Protection method for terminal, terminal and computer readable storage medium
A terminal and equipment technology, applied in the protection method of terminal, terminal and computer readable storage medium field, can solve the problem of reducing the possibility of legal user's recovery, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
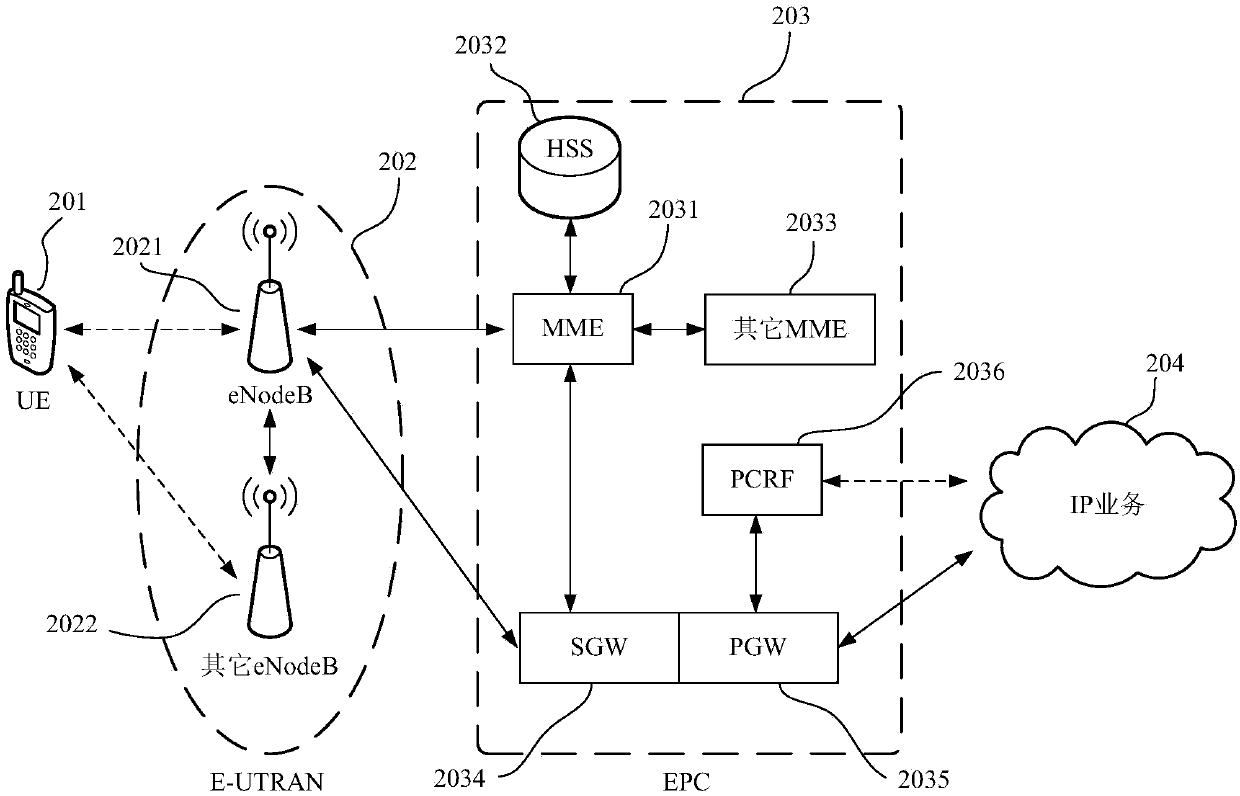
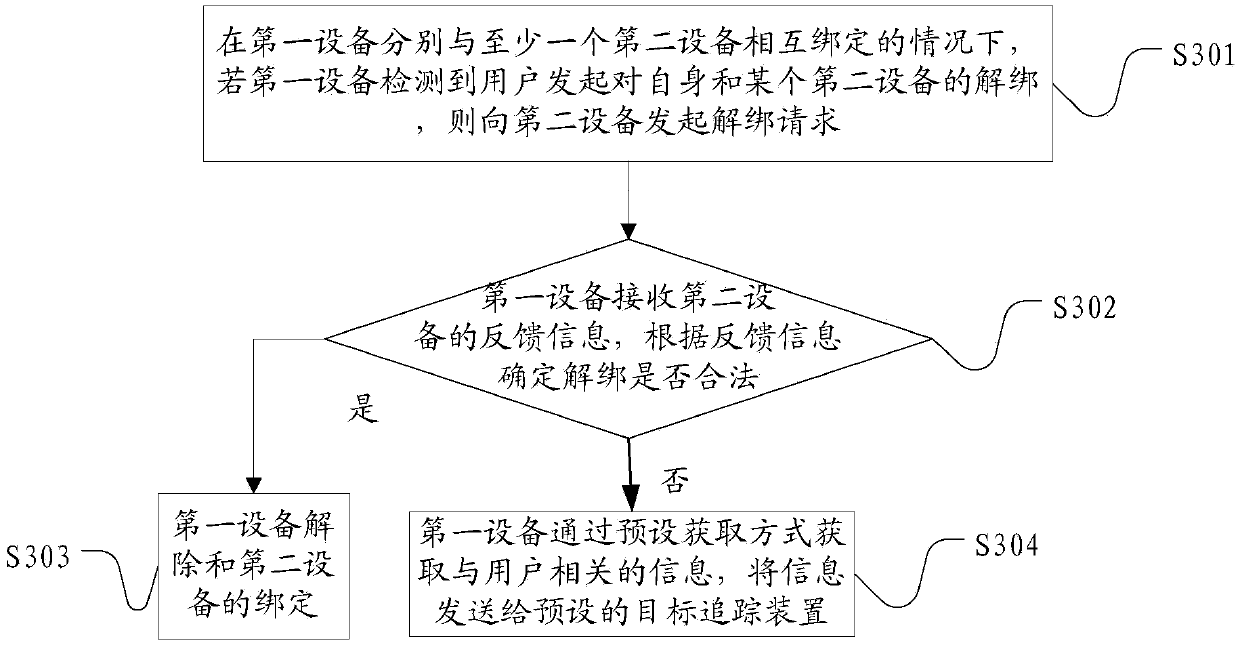
[0071] At present, many manufacturers have launched their own smart wearable devices such as smart watches and smart bracelets. These smart devices can be bound to the user's mobile phone as an extension of the user's mobile phone functions. To provide convenience for users' normal communication under certain circumstances. Some users even use a mobile phone to bind multiple smart wearable devices. In some cases, if the mobile phone or smart wearable device is obtained by an illegal user, the illegal user will prevent the information generated by the terminal from being sent to the terminal bound to the terminal. On other terminals, generally choose to unbind the terminal and other terminals, so that the legitimate user loses control over the terminal, in order to avoid such unbinding as much as possible and provide help for the legitimate user to track and retrieve the lost terminal , this embodiment proposes a terminal protection method, such as image 3 As shown, the termi...
