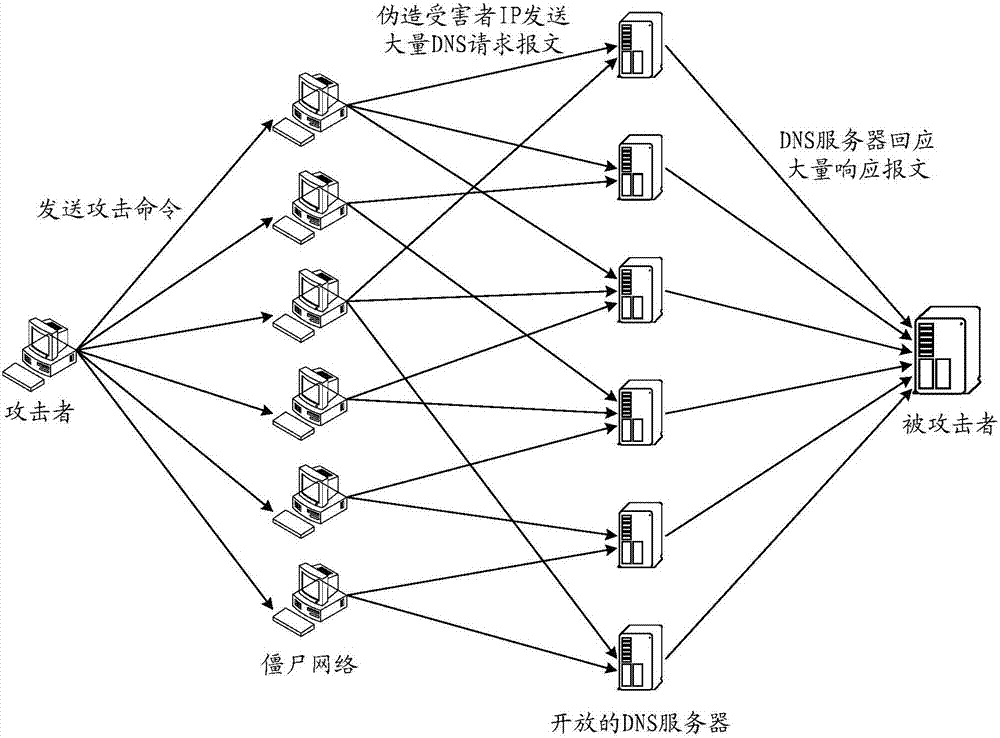
Reflection attack defending method, device and system
A technology for defending reflection and attacking packets, applied in the field of Internet security, it can solve the problems of increasing user costs, inability to implement in-line deployment, and limited deployment scenarios, so as to achieve the effect of defending reflection attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] According to an embodiment of the present application, an embodiment of a method for defending against reflection attacks is also provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
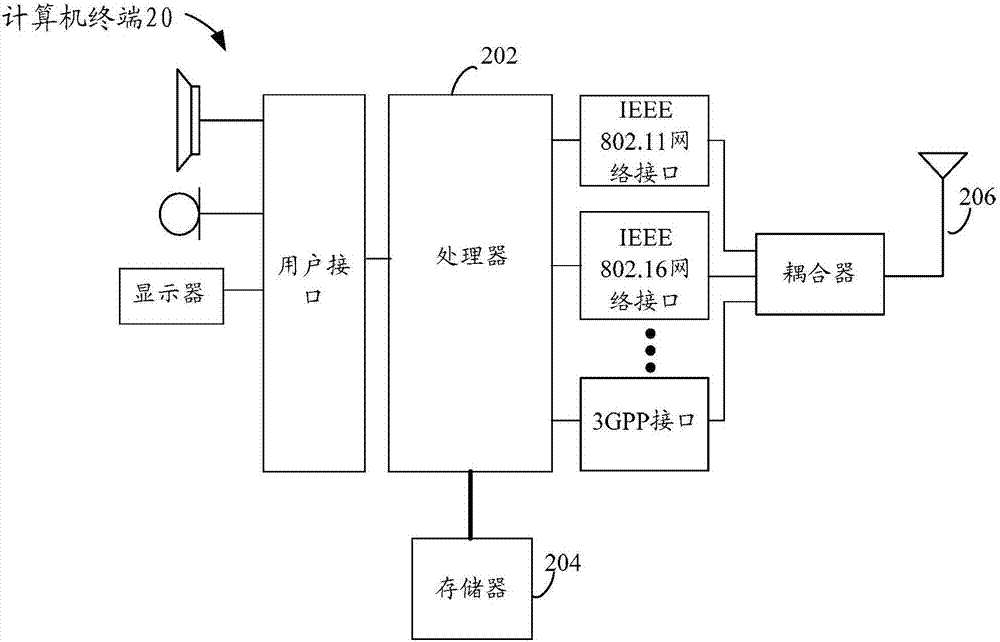
[0047] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 2 It is a hardware structural block diagram of a computer terminal according to a method for defending against reflection attacks according to an embodiment of the present application. Such as figure 2 As shown, the computer terminal 20 may include one or ...
