Secret divulging prevention method, terminal and computer readable storage medium
A storage medium and computer technology, applied in computer security devices, calculations, special data processing applications, etc., can solve problems such as low user experience satisfaction and easy leakage of leaked files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
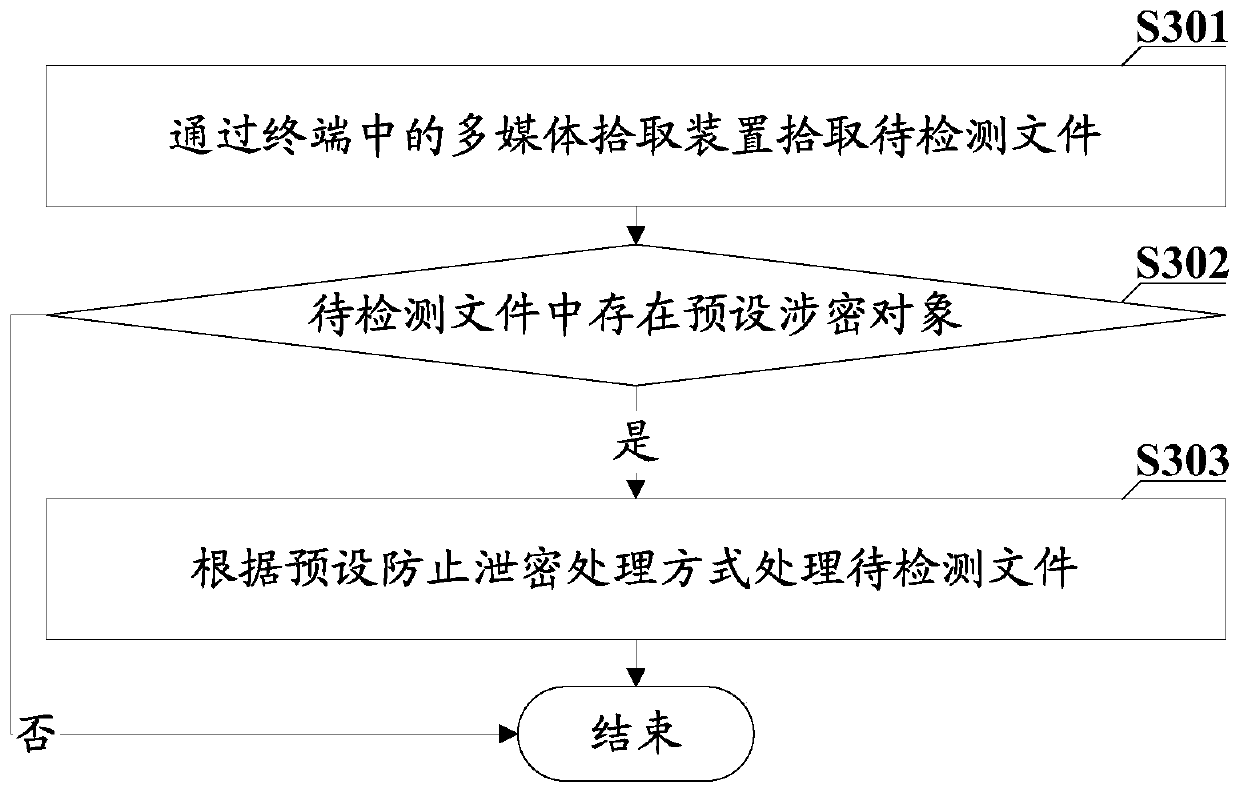
[0069] In order to solve the problem in the prior art that secret-related files are easily circulated, resulting in low user experience satisfaction, this embodiment provides a method for preventing secret leakage. Specifically, see image 3 as shown, image 3 The basic flowchart of the method for preventing leakage provided by this embodiment, the method for preventing leakage includes:
[0070] S301. Pick up the file to be detected by the multimedia pick-up device in the terminal.
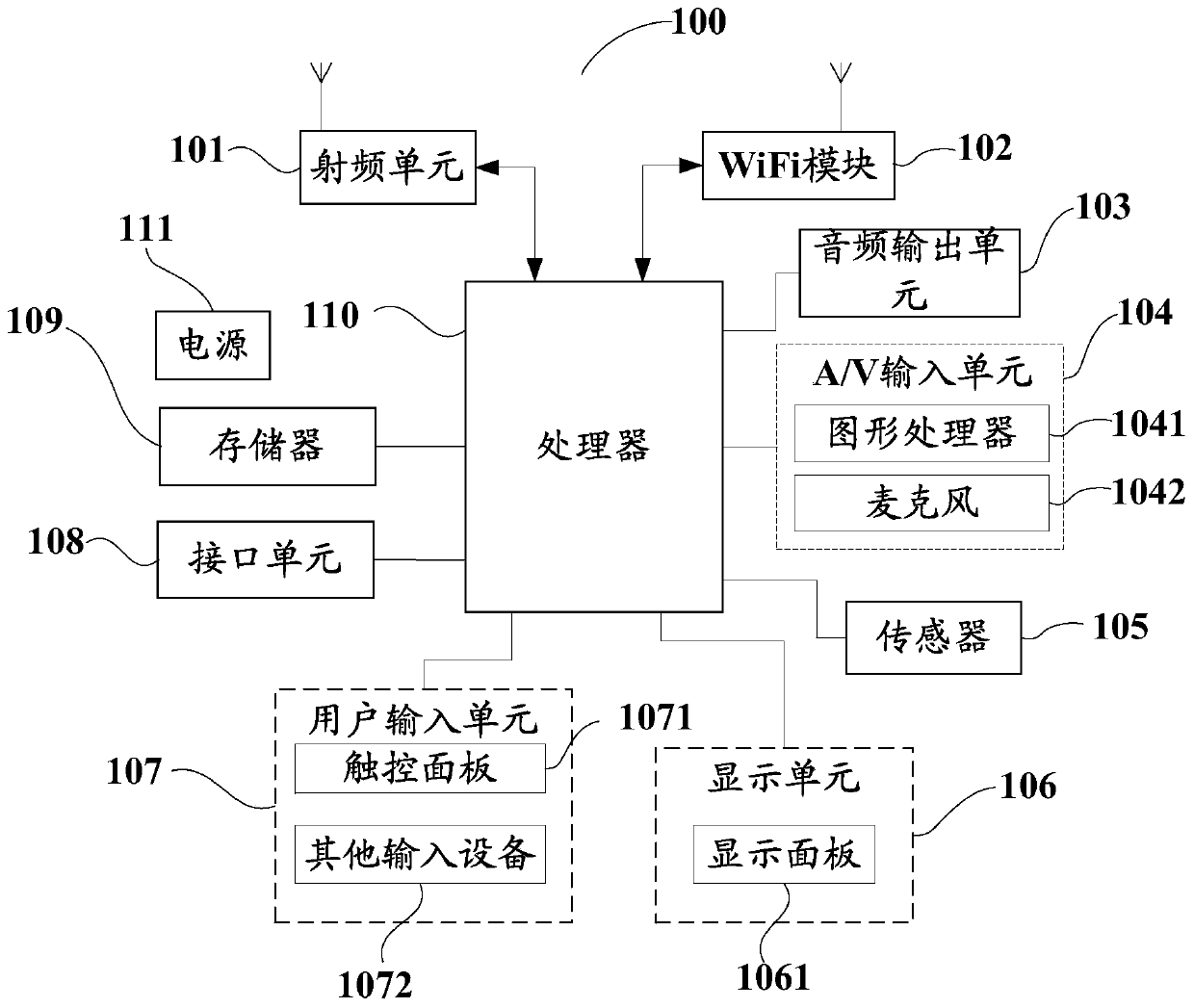
[0071] It should be noted that the terminal described in this embodiment may be as follows figure 1 The terminals shown can, of course, also be other terminals.
[0072] In this embodiment, the file is picked up by the multimedia picking device in the terminal, and then the picked up file is used as the file to be detected. Wherein, the multimedia pickup device includes but not limited to at least one of a camera, an audio pickup device, and the like. For audio pickup devices, this includes,...
no. 2 example
[0104] In order to better understand the present invention, this embodiment is described in combination with more specific examples, please refer to Image 6 as shown, Image 6 It is a detailed flow chart of the leak prevention method provided by the second embodiment of the present invention, the leak prevention method includes:
[0105] S601. Pick up the file to be detected by using the multimedia pick-up device in the terminal.
[0106] After the file is picked up by the multimedia pick-up device in the terminal, the file is taken as the file to be detected.
[0107] In this embodiment, the multimedia pick-up device includes a camera, that is, after taking a picture through the camera in the terminal, the taken picture is used as the picture to be detected. It should be noted that, in this embodiment, the multimedia pickup device is used as an example for description. In other embodiments, the camera may also be an audio pickup device or the like.
[0108] S602. Determin...
no. 3 example
[0140] This embodiment provides a terminal, please refer to Figure 7 As shown, the terminal provided in this embodiment includes a processor 701 , a memory 702 and a communication bus 703 .
[0141] Wherein, the communication bus 703 in this embodiment is used to realize connection and communication between the processor 701 and the memory 702;
[0142] The processor 701 is used to execute one or more programs stored in the memory 702, so as to realize the following steps:
[0143] Pick up the file to be detected by the multimedia pick-up device in the terminal;
[0144] Judging whether there is a preset secret-related object in the file to be detected;
[0145] If yes, the file to be detected is processed according to a preset leak prevention processing method.
[0146] In this embodiment, the file is picked up by the multimedia picking device in the terminal, and then the picked up file is used as the file to be detected. Wherein, the multimedia pickup device includes b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com