An unlocking request response method, mobile terminal
A mobile terminal, request-response technology, applied in digital data authentication and other directions, can solve problems such as malicious unlocking, and achieve the effect of improving unlocking security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
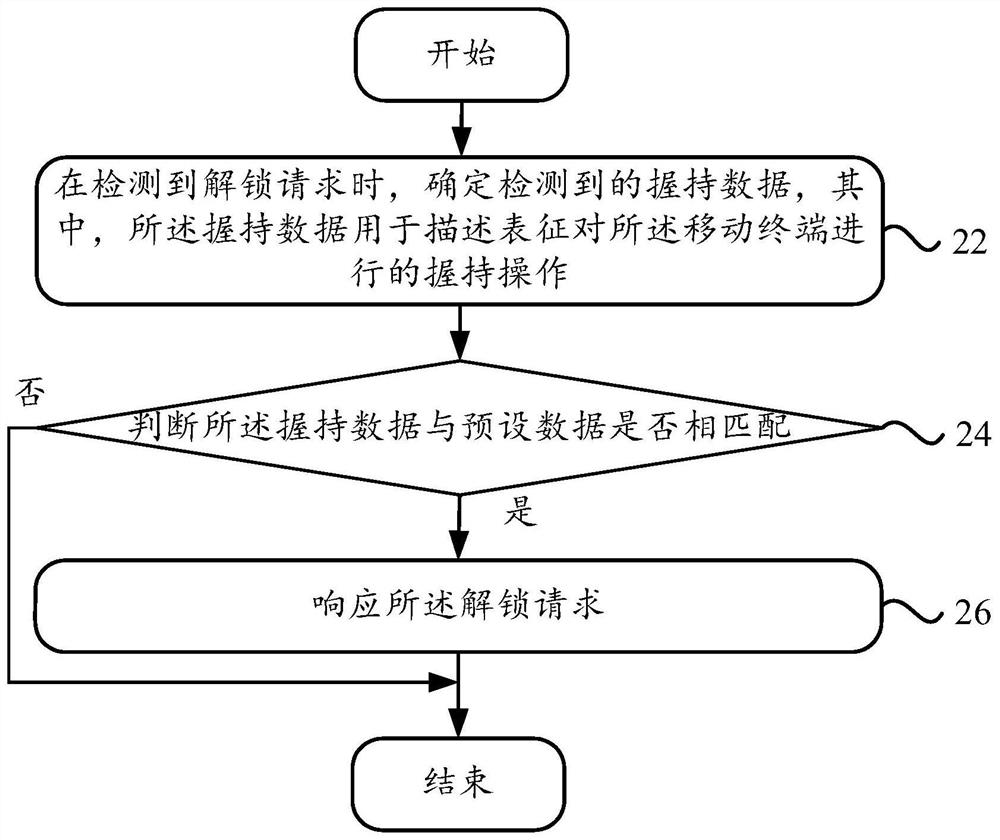
[0036] figure 2 It is a schematic flowchart of an unlocking request response method provided in Embodiment 1 of the present invention, see figure 2 , the method may specifically include the following steps:
[0037] Step 22. When an unlock request is detected, determine the detected grip data, wherein the grip data is used to describe and indicate that the main body of the grip operation on the mobile terminal is the mobile terminal;
[0038] In combination with the above application scenarios, it should be noted that the first implementation of step 22 may be:
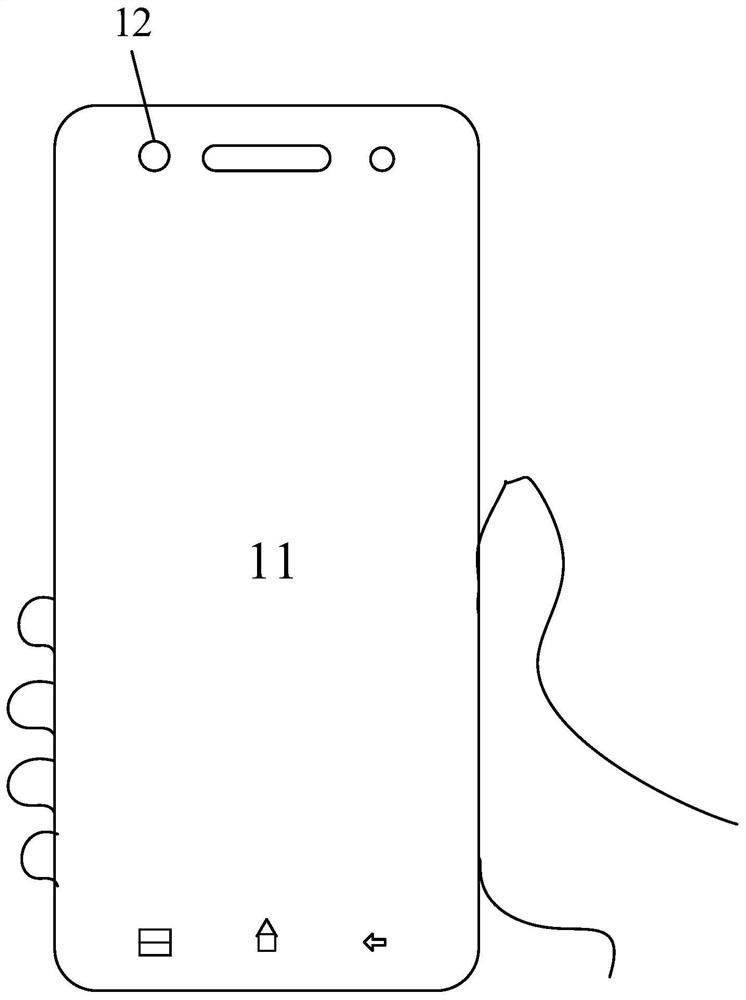
[0039] When the mobile terminal is in the locked screen state, if the user places his face in the image collection area of the camera of the mobile terminal, the camera collects the user's facial image (or facial feature data) and sends it to the mobile terminal in the form of an unlock request. processor. The processor uses the unlock request as a trigger condition to read the data currently collected by the g...
