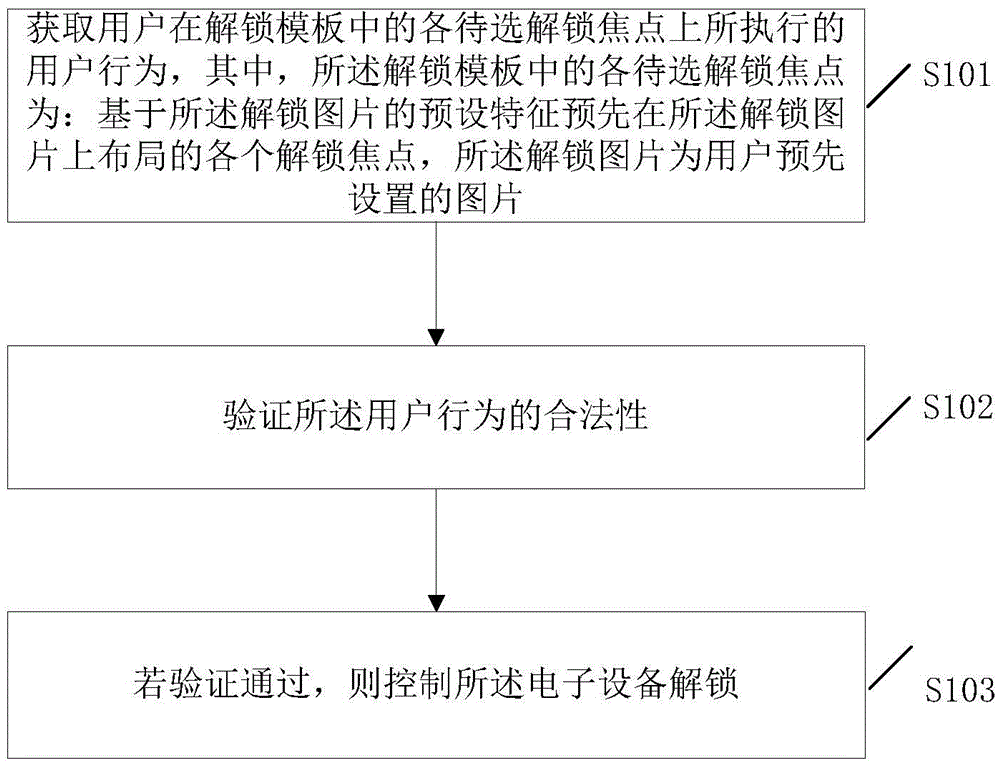
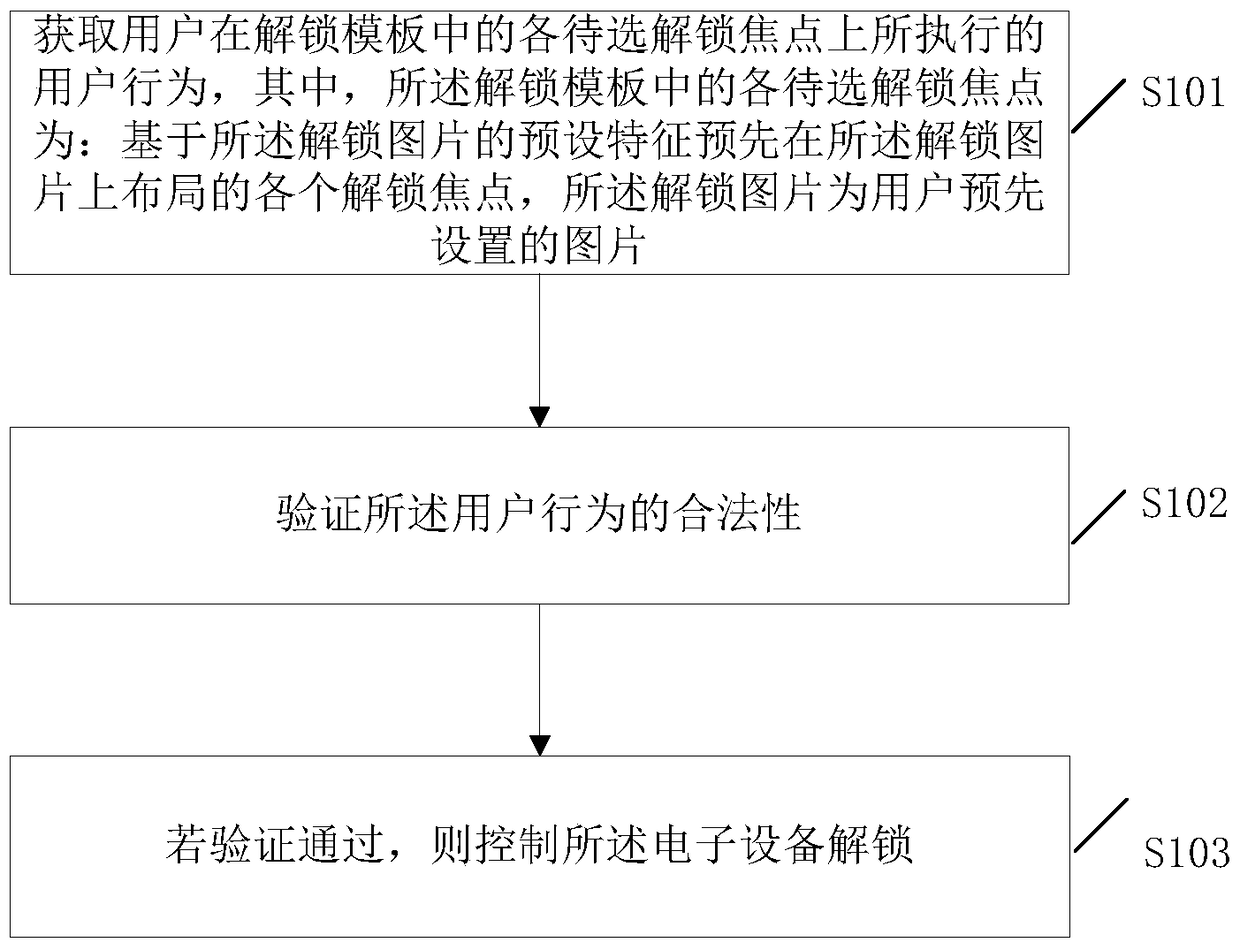
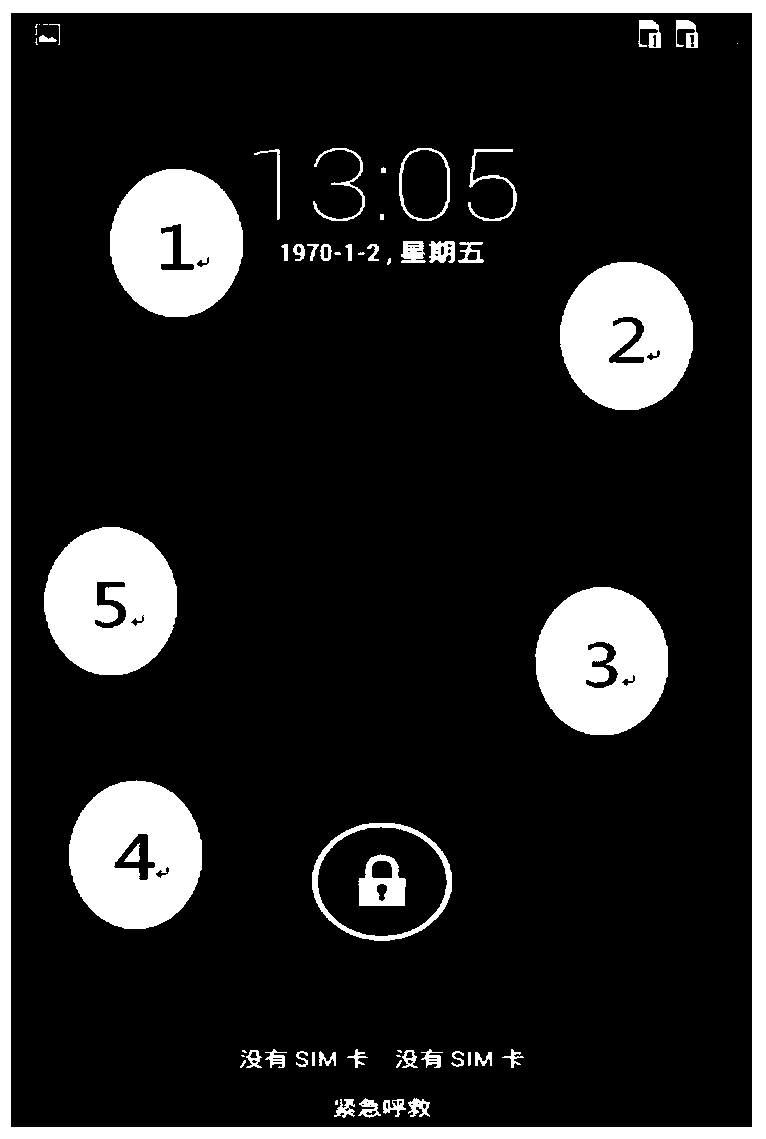
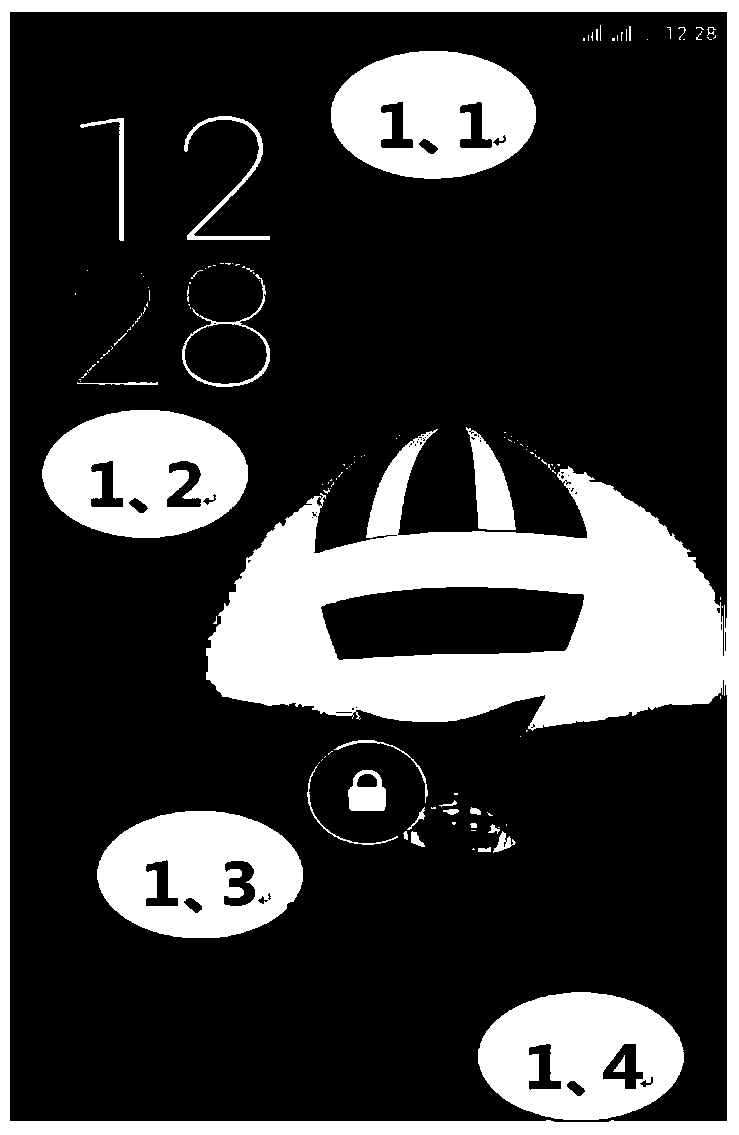
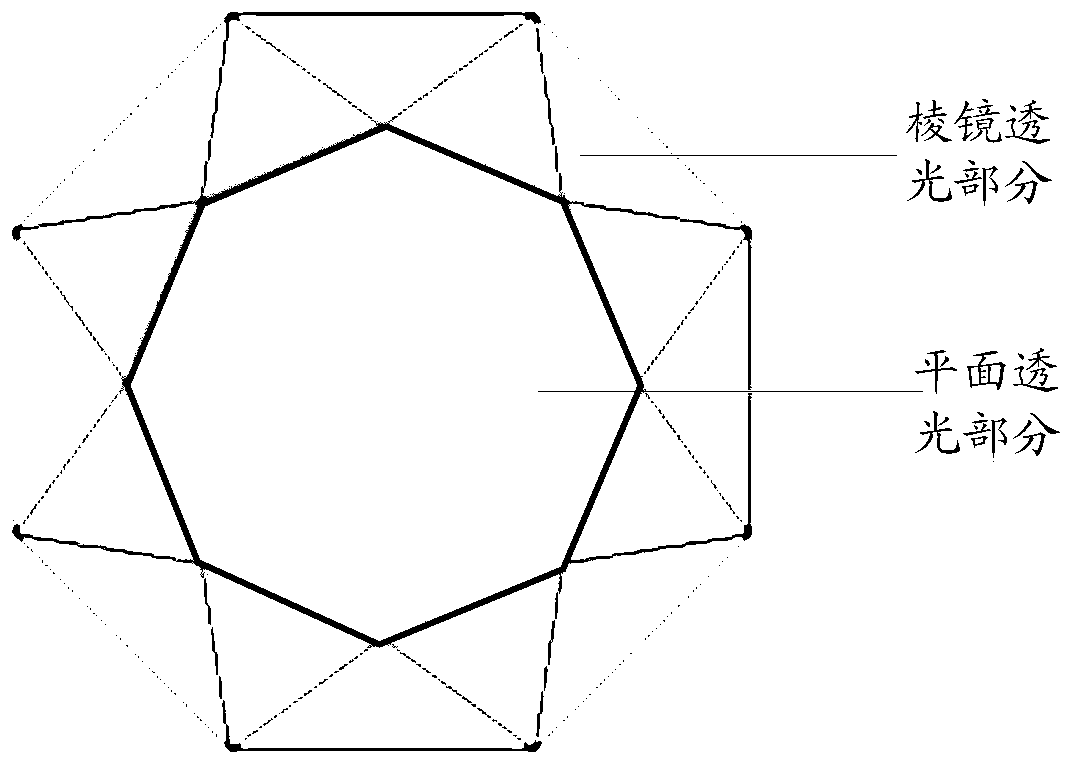
Patents
Literature
50results about How to "Improve unlock security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
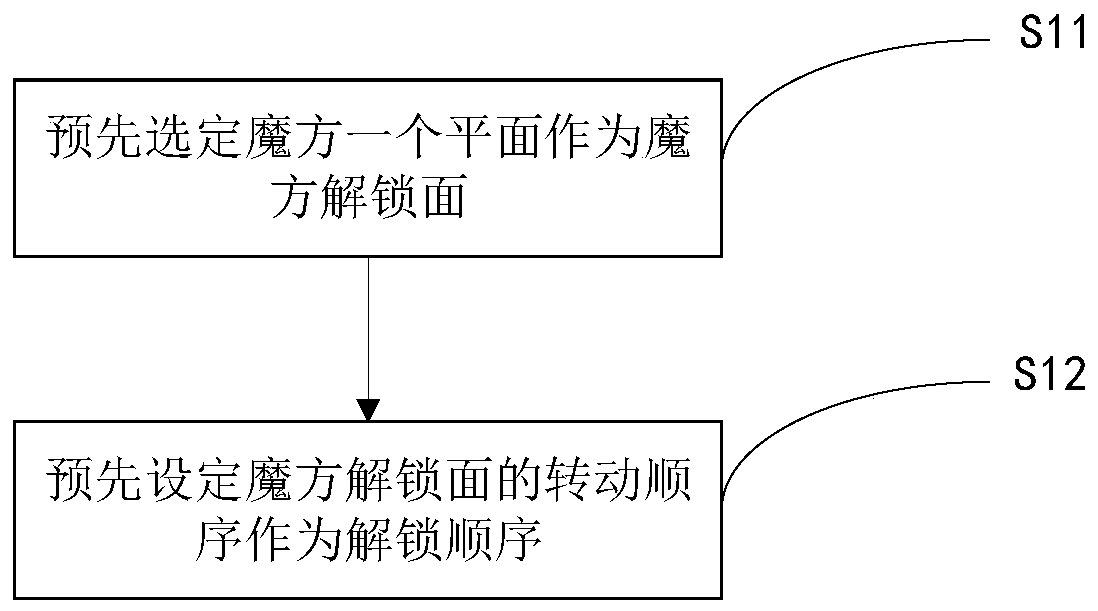
Unlocking method and device and terminal
InactiveCN106951749AImprove unlock securityImprove battery lifeDigital data authenticationComputer hardwarePassword
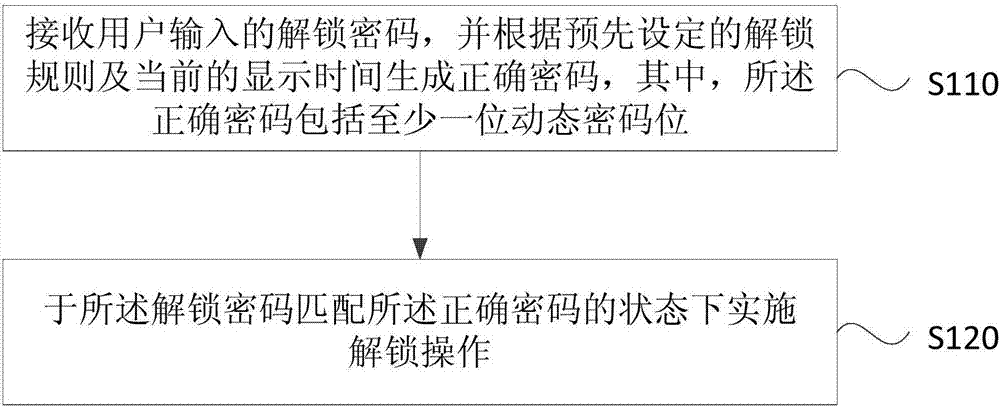
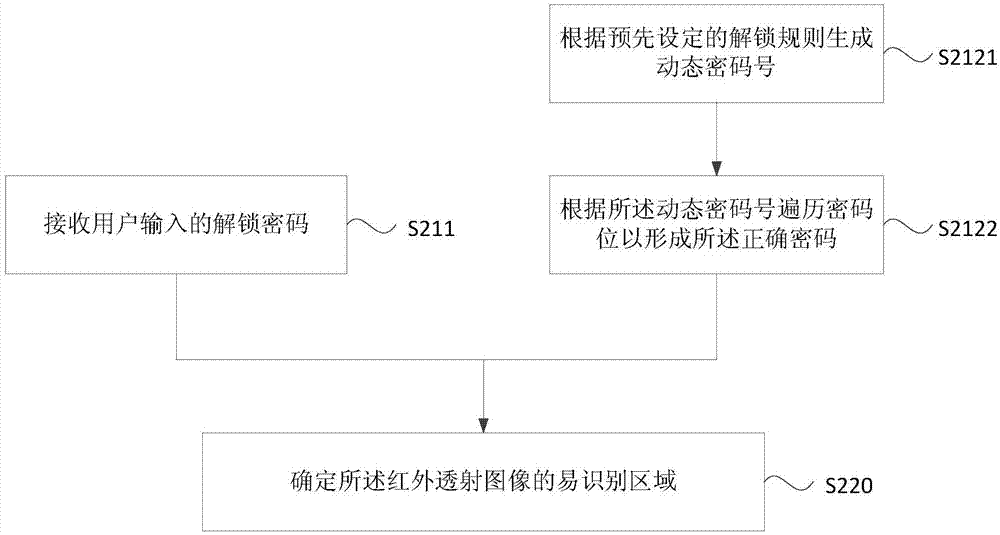
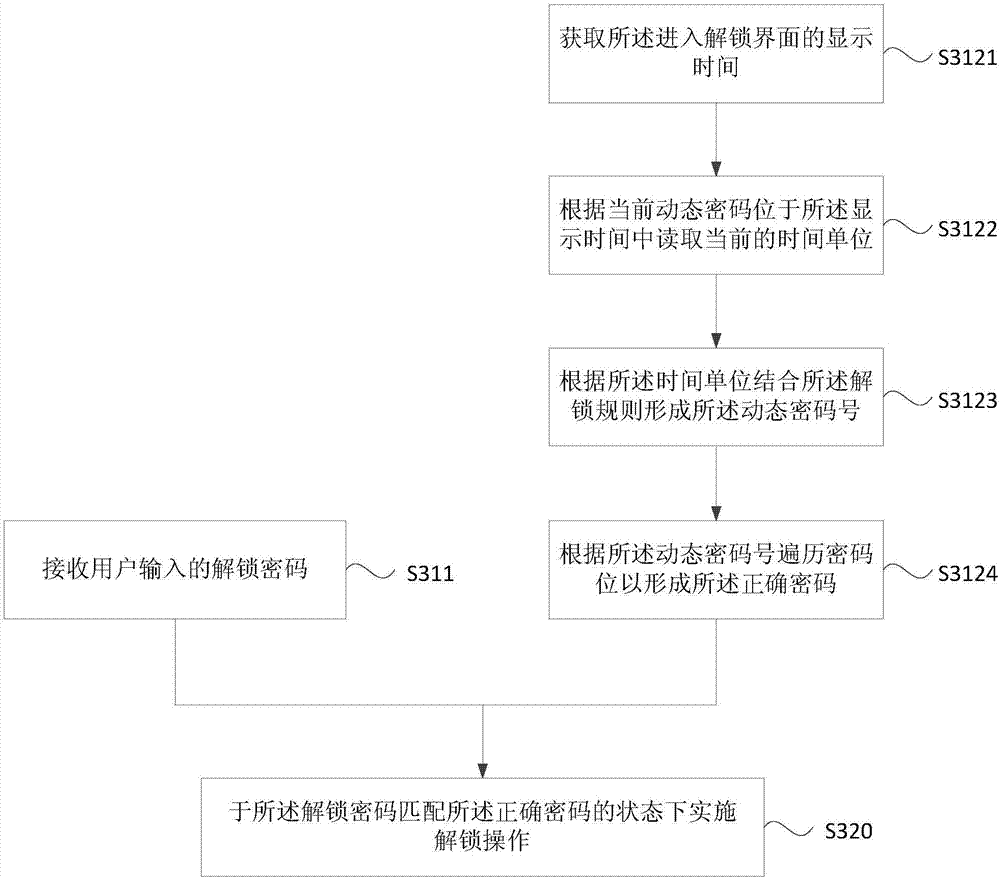
The embodiment of the invention discloses an unlocking method and device and a terminal. The method comprises the steps that an unlocking password input by a user is received, and a correct password is generated according to preset unlocking rules and current display time, wherein the correct password comprises at least one dynamic password bit; and unlocking operation is carried out under the state that the unlocking password is matched with the correct password. Specific to defects in the prior art, the unlocking method in the embodiment has the advantage of improving terminal unlocking security.
Owner:SHANGHAI YUDE TECH CO LTD
Method and device for unlocking display screen locking and terminal
InactiveCN103150120AImprove experienceImprove unlock securityInput/output processes for data processingValue setComputer terminal
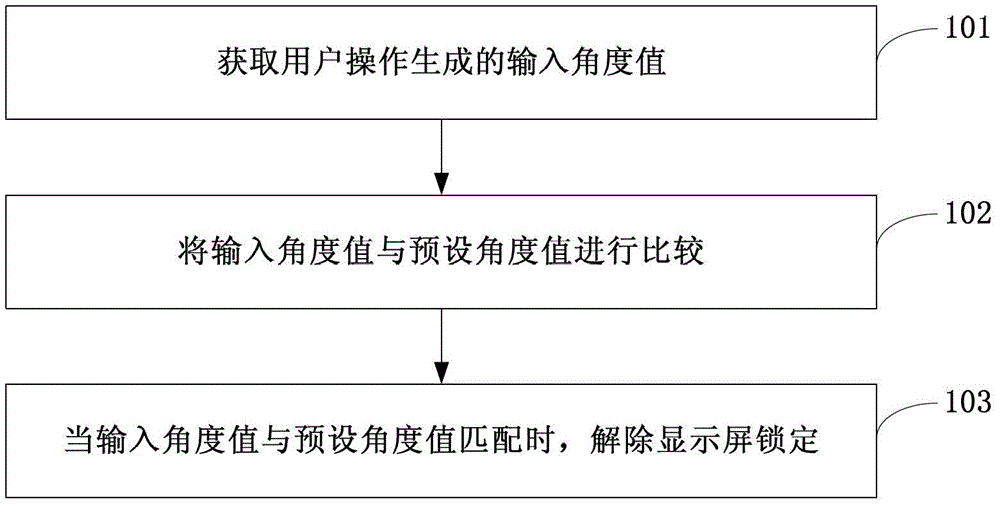
The embodiments of the invention disclose a method and a device for unlocking display screen locking and a terminal. The method comprises the following steps of: acquiring an input angle value generated by user operation; comparing the input angle value with a preset angle value; and unlocking the display screen locking when the input angle value is matched with the preset angle value. According to the embodiments of the invention, a display screen is unlocked according to an angle value set by a user, so that the user experience is good; and as the angle value can be flexibly set by the user, the security of unlocking is high.
Owner:HUAWEI TECH CO LTD
Intelligent unlocking method and system
InactiveCN106846580ASolve memory problemsAvoid the hassle of frequently using passwords to unlockIndividual entry/exit registersPasswordUser input
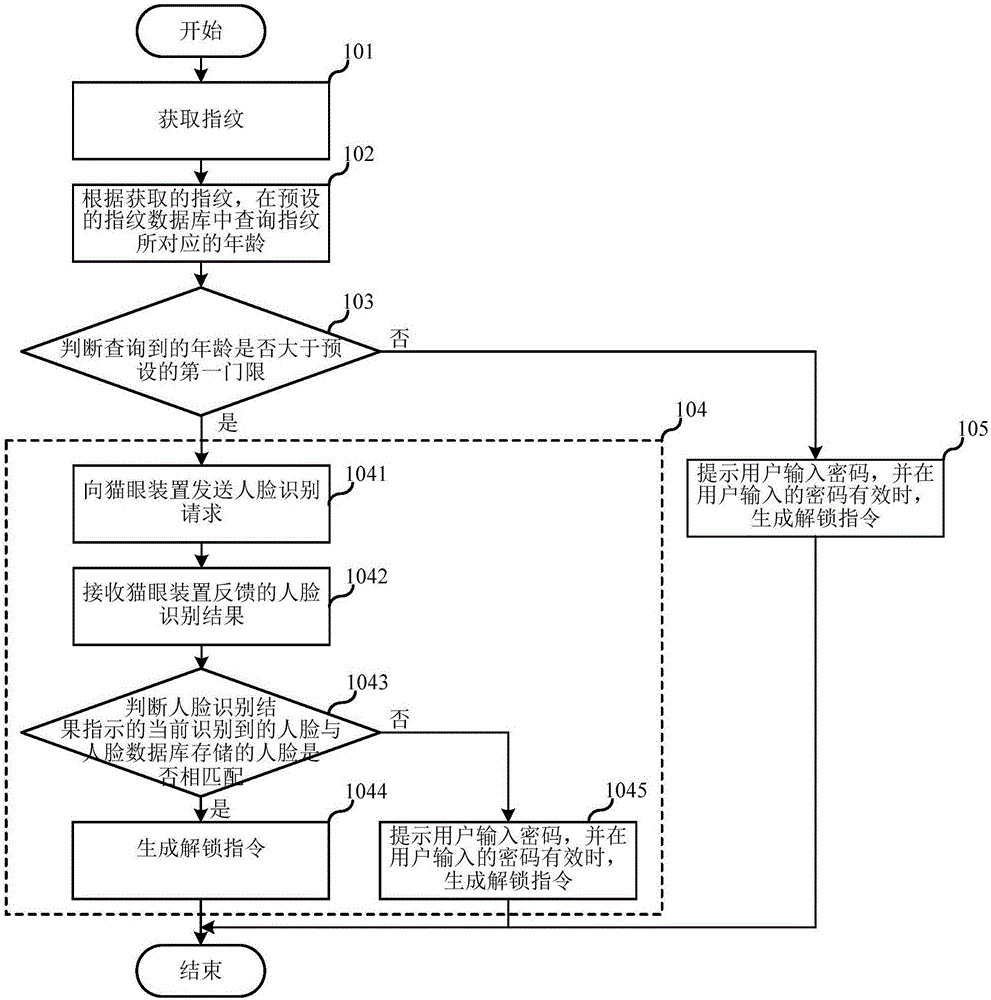
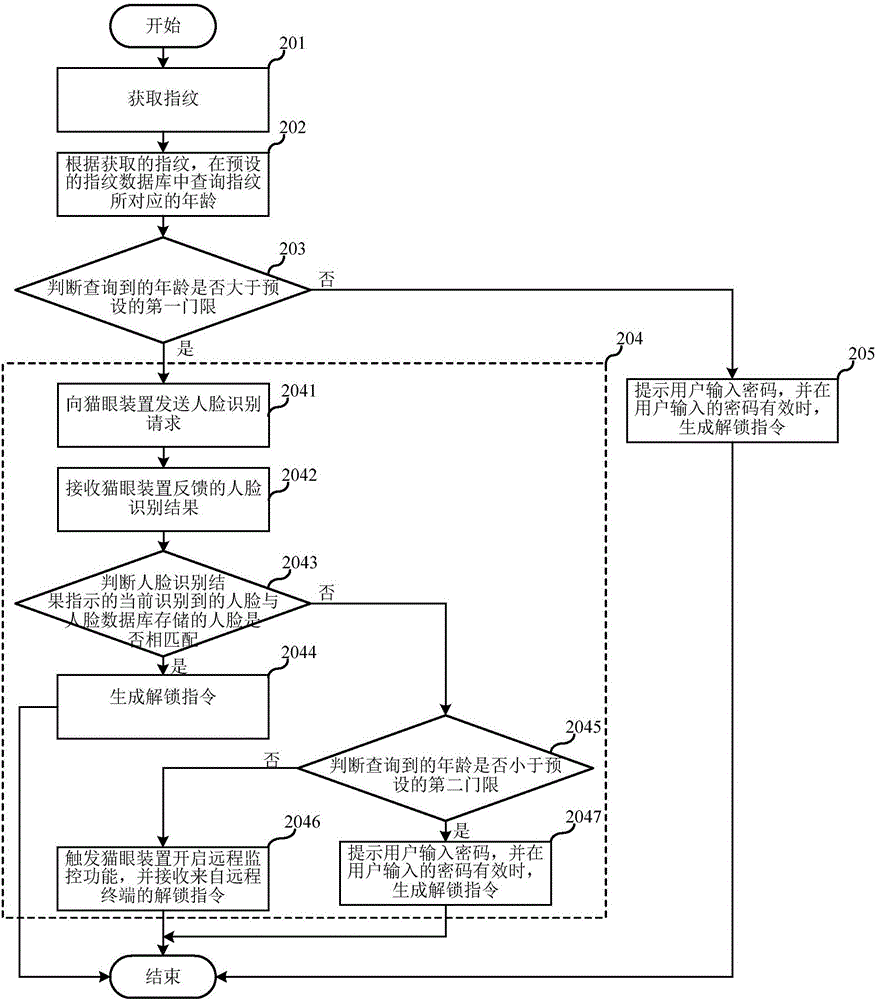
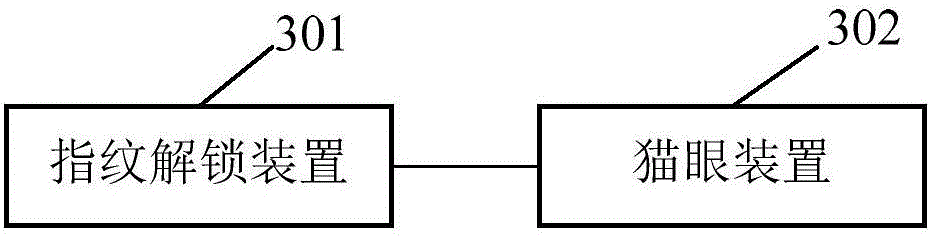
The invention relates to the technical field of home security, and discloses an intelligent unlocking method and an intelligent unlocking system. The intelligent unlocking method is applied to a fingerprint unlocking device and comprises the following steps: acquiring a fingerprint; inquiring the age corresponding to the fingerprint in a preset fingerprint database according to the acquired fingerprint; judging whether the inquired age is higher than a preset first threshold, if so, triggering a cat eye device to recognize a face, and generating an unlocking instruction when the recognized face is matched with a face stored in a face database; if the inquired age is lower than or equal to the preset first threshold, prompting a user to input a password, and generating an unlocking instruction if the password inputted by the user is effective. According to the implementation mode of the intelligent unlocking method, the fingerprint recognition is combined with the face recognition or password authentication, then the unlocking safety is further improved; the double unlocking schemes are provided, so that the problem of difficulty in memorizing the password of the aged is solved, and meanwhile, the success rate of unlocking is increased at a certain degree.
Owner:EQUES TECH
Iris unlocking system and method thereof
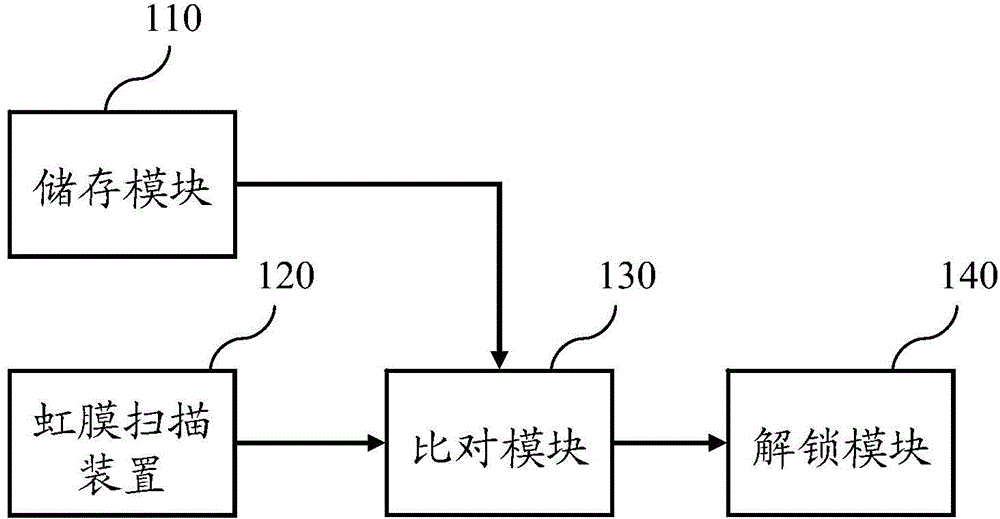
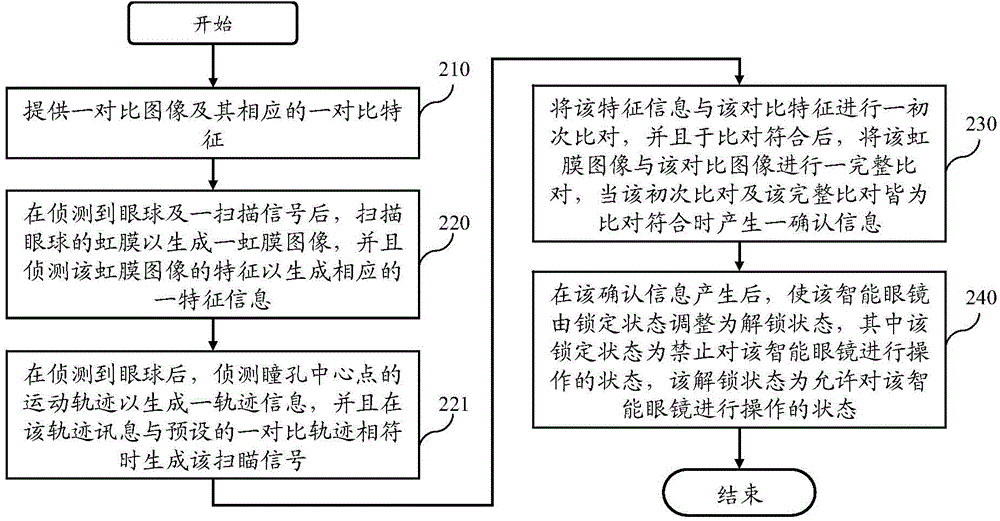
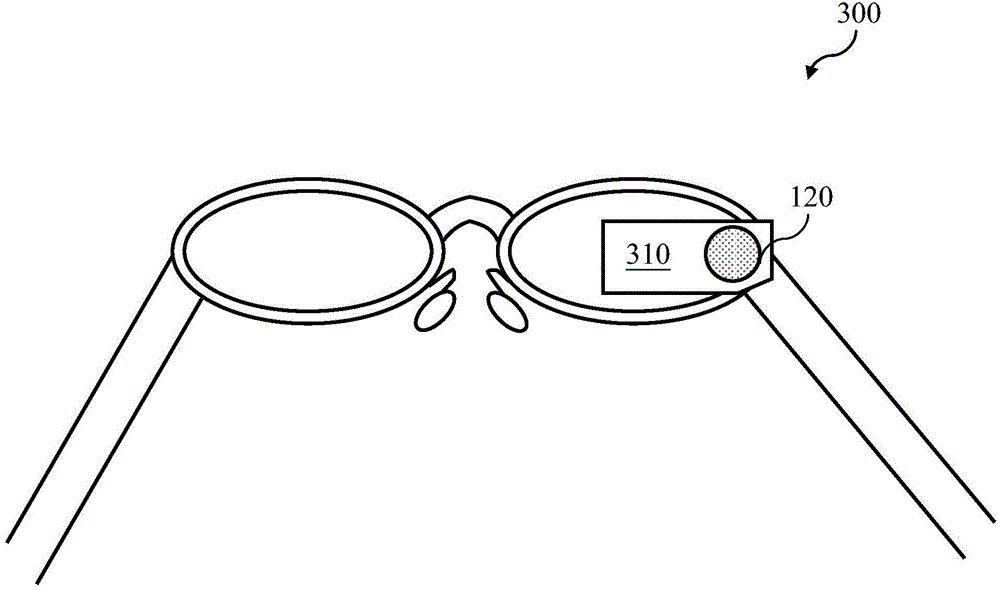
The invention discloses an iris unlocking system and a method of the iris unlocking. By detecting the eyeball and a scanning signal, iris of the eyeball is scanned to generate an iris image, characters of the iris image are detected to generate corresponding character information, so that a first time comparison between the character information and per-set contrast characters can be conducted, then a complete comparison between the iris image and a contrast image is conducted after the fist time comparison is coincident, when the two times of comparisons both are coincident, confirm information is generated to enable intelligent glasses to adjust to an unlocking state, so that the technical effect of improving the unlocking safety of the intelligent glasses can be achieved.
Owner:INVENTEC PUDONG TECH CORPOARTION +1
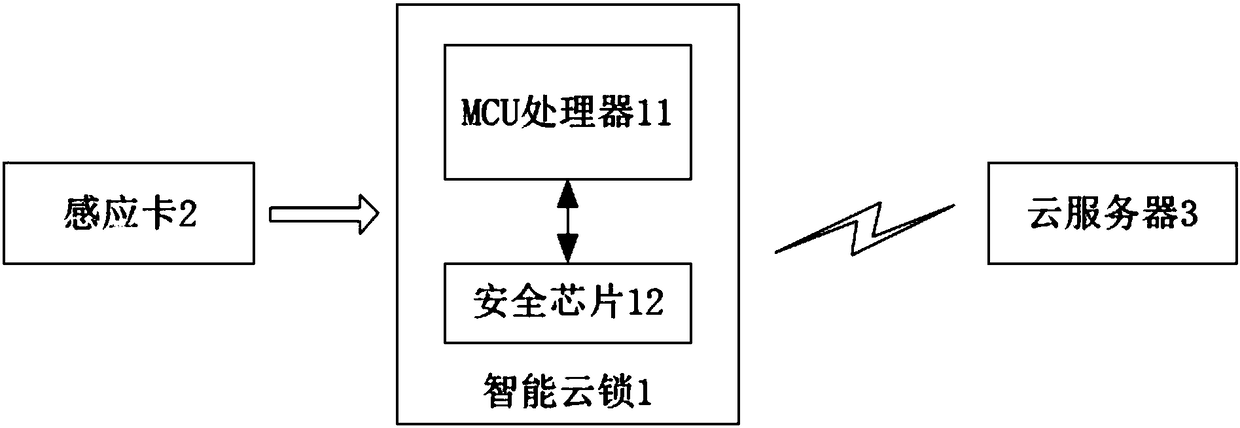
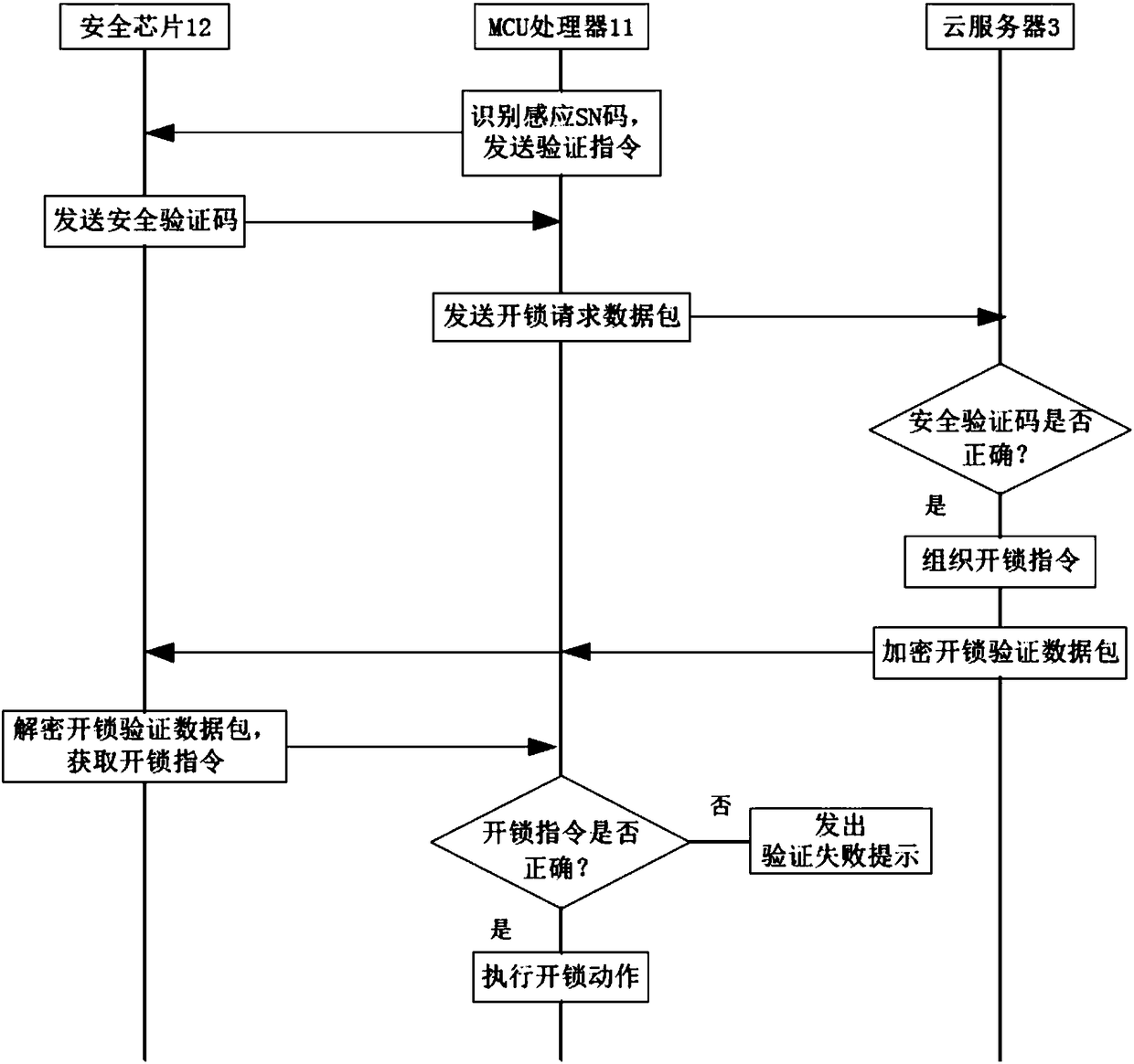
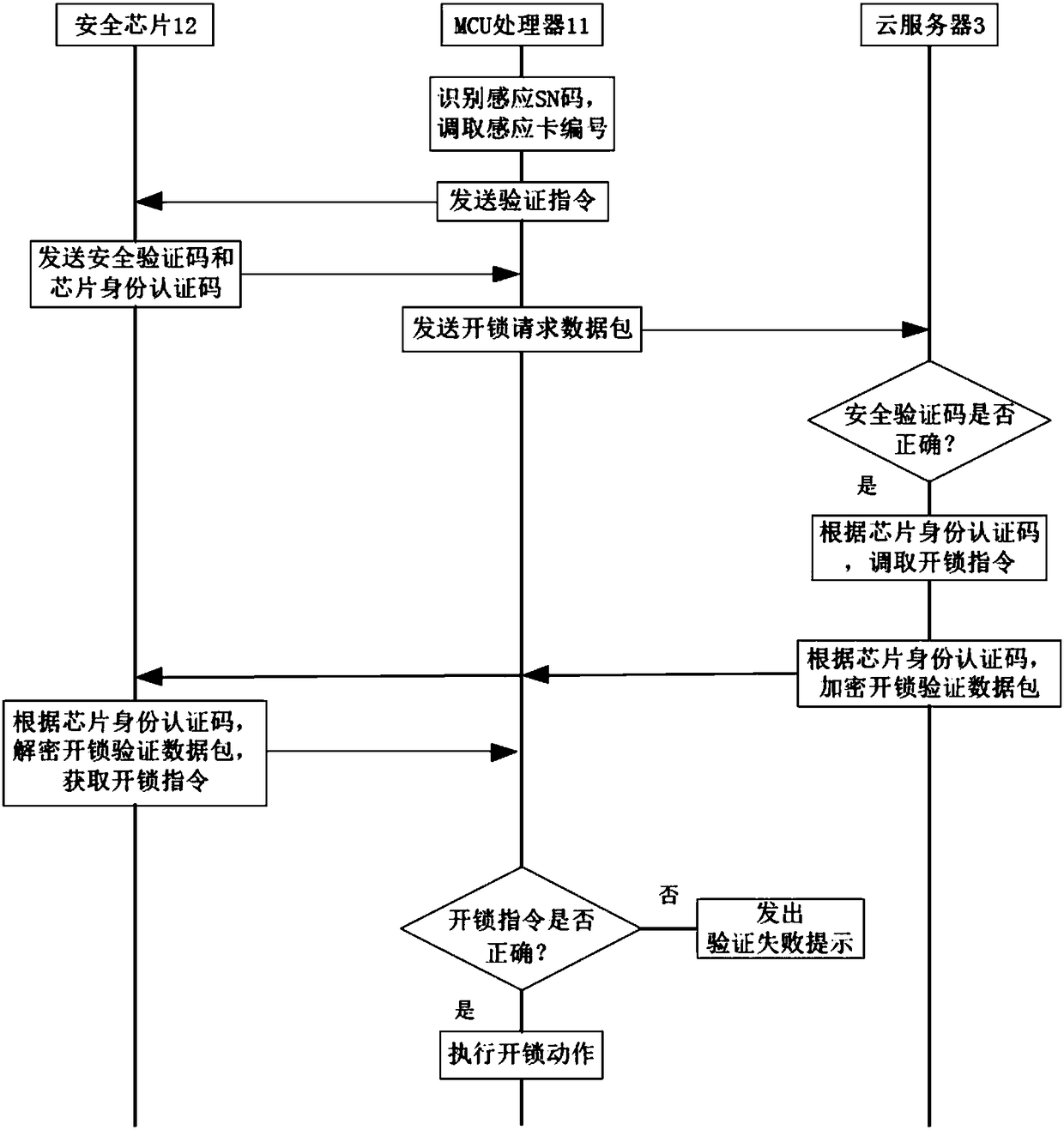
Method and system for encrypting hardware based on proximity card unlocking, and smart cloud lock
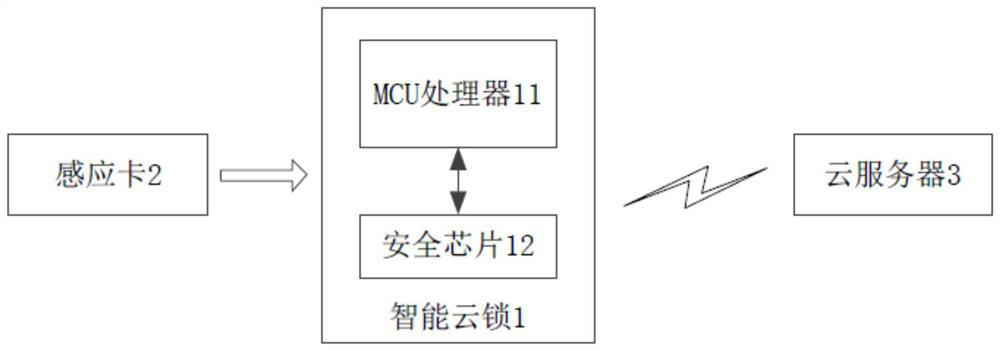
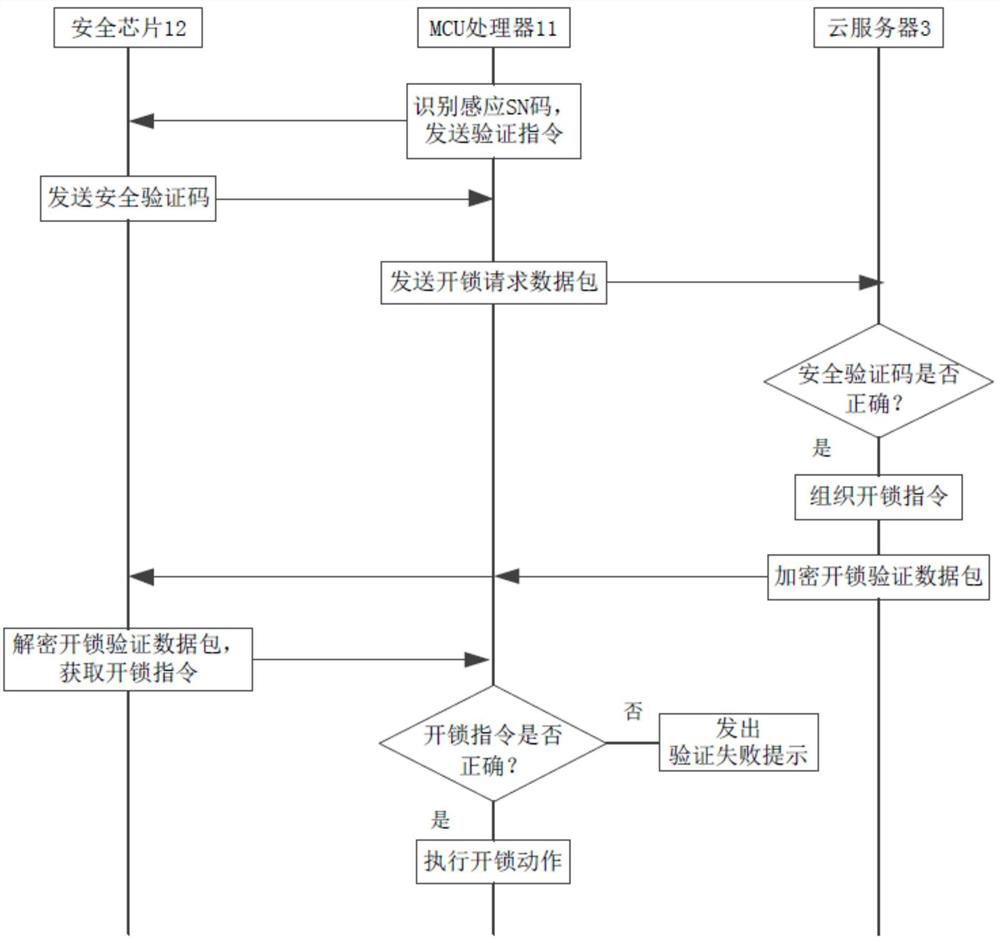
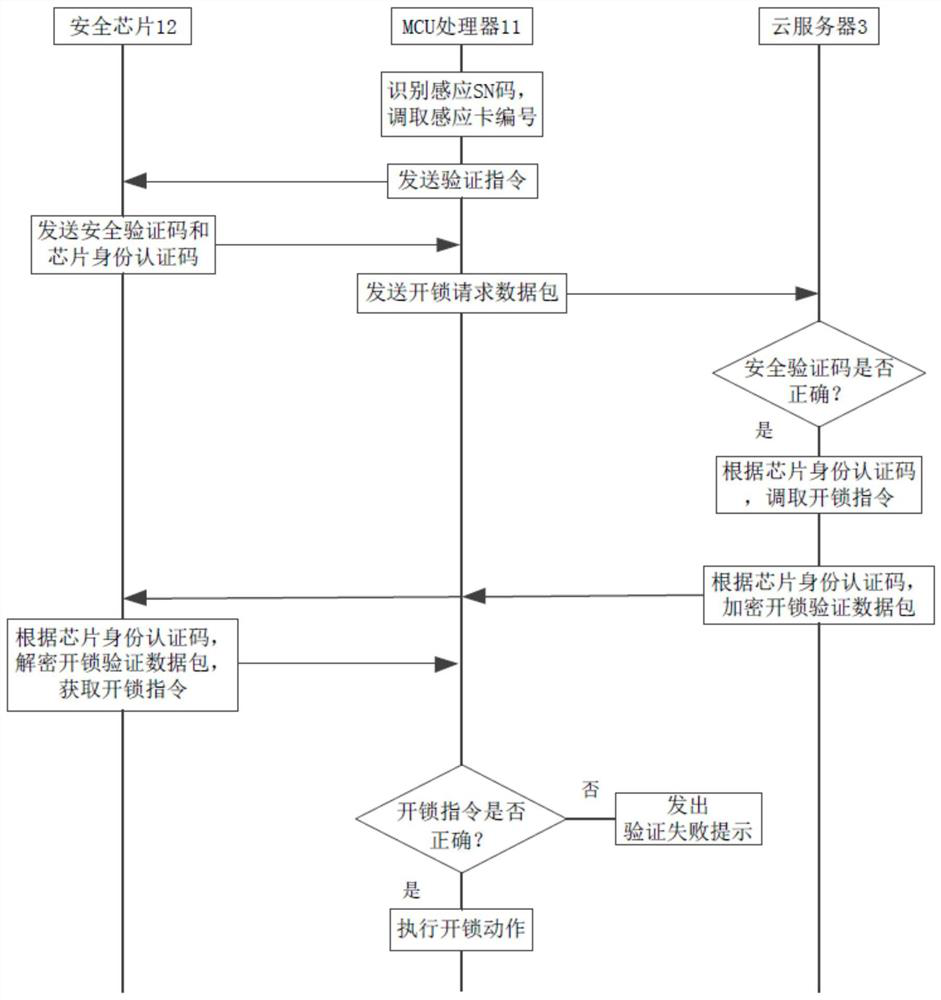
ActiveCN108171830AAvoiding Vulnerable Theft IssuesImprove unlock securityIndividual entry/exit registersTransmissionNetwork packetCloud server
The invention discloses a method and a system for encrypting hardware based on proximity card unlocking, and a smart cloud lock. The method comprises the following steps: step A, when a proximity cardcontacts the smart cloud lock, the MCU processor of the smart cloud lock identifies a sensing SN code in the proximity card, and sends a verification instruction to a security chip; step B, the security chip receives the verification instruction, and sends a security verification code to the MCU processor; and step C, the MCU processor packs the acquired sensing SN code and the security verification code into an unlocking request data packet, and sends the unlocking request data packet to a cloud server. An encrypted unlocking instruction sent by the cloud server, and is decrypted by the security chip, so the unlocking instruction is prevented from being stolen, the anti-theft performance is improved, and a problem that the unlocking instruction recorded in the proximity card can be easily stolen is avoided.
