cpk-based linux operating system login authentication method, equipment, terminal and server
A login authentication and operating system technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., to improve login security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
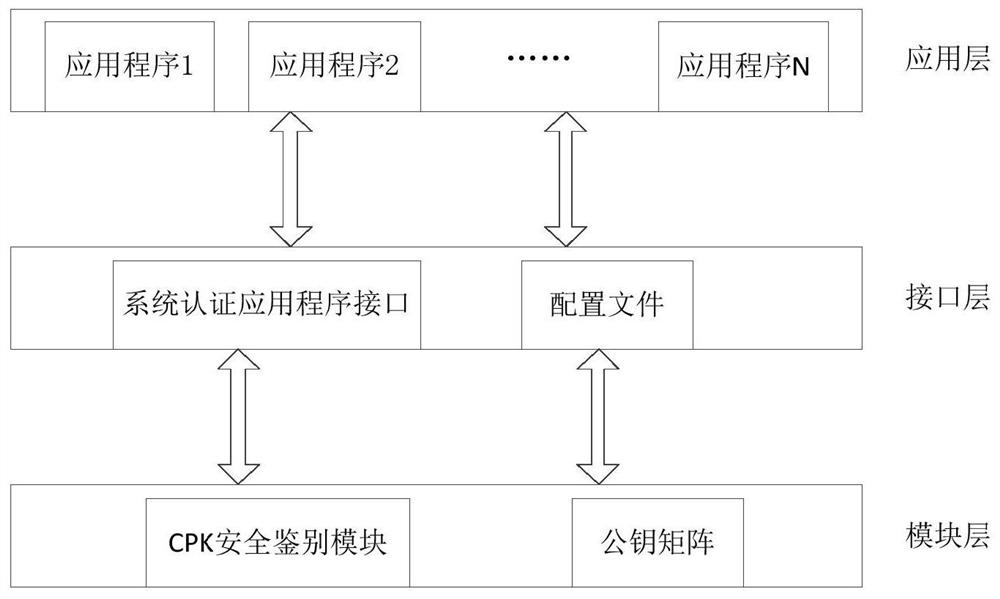
Image
Examples
Embodiment 1
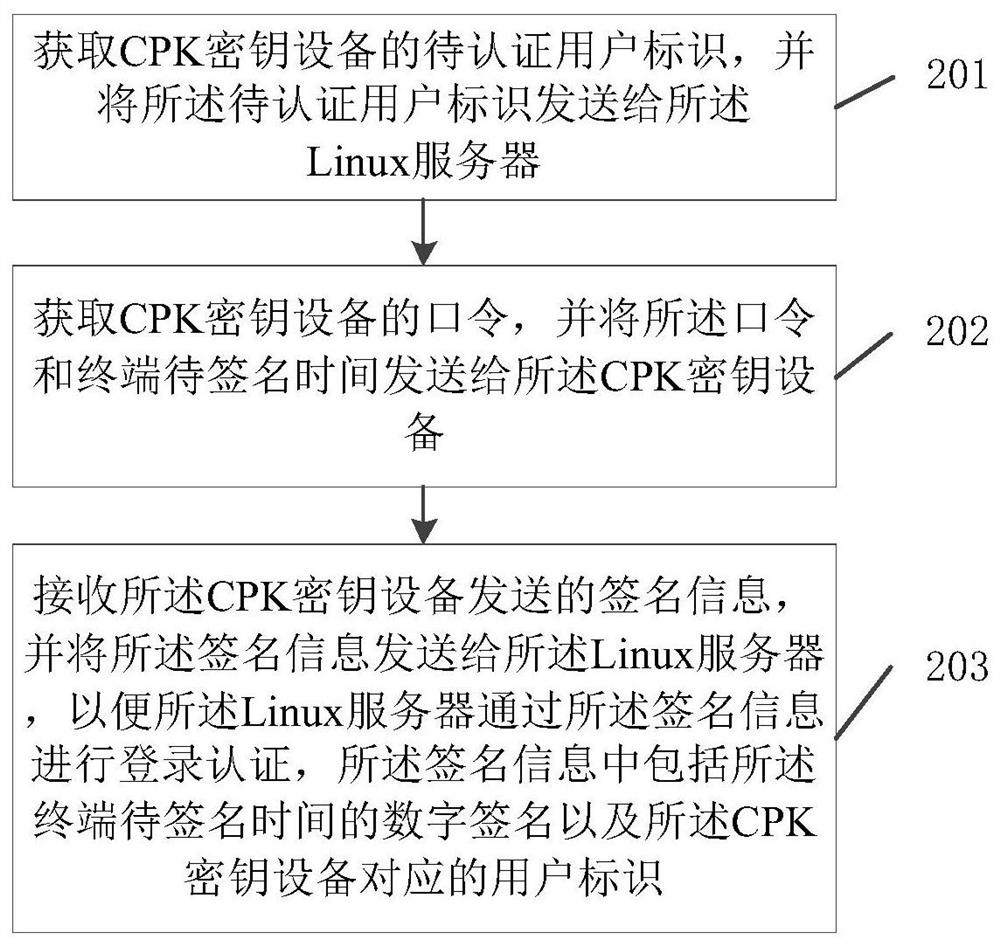
[0037] figure 2 It is a schematic flowchart of a CPK-based login authentication method for a Linux operating system provided by an embodiment of the present invention. like figure 2 As shown, the method is applied to a terminal, and the method includes the following steps:
[0038] Step 201, obtaining the user ID to be authenticated of the CPK key device, and sending the user ID to be authenticated to the Linux server;
[0039] Step 202, obtaining the password of the CPK key device, and sending the password and the waiting time of the terminal to be signed to the CPK key device;
[0040] Step 203: Receive the signature information sent by the CPK key device, and send the signature information to the Linux server, so that the Linux server can perform login authentication through the signature information, and the signature information includes the The digital signature of the terminal's pending signing time and the user identification corresponding to the CPK key device. ...
