Transport layer security TLS chain building method, user equipment, server and system
A technology for transport layer security and user equipment, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems that affect the competitiveness of cloud servers and poor equipment performance, and achieve the effect of reducing the number of authentications and improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
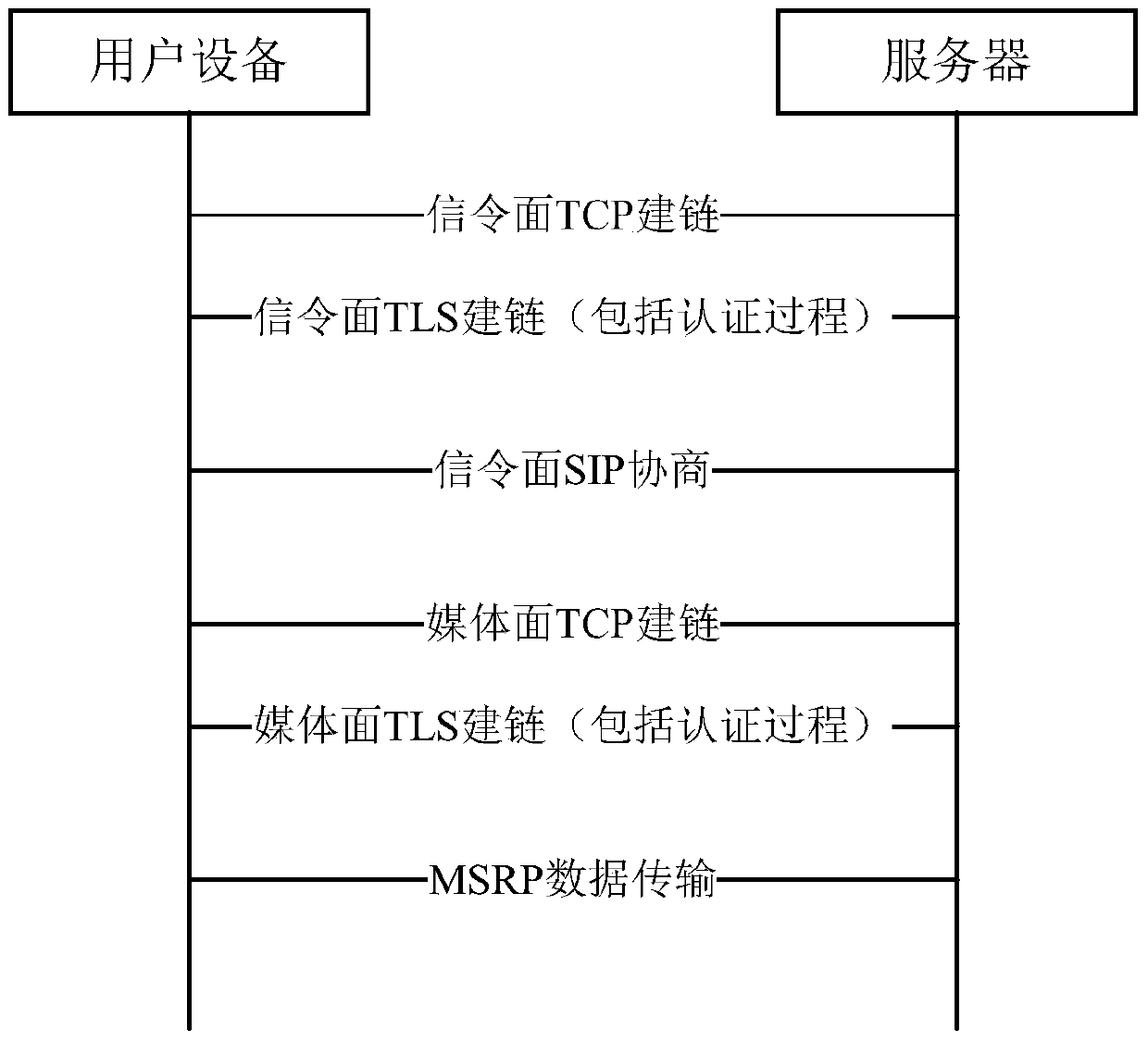
[0069] The method, client, server, and system for establishing a secure TLS link at the transport layer provided by the embodiments of the present invention can be applied to the RCS session of the rich communication suite. When both the signaling plane and the media plane are carried by TLS, the signaling plane needs to be completed first. The TLS link is established, and the two-way identity authentication between the user equipment (User Equipment, UE) and the server is completed during the link establishment process, and the Session Initiation Protocol (Session Initiation Protocol, SIP) is completed on the TLS link of the link establishment; When establishing a TLS link on the media plane, the authentication result during TLS link establishment on the signaling plane can be used to save the two-way identity authentication process between the client and server during TLS link establishment on the media plane, thus greatly improving device performance.
[0070] The following ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com