Big data hybrid Android malicious code detection method and apparatus
A malicious code detection and hybrid technology, applied in the field of big data hybrid Android malicious code detection, can solve the problems of lack of solutions and high false alarm rate, achieve more detailed and comprehensive detection, high reliability, and reduce false alarm rate high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
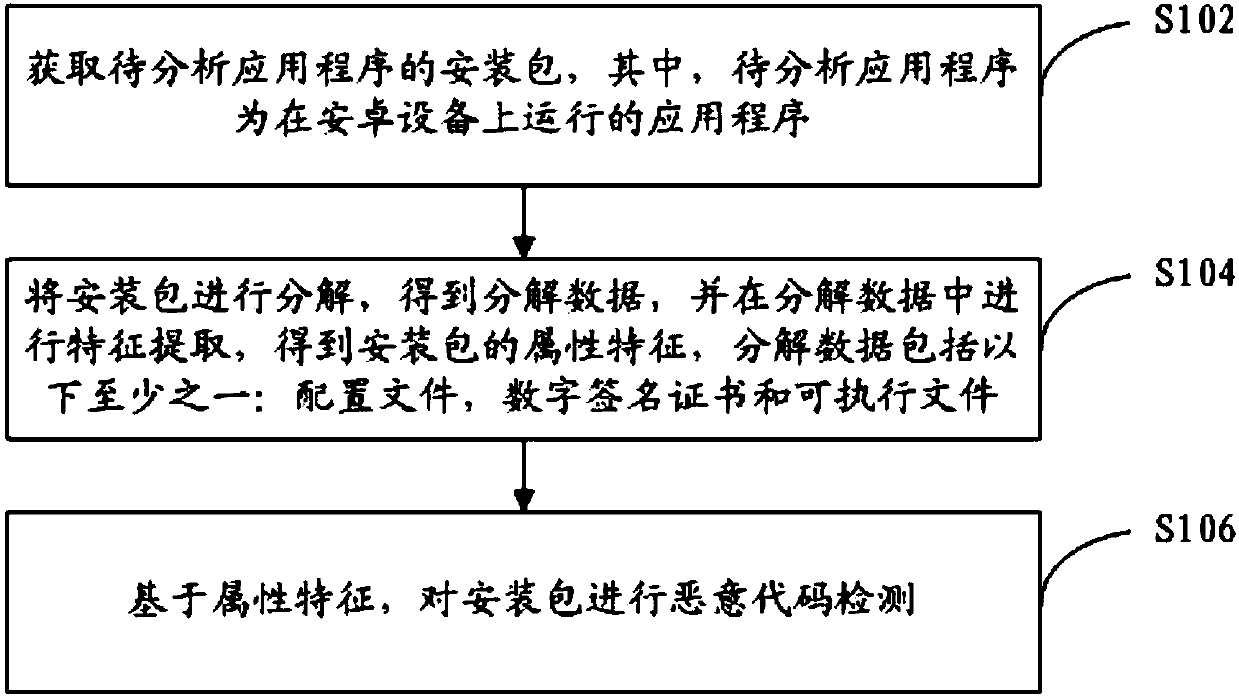
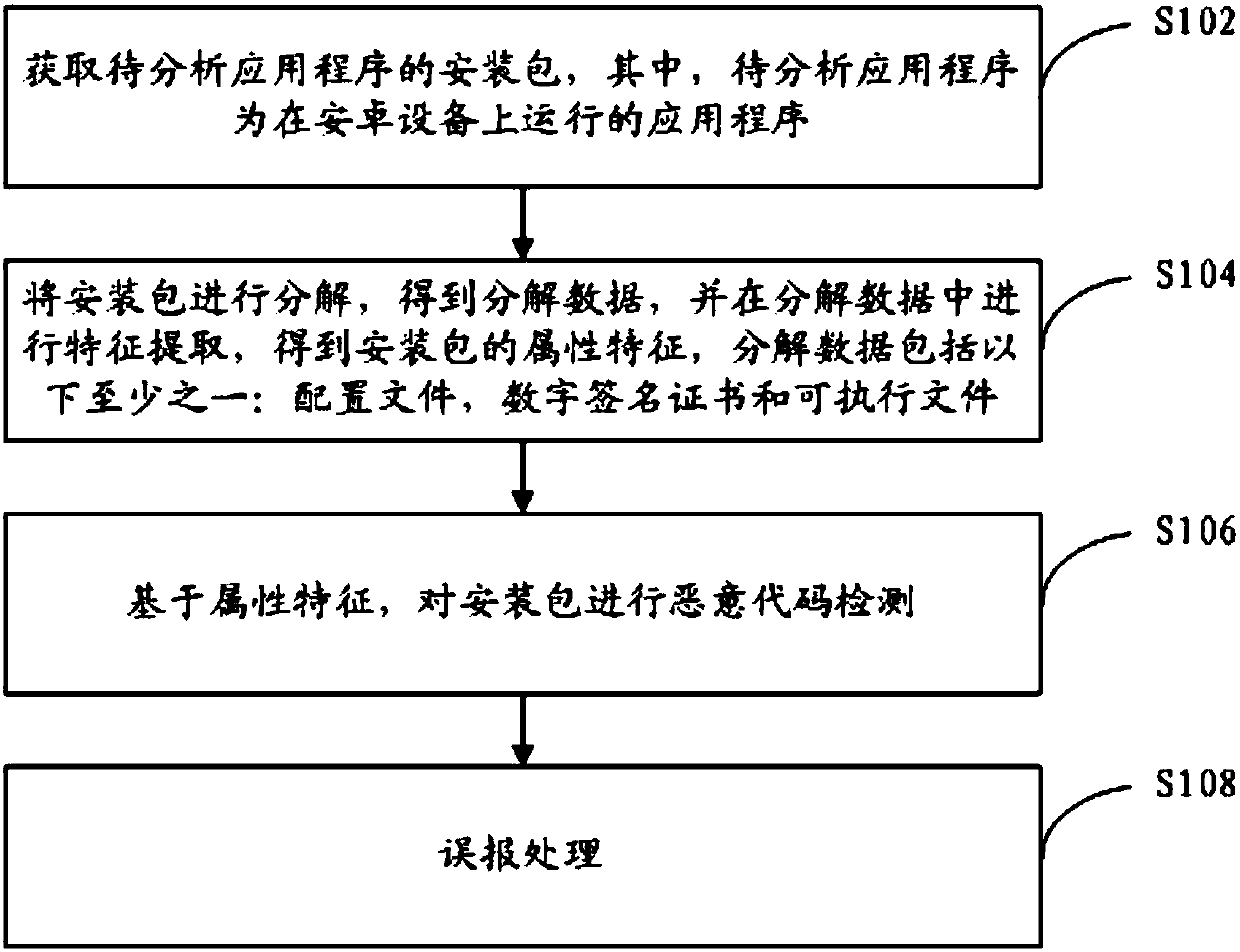
[0051] A kind of big data hybrid Android malicious code detection method that the embodiment of the present invention provides, such as figure 1 shown, including:
[0052] Step S102, obtaining the installation package of the application to be analyzed, wherein the application to be analyzed is an application running on the Android device.
[0053] Step S104, decompose the installation package to obtain decomposed data, and perform feature extraction from the decomposed data to obtain the attribute characteristics of the installation package. The decomposed data includes at least one of the following: configuration files, digital signature certificates and executable files.
[0054] Step S106, based on the attribute characteristics, perform malicious code detection on the installation package.
[0055] The big data hybrid Android malicious code detection method provided by the embodiment of the present invention decomposes the installation package to obtain decomposed data, th...
Embodiment 2
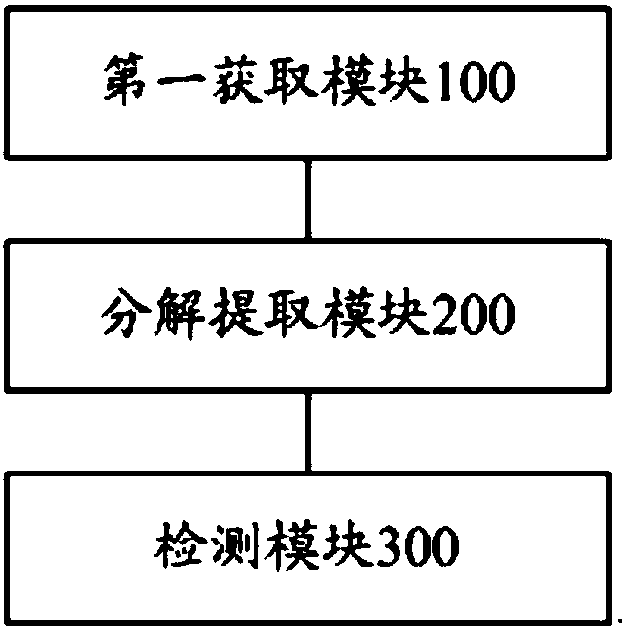
[0111] Such as Figure 3 to Figure 4 As shown, a big data hybrid Android malicious code detection device provided by the embodiment of the present invention.
[0112] refer to image 3 , the big data hybrid Android malicious code detection device includes:
[0113] The first acquiring module 100 is configured to acquire an installation package of an application to be analyzed, wherein the application to be analyzed is an application running on an Android device;
[0114] The decomposing and extracting module 200 is used to decompose the installation package to obtain decomposed data, and perform feature extraction in the decomposed data to obtain the attribute characteristics of the installation package. The decomposed data includes at least one of the following: configuration files, digital signature certificates and executable document;
[0115] The detection module 300 is configured to detect malicious codes on the installation package based on attribute characteristics....
Embodiment 3
[0141] An embodiment of the present invention provides a computer-readable medium having a non-volatile program code executable by a processor, and the program code causes the processor to execute the method of Embodiment 1.
[0142] Specifically, the storage medium includes: a USB flash drive, a mobile hard disk, a read-only memory (ROM, Read-Only Memory), a random access memory (RAM, Random Access Memory), a magnetic disk or an optical disk, and other media that can store program codes. .
[0143]In the embodiment of the present invention, the program code causes the processor to execute the method of Embodiment 1, that is, to decompose the installation package to obtain decomposed data, and the decomposed data includes at least one of the following: configuration files, digital signature certificates and executable files, and then decompose Feature extraction is performed on the data, and based on attribute features, malicious code detection is performed on the installation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com