A method and device for improving the accuracy of web application layer attack detection
An attack detection and web application technology, applied in the field of network security, can solve the problems of high false alarm rate and lack of solutions, and achieve the effect of alleviating the false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
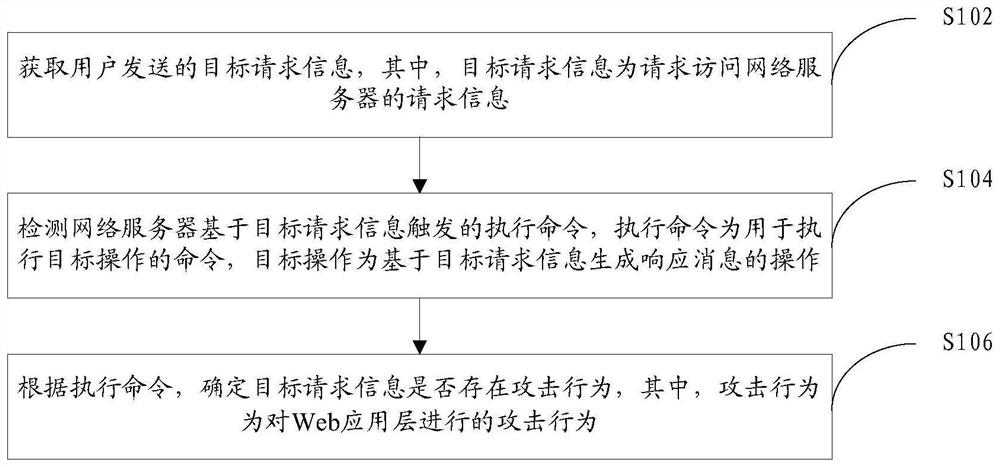
[0044] A method for improving the accuracy of Web application layer attack detection provided by the embodiment of the present invention, such as figure 1 shown, including:
[0045] Step S102, acquiring target request information sent by the user, wherein the target request information is request information for accessing a network server.
[0046] Specifically, when the target request information is request information stipulated by the HTTP protocol, the target request information is an HTTP request message. It should be emphasized that the protocol for the information requested by the target may use the HTTP protocol, but is not limited to the HTTP protocol.
[0047] Step S104 , detecting an execution command triggered by the network server based on the target request information, where the execution command is a command for executing a target operation, and the target operation is an operation for generating a response message based on the target request information.
[...
example 1
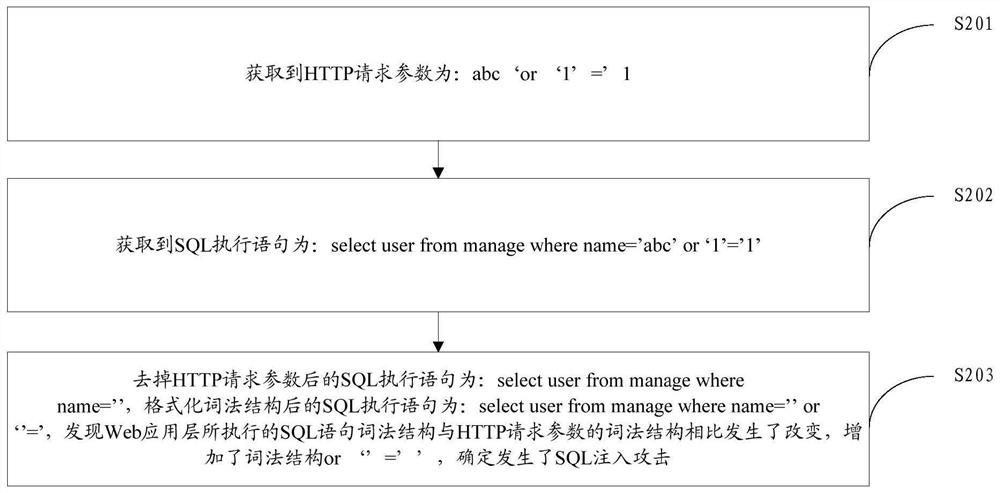
[0071] Example 1. SQL injection
[0072] First, using the Instrumentation principle in the JVMTI technology, a jar package named websec.jar with a function of detecting attacks is developed. The websec.jar includes a preset script, wherein the preset script includes a first subscript and a second subscript, The first sub-script obtains HTTP request parameters by intercepting the method of the HttpServletRequest class according to the characteristics of the HTTP protocol, and the second sub-script obtains the SQL execution statement by intercepting the method of the StatementImpl class according to the execution behavior characteristics triggered by identifying the target request information.
[0073] Then, edit the Tomcat startup script javaagent:websec.jar, and add websec.jar to the Tomcat server with parameters.
[0074] After the Tomcat server is started, the user accesses the test.jsp test page through the browser, and the Tomcat server receives the target request informat...
example 2
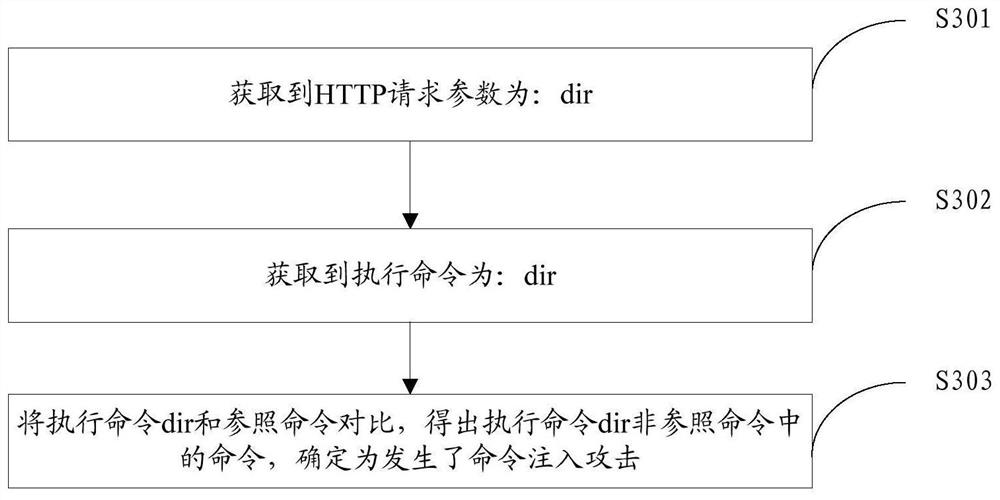
[0078] Example 2. Command Injection
[0079] First, using the Instrumentation principle in the JVMTI technology, a jar package named websec.jar with a function of detecting attacks is developed. The websec.jar includes a preset script, wherein the preset script includes a first subscript and a second subscript, The first sub-script obtains HTTP request parameters by intercepting the method of the HttpServletRequest class according to the characteristics of the HTTP protocol, and the second sub-script obtains the execution command by intercepting the method of the ProcessBuilder class according to the execution behavior characteristics triggered by the identification target request information.
[0080] Then, edit the Tomcat startup script javaagent:websec.jar, and add websec.jar to the Tomcat server with parameters.
[0081] After the Tomcat server is started, the user accesses the cmd.jsp test page through the browser, and the Tomcat server receives the target request informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com