Data layered encryption device, related electronic device, and storage medium
A technology for encrypting devices and data, applied in the electronic field, can solve the problems of heavy load and the security of the cryptographic system, etc., and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
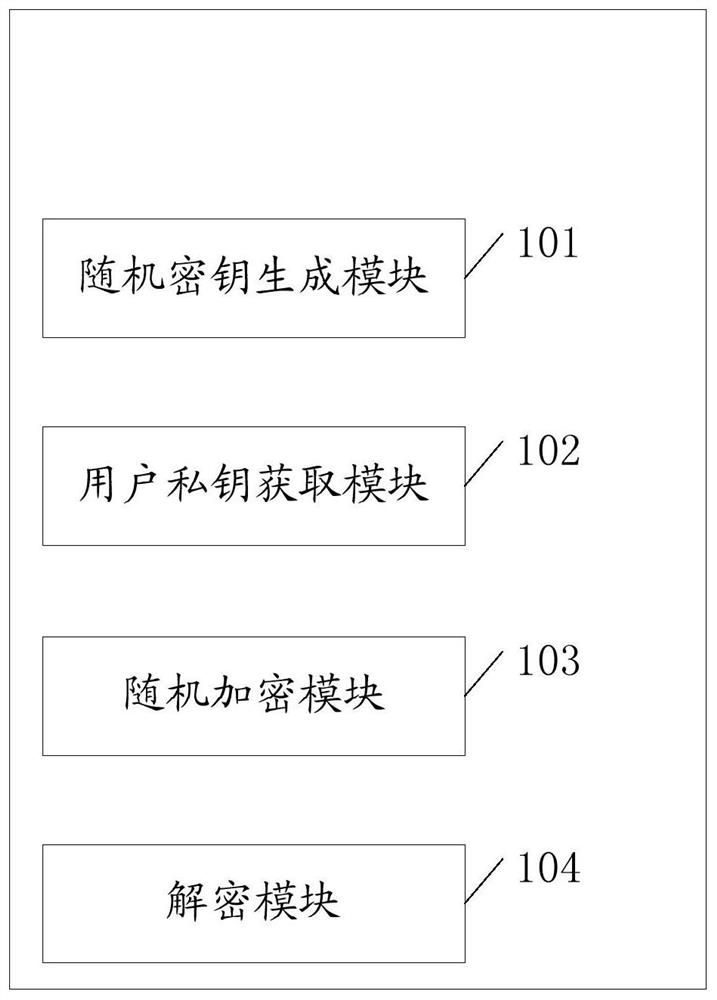
[0021] Hierarchical identity-based encryption (HIBE) is an extension of identity encryption technology. This technology can relieve the load on the trusted key generation center and is more suitable for ensuring data security in a distributed environment. The invention provides a lattice-based server data protection protocol. In terms of efficiency, since the protocol is designed based on the R-LWE difficulty assumption, it has high operating efficiency in the encryption and decryption stages, and the encryption and decryption operations of each bit The number is At the same time, the protocol proposed by the invention is semantically safe for adaptively chosen identity attacks.
[0022] In a layer-1 HIBE protocol, there is also a trusted authority center responsible for generating the master public key and the master private key. Like IBE, the center can use the master private key as the identity 1 The user generates the corresponding private key , while the additional fu...
Embodiment 2
[0046] On the basis of the structure of the above-mentioned embodiment one data layered encryption device, the embodiment of the present invention describes that: if any PPT second user whose security parameter is n The advantage in the following embodiment rules is negligible, then layer 1 HIBE (HIBESetup, HIBEDer, HIBEEnc, HIBEDec) selects identity attack security (ie IND-sID-CPA) under the CPA model.
[0047] Among them, the following first user is the user of the data layered encryption device in the embodiment of the present invention, and the second user is the attacking user of the data layered encryption device in the embodiment of the present invention; the IND-sID-CPA application embodiment rule can describe as follows:
[0048] Target identity determination: the first user will 1 n ,1 l and other public parameters are sent to the second user output a "target" identity vector
[0049] Setup: The first user enters the security parameter n, and runs the maste...
Embodiment 3
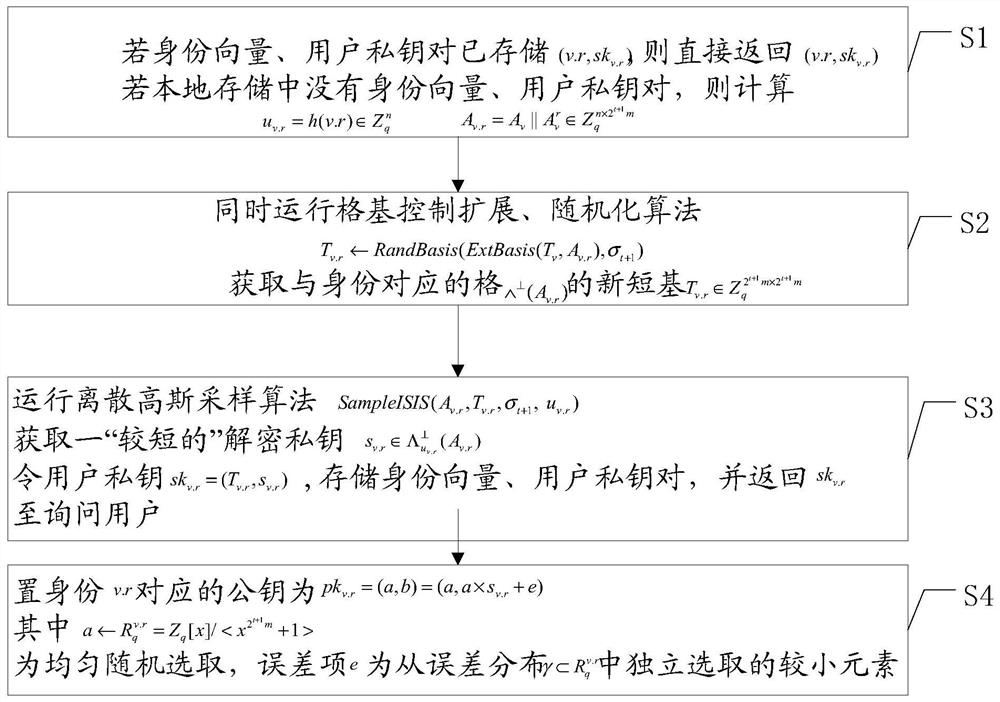
[0062] On the basis of the framework of the first embodiment of the data layered encryption device, the embodiment of the present invention describes: the specific setting content of the protocol based on the data layered encryption device, including:
[0063] Let the hash function respectively mapping the corresponding identity to and Two random oracles for elements in , is the upper bound on the norm of the group of Clem-Schmidt orthogonalization vectors of the secret short basis corresponding to the identity vector v(|v|=i), σ i (1≤i≤l) is the Gaussian parameter used to generate the secret short base time, which needs to meet the conditions: for have established.
[0064] An Efficient Layer-1 HIBE Protocol Based on the R-LWE Assumption Can be specifically described as follows:
[0065] ·Random key generation algorithm HIBESetup(1 n ): input security parameter n, integer m≥Cnlgq and m=2 d (d∈Z), a large prime number q=1mod(2m) and the layer number l of the HI...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com