Embodiment 2
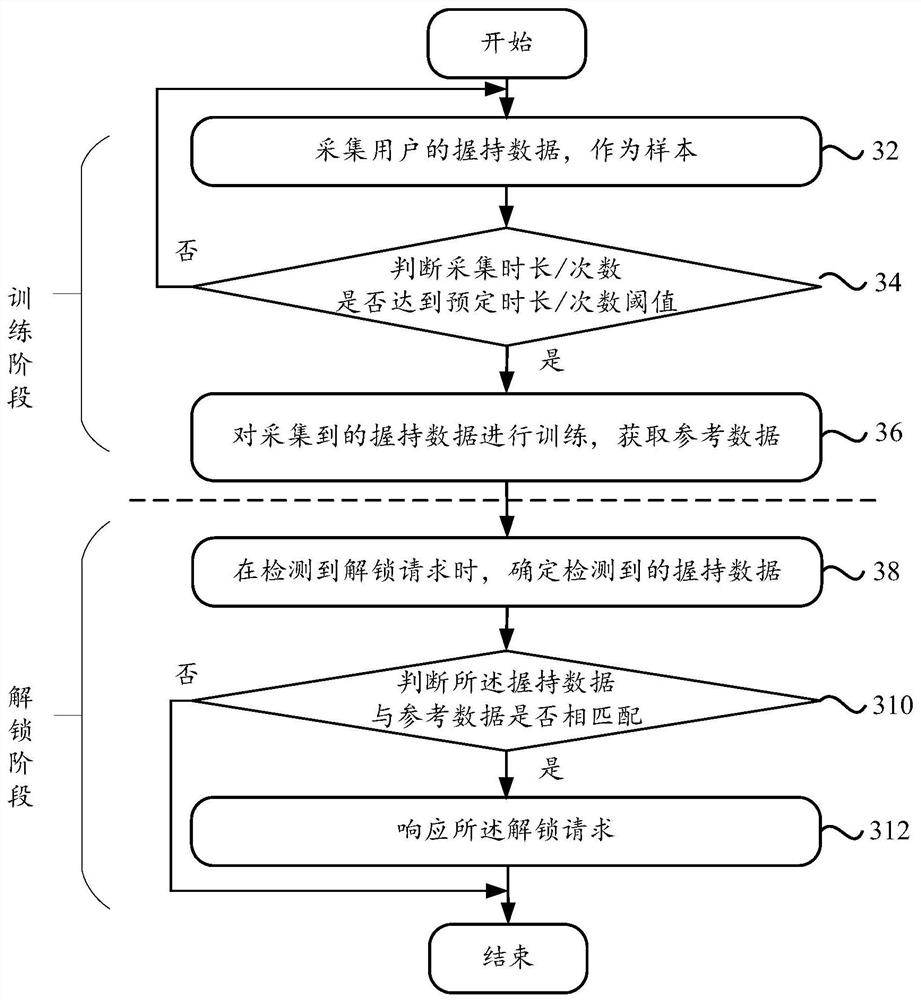
[0055] image 3 It is a schematic flowchart of an unlocking request response method provided in Embodiment 2 of the present invention, see image 3 , the method may specifically include the following steps:
[0056] Step 32, collect the gripping data of the user as a sample;
[0057] Step 34, judging whether the collection duration / number of times reaches the predetermined duration / number of times threshold
[0058] If yes, execute step 36; if not, execute step 32 again.
[0059] Step 36, train the collected gripping data and obtain reference data
[0060] Step 38. When an unlock request is detected, determine the detected grip data
[0061] Step 310, judging whether the gripping data matches the reference data
[0062] If yes, execute step 312; if no, end.
[0063] Step 312: Respond to the unlocking request.
[0064] It should be noted that steps 32 to 36 constitute the training phase of this embodiment, and steps 38 to 312 constitute the unlocking phase of this embodi...
Embodiment 3
[0148] Figure 6 is a schematic structural diagram of a mobile terminal provided in Embodiment 3 of the present invention, see Figure 6 , the mobile terminal may specifically include: a first determination module 61 and a response module 62, wherein,
[0149] The first determining module 61 is configured to determine the detected grip data when an unlock request is detected, wherein the grip data is used to represent a grip operation performed on the mobile terminal;
[0150] The response module 62 is configured to respond to the unlocking request when the holding data matches the preset data.
[0151] combine Figure 4a-Figure 4d , the first structure of the first determination module 61 includes:
[0152] A first acquiring unit, configured to acquire a predetermined parameter, the predetermined parameter including at least one predetermined characteristic parameter of the antenna of the mobile terminal; wherein, the antenna includes an antenna A41, an antenna B42, an ant...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com