Owner:HUITAILONG DECORATION MATERIAL YUEXIU DIST GUANGZHOU
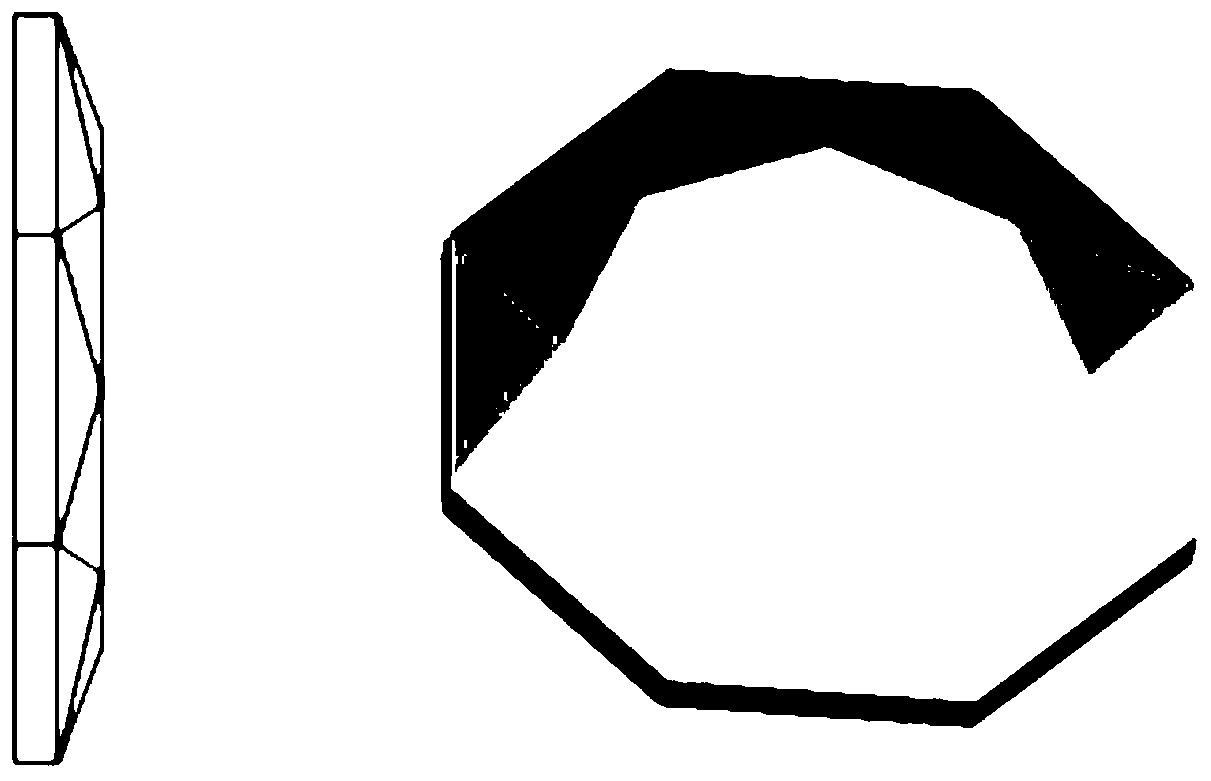
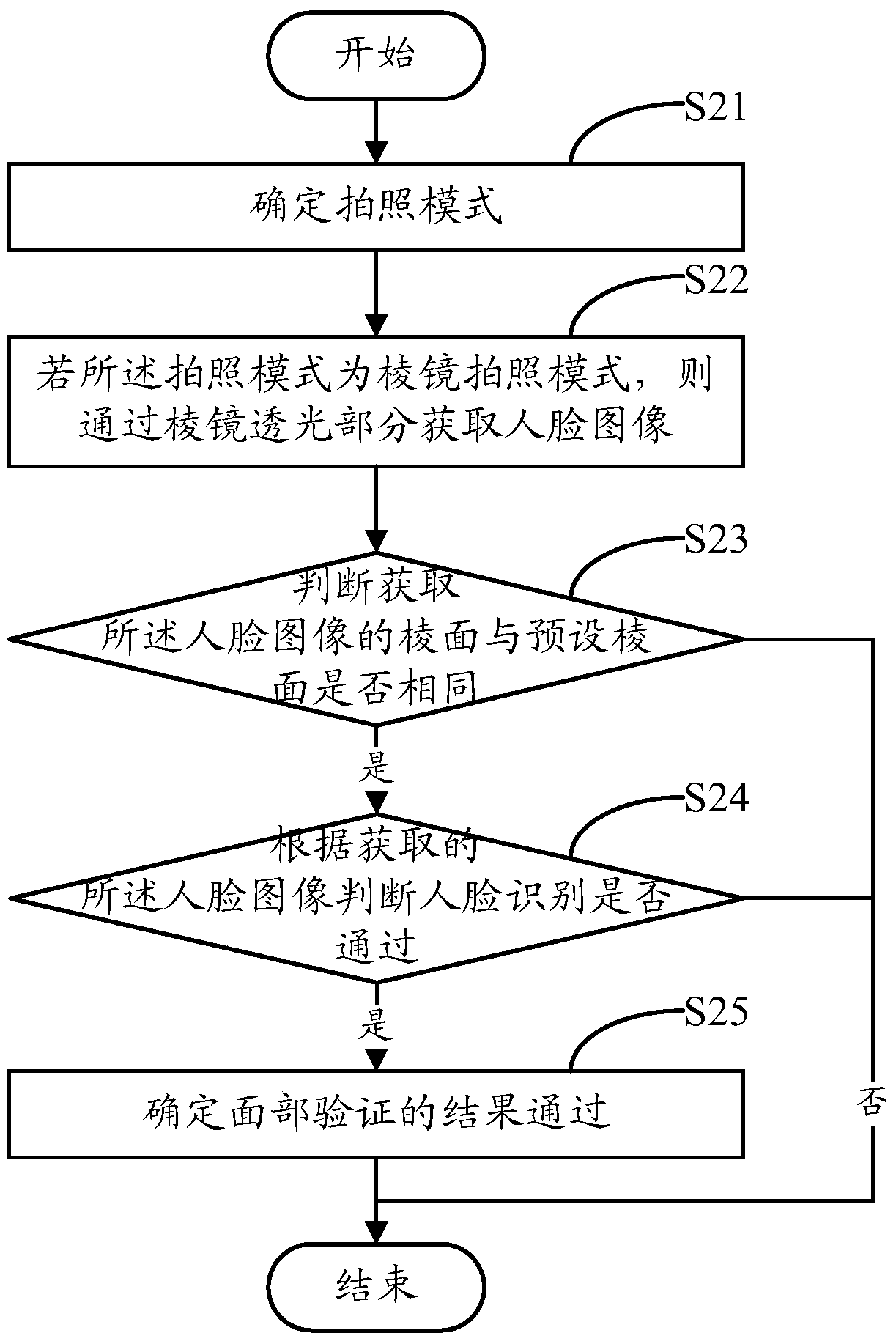
Face verification method and face verification device
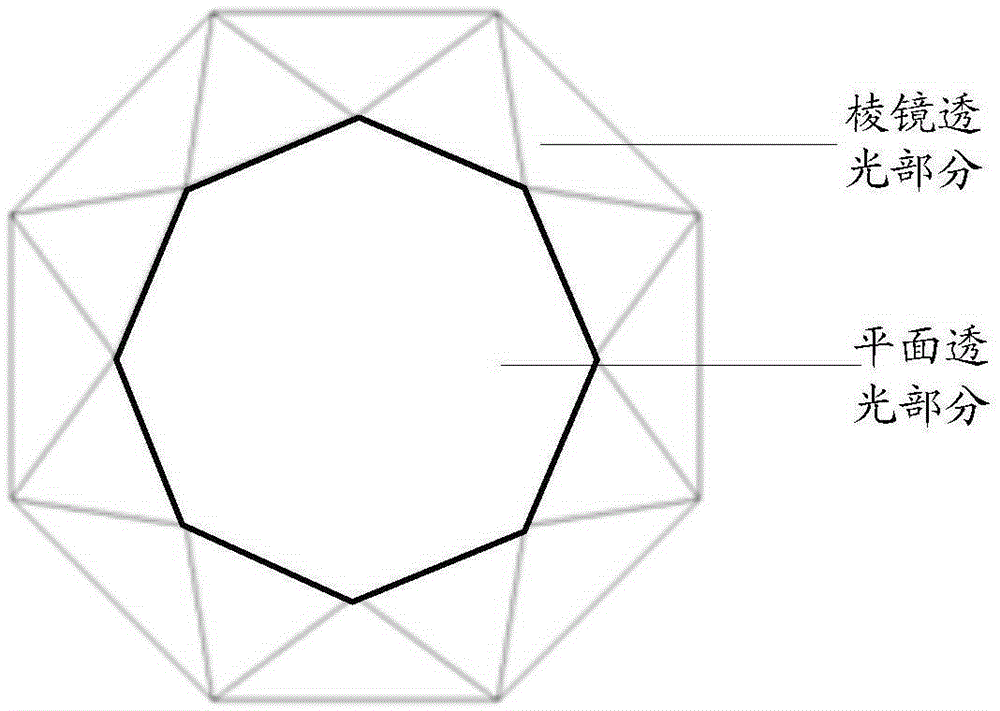
ActiveCN105426886AImprove securityImprove unlock securityCharacter and pattern recognitionComputer graphics (images)Validation methods
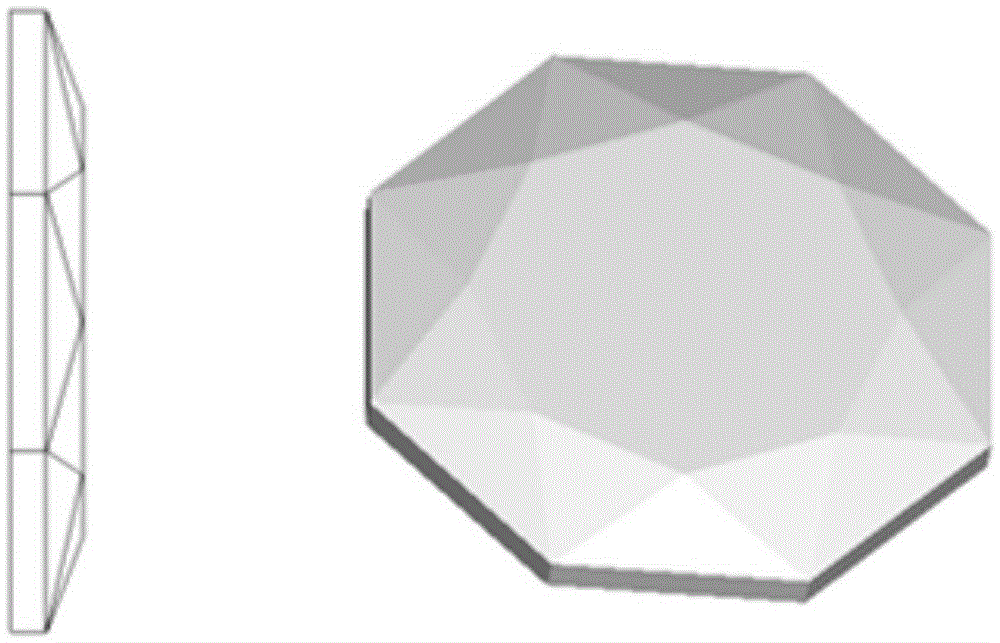
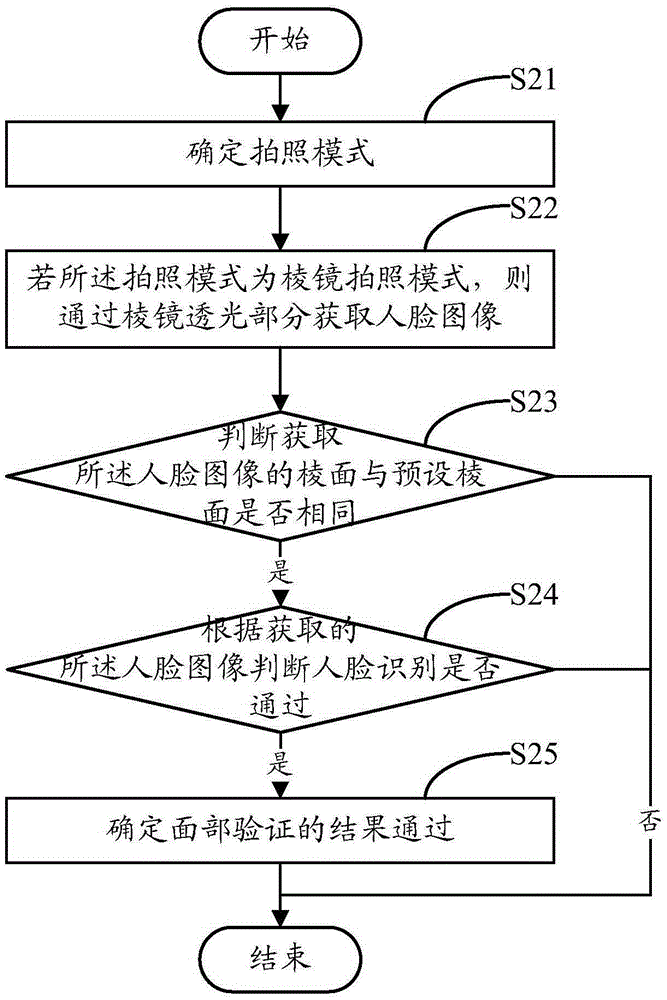
The embodiment of the invention discloses a face verification method. The face verification method is applied to a terminal with a camera, wherein a lens of the camera comprises a plane light transmission portion and a prism light transmission portion; the prism light transmission portion includes at least two prismatic planes. The face verification method includes: determining a shooting mode; if the shooting mode is a prism shooting mode, acquiring a face image through the prism light transmission portion; and determining the result of face verification is qualified if the prismatic plane of the acquired face image is identical to the preset prismatic plane and if the acquired face image determines that the face identification is qualified. Correspondingly, the embodiment of the invention also discloses a face verification device. The face verification method and the face verification device can improve the safety of a terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Information processing method and electronic equipment
ActiveCN104951717AEliminate technical issues with poor securityImprove unlock securityInternal/peripheral component protectionInput/output processes for data processingInformation processingInduction motor
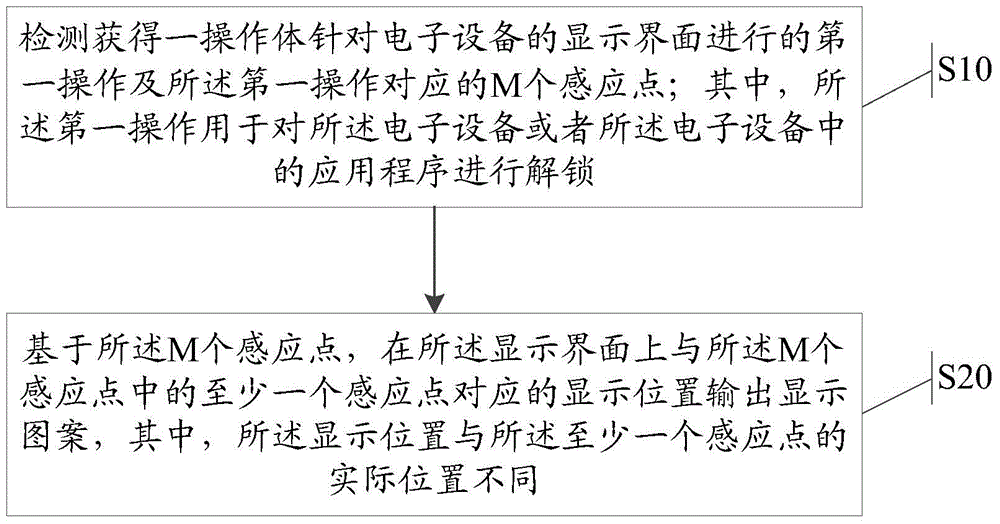
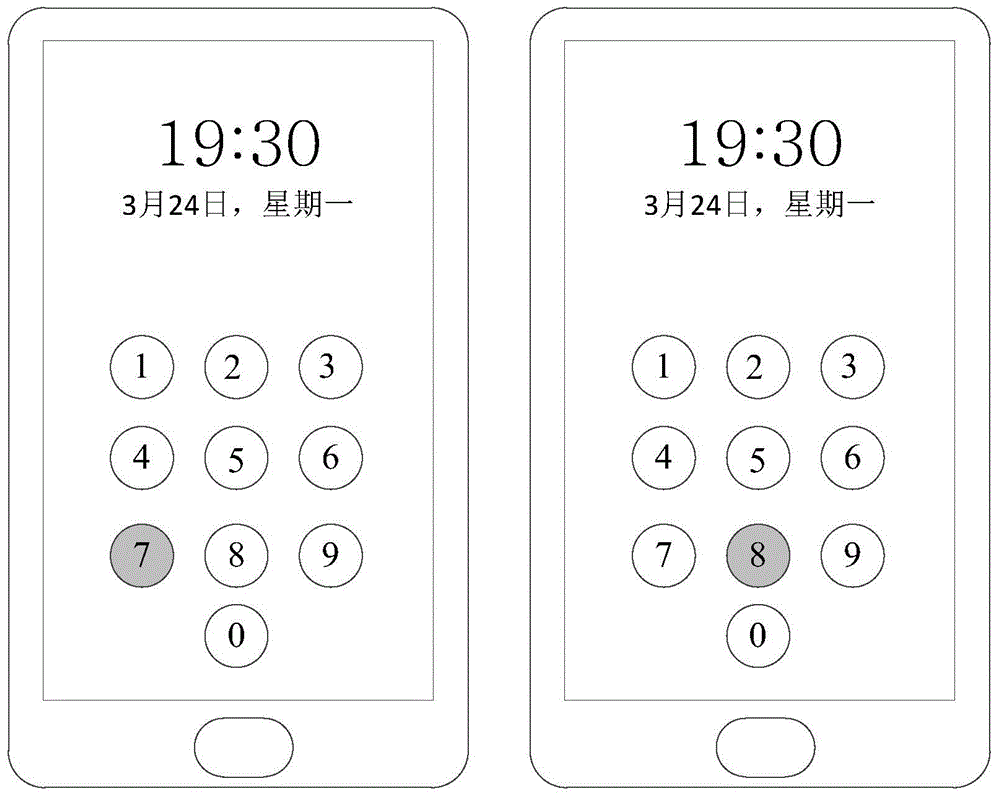
The invention discloses an information processing method and electronic equipment. The method comprises that first operation on a display interface of the electronic equipment by an operating body and M induction points corresponding to the first operation are detected and obtained, wherein the first operation is used for carrying out unlocking on the electronic equipment or an application program of the electronic equipment; based on the M induction points, a display pattern is output on the display interface at the display position corresponding to at least one induction point from the M induction points, wherein the display position is different from the actual position of at least one induction point.
Owner:LENOVO (BEIJING) LTD
Unlocking method based on holographic projection, password lock and system
ActiveCN108109246ANot easy to be stolenImprove unlock securityIndividual entry/exit registersProjection imageKey images
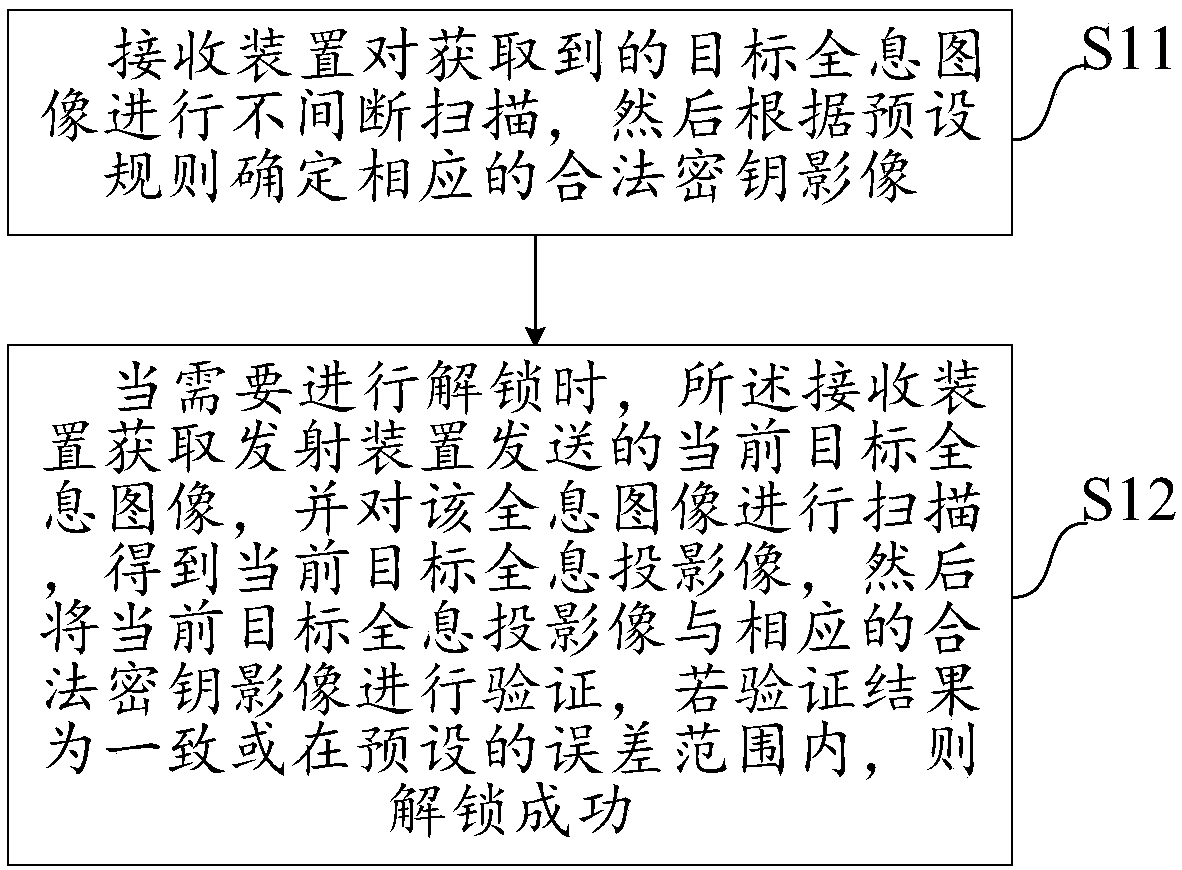
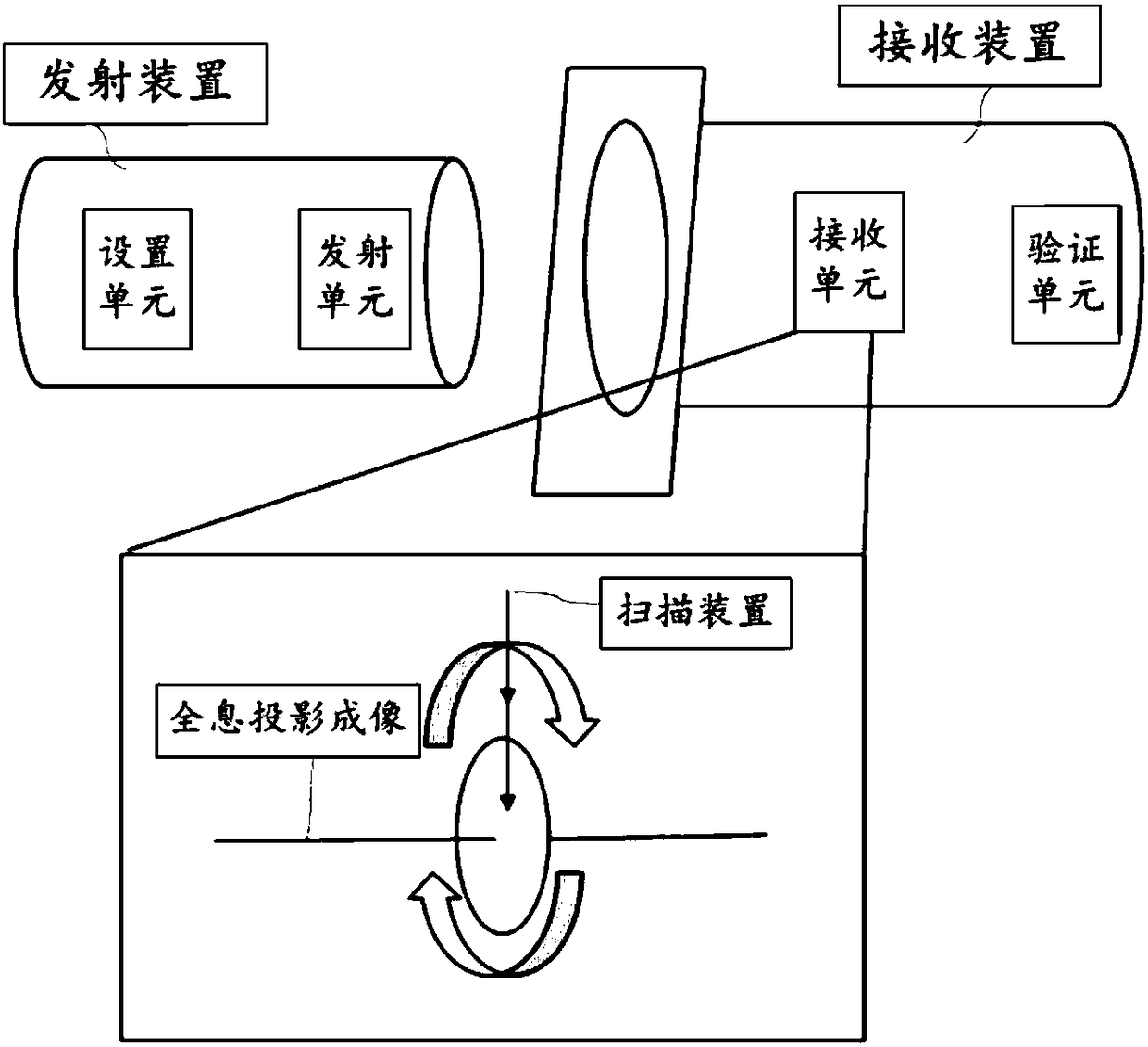
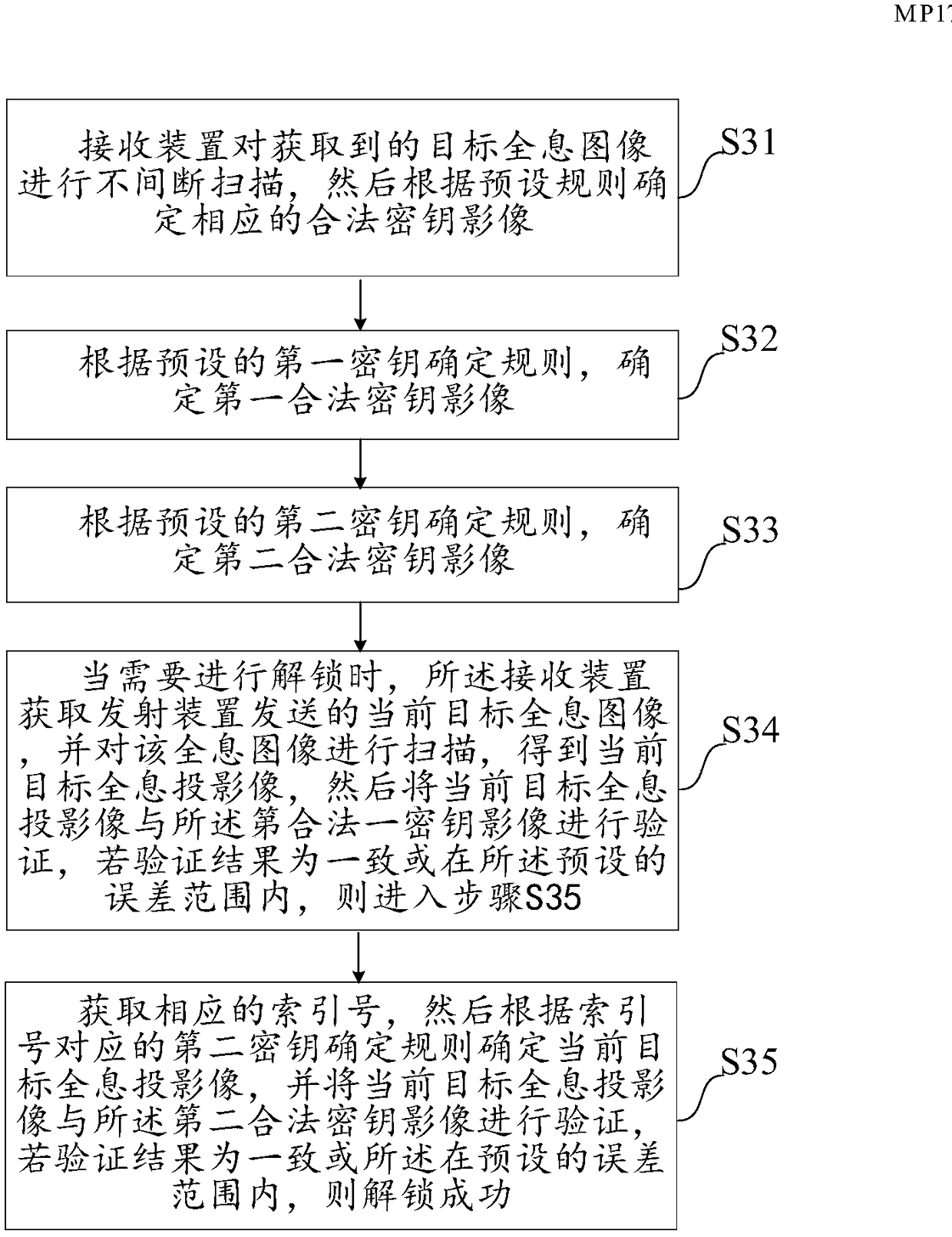
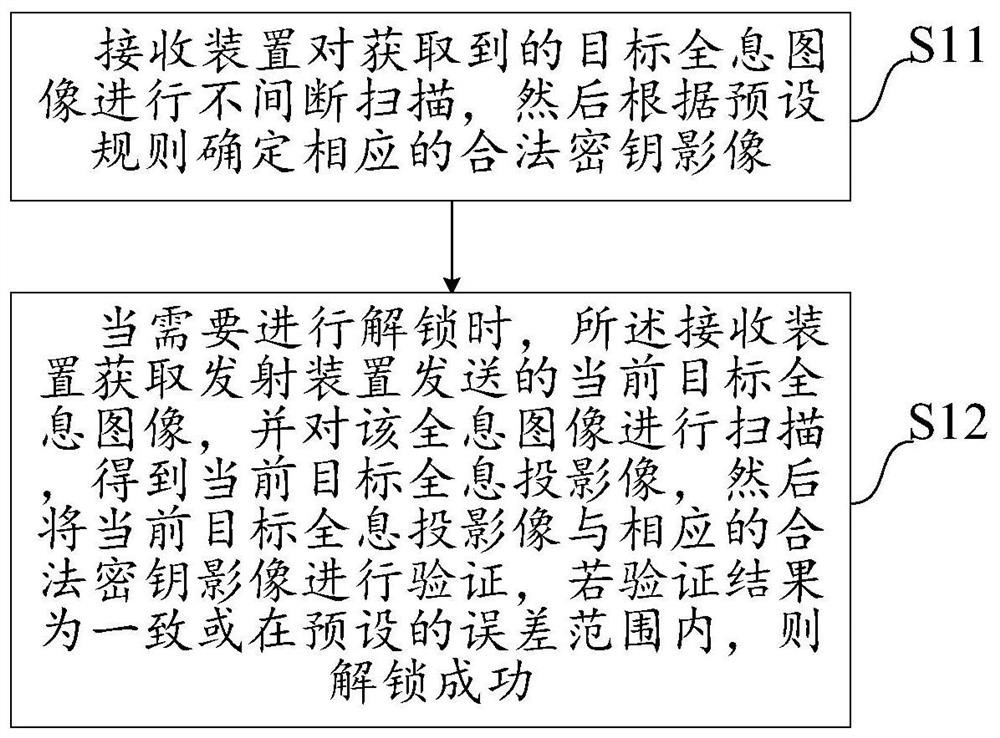
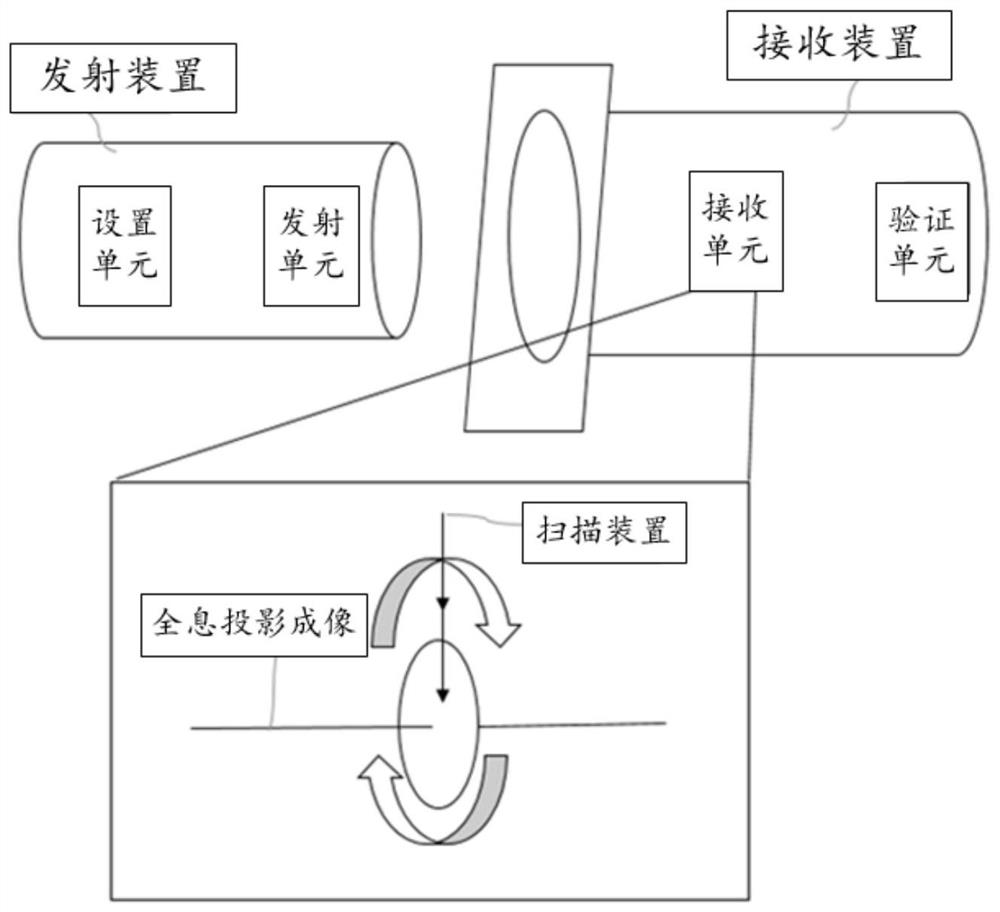
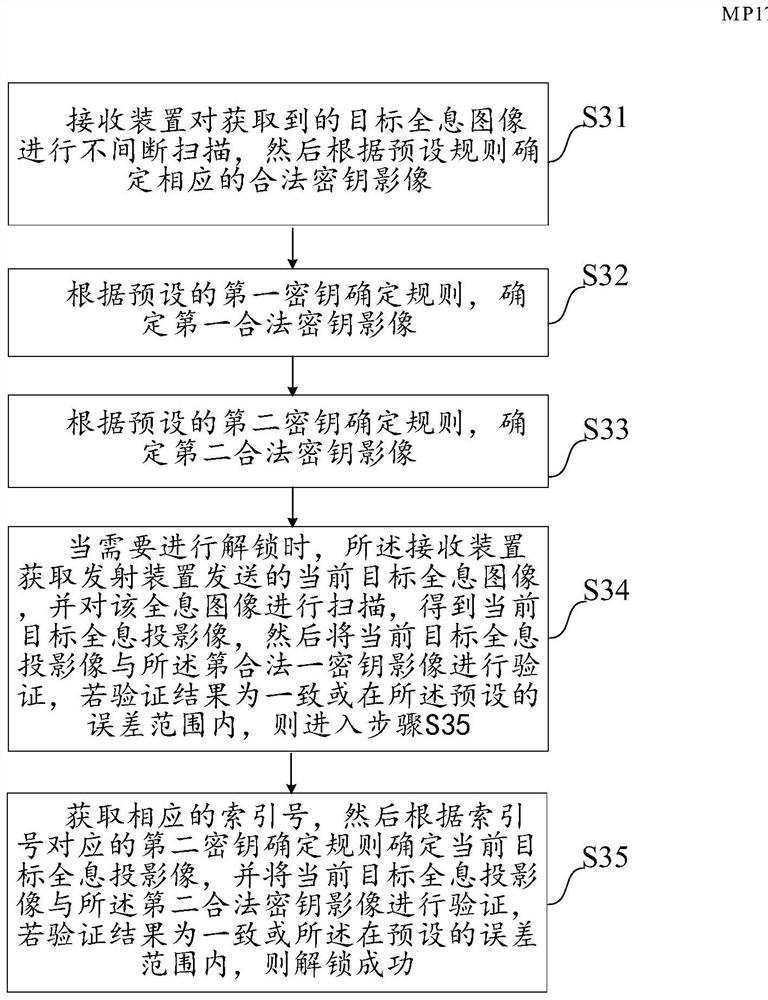
The invention discloses an unlocking method based on holographic projection, a password lock and a system. The method comprises the following steps: performing non-intermittent scanning on a receivedtarget holographic image by a receiving device, and confirming a corresponding legal key image according to preset rules; when unlocking is needed, acquiring a current target holographic image transmitted from a transmitting device by the receiving device, scanning the holographic image so as to obtain a current target holographic projection image, verifying the current target holographic projection image with a corresponding legal key image, and unlocking successfully if verification results are accordant or within a preset error range. By adopting the unlocking method based on holographic projection, unlocking can be implemented by only using key images which are set in advance, unlocking security can be improved through key image unlocking, and meanwhile inconvenience and potential danger caused by key loss in the prior art can be avoided.
Owner:GUANGDONG HONGQIN COMM TECH CO LTD
Safe deposit box capable of unlocking by using fingerprints
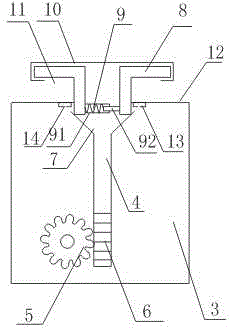
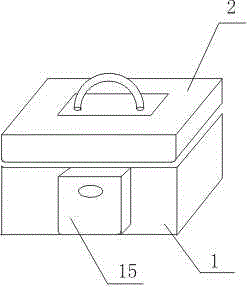
ActiveCN104358492APlay a limiting roleCan't exerciseElectric permutation locksIndividual entry/exit registersStructural engineeringMechanical engineering
The invention discloses a safe deposit box capable of unlocking by using fingerprints. The safe deposit box comprises a box body and a box cover hinged to the box body, wherein a cuboid groove is formed in the upper end of one side wall of the box body. The safe deposit box further comprises a lock body arranged in the cuboid groove, and the lock body comprises a toothed gear and a toothed bar engaged with the toothed gear. The safe deposit box further comprises a V-shaped seat fixed at the upper end of the toothed bar and two L-shaped lock bars arranged in the cuboid groove in a sliding mode; each L-shaped lock bar comprises a vertical section and a horizontal section, each horizontal section is connected with the top of the corresponding vertical section, the two L-shaped lock bars are symmetrically arranged, and each horizontal section extends towards the two sides; the vertical sections of the two L-shaped lock bars are connected through an elastic element, and the horizontal sections of the two L-shaped lock bars are positioned outside the cuboid groove. According to the safe deposit box, through the arrangement of a fingerprint recognition system and the lock body, the effect of opening the safe deposit box is achieved, and the safe deposit box is high in security and convenient to use by adopting fingerprints for unlocking.
Owner:四川金利邦智能科技股份有限公司
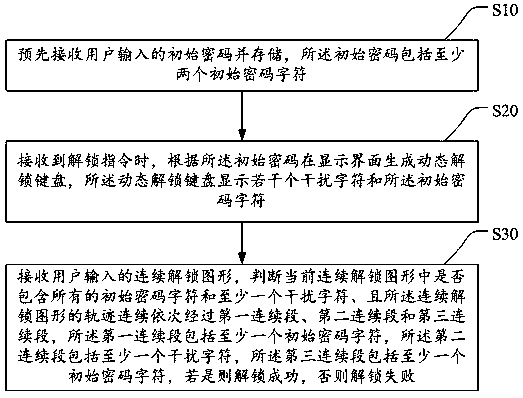
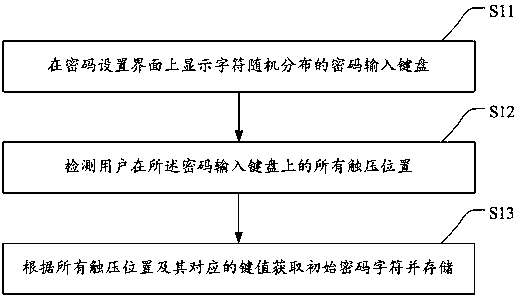
Graph unlocking method and device and storage medium
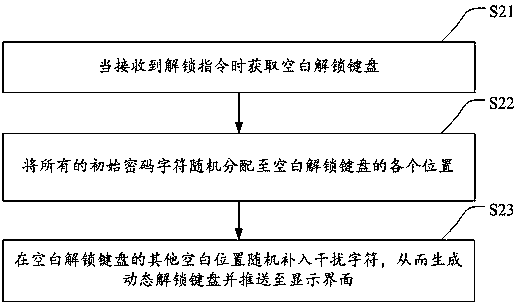
The invention discloses a graph unlocking method and device and a storage medium. The method comprises the steps of receiving initial passwords input by a user in advance and storing the initial passwords; generating a dynamic unlocking keyboard on a display interface according to the initial passwords when an unlocking instruction is received, and displaying a plurality of interference charactersand initial password characters on the dynamic unlocking keyboard; receiving a continuous unlocking graph input by the user, and judging whether or not the current continuous unlocking graph includesall the initial password characters and at least one interference character, wherein the track of the continuous unlocking graph sequentially passes through a first connecting section, a second connecting section and a third connecting section, the first connecting section comprises at least one initial password character, the second connecting section comprises at least one interference character, and the third connecting section comprises at least one initial password character; if yes, achieving unlocking successfully. The unlocking graphs input by the user during different times of unlocking are different due to the dynamic unlocking keyboard, and unlocking can only be achieved successfully through the interference characters, so that the unlocking safety is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Fingerprint unlocking method and apparatus
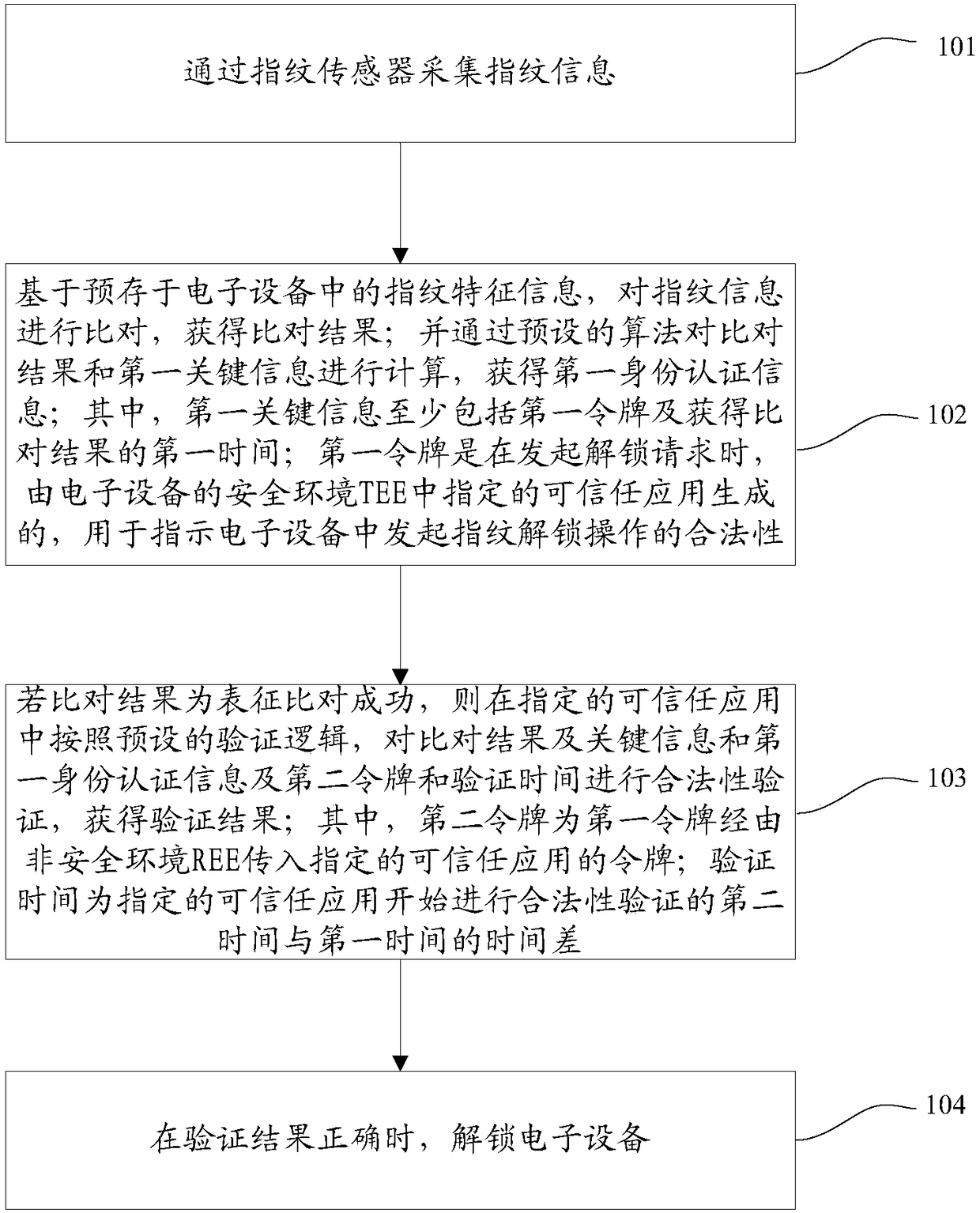
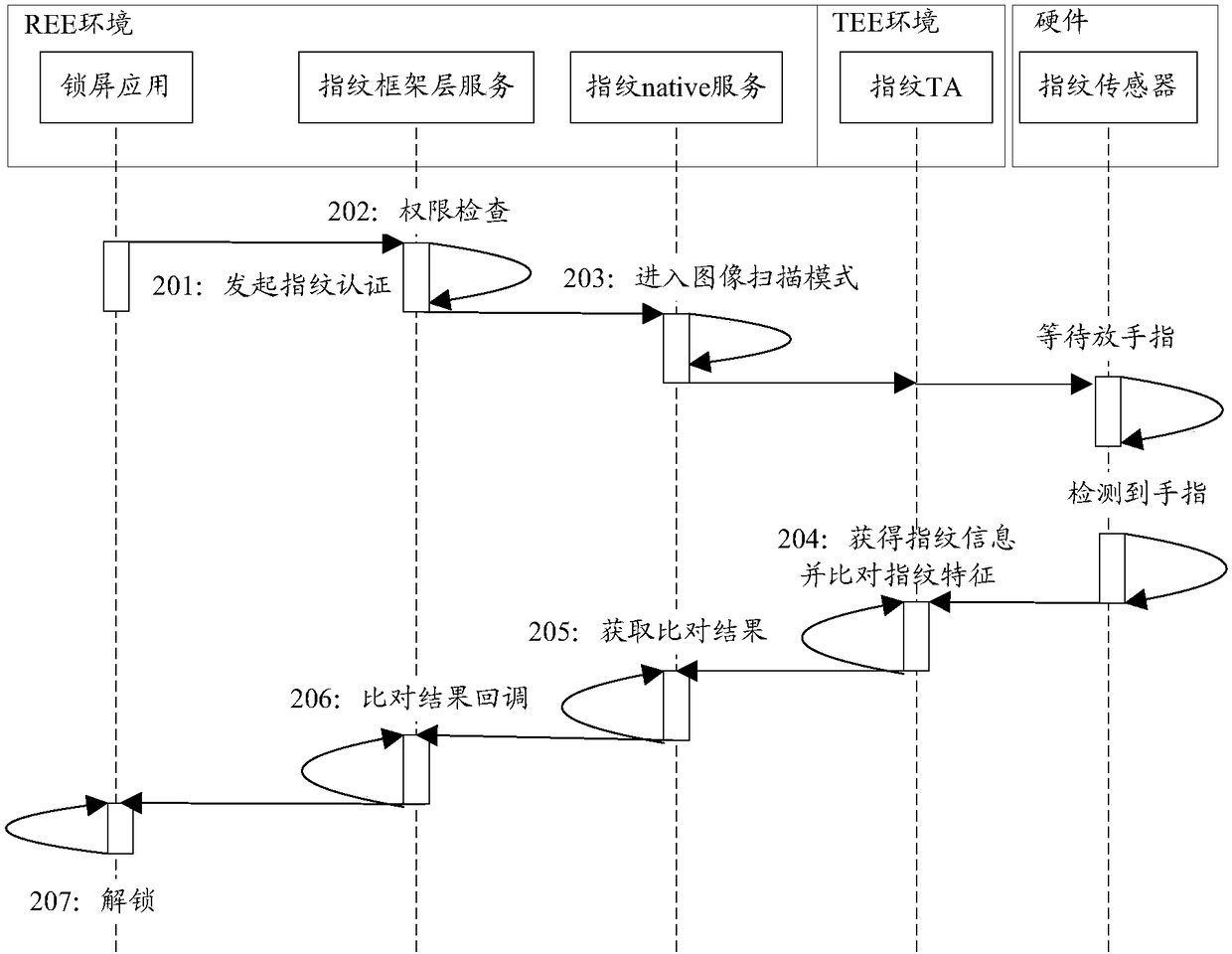
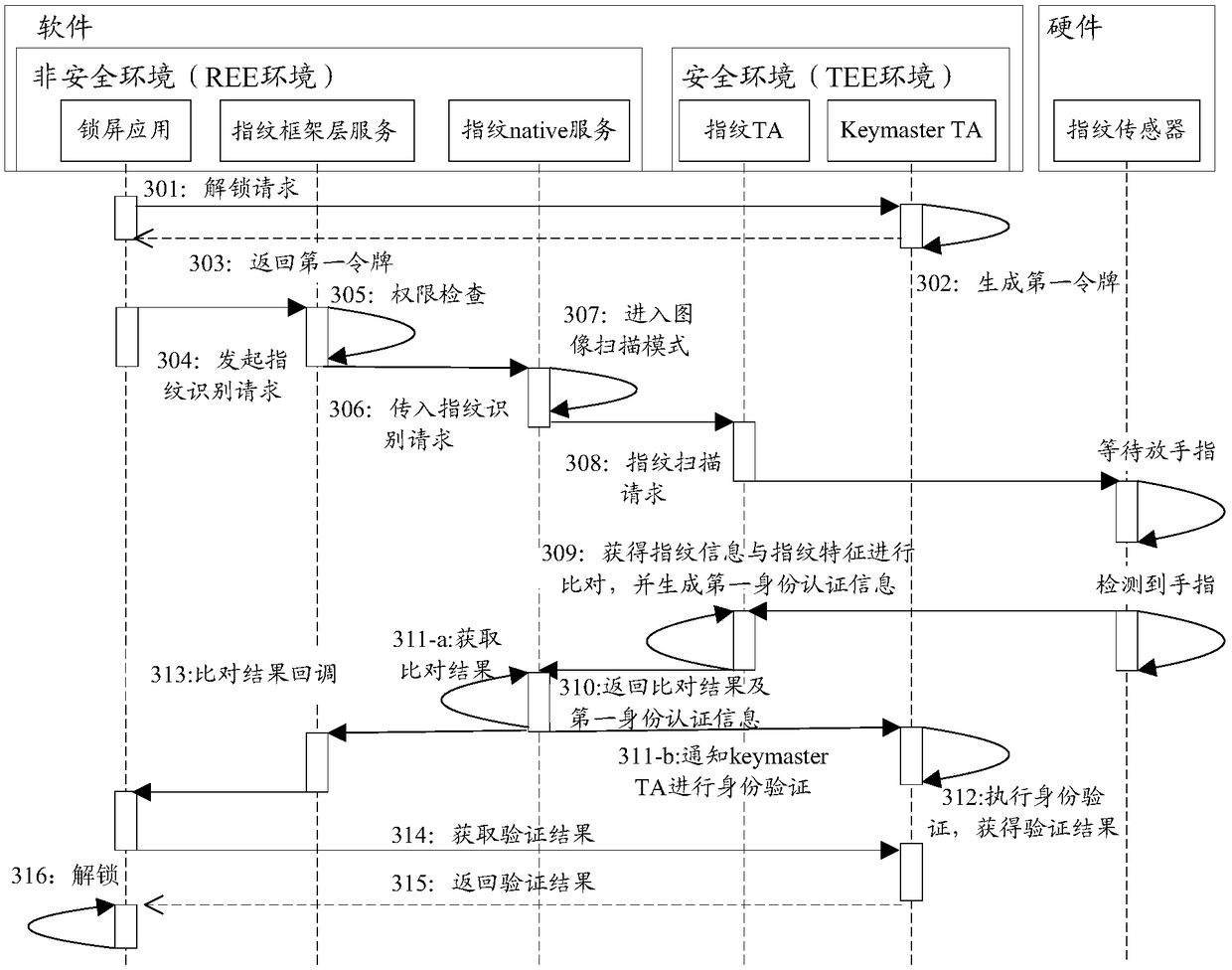
ActiveCN108563934AImprove unlock securityAvoid the risk of tamperingDigital data authenticationMatching and classificationFingerprintAuthentication information
The invention discloses a fingerprint unlocking method and apparatus, which is used for solving the technical problem of low fingerprint unlocking security in the prior art. The method comprises the steps of collecting fingerprint information through a fingerprint sensor; comparing the fingerprint information based on fingerprint feature information to obtain a comparison result; calculating the comparison result and first key information through a preset algorithm to obtain first identity authentication information, wherein a first token is generated by a trusted application specified in a TEE of an electronic device during initiation of an unlocking request, and is used for indicating the legality of initiating fingerprint unlocking operation in the electronic device; if the comparison result represents that the comparison succeeds, performing legality verification on the first identity authentication information, a second token and verification time according to preset verificationlogic in the specified trusted application, thereby obtaining a verification result, wherein the second token is a token generated after the first token is transmitted into the specified trusted application through the REE; and when the verification result is correct, unlocking the electronic device.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
Unlocking method and device, and electronic equipment
ActiveCN105631301AImprove unlock securityControl usage timeDigital data authenticationHabitElectric equipment
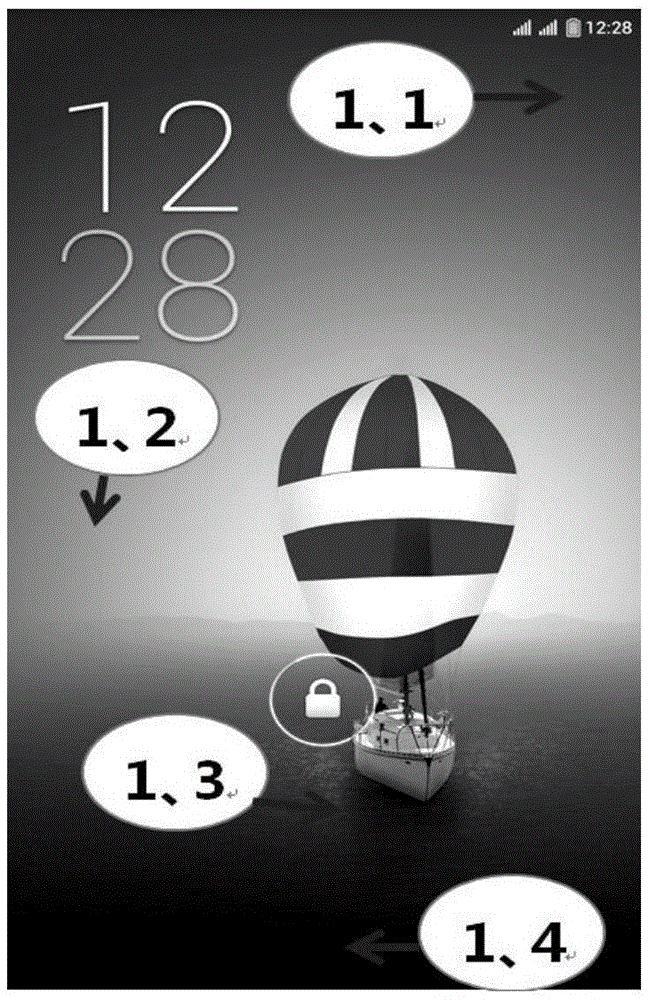
The invention discloses an unlocking method and device, and electronic equipment. The method adopts a non-stationary template as an unlocking template during unlocking, and the electronic equipment generates the unlocking template required for unlocking on the basis of an unlocking picture set by a user. In a use process of the electronic equipment, the user can set and replace the unlocking picture on the own on the basis of the use habits or hobbies of the user; on the basis, the electronic equipment carries out unlocking focus layout and unlocking template generation according to the picture characteristics of the unlocking picture so as to realize a purpose that the unlocking templates with different layout characteristics can be provided for different users, and unlocking characteristics are unlikely to be mastered by other people; meanwhile, the user can set and replace the unlocking picture on the own to control the use time of the unlocking template, so that safety risks caused by that the same template is used for an overlong time are avoided so as to further improve the unlocking safety of the electronic equipment.
Owner:DONGGUAN COOLPAD SOFTWARE TECH
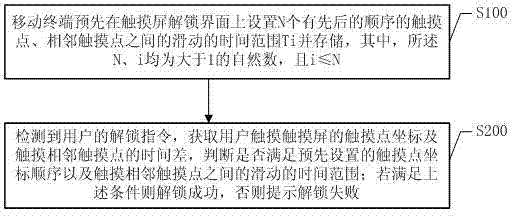
Touch screen unlocking method and system based on mobile terminal
ActiveCN104714752AImprove unlock securityInput/output processes for data processingTime rangeTouchscreen
The invention discloses a touch screen unlocking method and system based on a mobile terminal. The method includes the steps that N touch points sequentially arranged and the sliding time range Ti between every two adjacent touch points are set on a touch screen unlocking interface of the mobile terminal in advance and stored, wherein both the N and the i are natural numbers larger than 1, and the i is smaller than or equal to the N; an unlocking command of a user is detected, the touch point coordinates of touching a touch screen by the user and the time difference of touching the adjacent touch points by the user are obtained, and whether the preset touch point coordinate sequence and the sliding time range of touching the adjacent touch points are met or not is judged, if the conditions are met, unlocking is successful, and if not, a hint that unlocking is valid is given out. According to the touch screen unlocking method and system, whether the mobile terminal touch screen is unlocked by judging whether the sequence of the touch points and the touch time difference of the adjacent touch points are consistent with the preset value or not, the touch points can move according to the conditions as well, unlocking safety is improved, and convenience is brought to users.
Owner:威海神舟信息技术研究院有限公司
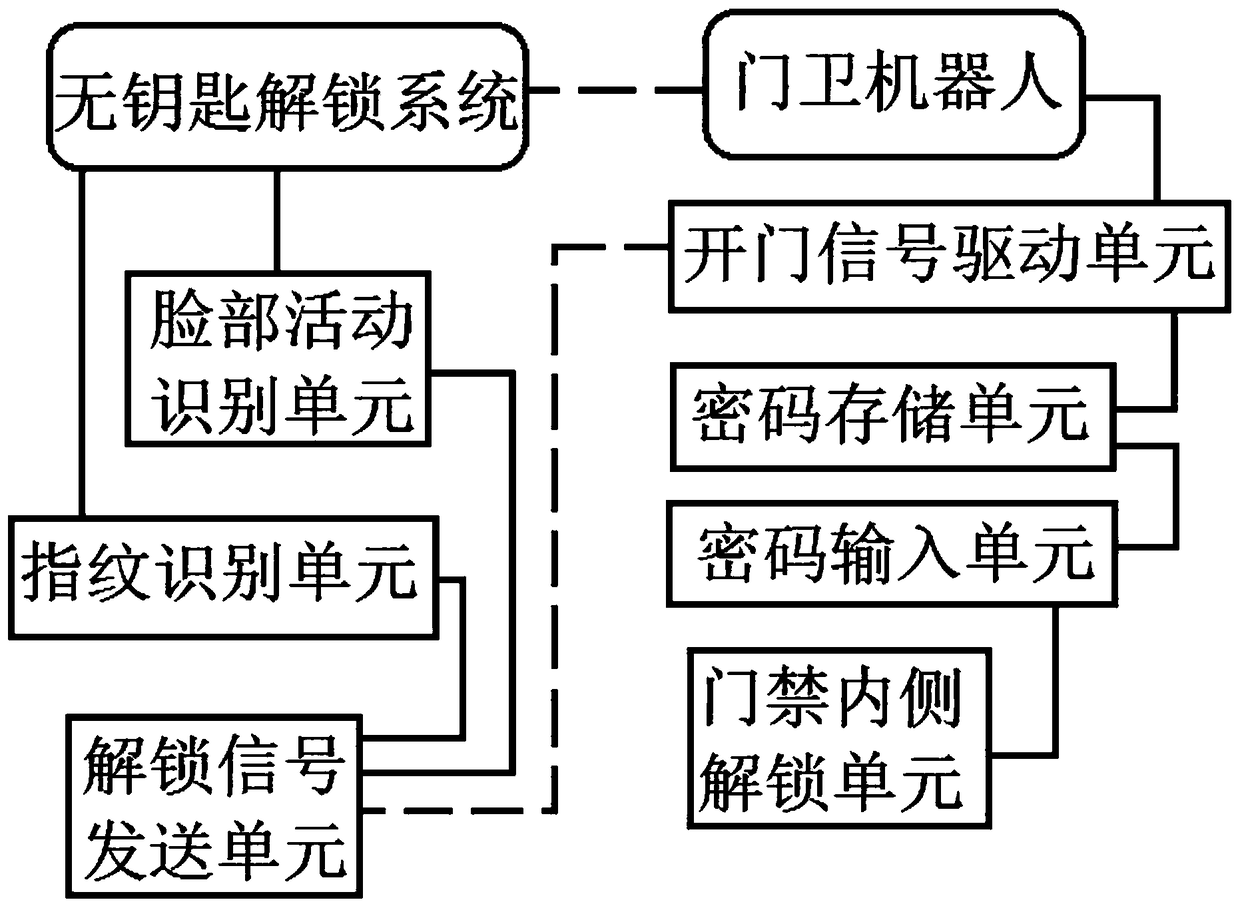
Household doorkeeper robot control system based on recognition logic supervision
InactiveCN108830989AImprove unlock securitySolve the accident that cannot enter the doorIndividual entry/exit registersManipulatorControl systemData information
The invention discloses a household doorkeeper robot control system based on recognition logic supervision, and relates to the field of smart driving control systems of robots. In the system, a face activity recognition unit used for recognizing information of a plurality of activities on the face of an operator is arranged in a keyless unlocking system; a fingerprint recognition unit used for recognizing fingerprint information of the operator is arranged in the keyless unlocking system; an unlocking signal transmitting unit is arranged in the keyless unlocking system and connected with a door opening signal driving unit in a data information transmission manner. The unlocking signal transmitting unit is driven to act by the face activity recognition unit and the fingerprint recognition unit which are arranged in the keyless unlocking system, and unlocking safety of household access control is improved; the door opening signal driving unit is arranged in a doorkeeper robot device anddrives an unlocking unit on the inner side of access control to act, household access control unlocking is finished, and the problem that a user cannot enter home when forgetting to carry a key out issolved effectively.
