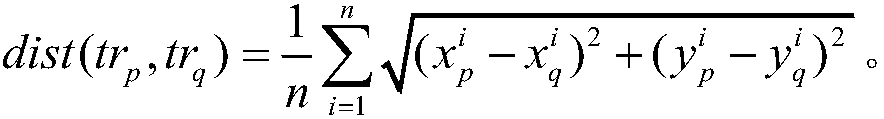Generalization-based location privacy protection method
A privacy protection and generalization technology, applied in the field of location privacy protection based on generalization, can solve problems such as user privacy leakage, achieve the effect of protecting privacy security, ensuring quality, and balancing contradictions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
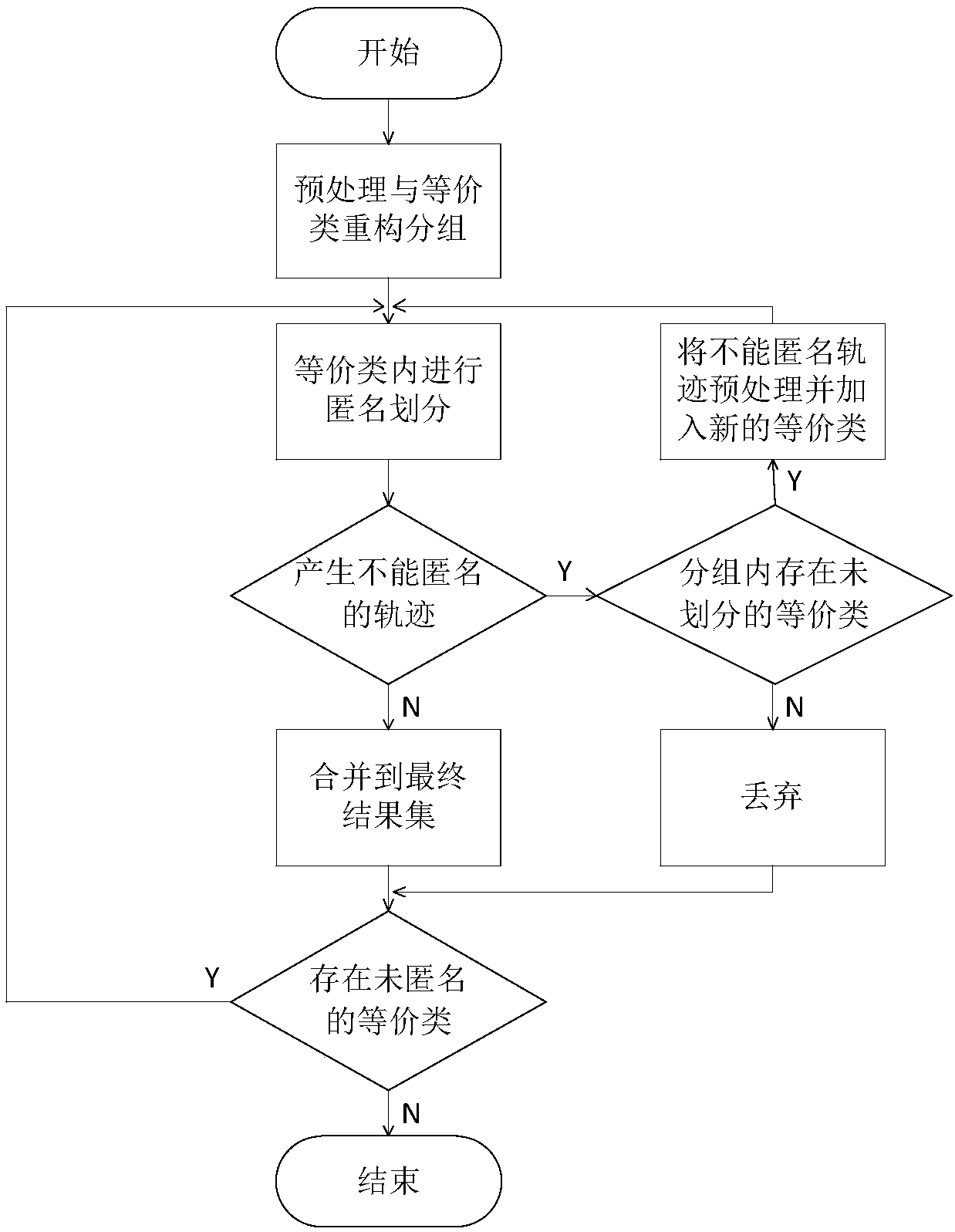
[0038] Such as figure 2 As shown, the location privacy protection method based on generalization of the present invention includes the following steps:
[0039] 1) Trajectory dataset preprocessing:
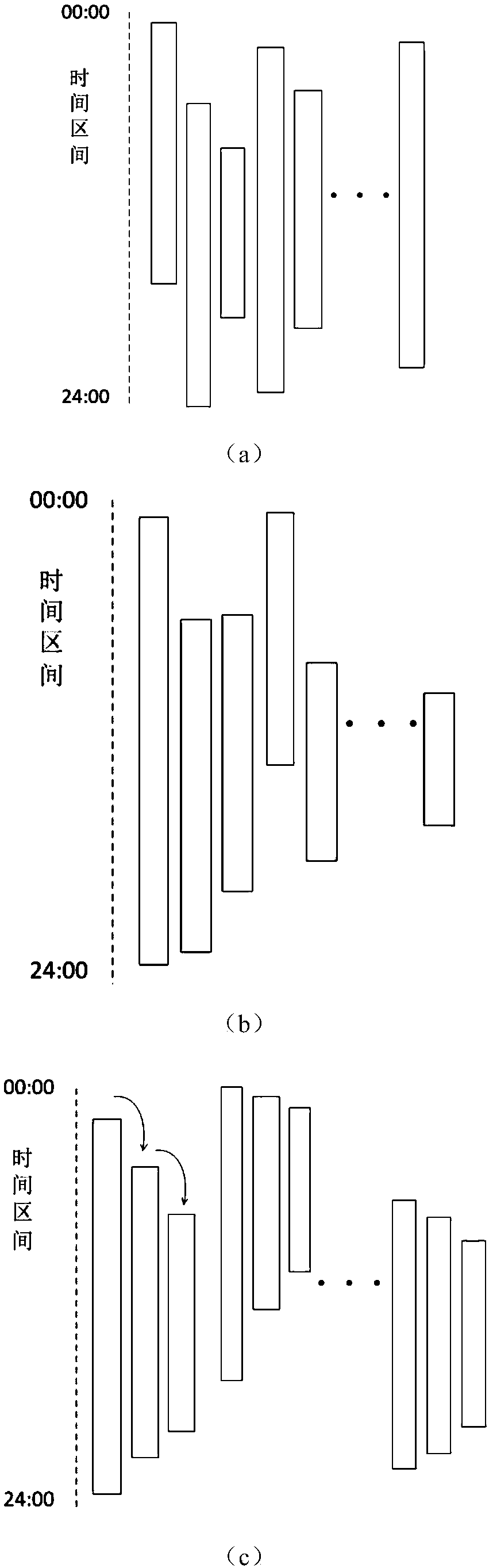
[0040] The coordinate set formed by the user location data collected by the location service provider in chronological order is called a trajectory, which can be expressed as: tr p ={p 1 ,p 2 ,...p n}, where each node contains a set of time and coordinate information, namely p i =(t i ,x i ,y i ), the subscript n represents the number of nodes.
[0041] Collect the respective trajectories generated by different users within the sampling time of the location server to form the original tra...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap