Data security protection method and device
A data security and data technology, applied in the field of data security, can solve problems such as single evaluation index and unreasonable evaluation process, and achieve the effect of solving single evaluation index
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
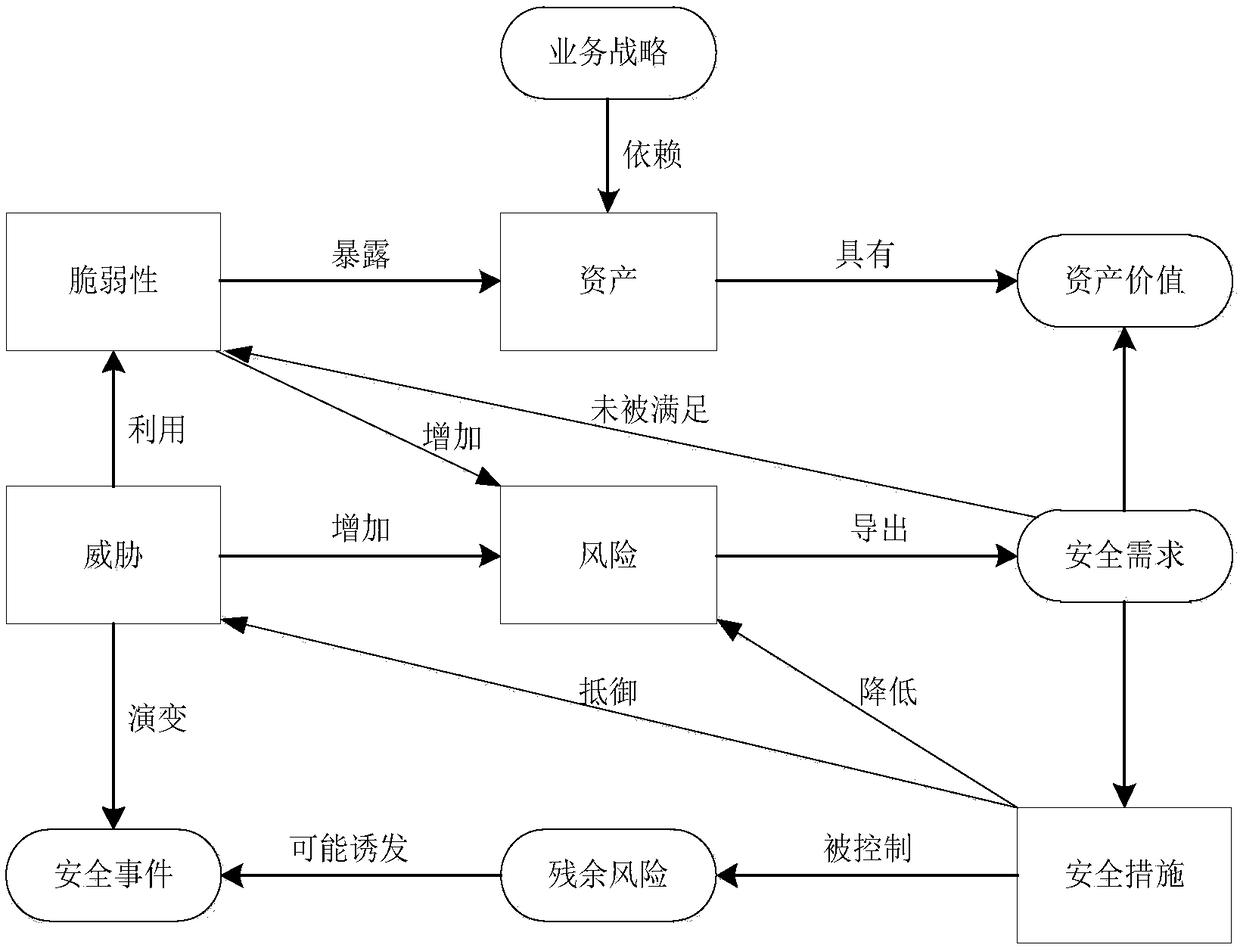
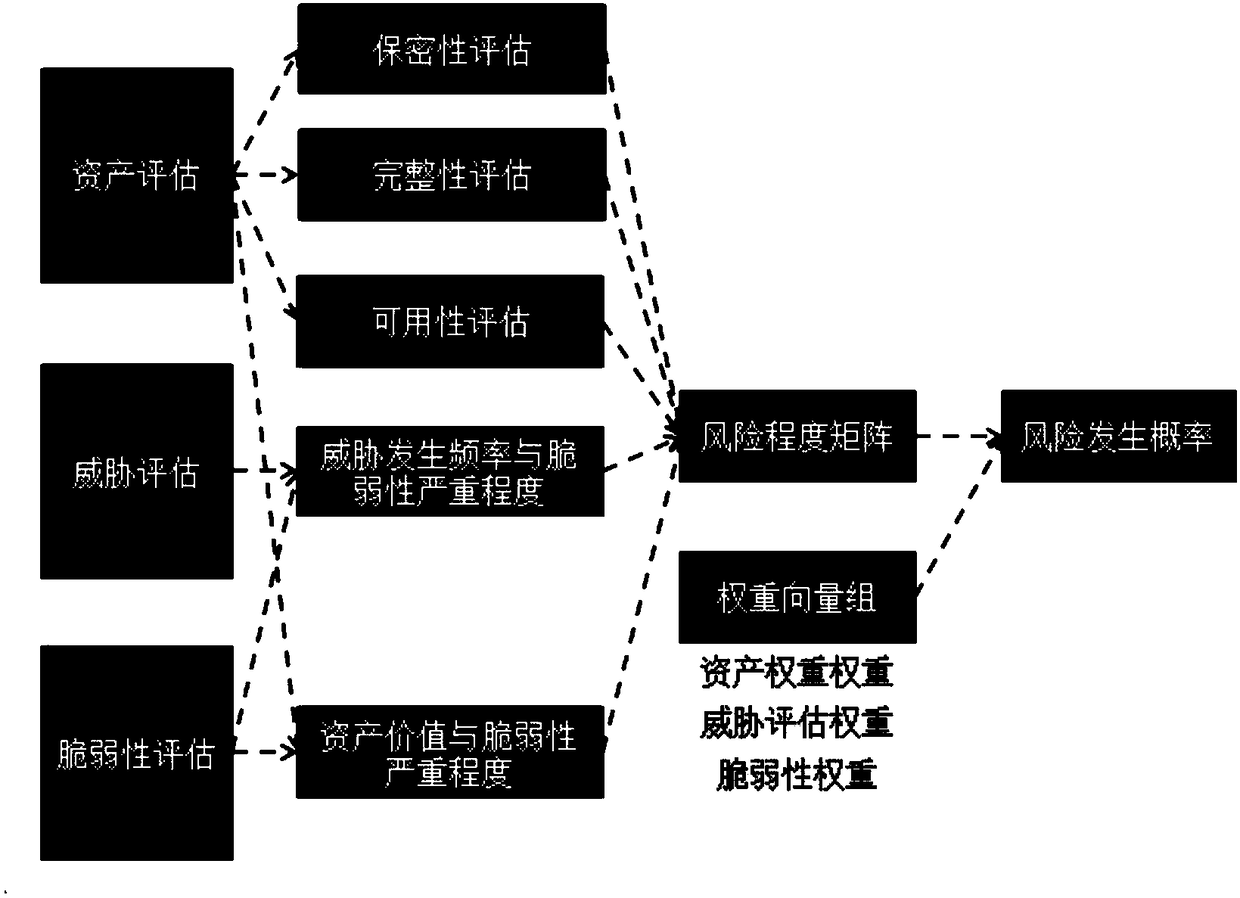
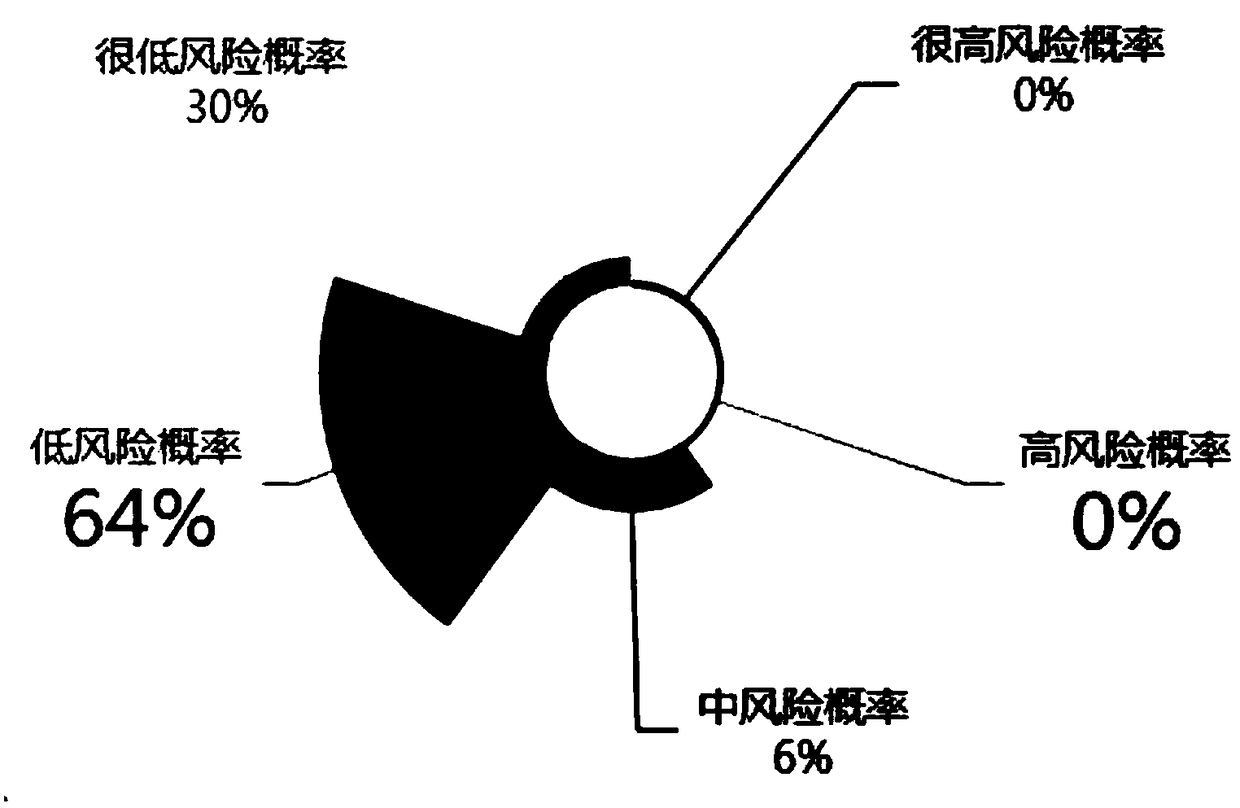
[0072] Such as figure 1 As shown, the content of the middle box part is the basic elements of risk assessment, and the content of the oval part is the attributes related to these elements. Risk assessment revolves around the basic elements of assets, threats, vulnerabilities, and security measures. In the process of evaluating the basic elements, it is necessary to fully consider business strategies, asset values, security requirements, security incidents, and residual risks related to these basic elements. of various attributes. The following pairs figure 1 The content in is explained.
[0073] Assets are valuable, and the higher the organization's business strategy relies on assets, the greater the value of assets;
[0074] Risks are triggered by threats, and the more threats an asset faces, the greater the risk, which may evolve into a security incident;
[0075] The vulnerability of assets may expose the value of assets, and the more weaknesses an asset has, the greate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com