Self-destructive documents for information security and privacy protection
A file and filament technology, applied in the field of self-destructing files for information security and privacy protection, can solve the problems of lack of practical application, solutions that cannot meet urgent needs, and incomplete erasure of information, etc., and achieve small increments cost effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
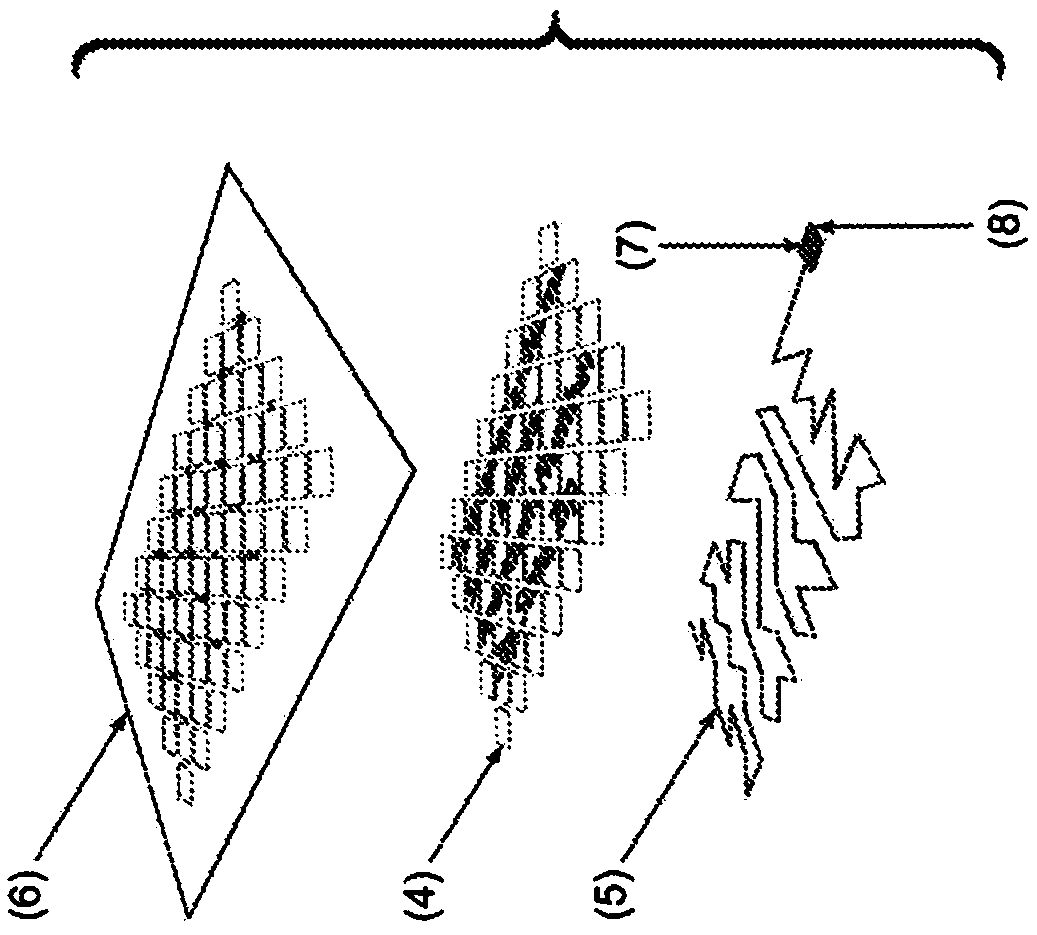
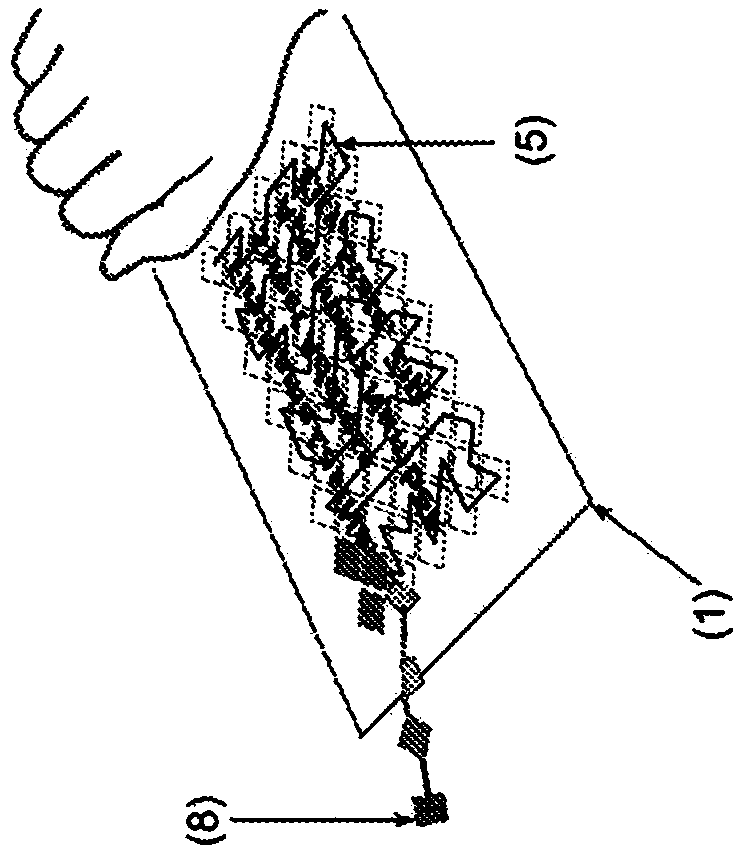
[0038] Example 1: This example provides a solution to the theft of corporate information such as communications generated in a controlled work environment. Such as Figure 1A As shown in , the present invention includes a cover sheet, a filament, and a release device, and may further include optional tabs. In this embodiment, the cover sheet is perforated so that the cutouts can be easily detached by pulling on the filament, but the pages retain their integrity and usability until detached. To destroy, the document is placed on a flat surface, text down, filament side up, anchored at the corners or as desired (e.g. by hand), and the filament is pulled to disengage the cutout. By removing the cutouts and the information printed thereon, the prints remaining on the residual document frame become incomprehensible when the prints are distributed over the entire surface of the document. Next, the stripper is pulled along the length of the hollow with the filament, sometimes with a...
example 2
[0039] Example 2: This example provides another solution to corporate information theft such as communications generated in a controlled work environment. As previously stated, the present invention includes a cover sheet, a filament with optional tabs, and a release device, and further includes a backing sheet. In this embodiment, the backing sheet has no adhesive covering the lower surface, and the optional release liner is omitted. The addition of the backboard supports and strengthens the covering sheet laid over it and provides a stronger file when the environment demands it. In this embodiment, the cover sheet can be perforated more heavily because the cutouts are supported by and adhered to the underlying non-perforated backing sheet. In this embodiment, the filaments are laid over the cover sheet and comprise a writable surface. In another embodiment, the cutouts can be completely severed from the cover sheet but held in place by an optional transparent top paper tem...
example 3
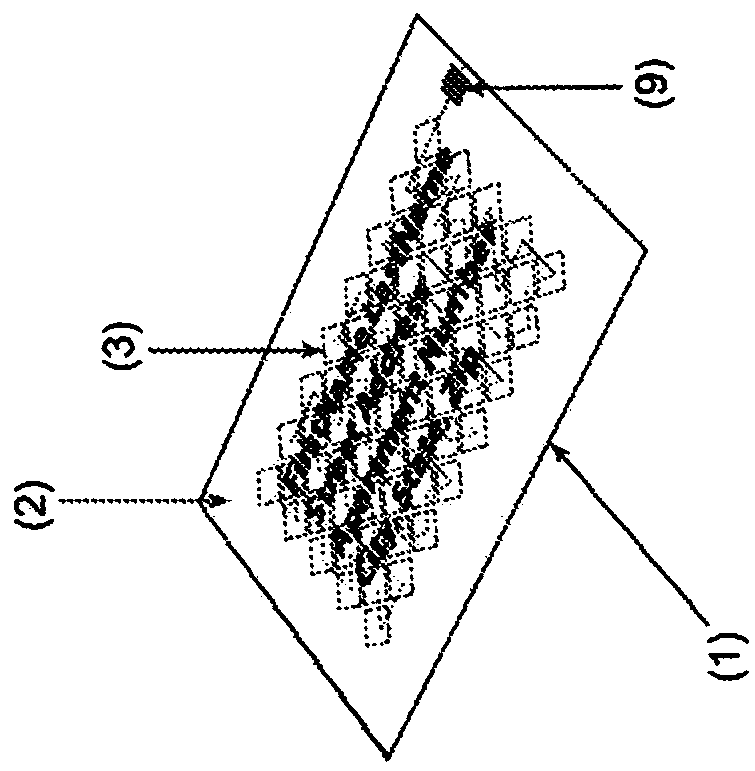
[0040] Example 3: This example provides a solution to the theft of personal information from discarded mail and containers. Such as Figure 2AAs shown in , the present invention provides a mailing label comprising a cover sheet, a filament, a release device and a backing sheet as described above, but in this embodiment, the lower surface of the backing sheet is coated with an adhesive compound, with an optional release liner that can be adhered to packaging, containers or mail. The addition of a backing sheet allows the invention to be attached to an article at will. In this embodiment, the cover sheet can be perforated more heavily because the cutouts are supported by and adhered to the underlying non-perforated backing sheet. By pulling the filaments and peeling away from the backing paper, the cutouts can be removed from the cover sheet, separating at the perforations while leaving the residual frame attached to the backing sheet. When the print is distributed over the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com