no. 2 example
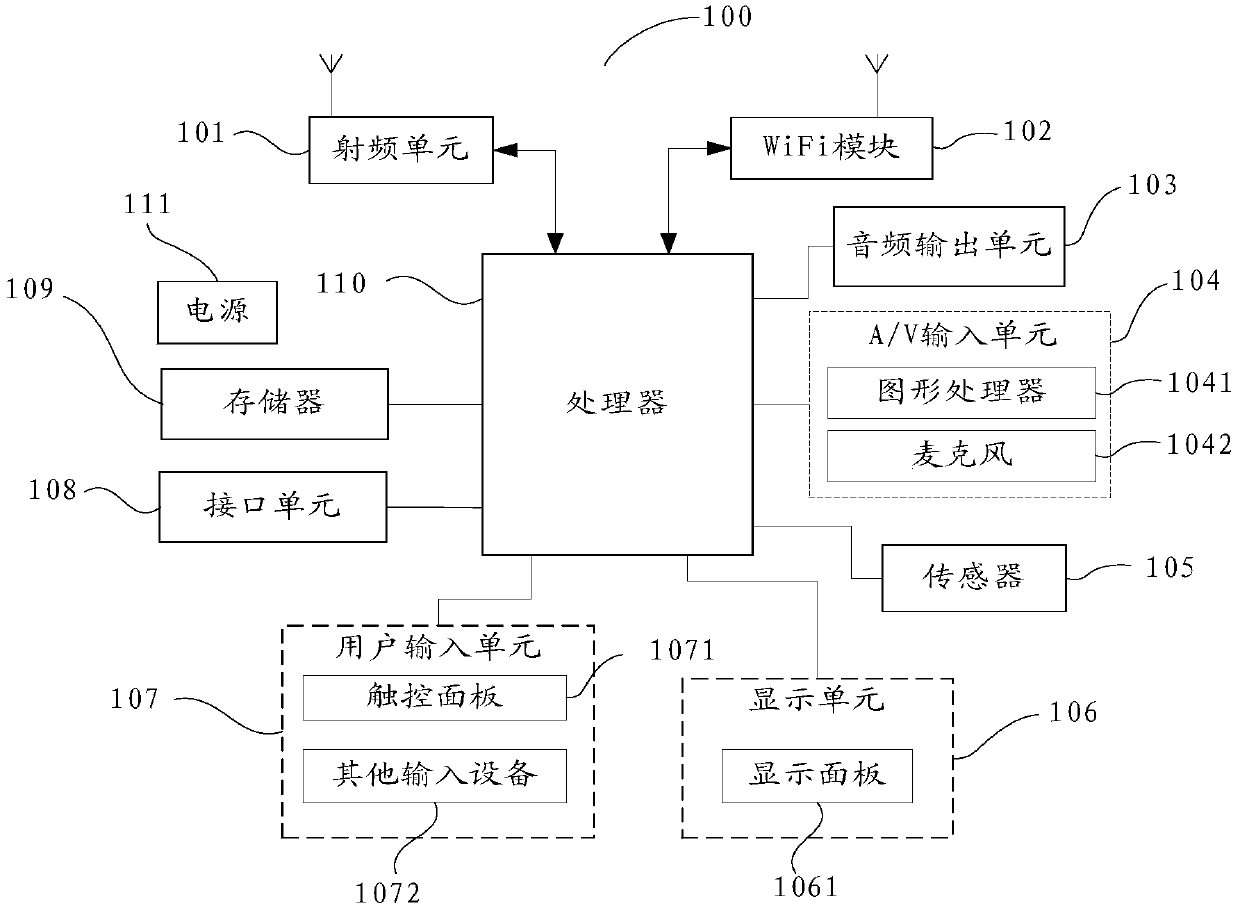
[0122] Such as Figure 5 As shown, this embodiment proposes a terminal, which includes a processor 51, a memory 52, and a communication bus 53;
[0123] The communication bus 53 is used to realize connection and communication between the processor 51 and the memory 52;
[0124] The processor 51 is configured to execute one or more programs stored in the memory 52, so as to implement the steps of the terminal protection method proposed in Embodiment 1.
[0125] This embodiment also proposes a computer-readable storage medium, where one or more programs are stored in the computer-readable storage medium, and one or more programs can be executed by one or more processors, so as to realize the The steps of the terminal protection method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com