A container-based intelligent network security function management method and system
A security function and intelligent network technology, applied in the container-based intelligent network security function management method and system field, can solve problems such as lack of connection and coordination, difficulty in realizing protection process, and single function
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
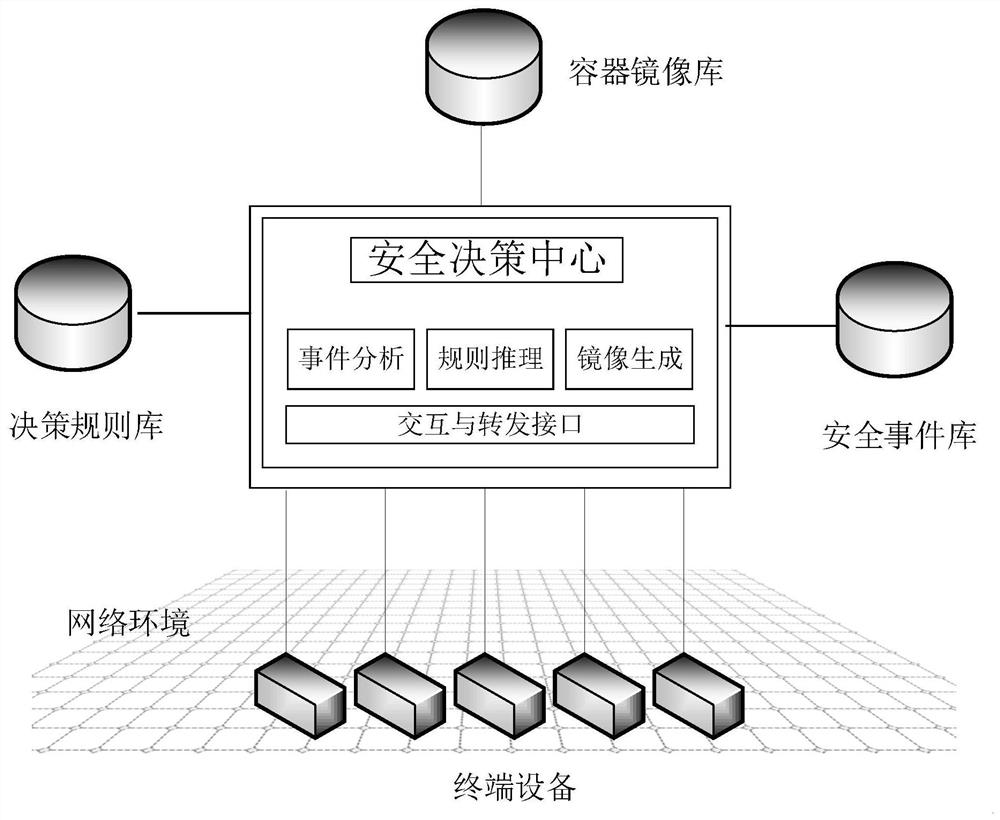
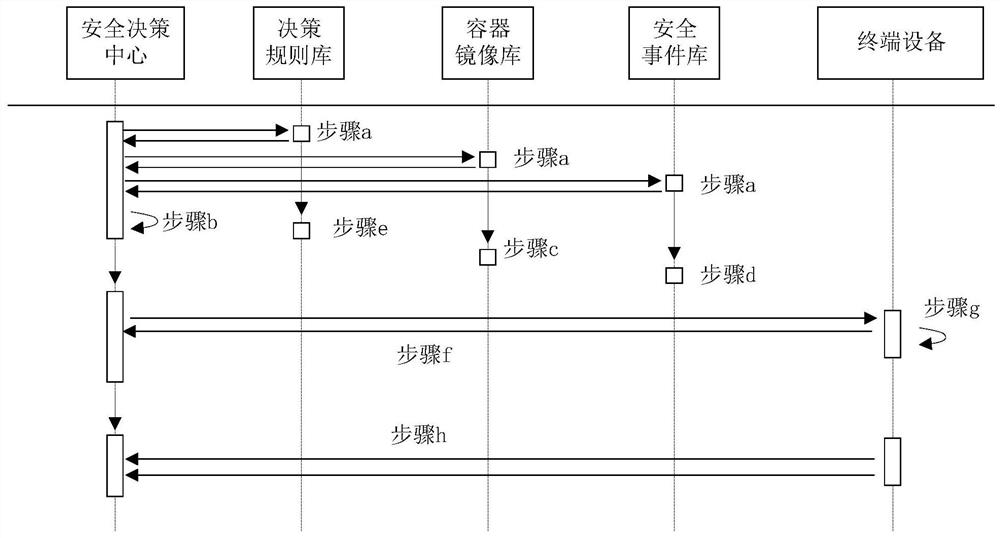
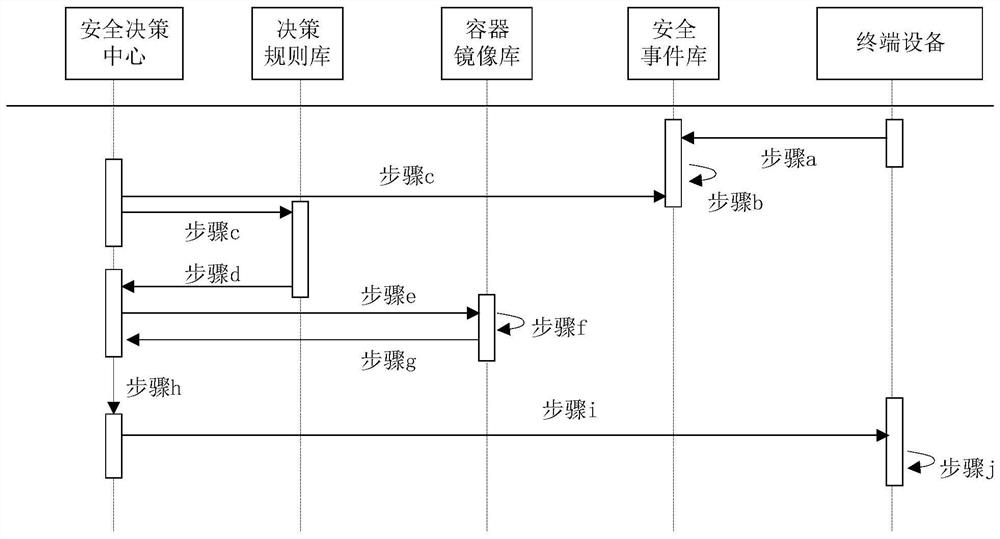
[0075] The container-based intelligent network security function management system provided in this embodiment supports a design pattern and implementation system for dynamic update of security capabilities, rapid deployment, global collaboration, and controllable overhead, and can realize the flow and integration of security resources in the global system. Configuration to achieve the dynamic definition and reconstruction of security functions, and then realize the effective cooperation and connection of security risks and security perception, security perception and security decision-making, security decision-making and security response, and realize the capabilities of security software and hardware equipment from single-point defense, The leap from local defense to overall defense maximizes the utility of security resources. Specifically: as figure 1 As shown, it includes: security decision center, decision rule library, container image library, security event library and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com