Local sensitivity counting summary method and system for network anomaly detection
A network anomaly and sensitivity technology, applied in the field of network communication, can solve problems such as judgment errors, reducing the effectiveness of counting summary queries, and query result deviations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
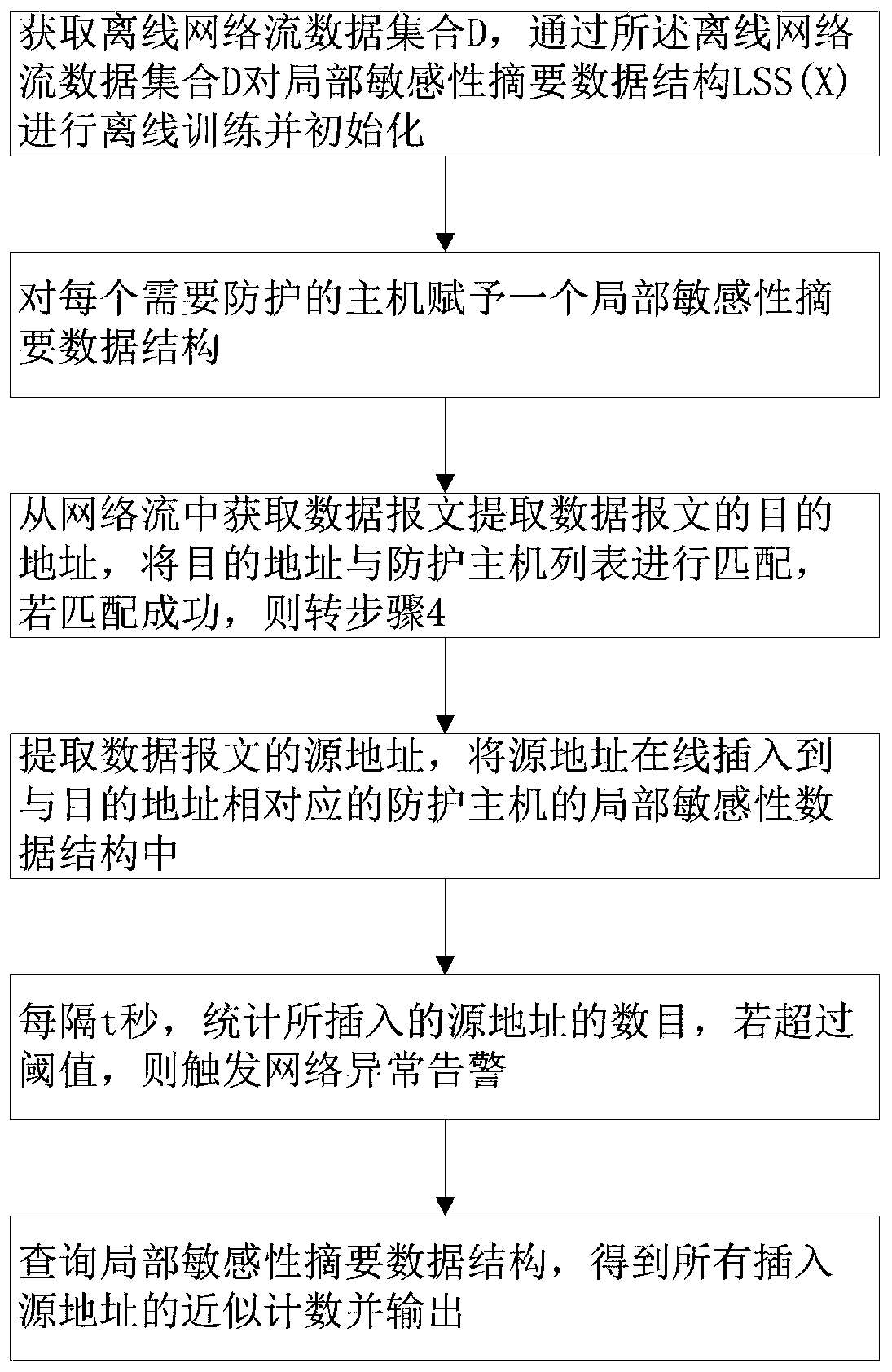
[0053] figure 1 A specific embodiment of a local sensitivity counting summary method for network anomaly detection of the present invention is shown, including the following steps:
[0054] Step 1: Obtain the offline network flow data set D from the network, and perform offline training and initialization on the local sensitivity summary data structure LSS(X) through the offline network flow data set D; use the network flow offline data for offline training to obtain a The data packet flow clustering model is used to guide the online insertion process of each local sensitivity summary data structure; the offline training in this embodiment regularly performs network flow data training, so as to update the data packet clustering model in time, and can also Avoid the cluster center shift caused by the real-time update process.
[0055] Step 1.1: Obtain the offline network flow data set D from the network, use the key key of each data packet in the network flow data as the uniqu...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap