User identity-based input association recommendation method and apparatus
A user identity and recommendation method technology, applied in the field of computer networks, can solve the problems of reducing the accuracy of recommended information and different user search habits.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
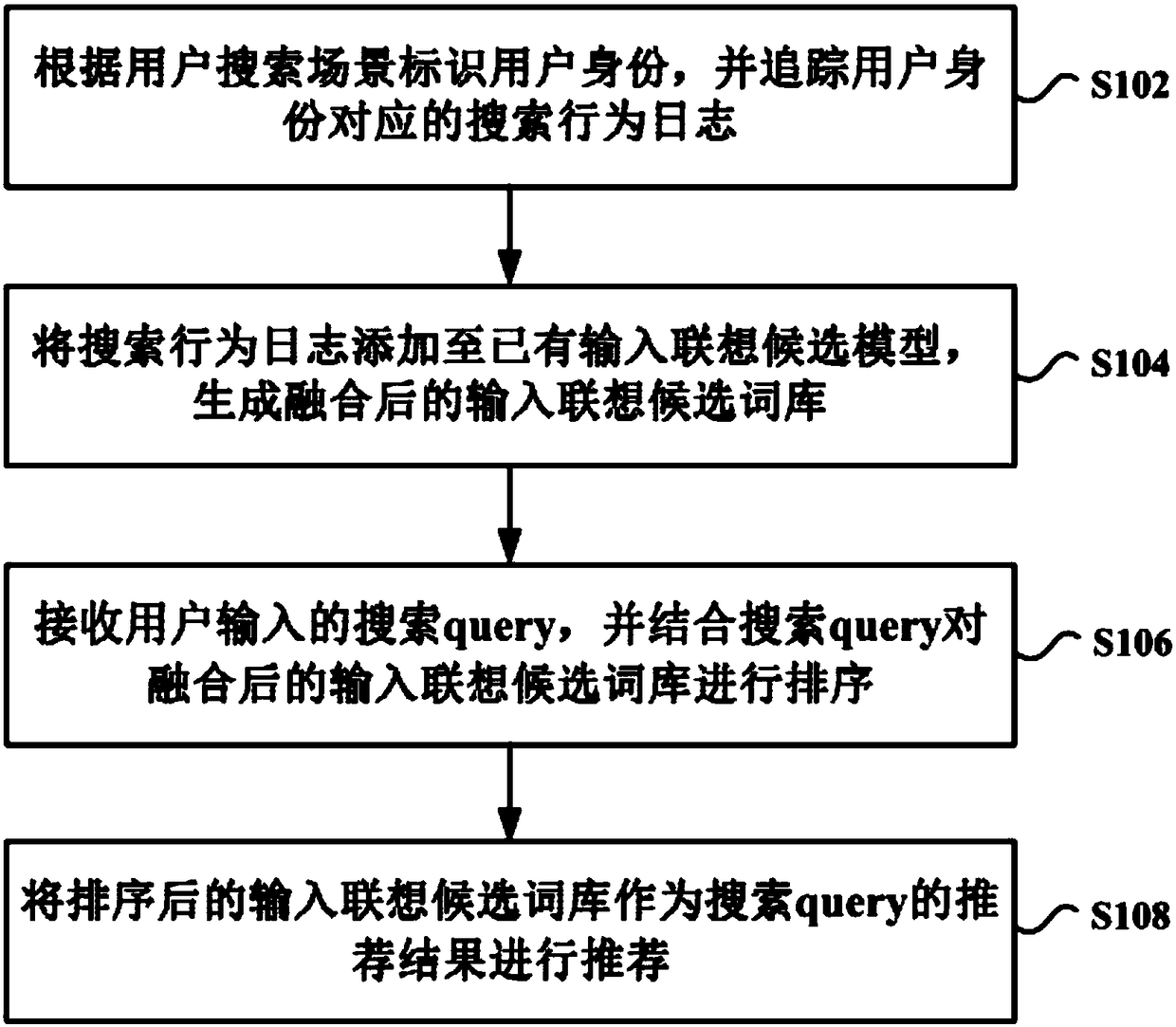
[0104] This embodiment makes further improvements on the basis of the original input association. Specifically, in this embodiment, the user searches for information through the search engine "360 Safe Browser". Moreover, when making specific inquiries, the user logs in to the 360 account on the "360 Secure Browser", and further, conducts information search on the "360 Secure Browser" through the 360 account.
[0105] figure 2 It is a specific flowchart of an input association recommendation method based on user identity according to an embodiment of the present invention. like figure 2 As shown, step S201 is firstly executed to mine user search behavior logs in the network to generate existing input association candidate models.
[0106] In this step, the user's input search behavior and / or click search behavior on each search engine in the network may be mined to generate a user search behavior log. Further, based on the preset extraction model, hot candidate words...
