A permission setting method and device
A permission and algorithm technology, applied in the field of data communication, can solve the problems of system administrators spending a lot of time, the permission setting process is rigid, and the response speed is slow, so as to save labor costs, respond quickly, and save resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
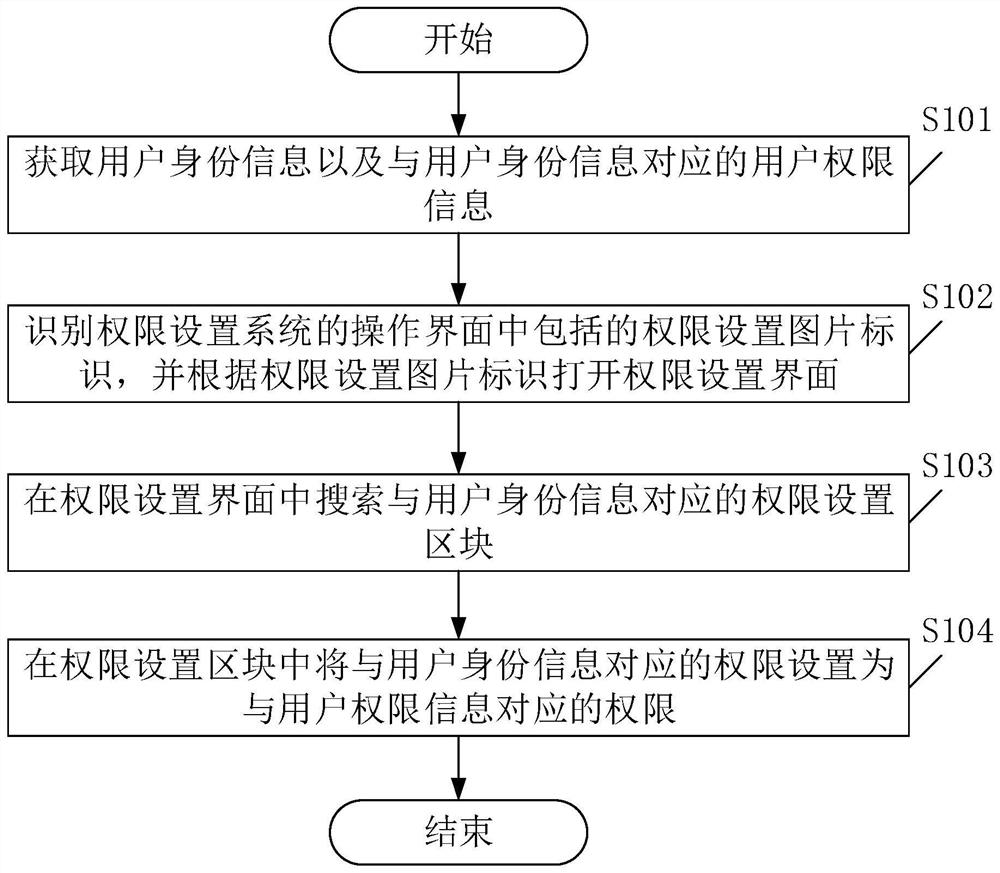
[0048] see figure 1 , figure 1 It is a schematic flowchart of a permission setting method provided by an embodiment of the present invention. Among them, such as figure 1 As shown, the permission setting method may include the following steps:
[0049] S101. Acquire user identity information and user authority information corresponding to the user identity information.
[0050] In this embodiment, a correspondence table of user identity information and user authority information can be input, and the correspondence table includes a plurality of user identity information and user authority information corresponding to each user identity information, which can be obtained one by one from the correspondence table For one user identity information and its corresponding user authority information, step S101 to step S104 are repeatedly executed until the authority corresponding to all user identity information in the corresponding table is set as the user authority information co...
Embodiment 2
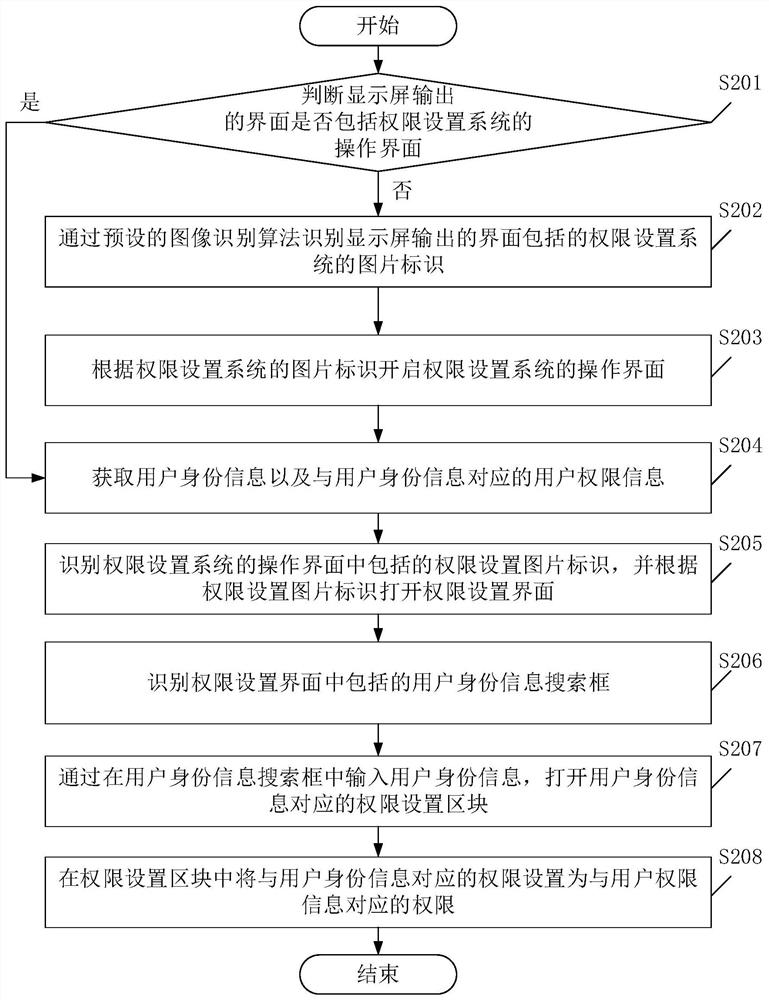
[0061] see figure 2 , figure 2 It is a schematic flowchart of a permission setting method provided by an embodiment of the present invention. Among them, such as figure 2 As shown, the permission setting method may include the following steps:
[0062] S201. Determine whether the interface output by the display screen includes the operation interface of the authority setting system, if yes, perform steps S204 to S208; if not, perform steps S202 to S208.