Owner:WUHU LE CHUANG ELECTRONICS TECH CO LTD
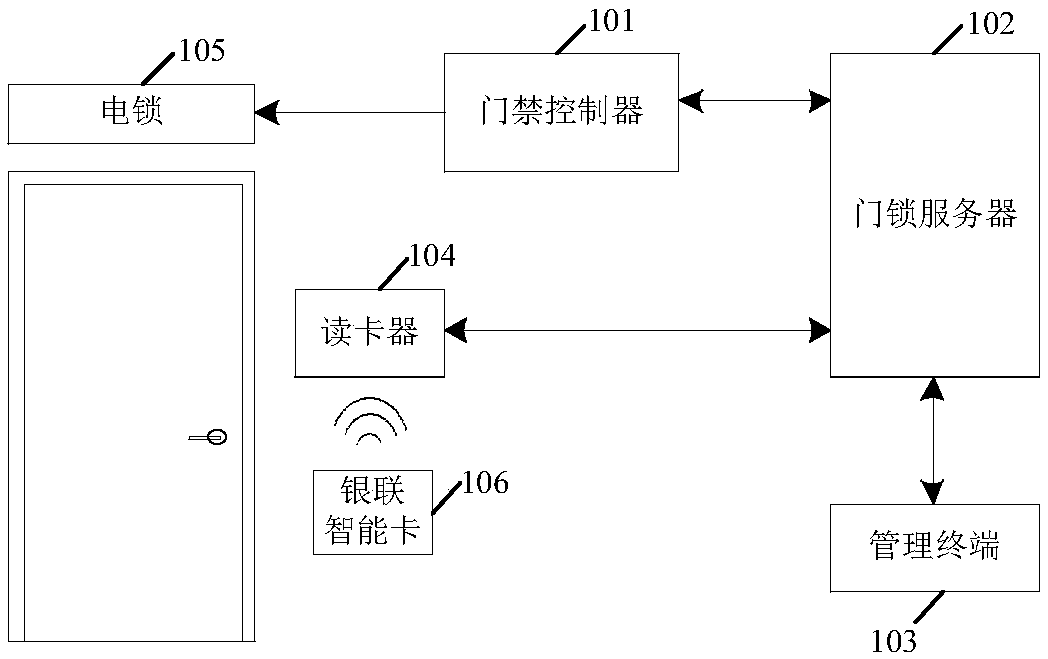
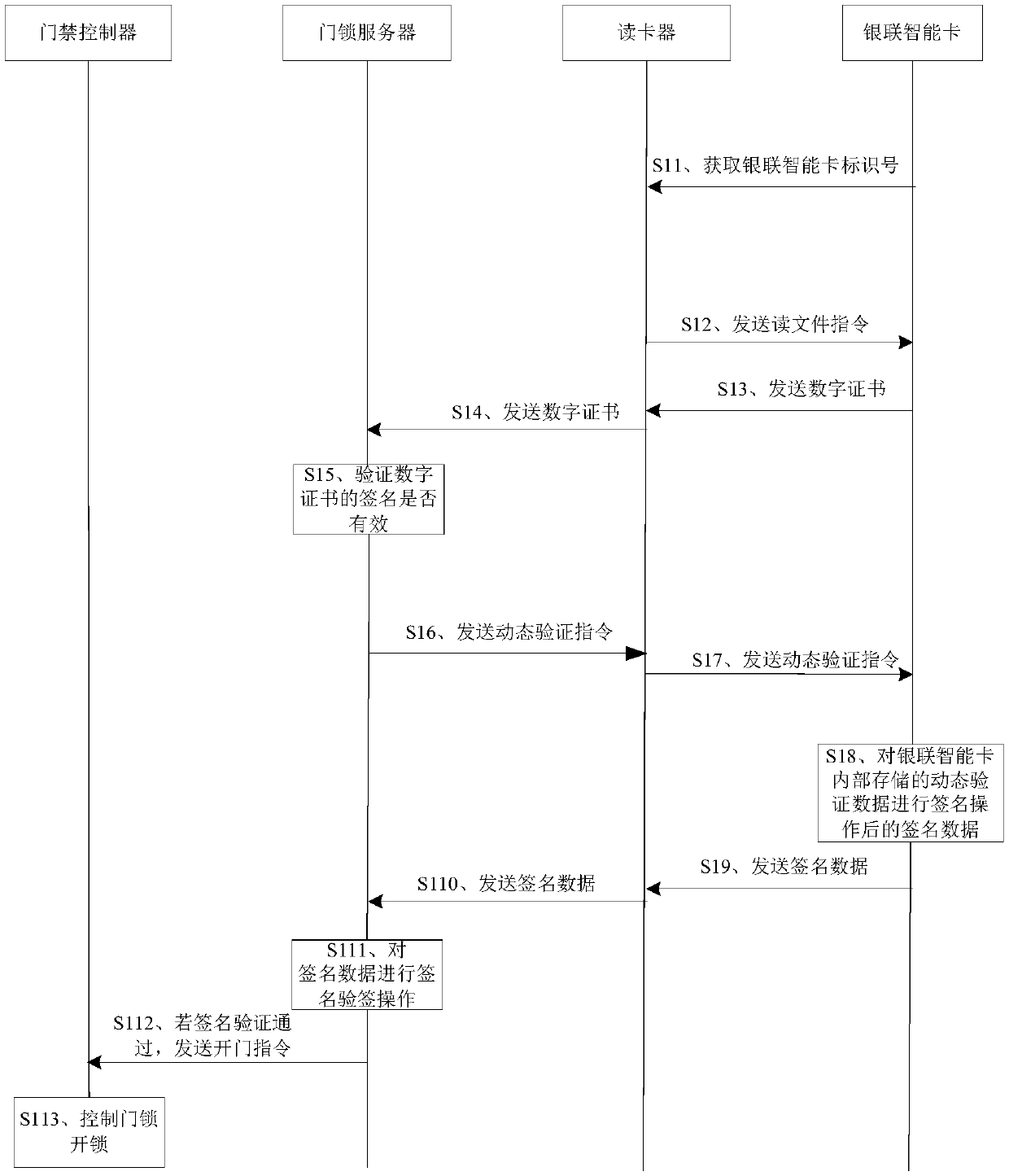
Unlocking method and device and equipment
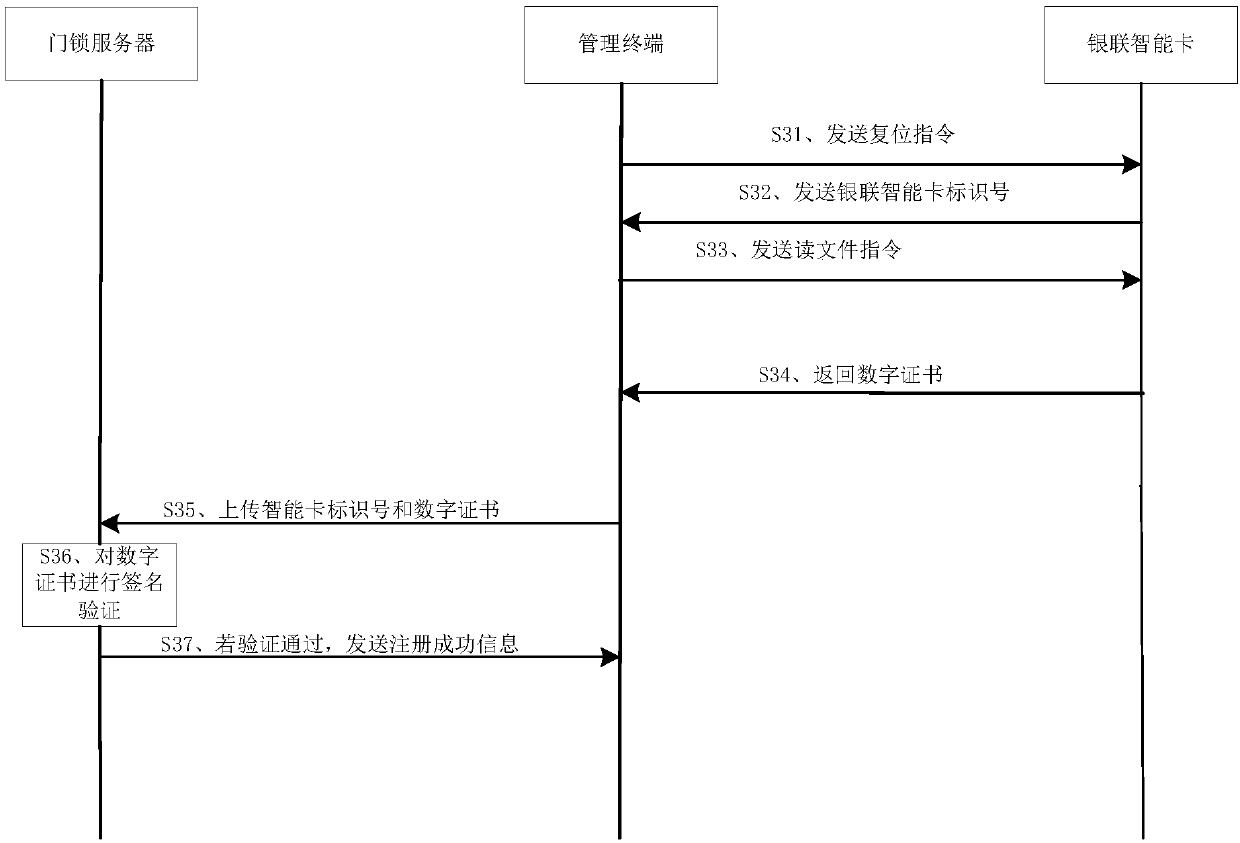
InactiveCN109685960AImprove unlock securityUser identity/authority verificationIndividual entry/exit registersSmart card
The invention provides an unlocking method and device and equipment. A door lock server firstly verifies whether a digital certificate signature in an UnionPay smart card is valid, that is, verifies whether the UnionPay smart card is a valid and legal UnionPay smart card, and then verifies whether the UnionPay smart card has the authority to open a door, only when a digital certificate inside theUnionPay smart card is valid and the UnionPay smart card has the authority to open the door, a door lock is controlled to be unlocked, and the unlocking security is improved.
Owner:BEIJING ZHONGJIN GUOXIN TECH
Unlocking method, device and system
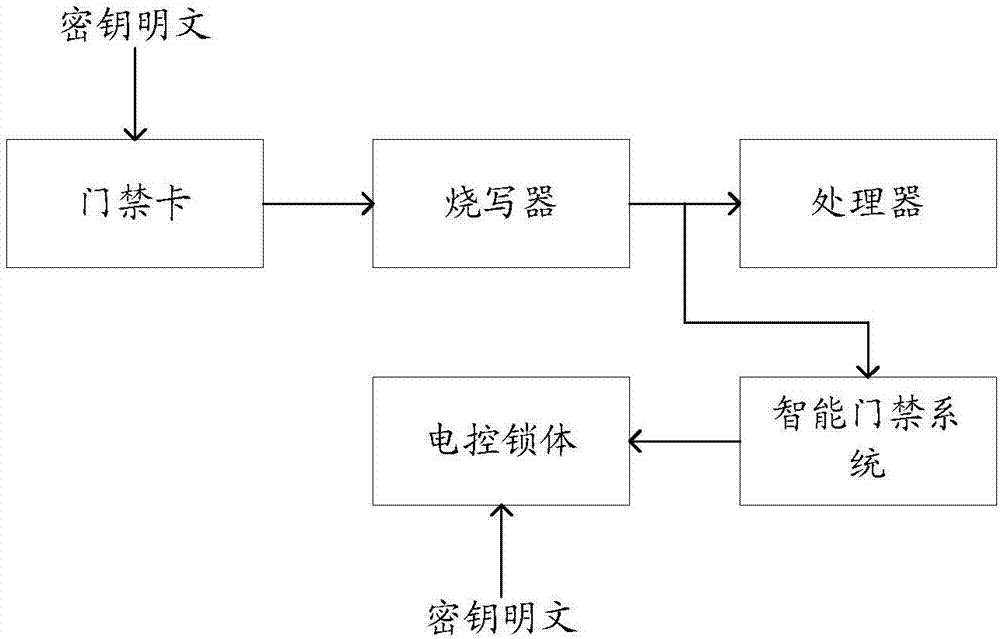
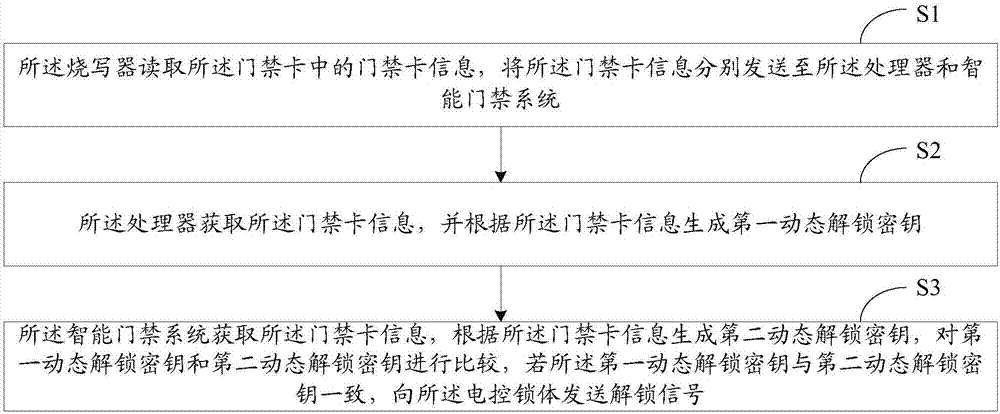
InactiveCN107516362AAchieve unlockImprove unlock securityIndividual entry/exit registersComputer hardwareElectric control
The invention relates to an unlocking method, device and system. The unlocking device comprises a processor, an intelligent access control system and an e-writerpro, wherein the processor is in communication connection with the e-writerpro; the e-writerpro is in communication connection with an access control card and the intelligent access control system respectively; the intelligent access control system is in communication connection with an electric control lock body; the e-writerpro is used for reading access control card information in the access control card and sending the access control card information to the processor and the intelligent access control system respectively; the processor is used for acquiring the access control card information and generating a first dynamic unlocking secret key; the intelligent access control system is used for acquiring the access control card information and generating a second dynamic unlocking secret key, comparing the first dynamic unlocking secret key and the second dynamic unlocking secret key and sending an unlocking signal to the electric control lock body.
Owner:GUANGZHOU POWER SUPPLY CO LTD
Real-name check-in system and method for rental house entrance guard
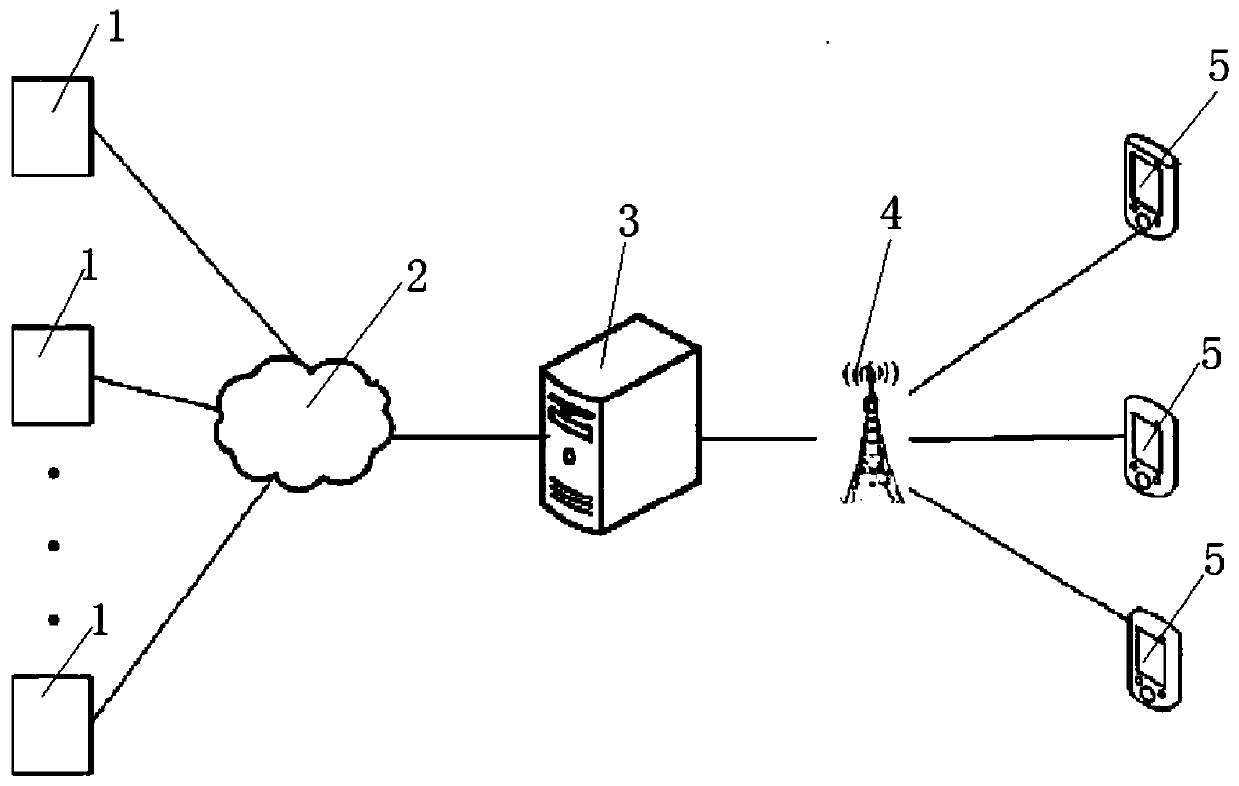
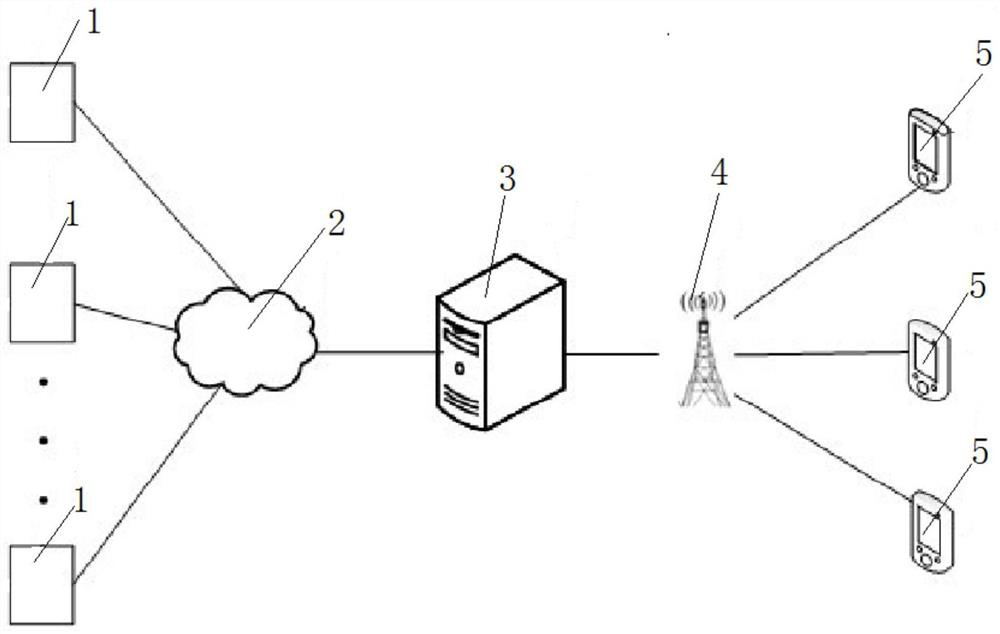
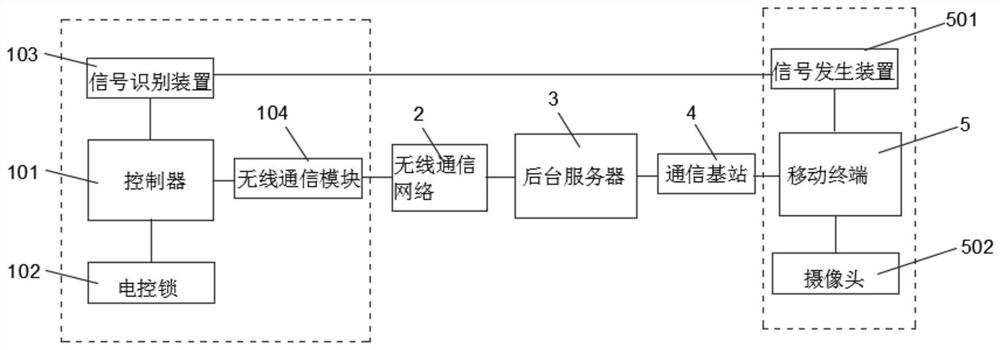
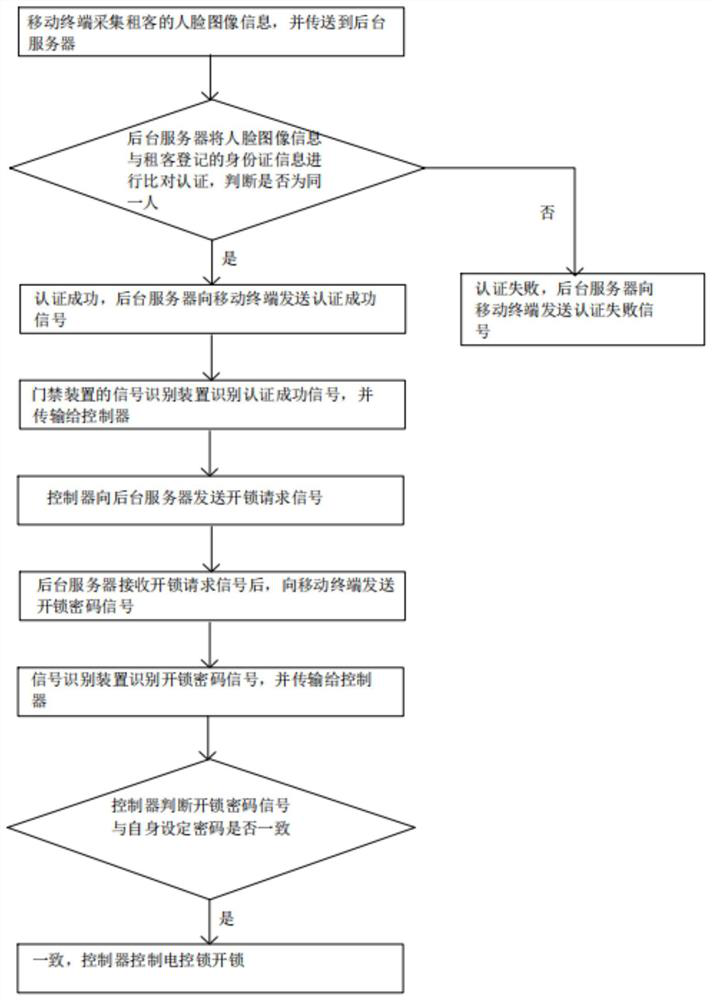
ActiveCN110060400AImprove accuracyImprove securityIndividual entry/exit registersSignal generatorAuthentication
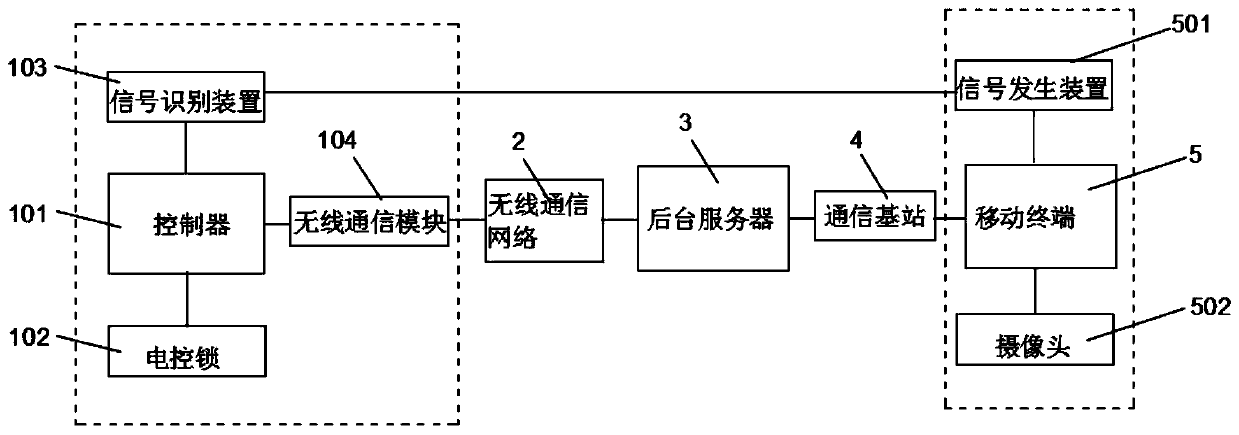
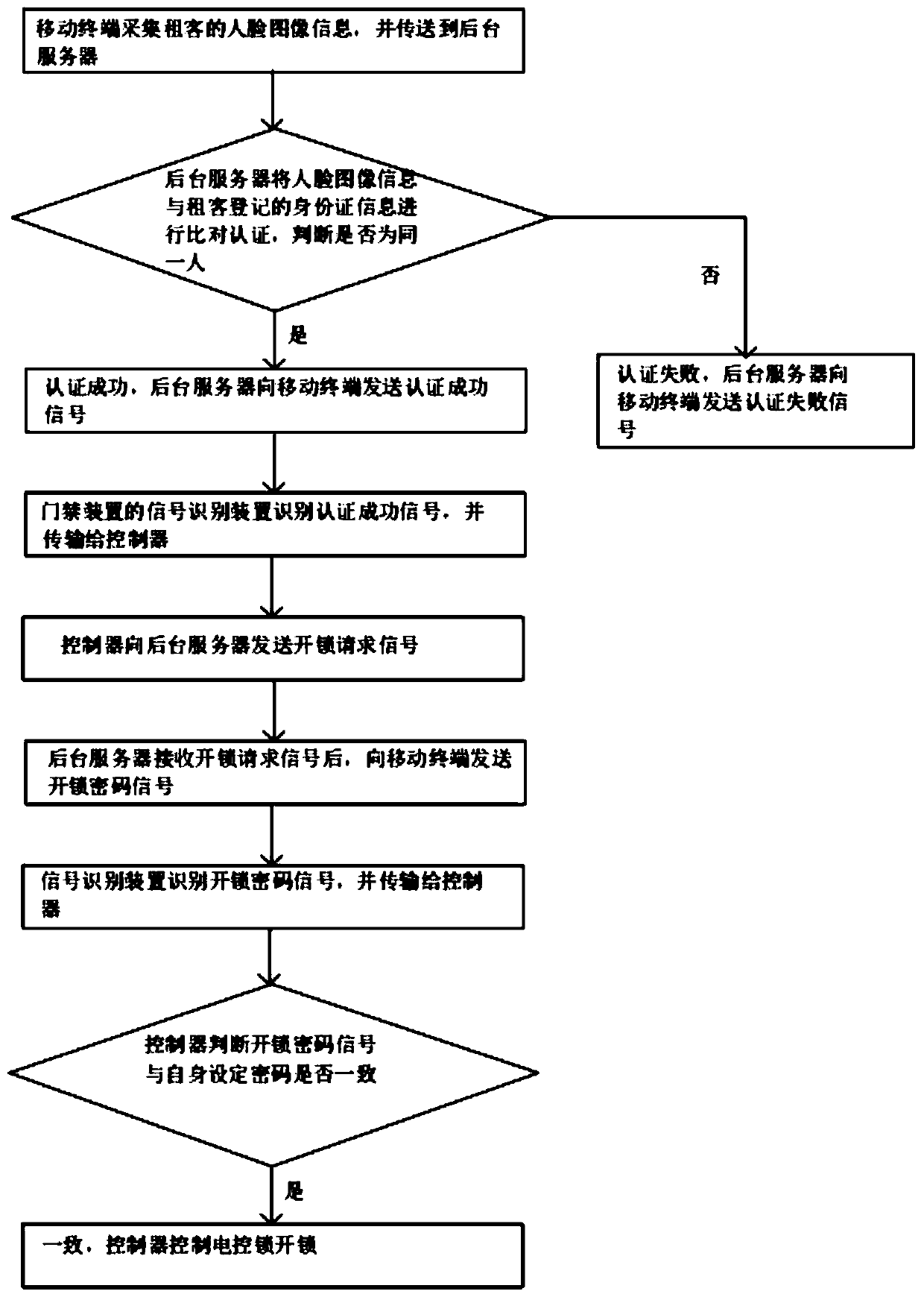
The invention discloses a real-name check-in system and method for a rental house entrance guard. The real-name check-in system comprises a background server, an entrance guard device and a mobile terminal; the background server is connected with the entrance guard device and the mobile terminal through a communication network correspondingly in a wireless communication mode; the mobile terminal is provided with a camera for collecting face image information of a tenant and a signal generator, and the mobile terminal transmits the face image information collected by the camera to the background server; and the entrance guard device includes an electronic control lock, a controller, a signal recognition device and a wireless communication module, and the controller is electrically connectedwith the electronic control lock, the signal recognition device and the wireless communication module correspondingly. According to the real-name check-in system and method of the rental house entrance guard, through information exchange among the mobile terminal, the background server and the entrance guard device, remote real-name authentication of rental house check-in is realized, unificationof people and personal identification is ensured, and security of the rental house check-in is improved.
