A security access system and security access method based on trust token
A secure access and token technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of client manslaughter, lack of strong authentication and continuity support, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] Below, the specific implementation manner of the technical solution of the present invention will be further described in detail in conjunction with the accompanying drawings:
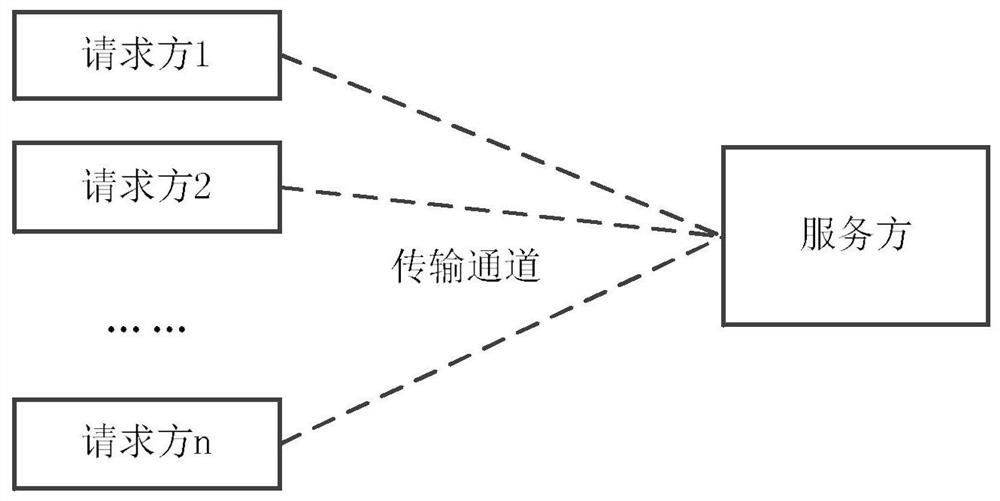
[0075] In the Internet environment, the server provides access services for a large number of clients at the same time. Usually, the server can support concurrent access operations of a certain number of clients. However, in some special cases, there will be more access operations than expected, such as centralized access operations caused by normal users due to a specific event, denial of service attacks caused by malicious users impersonating multiple users at the same time, etc. At this time, the server There is a need for a secure access system that can dynamically adjust the user access time according to the load state, and can increase the difficulty for a malicious user to impersonate multiple users at the same time.
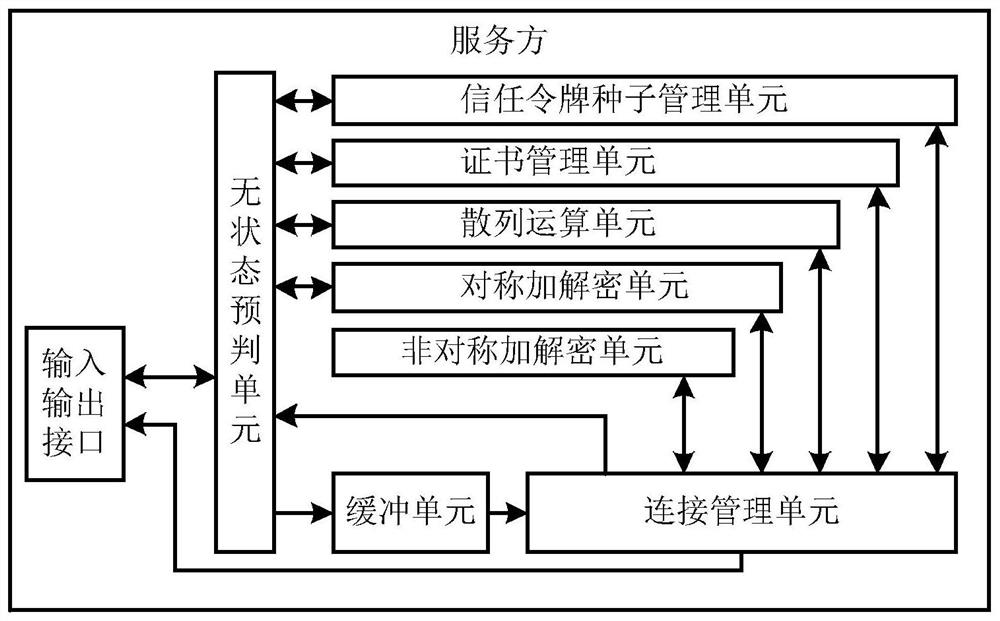
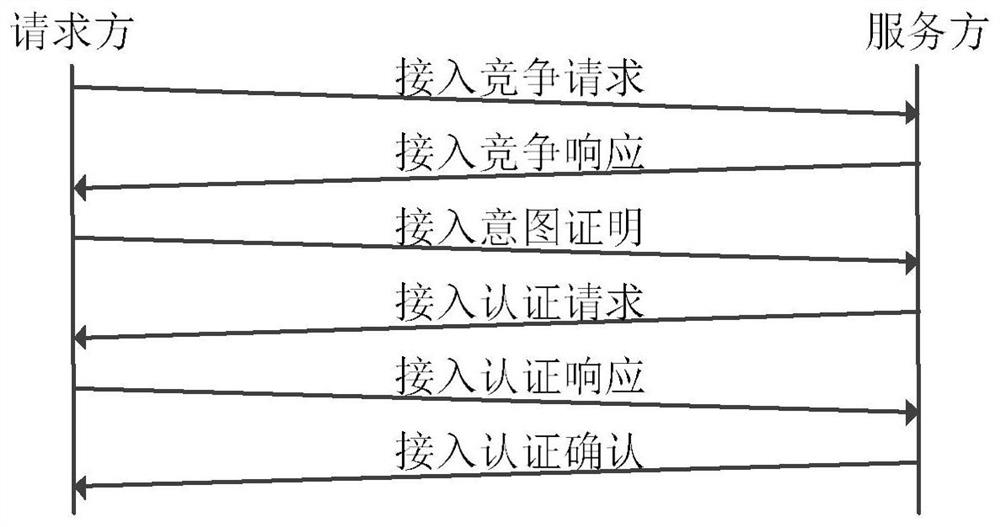
[0076]The secure access system based on trust tokens in the present i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com