Embodiment 2
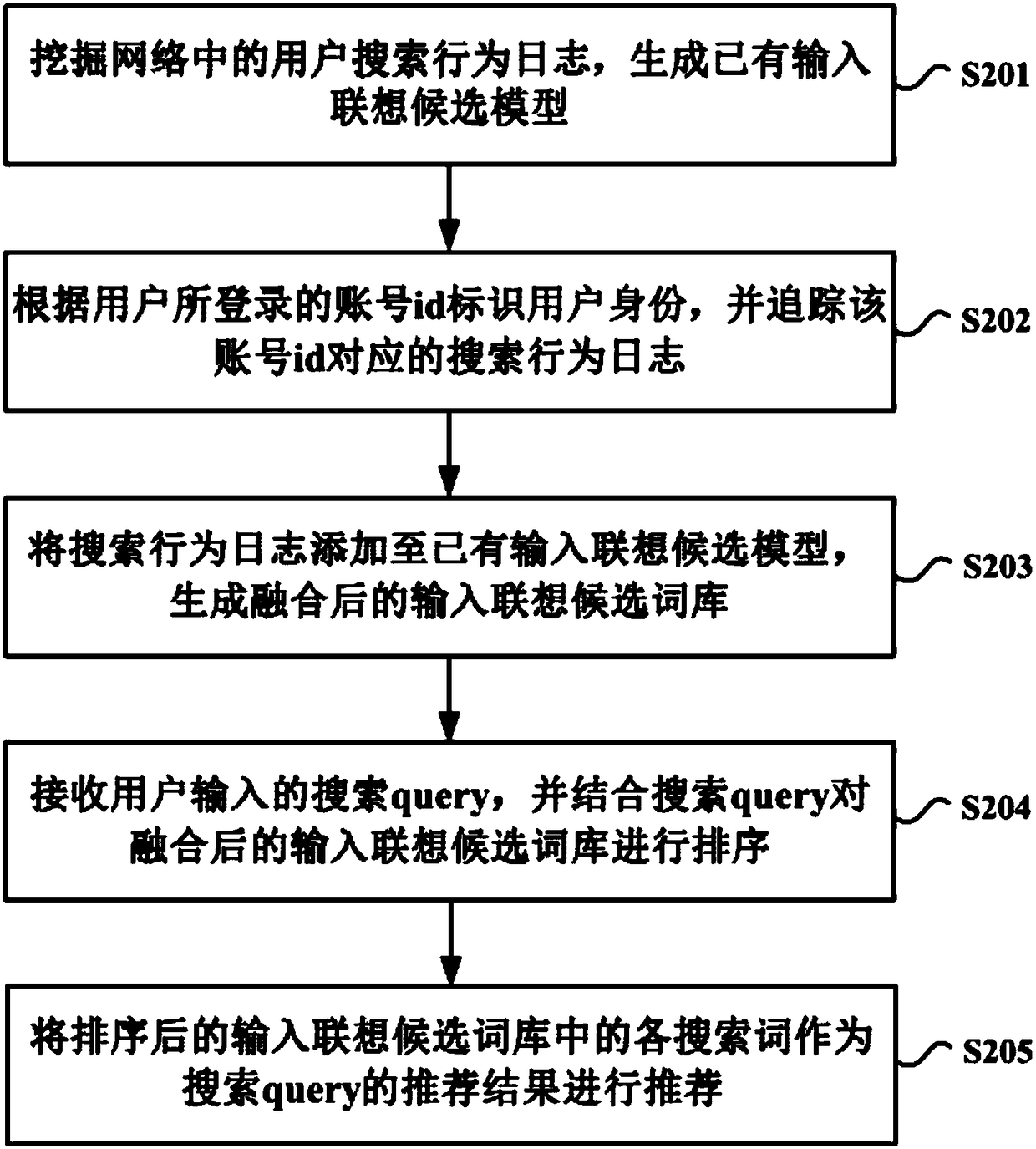
[0115]This embodiment is based on the first embodiment, and further expands the content of the first embodiment. This embodiment specifically introduces the step of adding the search behavior log to the existing input association candidate model to generate a fused input association candidate thesaurus.
[0116] Figure 5 It is a flow chart of a specific method for adding a search behavior log to an existing input association candidate model according to an embodiment of the present invention. like Figure 5 As shown, first, step S501 is executed to identify the user identity according to the user's search scenario, and track the search behavior log corresponding to the user identity.
[0117] Further, step S502 is executed to filter the traced search behavior logs according to a preset filtering logic.
[0118] In this step, the sensitive words in the tracked search behavior logs can be filtered according to the anti-cheating word brushing strategy. The anti-cheating word...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com