Embodiment 2
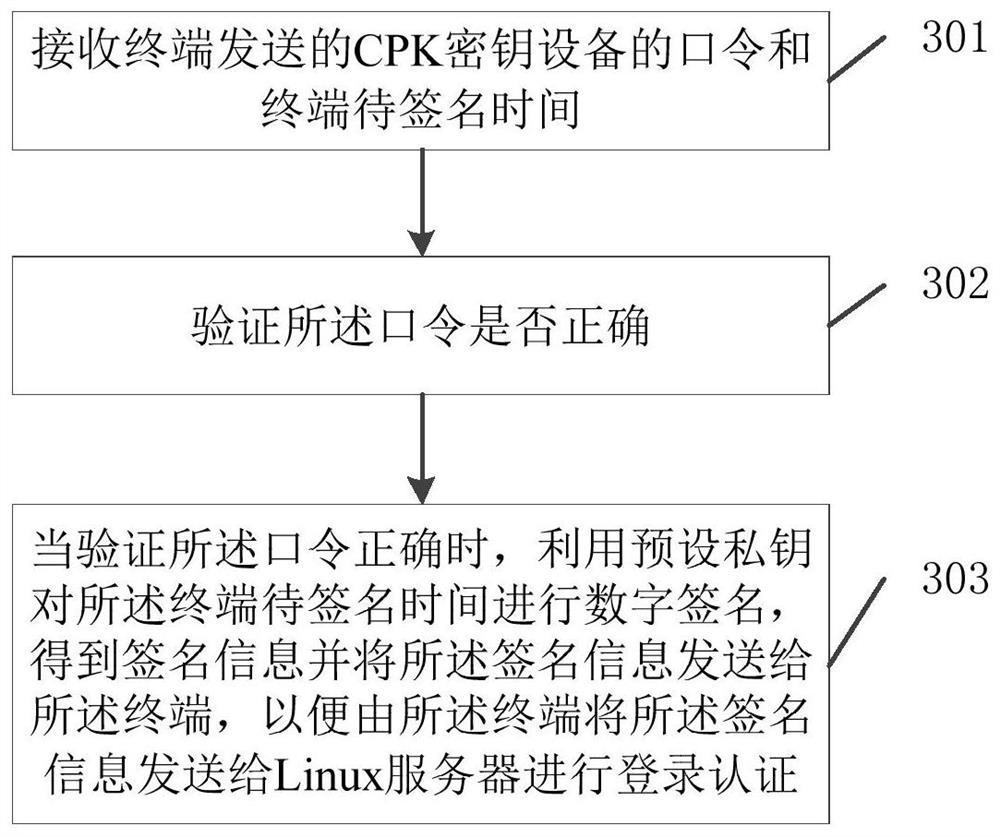
[0046] image 3 It is a schematic flowchart of a CPK-based login authentication method for a Linux operating system provided by an embodiment of the present invention. like image 3 As shown, the method is applied to a CPK key device, and the method includes the following steps:
[0047] Step 301, receiving the password of the CPK key device sent by the terminal and the time to be signed by the terminal;
[0048] Step 302, verifying whether the password is correct;
[0049] Step 303, when verifying that the password is correct, use the preset private key to digitally sign the time to be signed by the terminal, obtain signature information and send the signature information to the terminal, so that the terminal will The signature information is sent to the Linux server for login authentication.
[0050] Wherein, when the password is verified incorrectly, a password verification error notification is sent to the terminal.
[0051] In addition, the CPK key device stores the ...
Embodiment 3
[0055] Figure 4 It is a schematic flowchart of a CPK-based login authentication method for a Linux operating system provided by an embodiment of the present invention. like Figure 4 Shown, described method is applied to Linux server, and described method comprises the steps:
[0056] Step 401, receiving the user identifier to be authenticated sent by the terminal, and determining whether the user identifier to be authenticated exists in the legal user information of the Linux operating system;
[0057] Step 402: After determining that the user ID to be authenticated exists in the legal user information of the Linux operating system, receive the signature information sent by the terminal, and perform login authentication according to the signature information, the signature information includes The digital signature of the terminal's pending signature time and the user ID corresponding to the CPK key device.
[0058] Wherein, after determining that the user ID to be authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com