Owner:李佳怿
Recycled packaging box intelligent lock unlocking method based on base station communication
InactiveCN111932739AImprove unlock securityImprove unlocking efficiencyIndividual entry/exit registersLocation information based serviceEmbedded systemMobile phone
The invention discloses a recycled packaging box intelligent lock unlocking method based on base station communication, belongs to the technical field of recycled packaging boxes, and aims to solve the problems of low unlocking efficiency and low unlocking safety of existing large-batch packaging boxes. The method comprises the following steps: (1) a base station server is in communication matching with an MCU chip of an intelligent lock entering a base station communication range; (2) an electronic fence feeds back to the base station server after the electronic fence monitors that the intelligent lock enters the fence; (3) biological recognition features are inputted through a mobile phone terminal and transmitted to the base station server for authorization; (4) the base station serversends an unlocking signal instruction to an MCU chip of the intelligent lock, if the unlocking signal instruction is received, the step 6 is executed, and if the unlocking signal instruction cannot bereceived, the step 5 is executed; (5) the unlocking signal instruction is sent to the MCU chip by using an emergency key with a communication module; and (6) the MCU chip sends a power-on signal to unlock the intelligent lock. The method is suitable for unlocking the recycled packaging box.
Owner:四川巧盒物联科技有限公司
Mobile terminal unlocking method and device
PendingCN110262722APrivacy protectionImprove unlock securityExecution for user interfacesInput/output processes for data processingComputer engineeringThree dimensional model
Owner:SHENZHEN QUCHUANG TECH CO LTD
Terminal
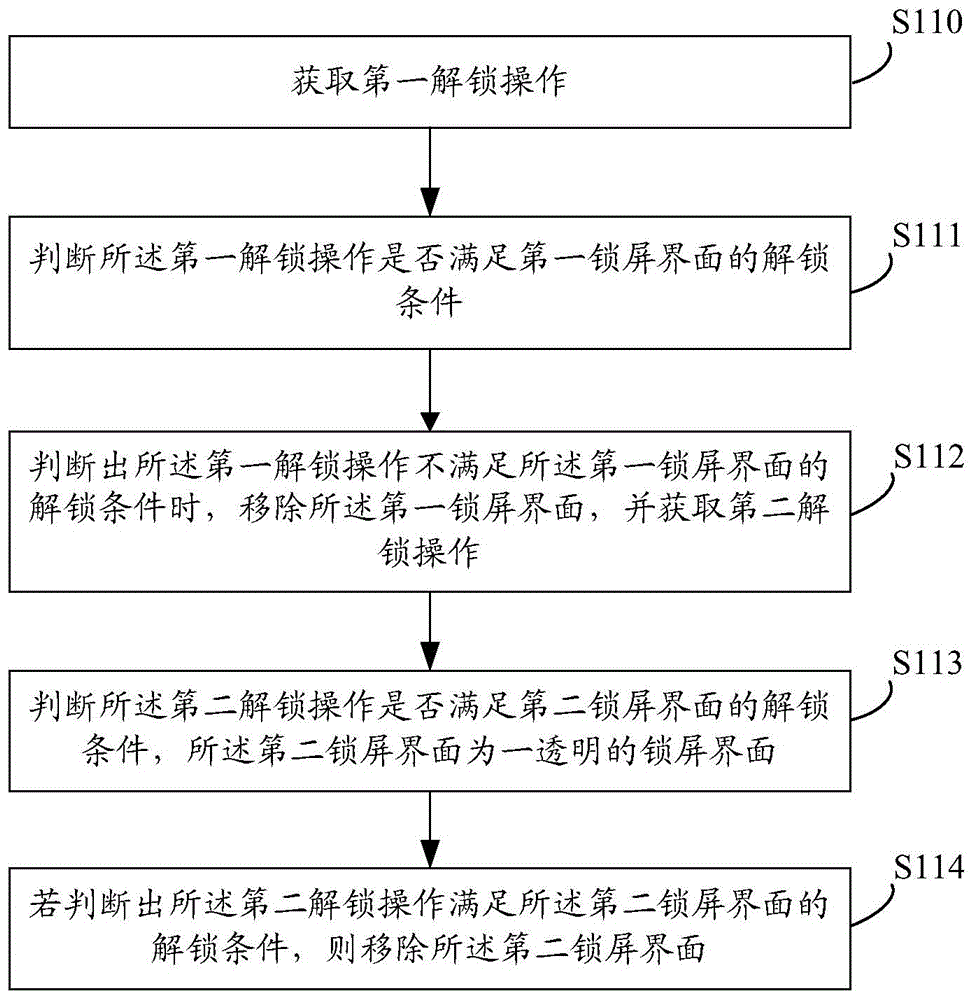
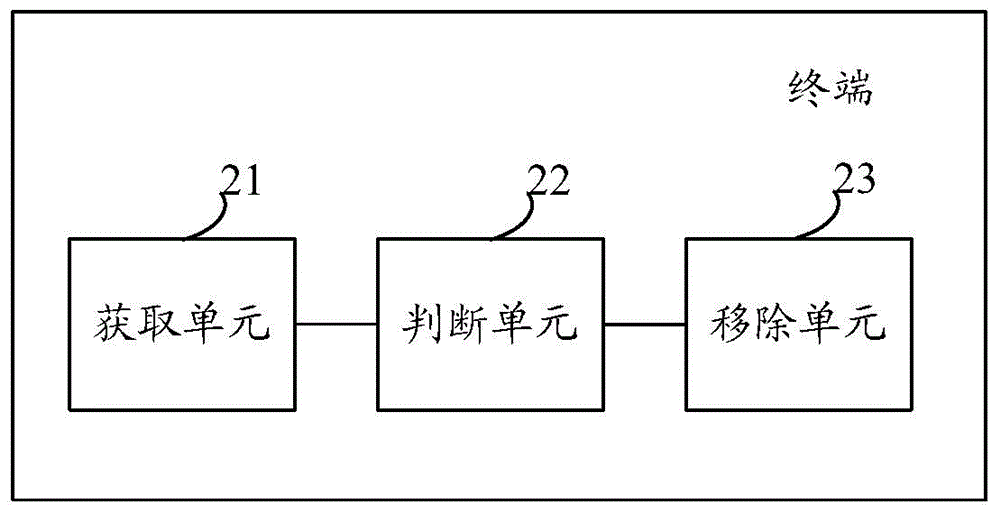
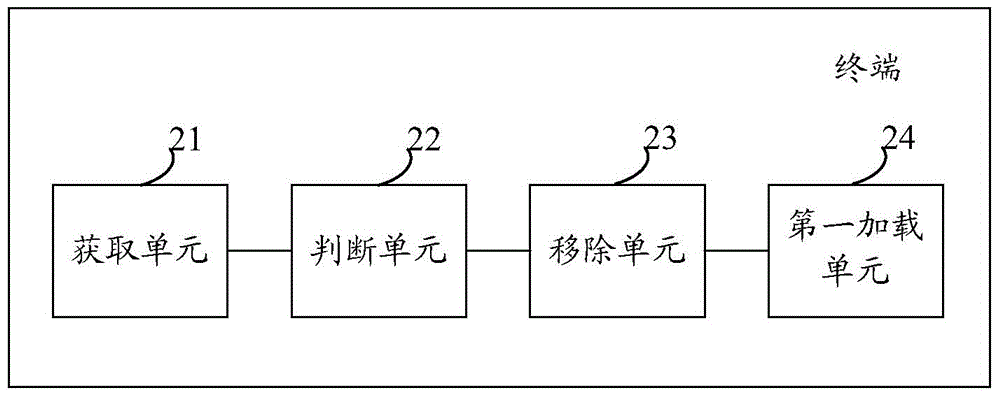
ActiveCN104809374AImprove unlock securityInput/output for user-computer interactionDigital data authenticationRemoval UnitsLock screen
An embodiment of the invention provides a terminal which can comprise an acquisition unit, a judgment unit and a removal unit, wherein the acquisition unit is used for acquiring a first unlocking operation, the judgment unit is used for judging whether the first unlocking operation meets unlocking conditions of a first lock screen or not, the removal unit is used for removing the first lock screen and acquiring a second unlocking operation when the judgment unit judges that the first unlocking operation does not meet the unlocking conditions of the first lock screen, the judgment unit is also used for judging whether the second unlocking operation meets unlocking conditions of a second transparent lock screen or not, and the removal unit is also used for removing the second lock screen when the judgment unit judges that the second unlocking operation meets the unlocking conditions of the second lock screen. Terminal unlocking safety can be improved.
Owner:SHENZHEN TRANSSION HLDG CO LTD
Multi-dimensional unlocking method for user equipment and user equipment
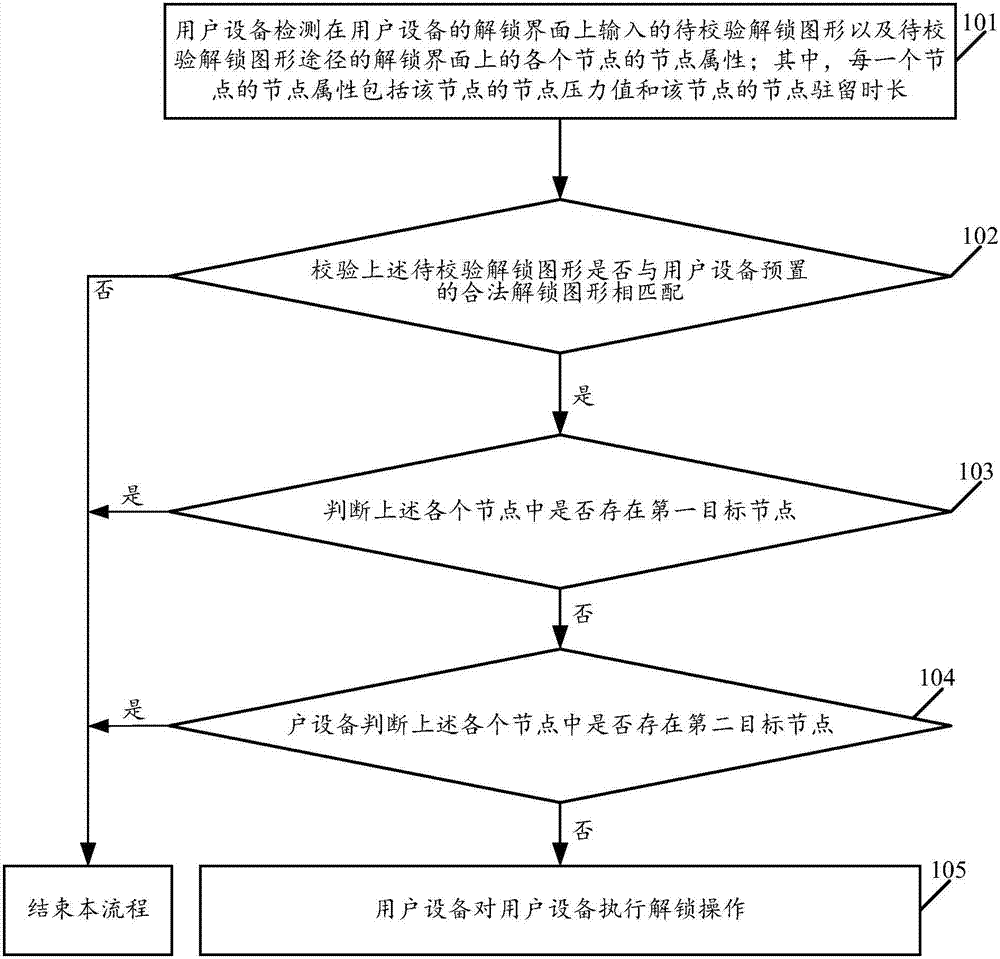
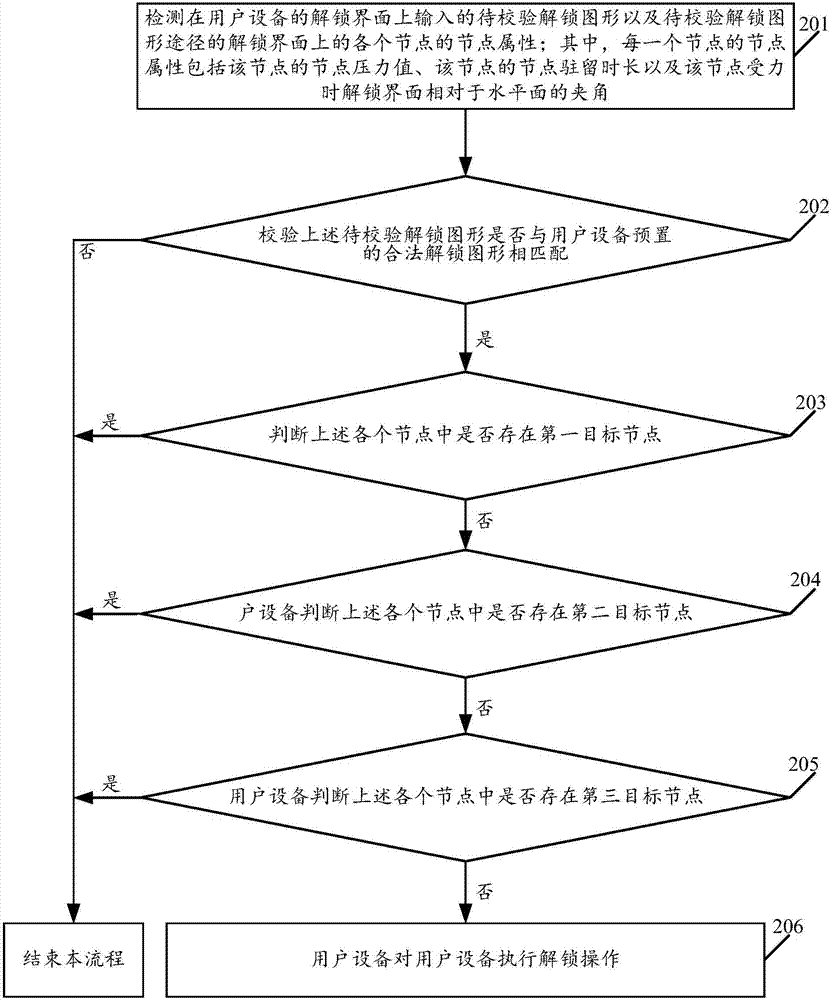
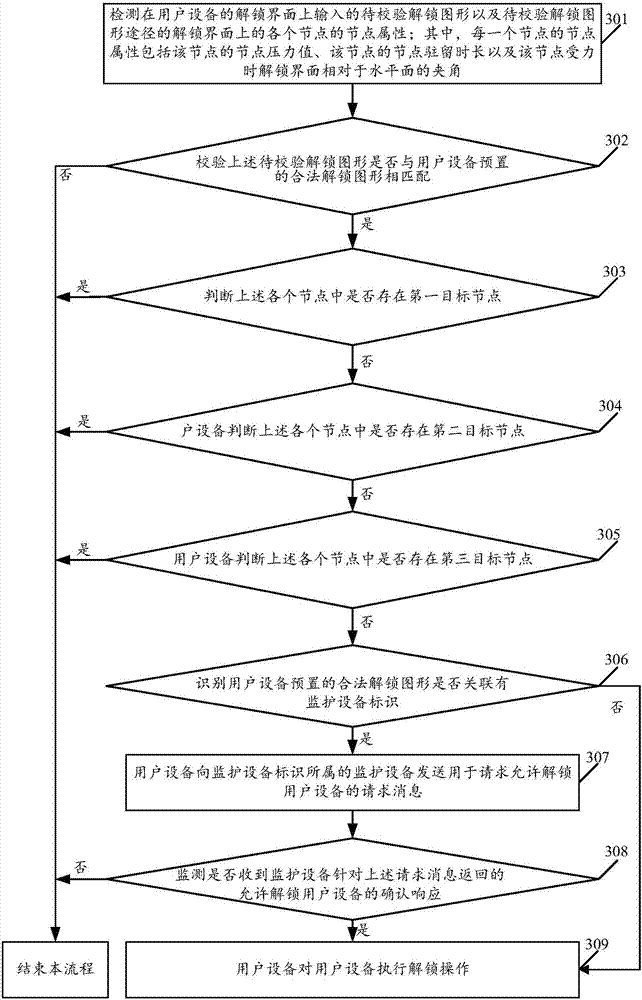
ActiveCN106886724AImprove unlock securityProtection securityUnauthorised/fraudulent call preventionInternal/peripheral component protectionGraphicsComputer network
The present invention discloses a multi-dimensional unlocking method for user equipment and user equipment. The method comprises: detecting to-be-checked unlock pattern input on an unlocking interface by the user equipment and a node attribute of each node on the unlocking interface of the path of the to-be-checked unlock pattern, wherein the node attribute comprises a node pressure value and a node residence time; if it is checked that the to-be-checked unlock pattern is matched with the legal unlock pattern preset by the user equipment, determining whether there is a first target node in each node, wherein the node pressure value of the first target node is not contained in the unlock pressure range corresponding to the first target node, and the unlock pressure ranges corresponding to each node are different; if there is no first target node in each node, determining whether there is a second target node in each node, wherein the node residence time of the second target node is not contained in the unlock residence time range corresponding to the second target node, and the node residence time ranges corresponding to each node are different; and if there is no second target node in each node, performing the unlock operation on the user equipment. According to the method and user equipment disclosed by the present invention, the unlock security can be improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
An unlocking method, combination lock and system based on holographic projection
ActiveCN108109246BSuccessfully unlockedNot easy to be stolenIndividual entry/exit registersComputer hardwareProjection image
The invention discloses an unlocking method based on holographic projection, a password lock and a system. The method comprises the following steps: performing non-intermittent scanning on a receivedtarget holographic image by a receiving device, and confirming a corresponding legal key image according to preset rules; when unlocking is needed, acquiring a current target holographic image transmitted from a transmitting device by the receiving device, scanning the holographic image so as to obtain a current target holographic projection image, verifying the current target holographic projection image with a corresponding legal key image, and unlocking successfully if verification results are accordant or within a preset error range. By adopting the unlocking method based on holographic projection, unlocking can be implemented by only using key images which are set in advance, unlocking security can be improved through key image unlocking, and meanwhile inconvenience and potential danger caused by key loss in the prior art can be avoided.
Owner:GUANGDONG HONGQIN COMM TECH CO LTD
Mobile terminal management method and mobile terminal
InactiveCN108334767AImprove unlock securityAvoid dataDigital data authenticationSubstation equipmentComputer terminalApplication specific
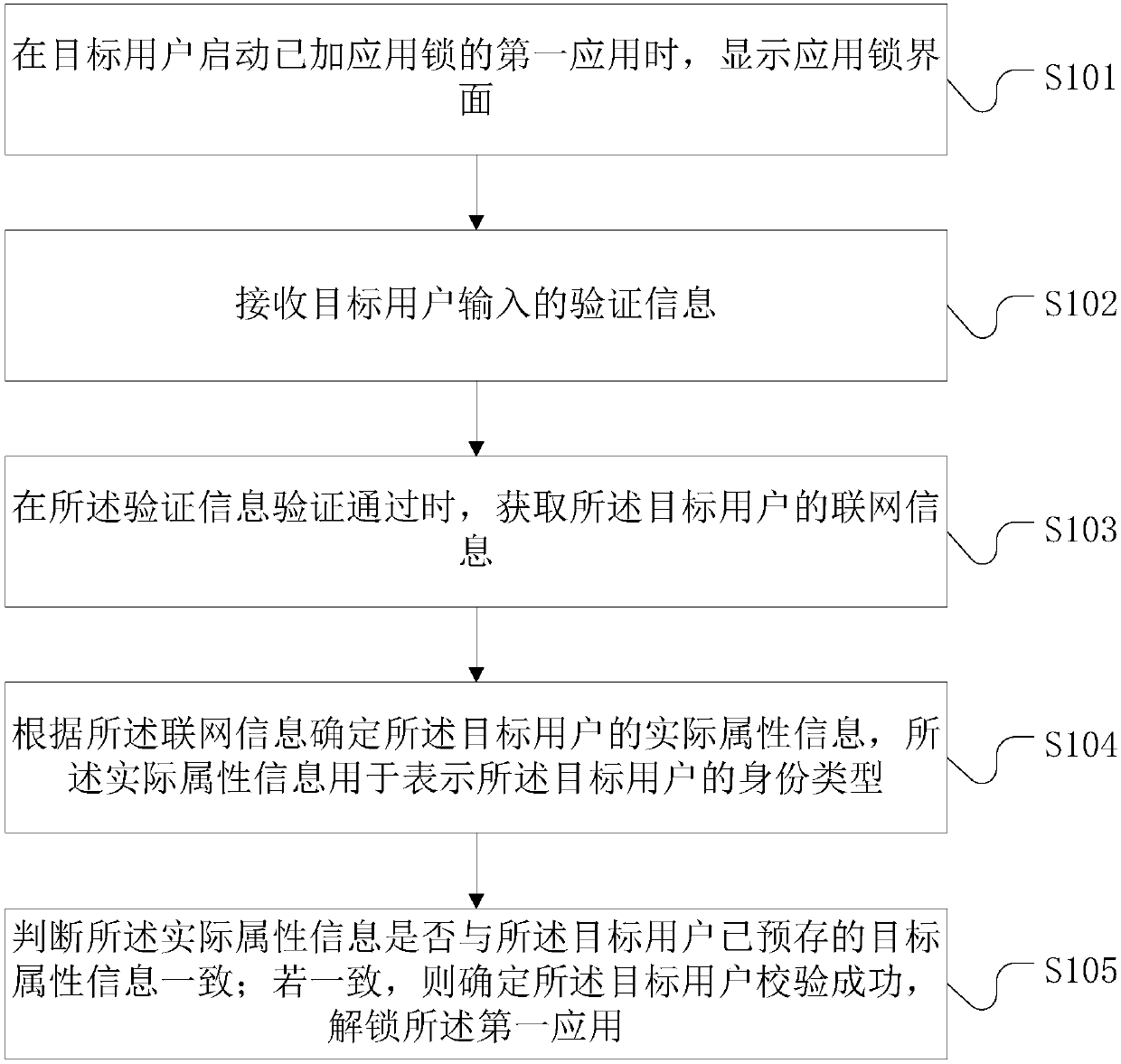
The embodiment of the invention discloses a mobile terminal management method and a mobile terminal and belongs to the technical field of mobile terminals. The mobile terminal management method includes the steps of: displaying an application lock interface when a target user starts a first application with an application lock applied to; obtaining verification information entered by the target user; obtaining networking information of the target user if the verification information is verified; determining actual attribute information of the target user based on the networking information, wherein the actual attribute information is used for indicating the identity type of the target user; determining whether the actual attribute information is consistent with target attribute informationpre-stored by the target user; determining that the target user is successfully verified and then unlocking the first application if consistent. The mobile terminal management method has the advantages of improving unlock security for application-specific app locks and avoiding user data and privacy leaks with not only monomer information but also the networking information used when when the application lock is being released.
