A confirmation method for web backdoor attack events
An attack event and backdoor technology, applied in electrical components, digital transmission systems, data exchange networks, etc., can solve problems such as frequent page turning, misjudgment, and lack of authority for server operation and maintenance, and achieve improved recognition rate and accuracy, The effect of reducing the false positive rate of alarms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
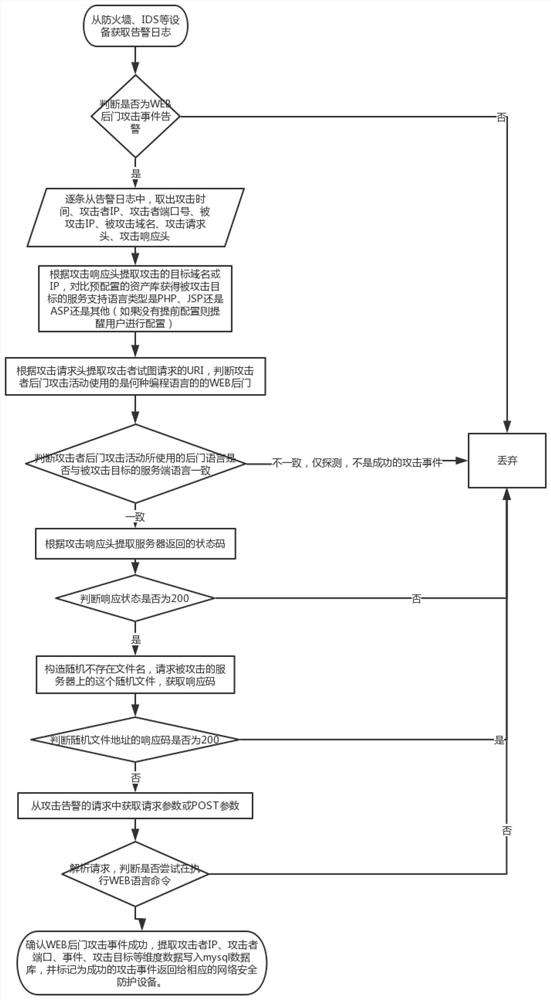
[0025] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0026] The confirmation method of WEB backdoor attack event of the present invention comprises the following steps:
[0027] (1) Obtain the alarm log from the network security protection device, judge whether it is a WEB backdoor attack event alarm according to the type description field of the log, and discard if not; the network security protection device can refer to a firewall or an IDS device (Intrusion Detection System, Intrusion Detection Systems ).
[0028] (2) From the alarm log of WEB backdoor attack, take out the attack time, attacker IP, attacker port number, attacked IP, attacked domain name, attack request header and attack response header recorded in each alarm log one by one;
[0029] (3) Extract the target domain name or IP of the attack according to the attack response header, and compare the pre-configured se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com