A business processing method, device and intelligent terminal
A business processing and business technology, applied in the field of network communication, can solve the problems of user property loss, illegal transfer or use of funds, easy leakage of user credentials, etc., to achieve the effect of improving security and preventing misoperation of services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
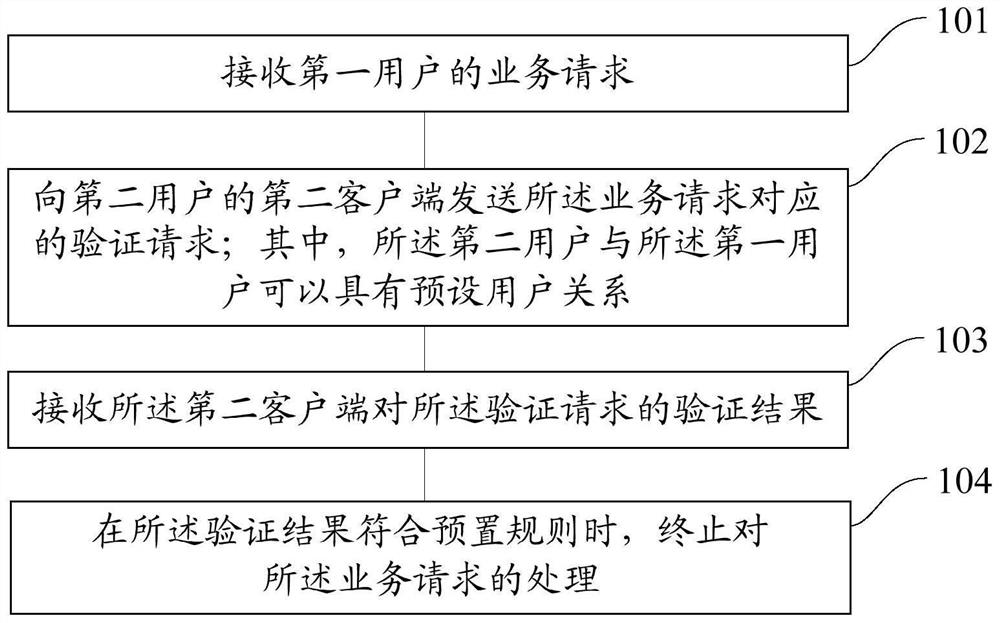
[0158]Referfigure 1 The step of the step of the embodiment of the present application is shown, and the specifically can include the following steps:
[0159]Step 101: Receive the service request of the first user;
[0160]Step 102: Send the verification request corresponding to the service request to the second client of the second user; wherein the second user can have a preset user relationship with the first user;
[0161]Step 103 receives the verification result of the second client to the verification request;
[0162]Step 104, when the verification result is in line with the preset rule, the processing of the service request is terminated.
[0163]The service processing method provided herein can be applied to the application environment corresponding to the client and server. Among them, the client and the server can be in a wired or wireless network, and the client is interacting with the server through this wired or wireless network.
[0164]Among them, the client can operate on the intelli...
Embodiment 2
[0238]ReferFigure 4 The step flow chart of the second example 2 of the operation method of the present application is shown, and the specifically can include the following steps:
[0239]Step 401: The server receives the service request of the first user;
[0240]Step 402, the server transmits a verification request corresponding to the service request to the second client of the second user; wherein the second user can have a preset user relationship with the first user;
[0241]Step 403: The server receives the verification result of the second client to the verification request;
[0242]Step 404, the server terminates the processing of the service request when the verification result conforms to the preset rule;
[0243]Step 405, the server sends a termination message to the first client of the first user; the termination message is used to indicate the termination of the service request.
[0244]Relative tofigure 1 Method Example 1,Figure 4 The process can be applied to the server, and the server...
Embodiment 3
[0247]ReferFigure 5 The steps flow diagram of an embodiment three of the third embodiment of the present application are shown, and the specifically can include the following steps:
[0248]Step 501, the first client sends a service request for the first user to the server;
[0249]Step 502, the server transmits a verification request corresponding to the service request to the second client of the second user; wherein the second user can have a preset user relationship with the first user;
[0250]Step 503, the second client receives the verification request corresponding to the service request of the first user;
[0251]Step 504, the second client verifies the verification request by the second user to obtain the corresponding verification result;
[0252]Step 505, the second client sends the verification result to the server;
[0253]Step 506, the server receives the verification result of the second client to the verification request, and terminates the processing of the service request when the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com