Information collection method and terminal
A terminal and collection card technology, applied in instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of no private collection, information exposure, lack of exclusivity of portable electronic devices, etc., to improve user experience and ensure security and the effect of stealth
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
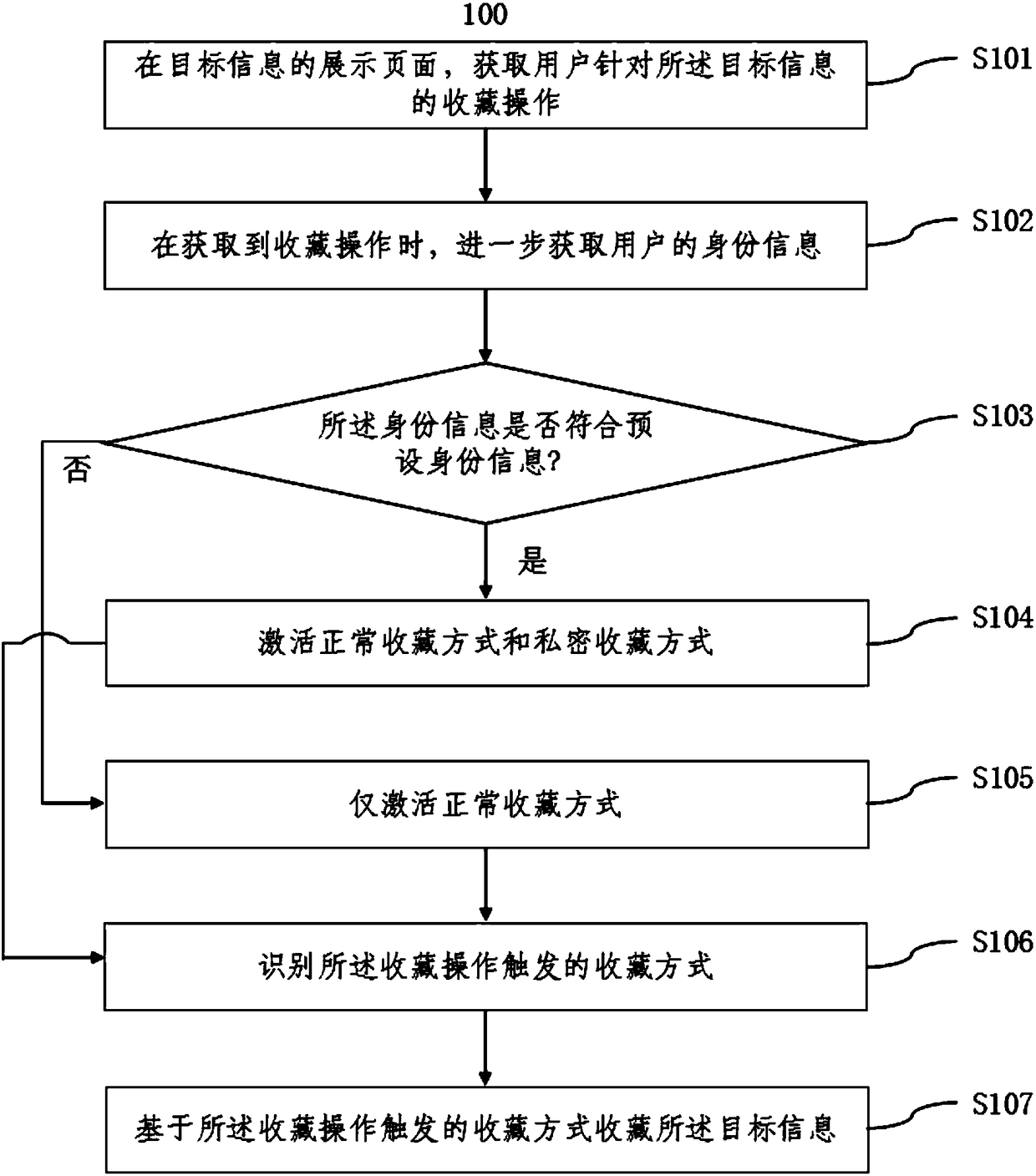
[0062] Please refer to figure 1 (i.e. 100 shown in the accompanying drawings), figure 1 It is a schematic flowchart of an information collection method provided according to some embodiments of the present application;
[0063] Such as figure 1 As shown, the embodiment of the present application provides a method for storing information, which is applied to a terminal, and the method includes:
[0064]Step S101: On the target information display page, acquire the user's collection operation for the target information;
[0065] Step S102: when the collection operation is obtained, further obtain the identity information of the user;
[0066] Step S103: judging whether the identity information conforms to the preset identity information;
[0067] If the identity information conforms to the preset identity information, enter step S104: activate the normal collection mode and the private collection mode;
[0068] If the identity information does not conform to the preset iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com