Privacy information protecting method, mobile terminal and computer readable storage medium
A technology for privacy information and storage media, applied in the fields of privacy information protection, mobile terminals and computer-readable storage media, can solve problems such as leakage of user privacy data, and achieve the effect of tracking protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
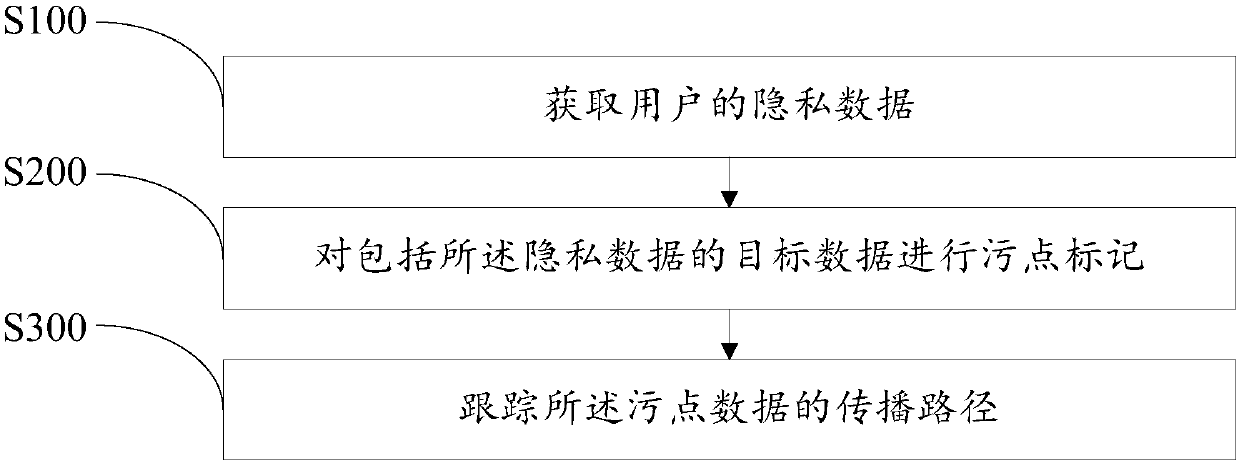
[0085] Based on the first embodiment, the second embodiment of the privacy information protection method of the present invention is proposed, refer to Figure 4 , in this embodiment, before step S200, the privacy information protection method further includes:
[0086] Step S400, marking the private data as privacy tainted data;
[0087] In this embodiment, when the private data is acquired, the private data is marked with a taint, and the marked private data is the private tainted data, and the process of the tainted mark is through the tainted information added to the private data, The private data can be uniquely identified and tracked through the taint information; specifically, when the private data is obtained, the first handle cursor of the private data is obtained, and the first handle cursor is the private data corresponding to the The handle cursor of the taint mark, wherein the handle cursor is used to uniquely identify a target resource, and the target resource p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com