Embodiment 2
[0129] According to an embodiment of the present application, an embodiment of a method for defending against reflection attacks is also provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
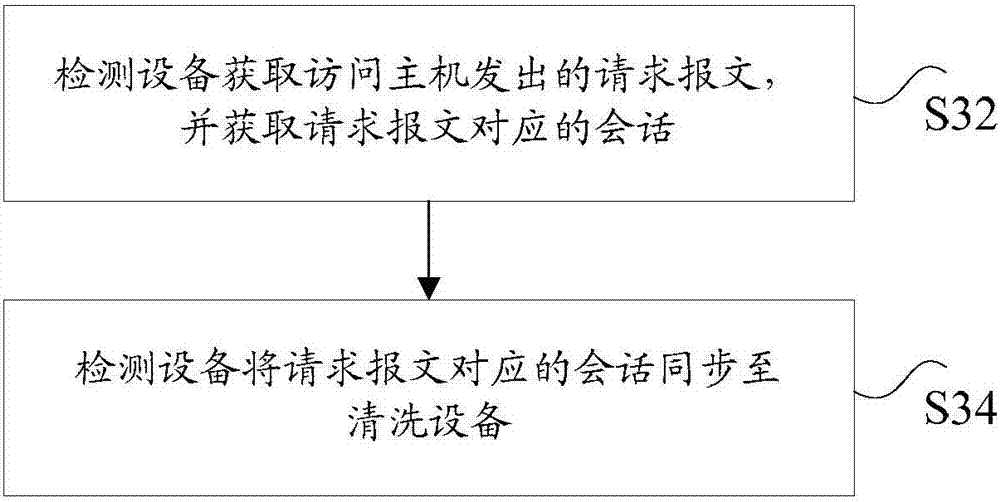
[0130] This application provides Figure 11 The method shown to defend against reflection attacks. Figure 11 is a flow chart of a method for defending against reflection attacks according to Embodiment 2 of the present application, such as Figure 11 As shown, the above method may include the following steps:
[0131] In step S112, the cleaning device receives a session synchronized by the detection device, wherein the session is a session obtained by the detection device according...
Embodiment 3
[0189] According to an embodiment of the present application, there is also provided a reflection attack defense device for implementing the above reflection attack defense method, such as Figure 12 As shown, the device includes: a first acquisition module 122 and a synchronization module 124 .
[0190] Wherein, the first obtaining module 122 is used to obtain the request message sent by the access host, and obtains the session corresponding to the request message; the synchronization module 124 is used to synchronize the session corresponding to the request message to the cleaning device; wherein, the cleaning device receives After receiving any response message, check whether there is a session matching the response message according to the response message, and if the query fails, determine that the response message is an attack message.
[0191] Specifically, the detection device can be deployed on the routing device in a bypass, and the request message sent by the access...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com