Android integrity verification method and device based on trusted execution environment
A technology for integrity verification and execution environment, applied in the field of trusted computing of mobile terminals, it can solve the problems of inability to widely popularize applications, rough security of rights management, etc., and achieve the effect of avoiding attacks and facilitating popularization and application.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0046] This embodiment provides a method for detecting abuse of Android application rights based on process communication, including the following steps:
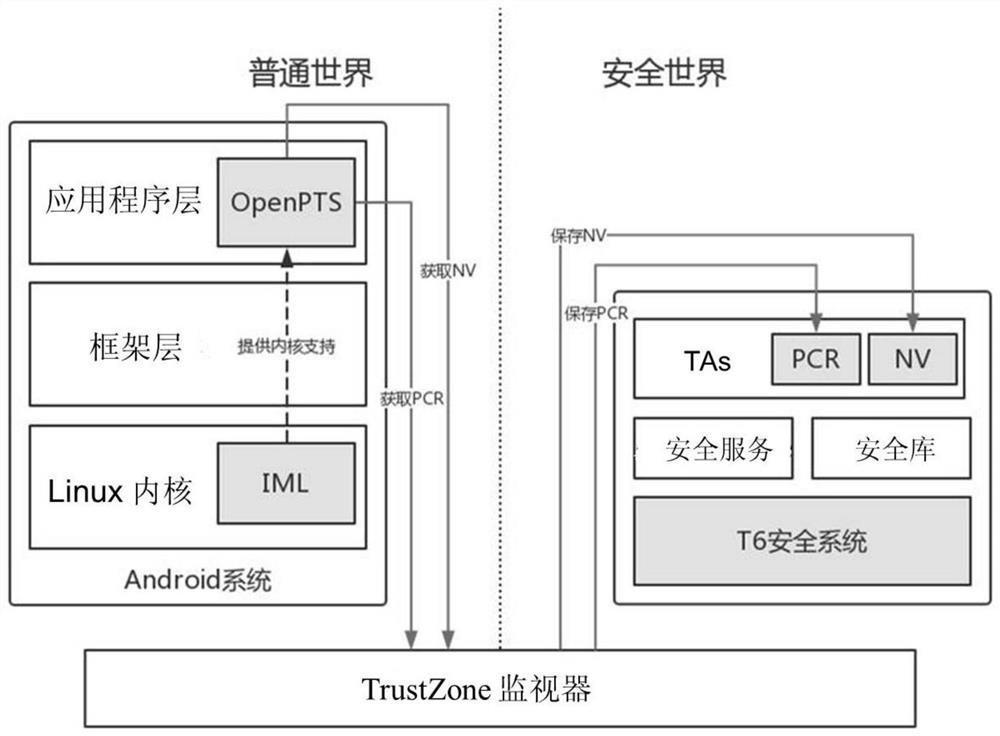
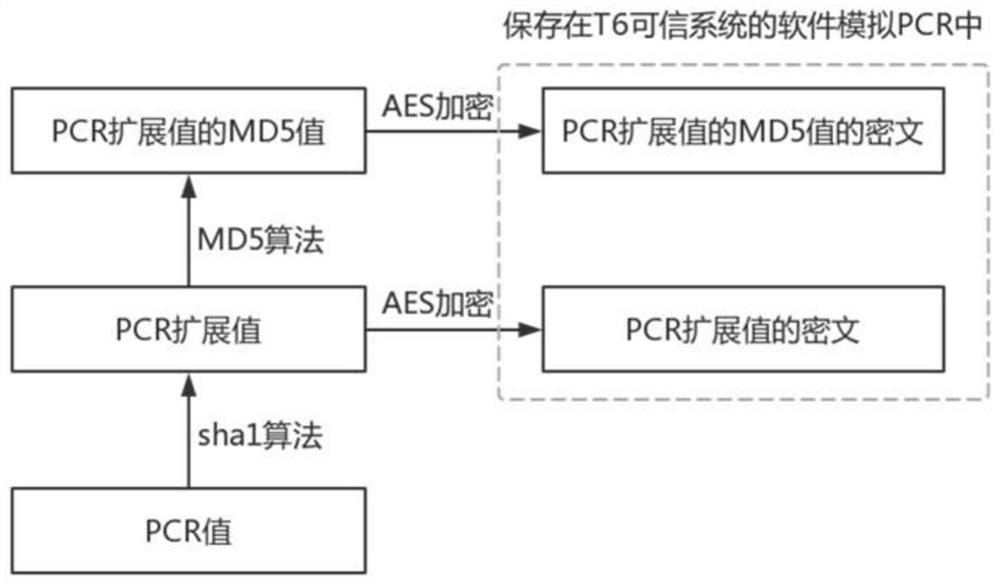
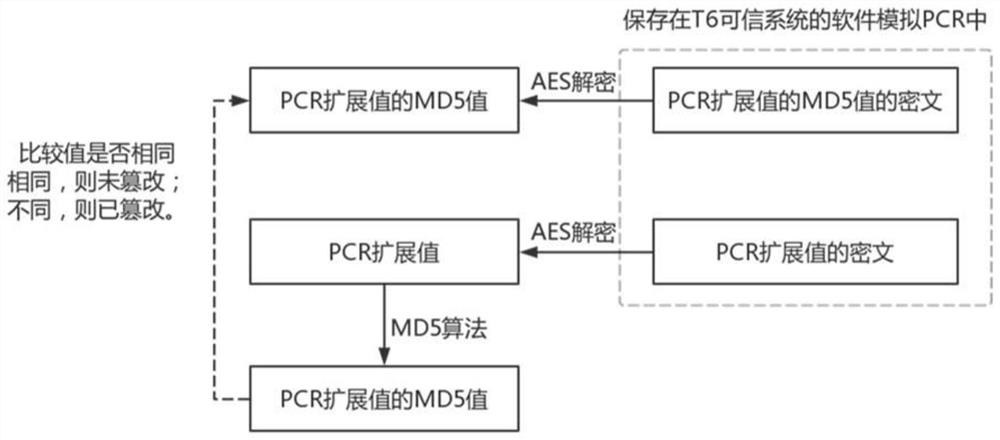
[0047] S1. With the support of the TrustZone trusted platform, develop trusted software based on the T6 security system to simulate the PCR and NV registers of the hardware TPM chip. Among them, the T6 security system refers to the operating system and Trusted Execution Environment (TEE) platform independently developed by the core team of Pingbo Information Technology, which is designed for security. By using the chip-level isolation technology ARM TrustZone and the most The advanced protection mechanism effectively prevents the leakage of sensitive information, and ensures the security of the operating system itself and the applications, biometrics, passwords, files, etc. carried...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com