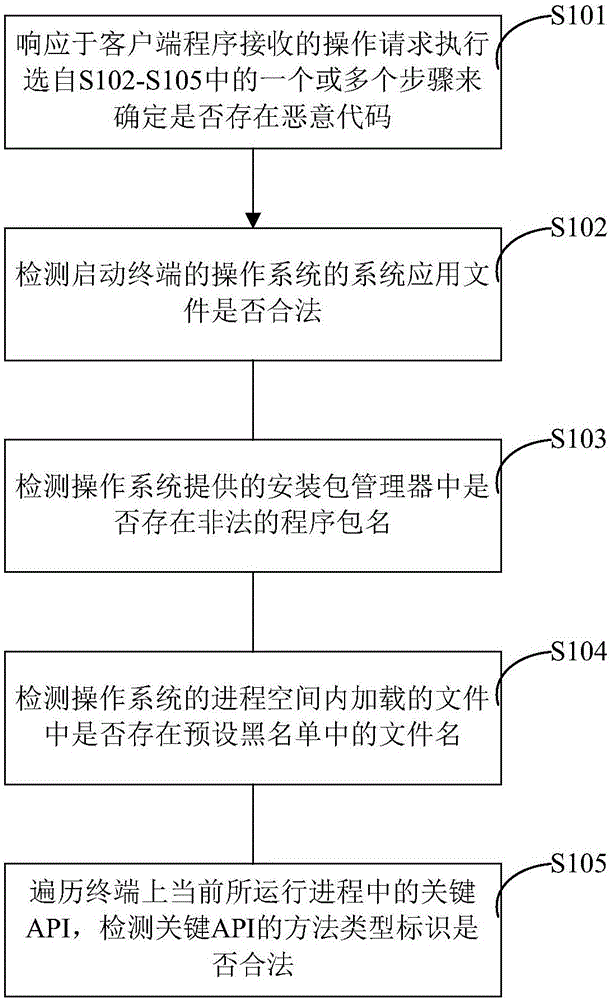
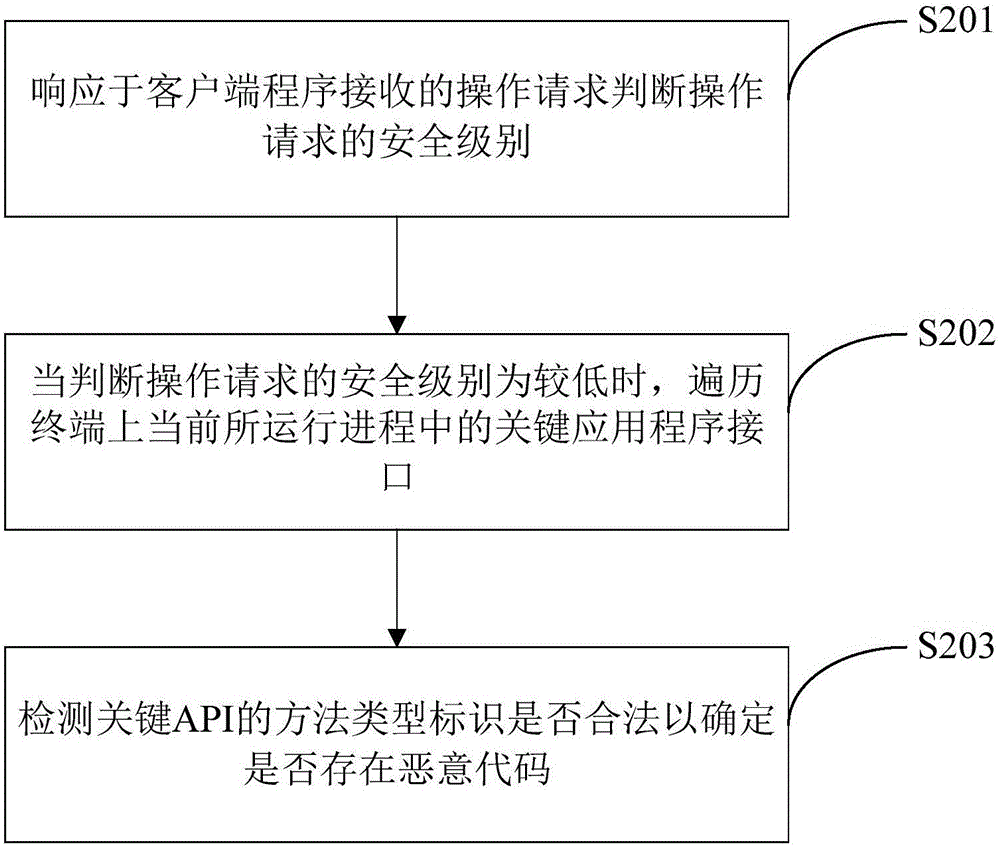
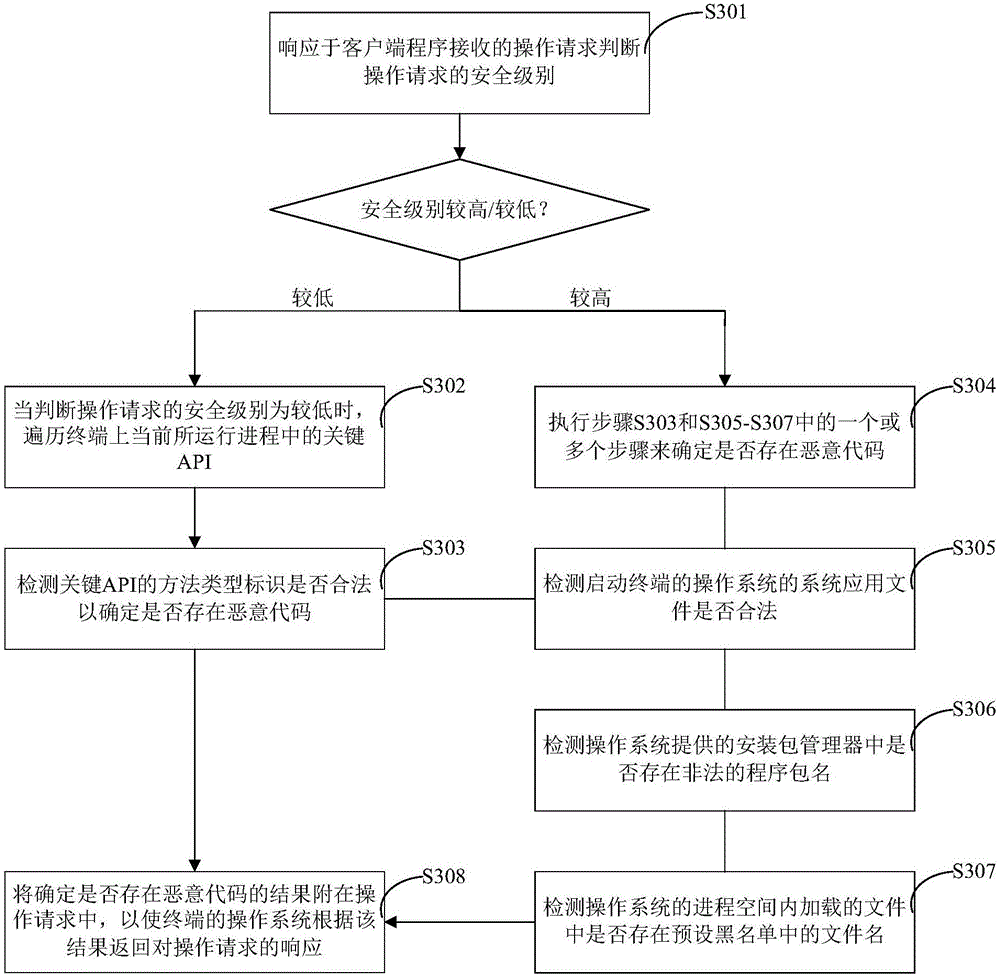
[0021] In this disclosure specification, malicious code refers to any code that is added and run in conjunction with the application without authorization by any third party other than the original provider of the application, regardless of the purpose of adding this part of the code. On the other hand, a plug-in program refers to the manifestation of malicious code when running together with the original application program or alone, and the plug-in program and malicious code may be used interchangeably in the following description unless otherwise specified.
[0022] As mentioned above, in the prior art, there are endles...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com