Owner:DONGGUAN HUARUI ELECTRONICS TECH CO LTD
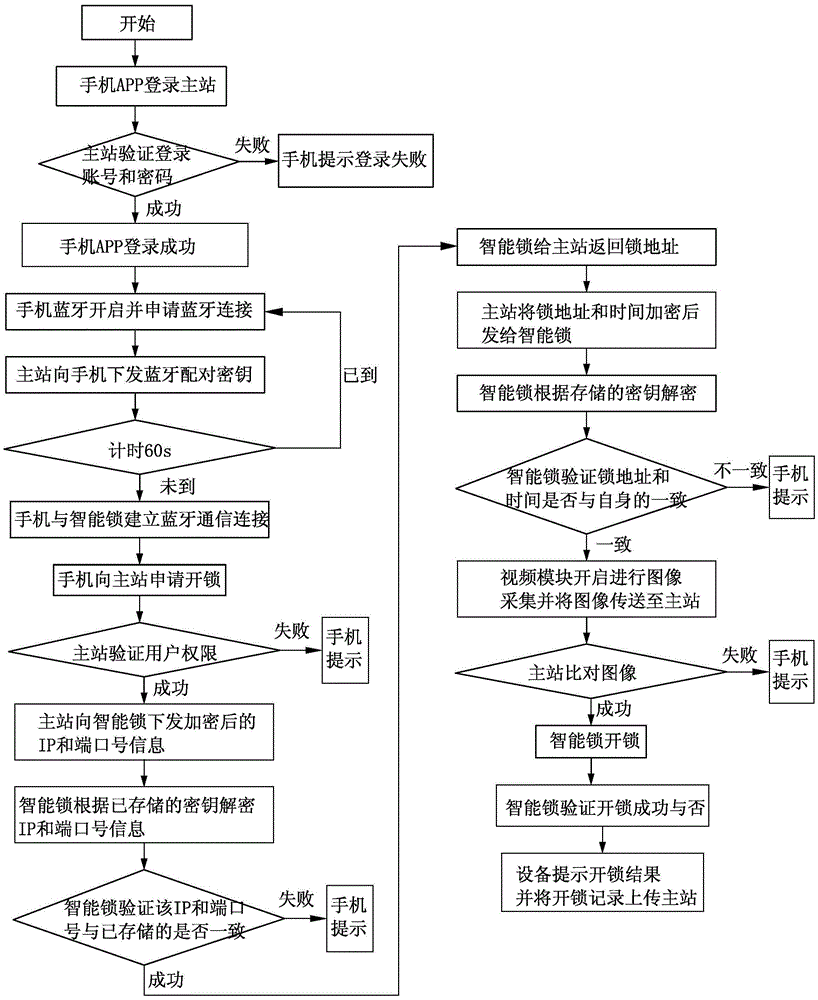
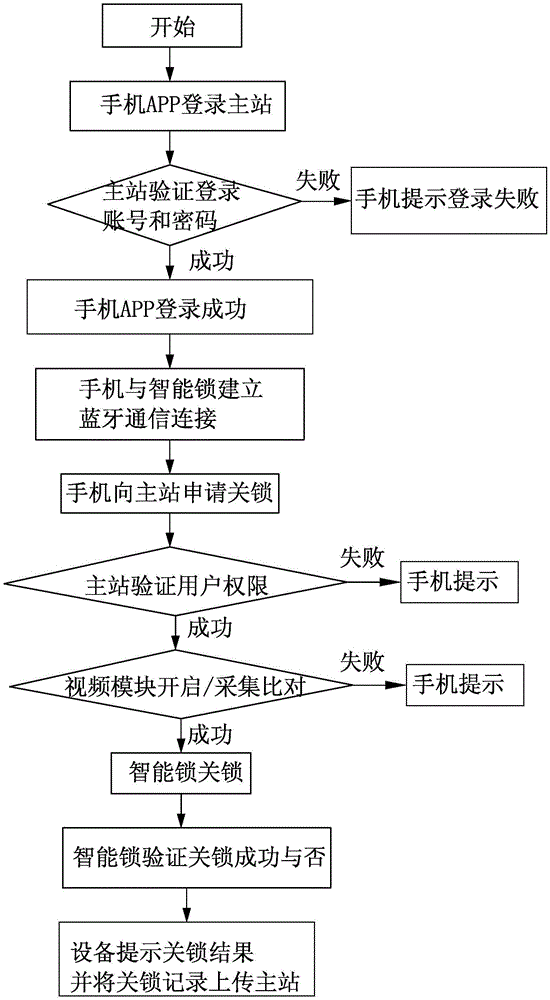
Unlocking method of security intelligent lock system with video surveillance based on bluetooth
ActiveCN104282058BEfficient managementValid recordUser identity/authority verificationNear-field systems using receiversVideo monitoringMaster station
The present invention discloses a method for unlocking Bluetooth with security video surveillance system based on intelligent lock, intelligent lock system comprises a smart safety lock, a mobile terminal, the master station, the lock is provided with MCU intelligent control module and a video module, mounted on the mobile terminal there are software modules operating, intelligent lock via Bluetooth communication mobile terminal, the mobile communication terminal connected to the master station; transmitting and intelligent lock command to the mobile terminal, key verification or authentication information between the intelligent lock and the mobile terminal, the master image verify achieve security intelligence gathering unlock the lock. Smart, easy to operate, safe and reliable, because the use of integrated management of a communication network, and the master station, an information storage function, it is possible to realize the operation target of the switch lock, the operator, the object status, operation time information such as a valid record and manage and part of the lock system software update upgrades to increase the level of security, strong adaptability and adjustability to improve the effective management of locking system.
Owner:XIAMEN HUASHU ELECTRIC POWER SCI & TECH CO LTD
An unlocking method, unlocking device and electronic equipment
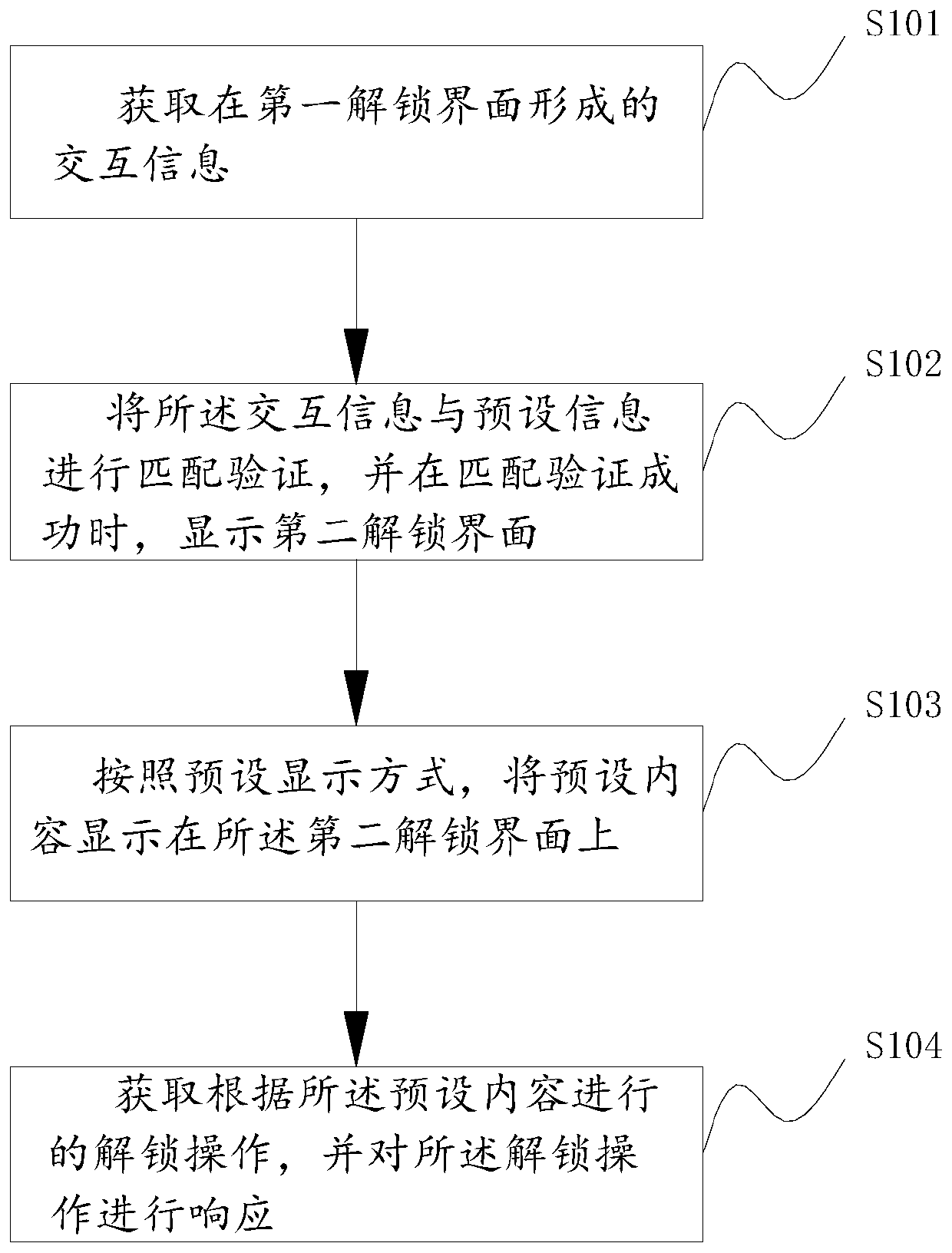
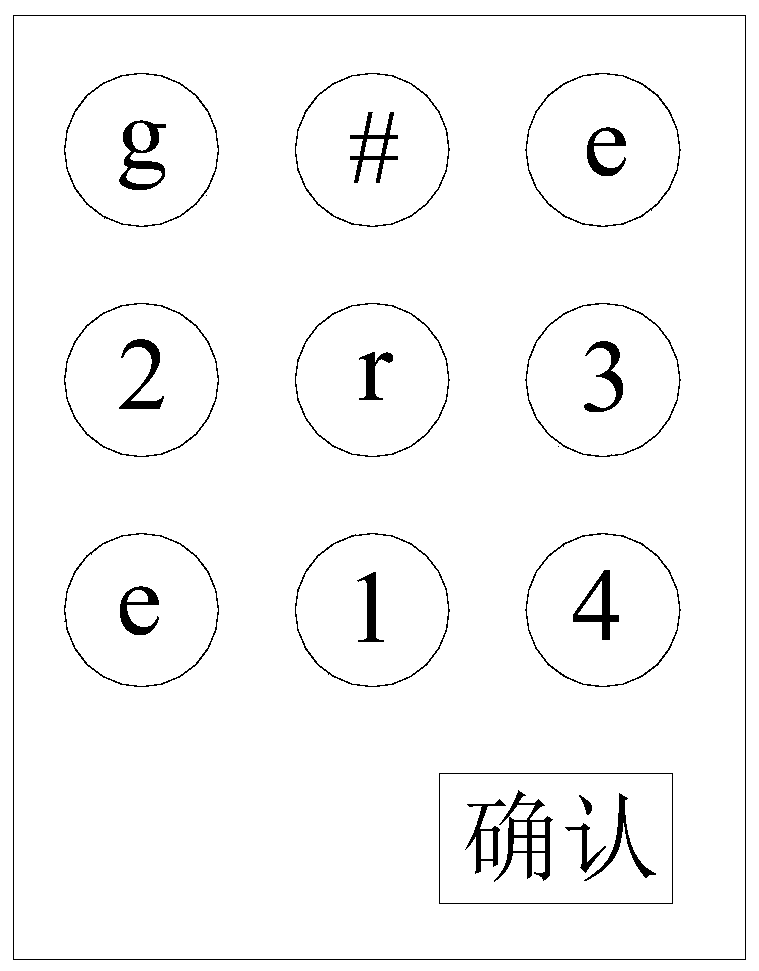
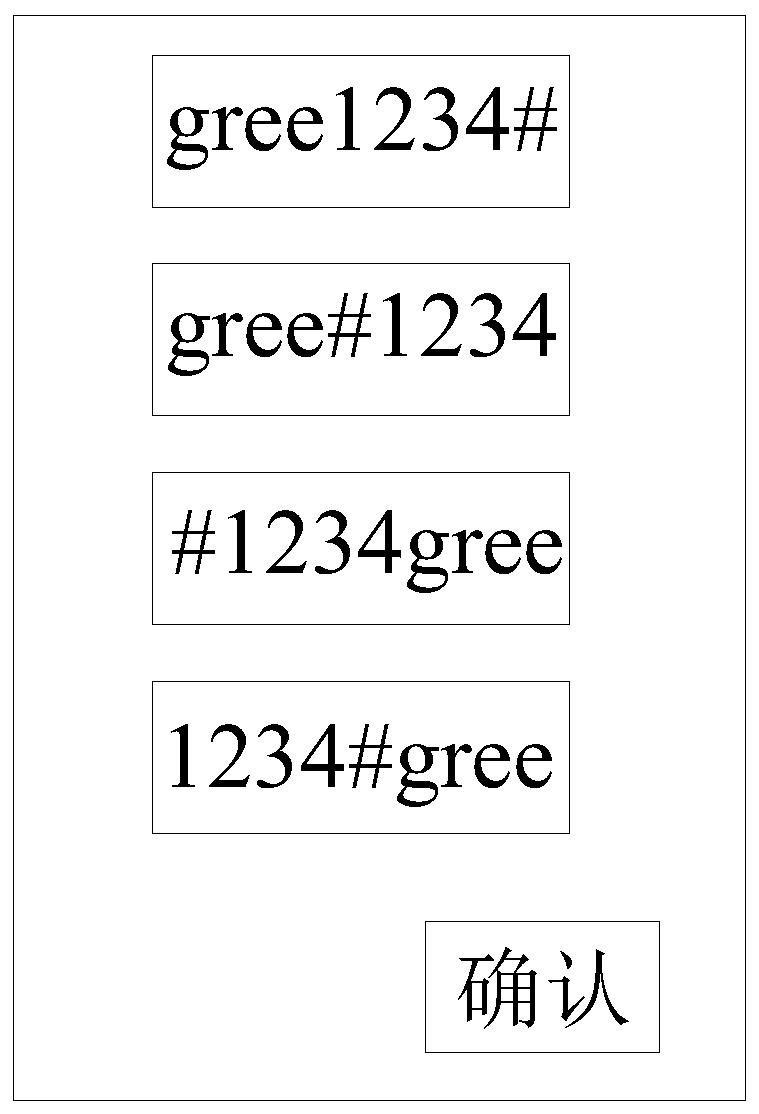
ActiveCN109063455BImprove unlock securityOptimize the unlocking methodDigital data authenticationPasswordEngineering
The invention relates to an unlocking method, an unlocking device and an electronic device, belonging to the technical field of unlocking. The present application includes: acquiring interaction information formed at a first unlocking interface; Carrying out matching verification on the interaction information and the preset information, and displaying a second unlocking interface when the matching verification is successful; Displaying a preset content on the second unlocking interface according to a preset display mode; Acquiring an unlocking operation according to the preset content and responding to the unlocking operation. After the matching verification of the interaction information formed by the first unlocking interface is successful, The preset content is displayed on the secondunlocking interface according to the preset display mode, and the unlocking operation carried out by the user according to the preset content can increase the unlocking security of the electronic equipment and improve the convenience of the user to use the password, thereby realizing the improvement of the unlocking method of the electronic equipment.
Owner:GREE ELECTRIC APPLIANCES INC
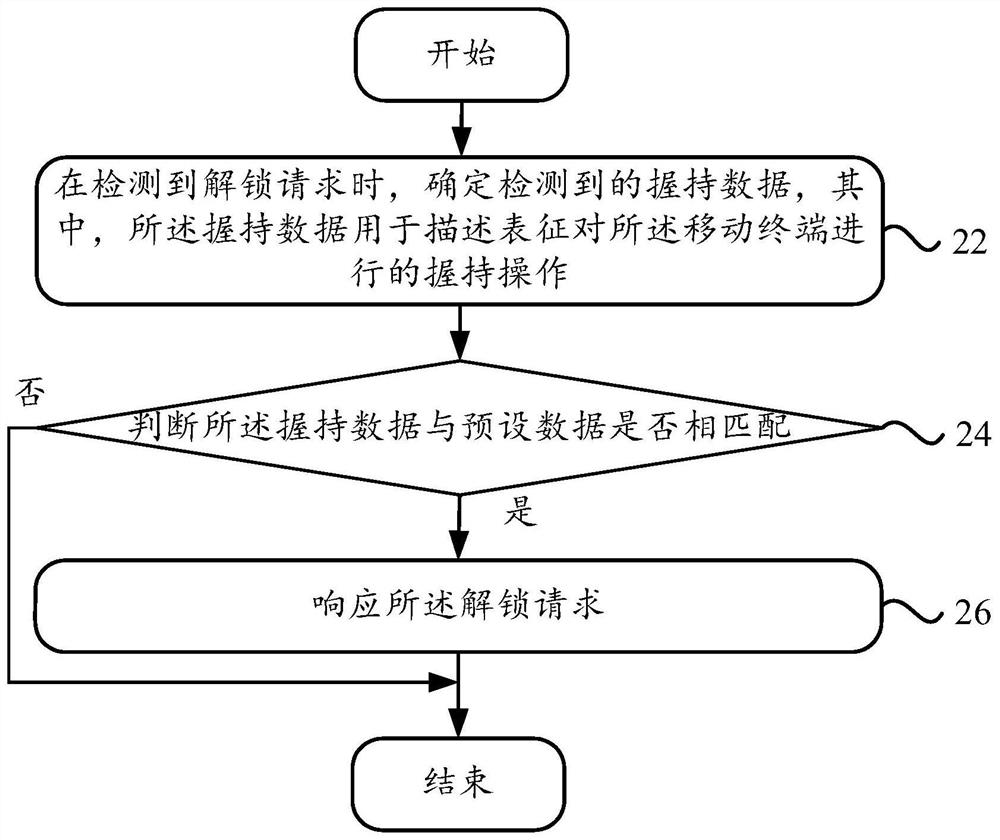
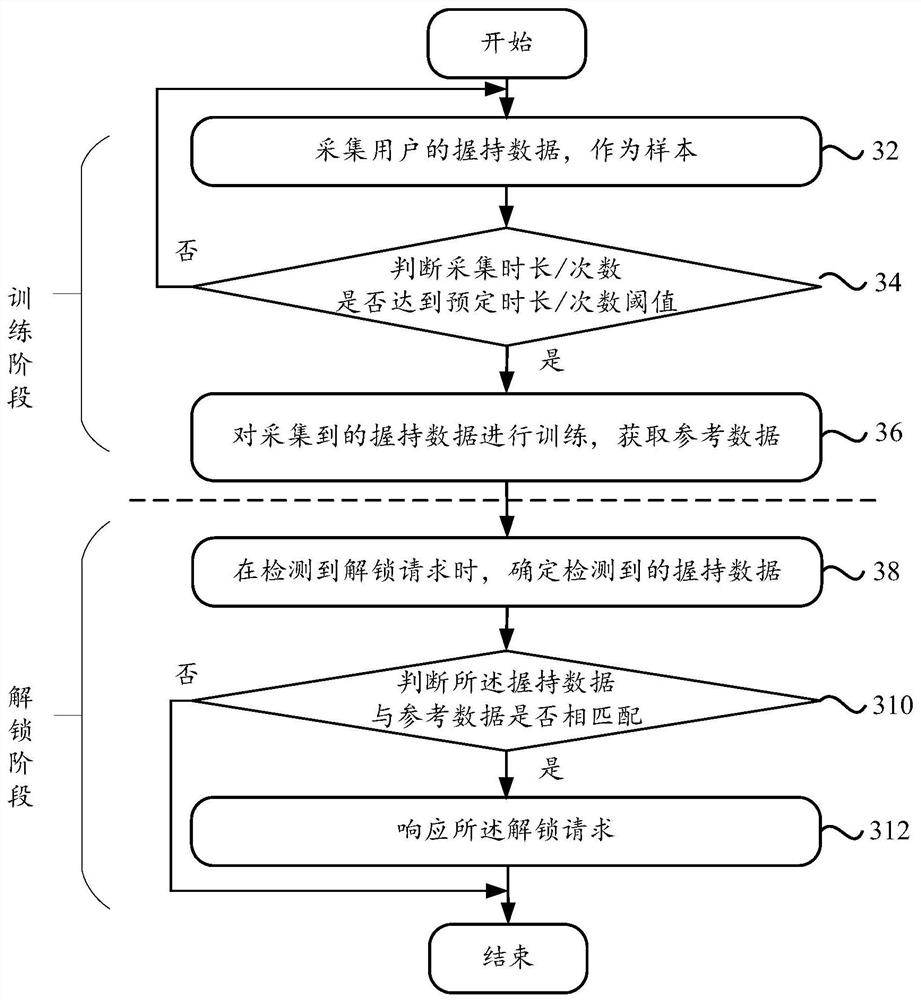
An unlocking request response method, mobile terminal
ActiveCN108388790BAvoid malicious unlocking situationsImprove unlock securityDigital data authenticationInternet privacyEngineering
The invention discloses an unlocking request response method and a mobile terminal. The method comprises the steps of determining detected holding data when an unlocking request is detected, wherein the holding data is used for representing holding operation performed for the mobile terminal; and when the holding data is matched with preset data, making a response to the unlocking request. Beforethe mobile terminal makes a response to the unlocking request, the holding data of holding the mobile terminal is determined; the holding data is matched with reference data to determine whether a user holding the mobile terminal initiates the unlocking request or not; and if yes, the unlocking request is responded, so that the situation of malicious unlocking performed not based on subjective wishes of the user is avoided and the purpose of improving the unlocking security is achieved.
Owner:VIVO MOBILE COMM CO LTD
A hardware encryption method, system and intelligent cloud lock based on proximity card unlocking
ActiveCN108171830BAvoiding Vulnerable Theft IssuesImprove unlock securityIndividual entry/exit registersTransmissionData packSecurity validation
The invention discloses a method and a system for encrypting hardware based on proximity card unlocking, and a smart cloud lock. The method comprises the following steps: step A, when a proximity cardcontacts the smart cloud lock, the MCU processor of the smart cloud lock identifies a sensing SN code in the proximity card, and sends a verification instruction to a security chip; step B, the security chip receives the verification instruction, and sends a security verification code to the MCU processor; and step C, the MCU processor packs the acquired sensing SN code and the security verification code into an unlocking request data packet, and sends the unlocking request data packet to a cloud server. An encrypted unlocking instruction sent by the cloud server, and is decrypted by the security chip, so the unlocking instruction is prevented from being stolen, the anti-theft performance is improved, and a problem that the unlocking instruction recorded in the proximity card can be easily stolen is avoided.
Owner:HUITAILONG DECORATION MATERIAL YUEXIU DIST GUANGZHOU
Real-name check-in system and method for rental house access control
ActiveCN110060400BImprove accuracyImprove securityIndividual entry/exit registersIdentification deviceElectric control
The invention discloses a real-name check-in system and method for access control of a rental house. The system includes a background server, an access control device and a mobile terminal. The camera and signal generating device that collects the face image information of the tenant, and the mobile terminal transmits the face image information collected by the camera to the background server; the access control device includes an electric lock, a controller, a signal recognition device and a wireless communication module. The device is electrically connected with the electric control lock, the signal identification device and the wireless communication module respectively. The rental house access control real-name check-in system and method provided by the present invention realize the remote real-name authentication of rental house check-in through information interaction between the mobile terminal, the background server and the access control device, ensure the unity of witnesses and certificates, and improve the safety of rental house check-in sex.
Owner:李佳怿
An unlocking method, device and electronic equipment
ActiveCN105631301BImprove unlock securityControl usage timeDigital data authenticationHabitEmbedded system
The invention discloses an unlocking method and device, and electronic equipment. The method adopts a non-stationary template as an unlocking template during unlocking, and the electronic equipment generates the unlocking template required for unlocking on the basis of an unlocking picture set by a user. In a use process of the electronic equipment, the user can set and replace the unlocking picture on the own on the basis of the use habits or hobbies of the user; on the basis, the electronic equipment carries out unlocking focus layout and unlocking template generation according to the picture characteristics of the unlocking picture so as to realize a purpose that the unlocking templates with different layout characteristics can be provided for different users, and unlocking characteristics are unlikely to be mastered by other people; meanwhile, the user can set and replace the unlocking picture on the own to control the use time of the unlocking template, so that safety risks caused by that the same template is used for an overlong time are avoided so as to further improve the unlocking safety of the electronic equipment.
Owner:DONGGUAN COOLPAD SOFTWARE TECH
A face verification method and face verification device
ActiveCN105426886BImprove securityImprove unlock securityCharacter and pattern recognitionPattern recognitionValidation methods
The embodiment of the present invention discloses a face verification method, which is applied to a terminal with a camera. The lens of the camera includes a plane light-transmitting part and a prism light-transmitting part, and the prism light-transmitting part includes at least two prism faces. The method includes determining a photographing mode; if the photographing mode is a prism photographing mode, acquiring a face image through the light-transmitting part of the prism; If the acquired face image determines that the face recognition is passed, then it is determined that the face verification result is passed. Correspondingly, the embodiment of the present invention also discloses a face verification device. By adopting the embodiment of the present invention, the security of the terminal can be improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com