[0063] The execution subject of the permission setting method described in this embodiment may be a computer device with a display screen, a terminal device with a display screen, a wearable device with a display screen, etc., which is not limited in this embodiment.
[0064] S202. The image identification of the permission setting system included in the interface output by the preset image recognition algorithm and the model recognition display screen.
[0065] S203. Open the operation interface of the authority setti...
Embodiment 3
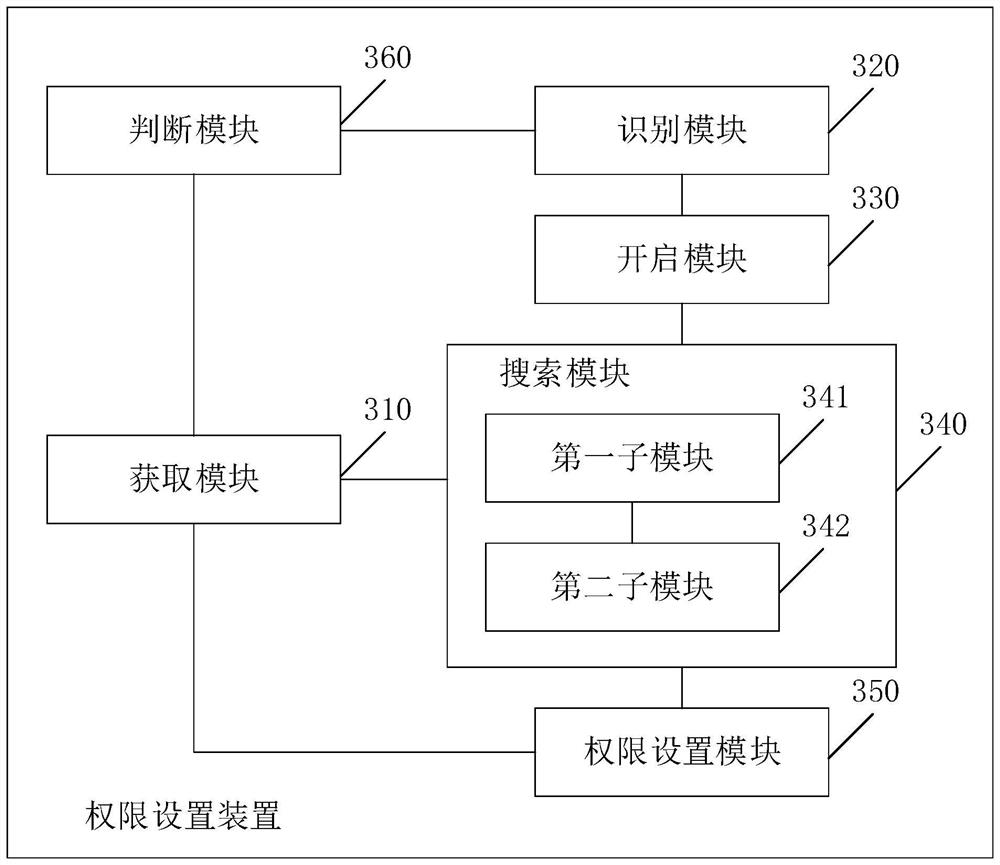
[0106] see image 3 , image 3 It is a schematic structural diagram of a permission setting device provided by an embodiment of the present invention. Among them, such as image 3 As shown, the permission setting device includes:
[0107] The acquiring module 310 is configured to acquire user identity information and user authority information corresponding to the user identity information.
[0108] The recognition module 320 is configured to recognize the permission setting picture logo included in the operation interface of the permission setting system.
[0109] The opening module 330 is configured to open the authority setting interface according to the authority setting picture identification.
[0110] A search module 340, configured to search the authority setting block corresponding to the user identity information in the authority setting interface.
[0111] The authority setting module 350 is configured to set the authority corresponding to the user identity info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com